Author: Innokenty Sennovsky (rumata888)
How to get a student interested in a boring subject? Give learning a form of play. Quite a long time ago someone came up with such a security game - Capture the Flag, or CTF. So lazy students were more interested in learning how to reverse programs, where it is better to insert quotes, and why proprietary encryption is like jumping on a rake with a running start.
Students have grown up, and now experienced professionals with children and mortgages participate in these "games". They have seen a lot, so making a task for the CTF so that the “old people” don't whine is not an easy task.
And if you overdo it with hardcore, the teams who have this non-core subject area or the first serious CTF will be blasted.
In this article, I will tell you how our team found a balance between “hmm, something new” and “this is some kind of tin,” developing the crypt task for the CTFZone finals this year.
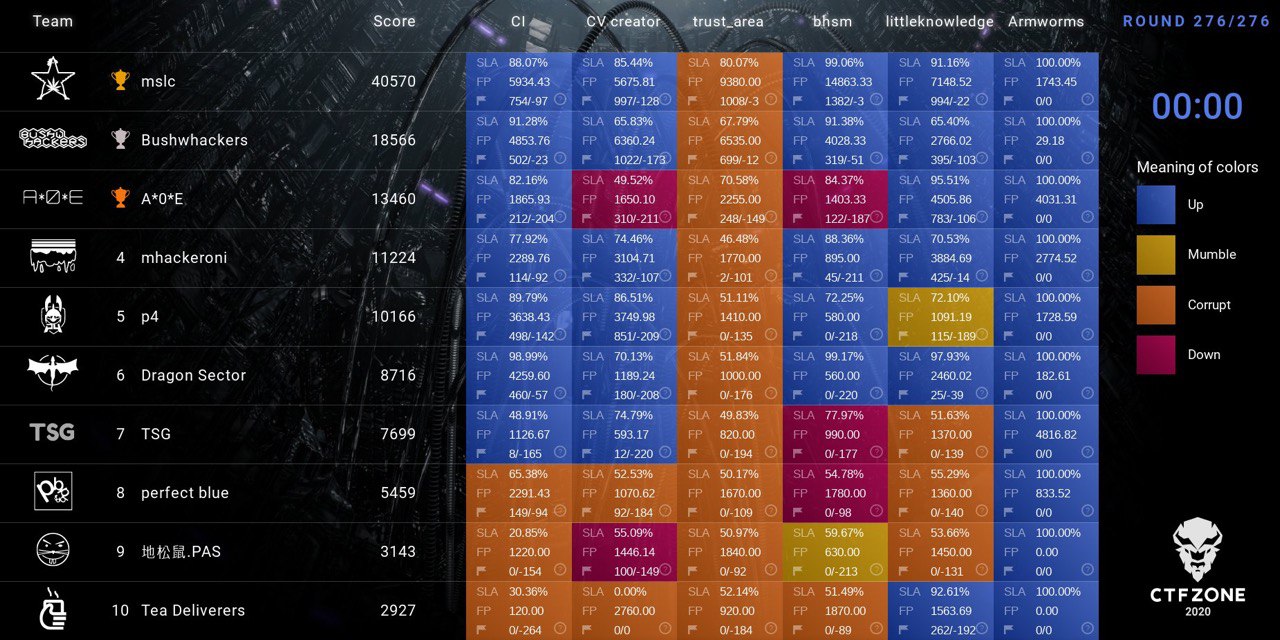
Final scoreboard CTFZone 2020
Content
- Optional introduction: explaining CTF in 2 minutes
- How did we understand that we needed a crypt
- How we chose the stack
- How we found the idea for the task
4.1. A. What is the Hamiltonian property of graphs
4.2. B. How to identify yourself using the Hamiltonian cycle - How we built the task
5.1. Protocol: top view
5.2. Protocol: internals
5.3. The latest vulnerability - How we developed the task
- How we tested the task
- How we dealt with cheating
- Conclusion
Optional introduction: explaining CTF in 2 minutes
, CTF, — . , CTF- .
: jeopardy attack-defense.
jeopardy . «Jeopardy!», « ». , . , «» . , .
attack-defense (AD) . , — . : attack-defense -10 -20 jeopardy.
AD vulnboxes — , . vulnboxes . — , (checker). , .
, — , . , 5 . . vulnbox , .
, :
- vulnbox;
- , ;
- , .
- CTF, , :
- web,
- pwn,
- misc,
- PPC,
- forensic,
- reverse,
- crypto ( , ).
