
The word "hacker" found its current sound only in the second half of the 20th century thanks to journalists. Initially, hackers were called specialists who have extensive knowledge in the field of computer technologies and are able to masterfully use them. It is about the activities of one of the groups of such hackers that will be discussed in this article.
Introduction
2007 Nvidia CUDA — - , , . GPU GPGPU (General Purpose GPU), Nvidia - . , , . , , , . UCAS AES, .
, CUDA AES:
CUDA
CUDA (Compute Unified Device Architecture) — - , Nvidia . CUDA .
, CUDA, :
(kernel) — , GPGPU;
(grid) — , ;
(block) — . --- ;
(, thread) — .
, . CUDA .
, GPGPU.
CUDA
CUDA, GPGPU ( ):
(Scalar Processor, SP) — , ;
(Streaming Multiprocessor, SM) — SP, , 32- (Instruction Unit). SM L1-, SP. SM , ;
GPU — SM, .
GPGPU, , . 32 (warp). , SIMT- (Single Instruction Multiple Threads).
GPGPU , . .
.
AES
Advanced Encryption Standard (AES), Rijndael — . 128 128, 192 256 . 128 , 128 .
AES-128 S 4 4 , (state), 11 :
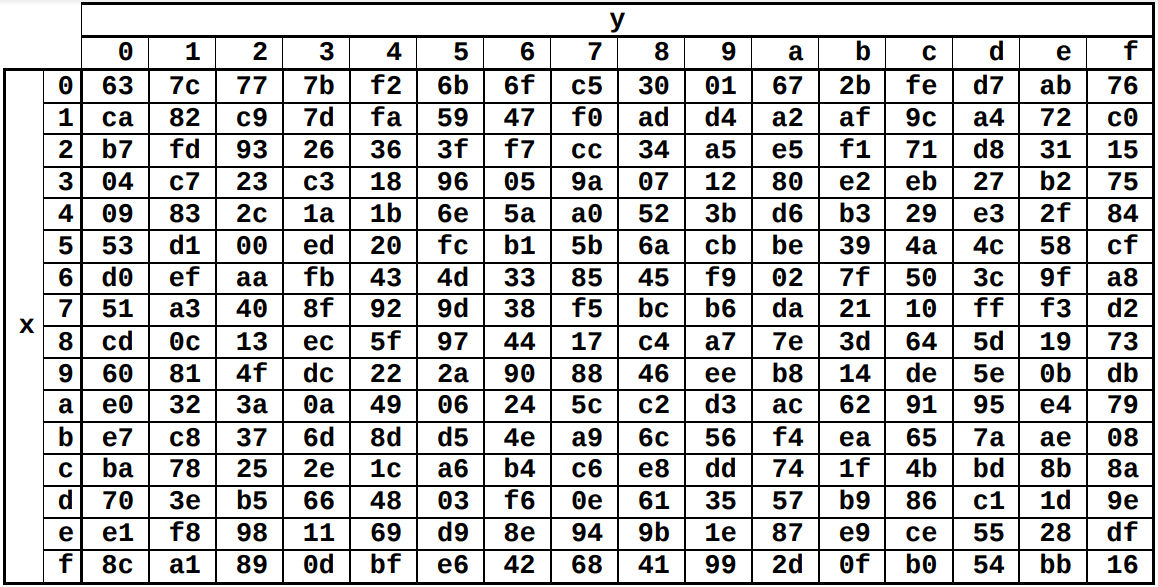
SubBytes — , SBox. 16 16, . :
,
— , ,
-
- SBox. , (Row-Major Ordering)
.
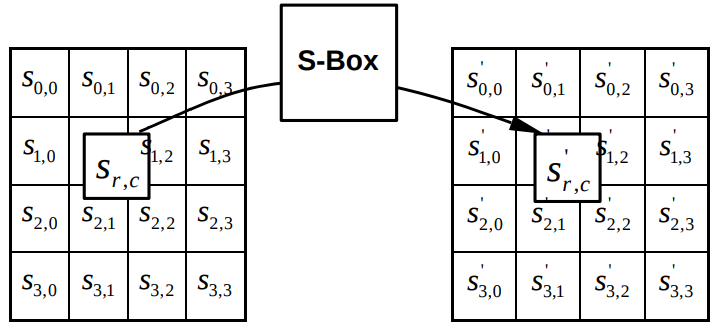
, , . SBox, SBoxLUT (Look Up Table).
ShiftRows — . , , .

MixColumns — , — . SBox, , .

AddRoundKey — RounKey 4 4, . AES " " — 11 , , . KeyExpansion .

, 11 . . , 11- , :
AddRoundKey(0)
for (i = 1; i <= 10; i += 1) {
SubBytes()
ShiftRows()
MixColumns()
AddRoundKey(i)
}
SubBytes()
ShiftRows()
AddRoundKey(11)
, . , -,
.
AES, AES, — , .
32x16 , (Embarrassingly Parallel): , . , , .
. , . .
, ;
;
, ;
, , 16 :
;
256
:
;
3
;
,
;
,
;
, .
, . , , .
— , , . , , GPGPU, , . , . , . .
. , GPGPU, , . , . GPGPU. , .
-
, , - (Simultaneous Cache Collision, SCC). , warp-, , ( SCC) (SCC ) -. .
, - GPGPU Fermi, , 128 . SBoxLUT, SubBytes, 256 , -, . , SCC SBoxLUT ,
.
. :
—
-
- , ,
— . ,
. ,
,
:
InvSBox — , ,
—
-
. , . , , .
-
, , :
. SBoxLUT, -, .
, : :
.
-
: . :
, .
, , , , , . ,
, ,
. ,
—
, . , ,
,
:
.
, ,
, . ,
.
. ,
- 256 ,
. :
—
-
. :
- . , 256 .
.
, . , , AES-128 .
, 1000 , 100 . KEA 600.
, , — .
, . . Nvidia GeForce GT 620 454MiB. , — PolarSSL. Agilent KeySight DSO9104A Rohde&Schwarz RF B.
. AES-128 , , AES-192 AES-256 . , AES-256 2256 2128, .
- GPGPU . , , , , .
Despite the fact that it is difficult to conduct an attack in real life at the moment, it remains interesting from a scientific point of view and can give impetus to the further development of ideas in the direction under study.
PS At the moment, the differences in the formatting of formulas in the editor and when viewing the post are somewhat surprising, in the near future I will try to figure it out.