Accordingly, the lifespan of such attacks is short. In 73% of cases, fake domains are active for one day and are used to send a small number of messages, or even a single one, to a predetermined victim. Analysis of attacks using lookalike domains shows that in 2020 they were most often targeted at e-commerce companies (grocery delivery, online shopping, air ticket sales, etc.). IT services are in second place, followed by industrial production and retail. Last year, the alignment was different: a relatively “expensive” (in terms of time spent on preliminary exploration, but not technology) attack threatened primarily corporations in the financial industry.

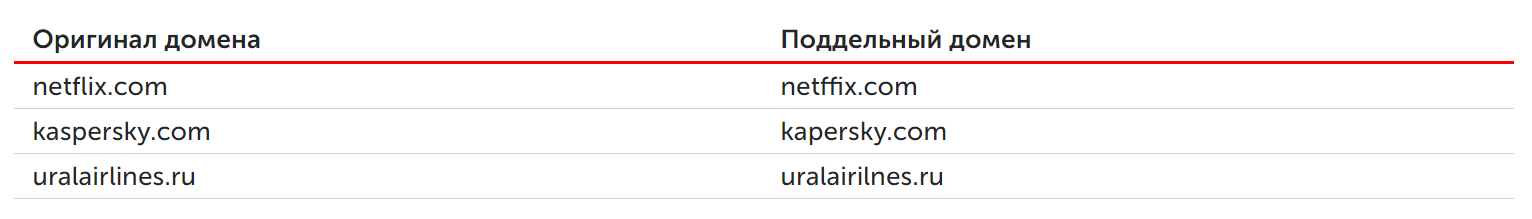
Large companies invest certain efforts in protecting against attacks from domains with extra (missing, confused) letters: most often it is the preventive registration of all similar domains. This approach has an understandable drawback: there are many options for domains, and in a large organization a fake letter can come not only from "own" lookalike addresses, but also from addresses similar to contractors' contacts. The second method is to add lookalike domains to the blacklist, which is fraught with typos and blocking legitimate messages. The research proposes a protection method using a modern anti-spam solution. It not only maintains an up-to-date list of already used lookalike domains, but also analyzes the sender of the letter according to a specific algorithm. The message from a previously unknown source is quarantined, the whois records are analyzed,the time of domain creation and other parameters are noted. The similarity of the sender's address to regular correspondence, combined with other information found during domain analysis, allows you to more accurately separate normal correspondence from phishing attacks.

The article contains data from the FBI unit and the Internet Crime Complaint Center. Aggregated statistics from reports over the past five years show that damage from email attacks has grown fivefold in the United States alone. Public examples of successful BEC attacks are striking in scale and relatively easy to attack. $ 50 million was stolen by sending invoices from a domain similar to a major Taiwanese manufacturer. Toyota subsidiary lost 37 million . An example of a slightly more subtle email scam: cybercriminals have connectedto the correspondence between the two football clubs and took one of the tranches of the player's transfer to their accounts. The damage is half a million dollars. Despite the evolution of modern communication methods (messengers and teleconferencing), email remains an actively used and no less regularly attacked business tool.
What else happened
A serious vulnerability has been found in medical devices such as GE's MRI and X-ray machines. This technique is controlled by a Unix-based computer that the manufacturer can connect to for maintenance. Logins and passwords for connection are default and cannot be changed by the operating organization. Until they are forcedly changed by the service company, it is recommended to restrict access to devices via standard FTP, SSH and Telnet protocols.
FireEye informsabout hacking servers and stealing tools for testing the security of the corporate perimeter. In other words, the cybercriminals gained access to a well-oiled set of “master keys” - exploits for various vulnerabilities in software and network infrastructure. In addition to publicly disclosing information, the company also posted a set of rules on Github to identify and block attacks using stolen software.
Another publication by Kaspersky Lab for 2020 examinesnew habits of remote workers and related threats. Attacks on employees have not fundamentally changed this year, but there are more vulnerabilities in the corporate infrastructure. One of the examples in the study: widespread use of home computers and personal accounts at a distance - most often accounts in mail and instant messengers - for work tasks. Or vice versa - using a work computer for personal affairs.