, , jeopardy. , AD . «» , - , CTFZone.
,
CTFZone, , AD.
, AD, , . , . , .
, . . , nonce ECDSA, , .
, . - AD- , . , : . , , .
, ( ), . , .
, , CTF . — .
, , . , ? :)
, , Python. , .
, DEF CON , Python + C ( , ). C, Python , .
, , , .
, , CTF, — Zero Knowledge Proofs of Knowledge (ZKPoK), . , , - , . ZKPoK : - , . .
.
. . . — , .
, , . , , .
— . , . , .
.
. , , , , , . , 4 : A, B, C, D. A B, C D.
:
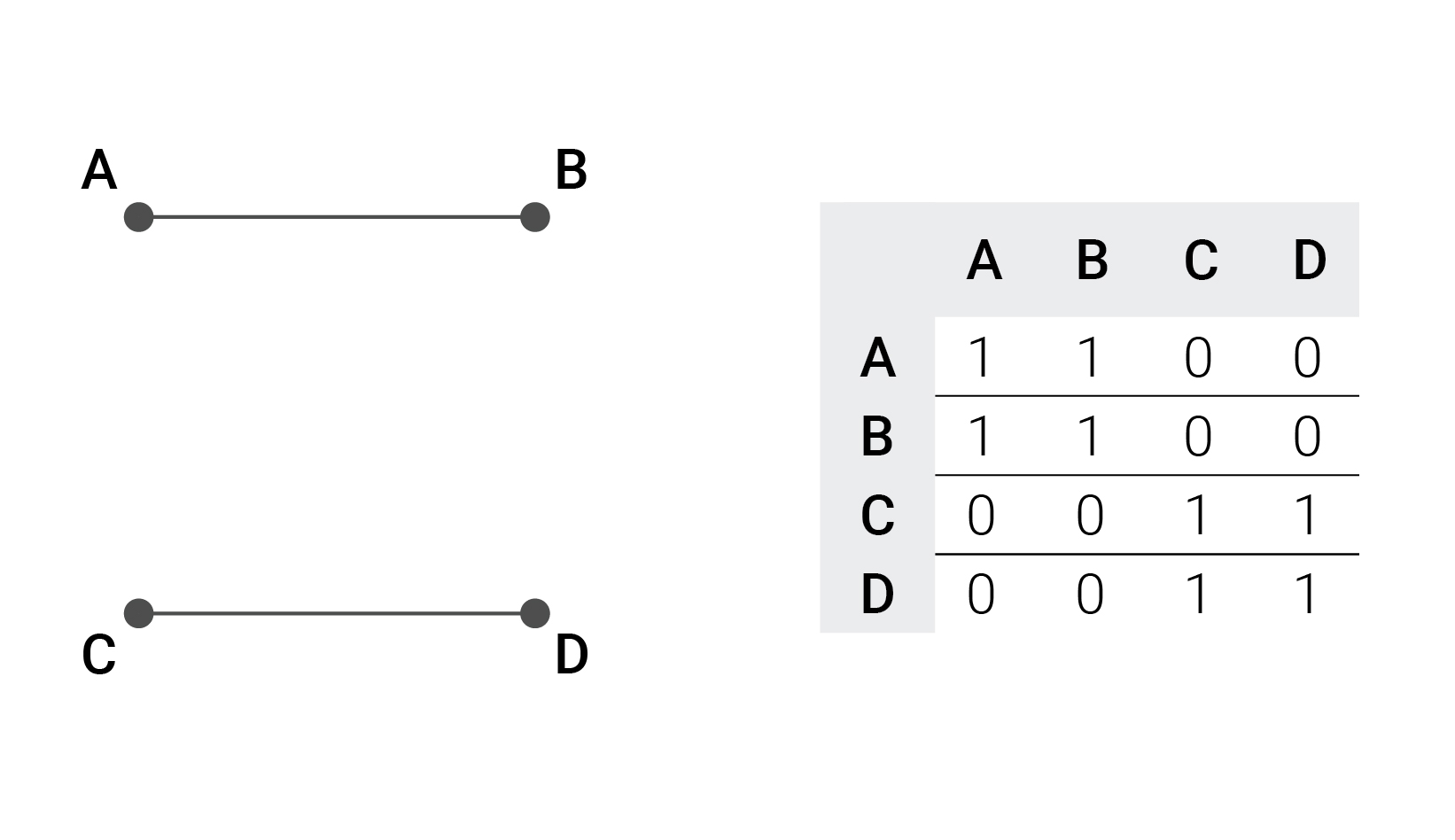
, , .
, , : , ABCD → BADC. (): B→A→D→C→B.
. . . , — . :
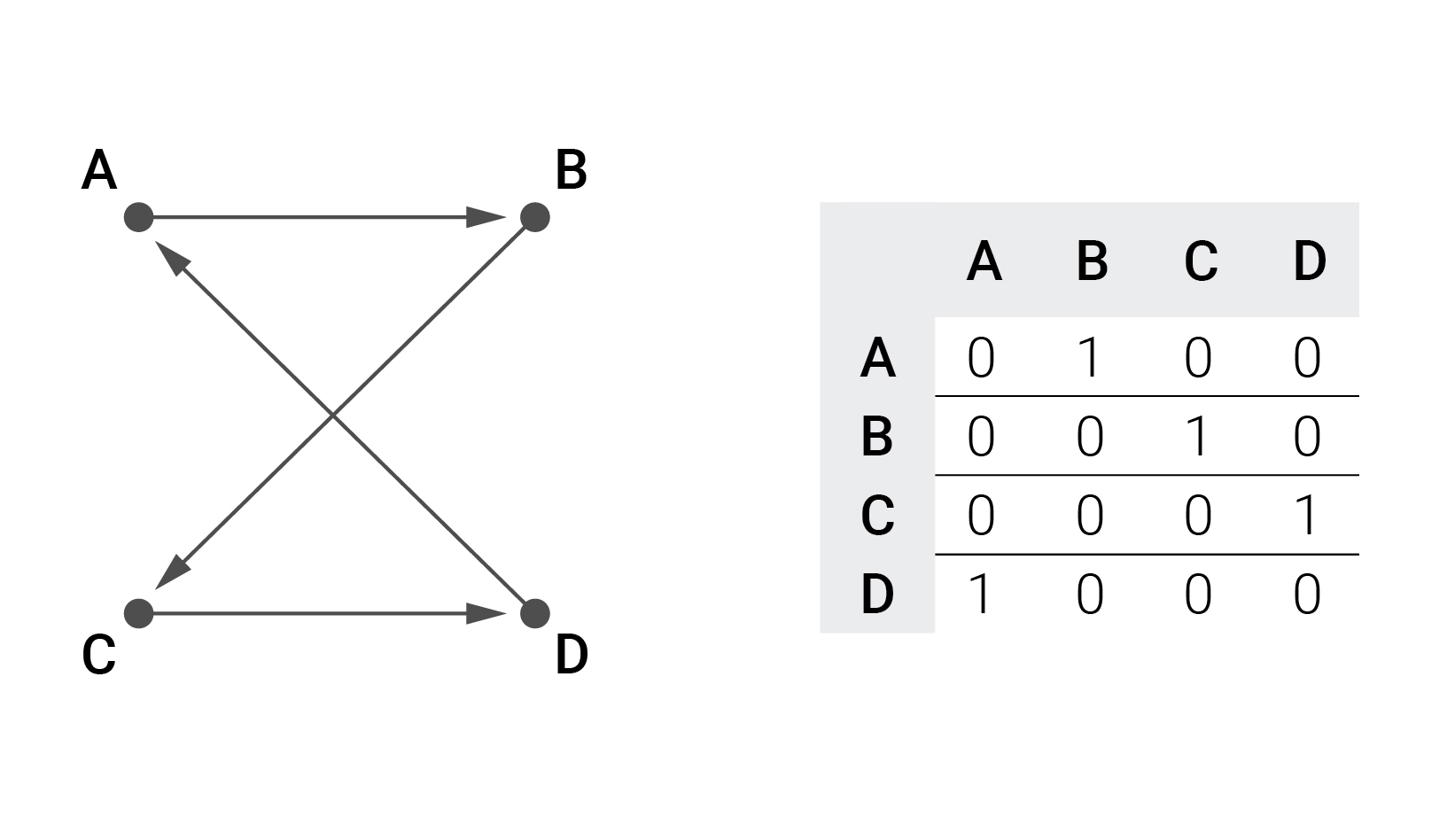
, . .
, . , , .
— :
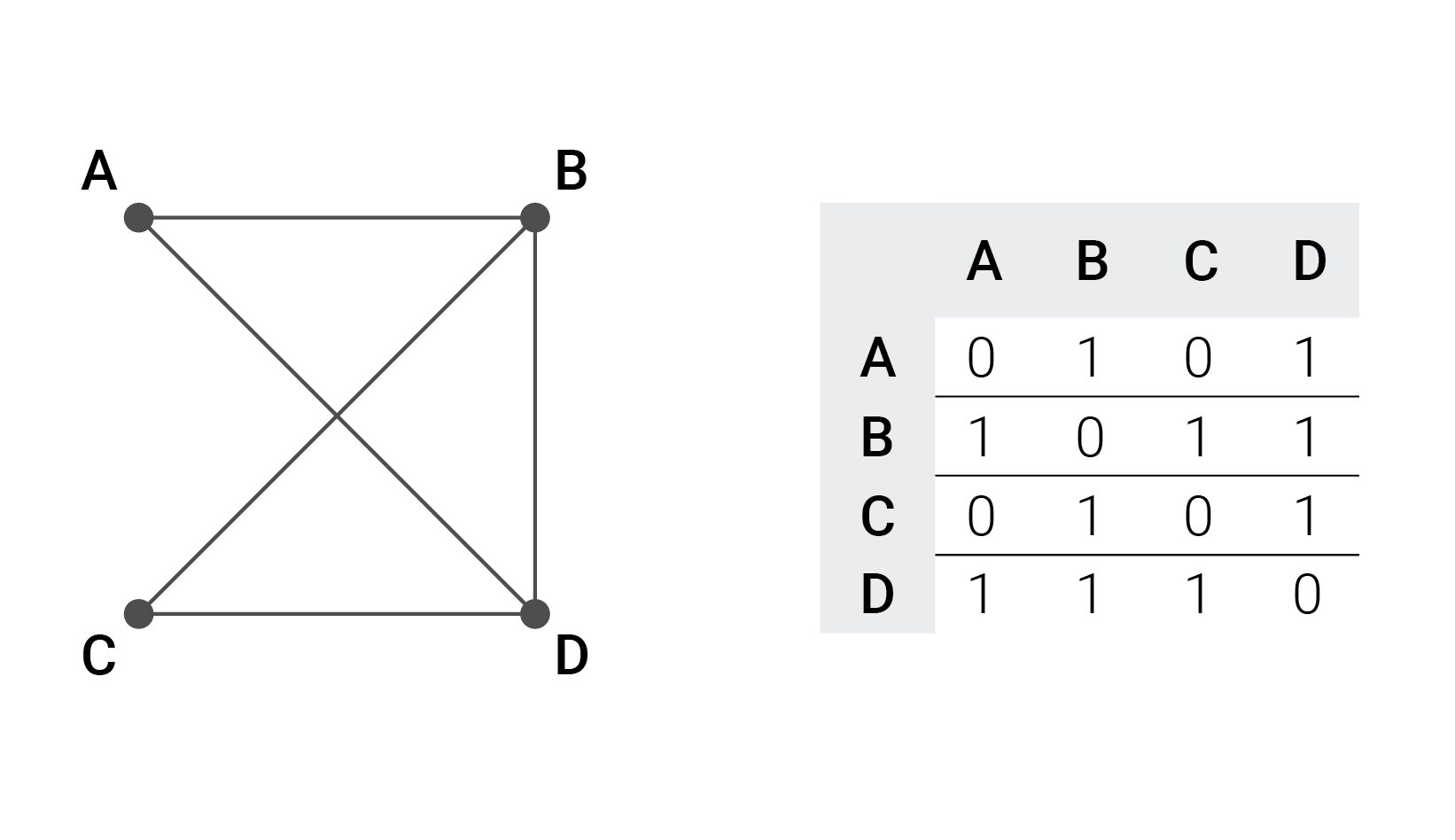
, (x, y) (y, x), B D.
.
:
- - , . ;
- , , .
, , (Prover), (Verifier).
0. . , : A→B→C→D→A. , , (. . ) . ( ) .
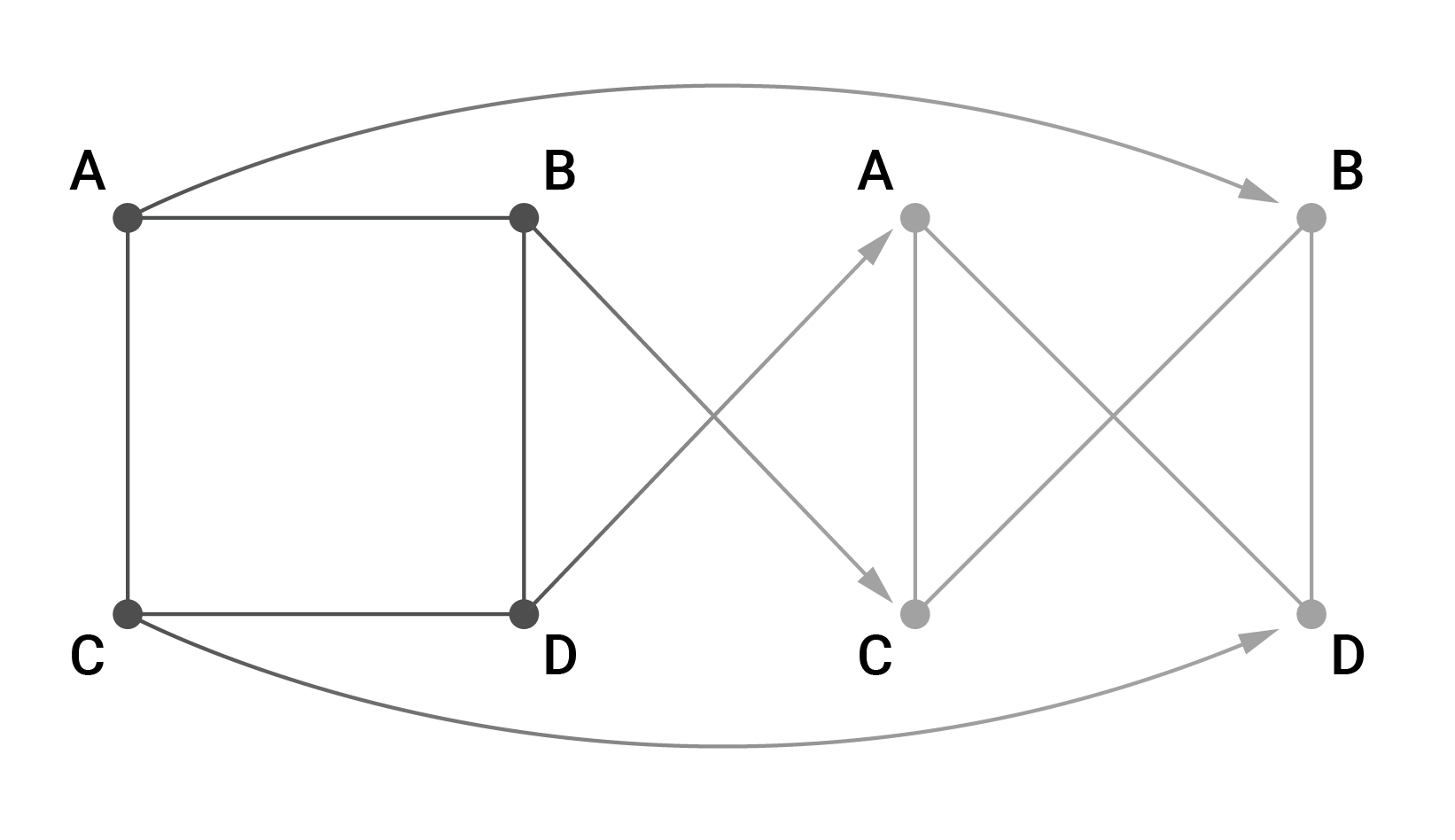
, . — .
1. . , (commitment). , , : , — , . , , .
:
- . ;
- . , . : .
2. . , (challenge) . , ( ) ( ) .
, , — .
3. . , , , , . , , , .
, , . , , .
. , . , : , , , . , . , - ( , ).
, , , 50- , , . , . . , . 25%, — 12,5% . . , .
.
P.S. Zero Knowledge, - Zero Knowledge Proofs: An illustrated primer. .
. « » = «», « » = «», « » = « ».
:
, , . , , , . :
- ;
- ;
- 16- RANDOMR, ;
- RSA- .
RANDOMR , .
, : , DoS- . PKCS#1 v1.5. , , 3 (Bleichenbacher's e=3 signature attack). , 3 (, SAFE_VERSION macro ):
uint8_t* badPKCSUnpadHash(uint8_t* pDecryptedSignature, uint32_t dsSize){
uint32_t i;
if (dsSize<MIN_PKCS_SIG_SIZE) return NULL;
if ((pDecryptedSignature[0]!=0)||(pDecryptedSignature[1]!=1))return NULL;
i=2;
while ((i<dsSize) && (pDecryptedSignature[i]==0xff)) i=i+1;
if (i==2 || i>=dsSize) return NULL;
if (pDecryptedSignature[i]!=0) return NULL;
i=i+1;
if ((i>=dsSize)||((dsSize-i)<SHA256_SIZE)) return NULL;
#ifdef SAFE_VERSION
//Check that there are no bytes left, apart from hash itself
//(We presume that the caller did not truncate the signature afte exponentiation
// and the dsSize is the equal to modulus size in bytes
if ((dsSize-i)!=SHA256_SIZE) return NULL;
#endif
return pDecryptedSignature+i;
}30 :
- ;
- , ;
- , .
, .
. , , . , , .
:
, , .
— Python + C. C, 95% . Python . . (, void_p ctypes. 64- 32 ).
Python :
verifier=Verifier(4,4,7):
- .
- .
- .
.
. , , , : .
, 256. :
- -, , 2 ( , ). , 5 , .
- -, , .
. , , - . . .
, , 64, . — .
, — .
. , 3 , :
- , "" CRC32;
- , SHA-256;
- , AES-128 CBC.
, . : CRC32, SHA-256, AES. , CRC32 AES, CRC32.
, :
- ( ).
- .
- , 1. proof_count.
- ( proof_count).
- , .
- , , .
- 3.
. (, ). . (simulation mode), . . . , , , . , . , ,
. .
CRC32 SHA-256 , . , (uint16_t), , 8 . , , -. :
. , , . , , . , , .
AES, : . , , . :
. .
, , AES, ( , , ). , SHA-256, ( ), - , .
CRC32, , , . CRC32 . Meet-in-the-Middle (« »), .
: , . . MitM , .. .
Meet-in-the-Middle , CRC32. ,
,
, 6 ( ). CRC32 :
- .
- , ( — , — ).
- .
, 6 :
:
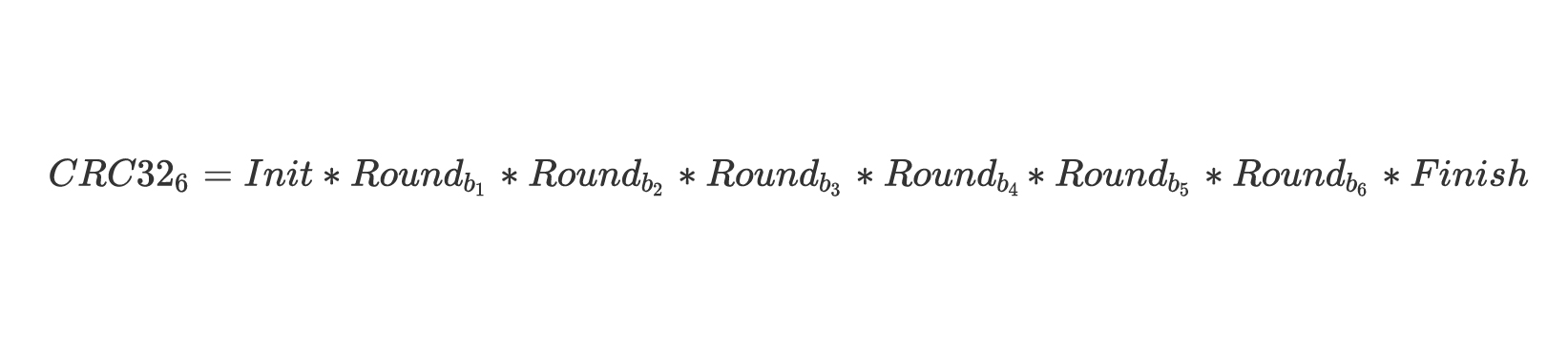
:
CRC32 . , , :
:
- -, .
- . , -. , . .
- : , , , .
: « , , , — , , ». — , . , :
, HASHES — , , , . , 6 :
,
.
4 . . , , — (PRNG ).
C rand, - . Legendre PRF, .
, , , - . , . , ( 0) .
- , , , , . , ( — ) . . , . 50%, , .
. Python :
def LegendrePRNG(a,p):
if a==0:
a+=1
while True:
next_bit=pow(a,(p-1)//2,p)
if next_bit==1:
yield 1
else:
yield 0
a=(a+1)%p
if a==0:
a+=132- , Meet-in-the-Middle. , , . , 32- , 32 . , — big-endian little-endian, — .
, . Legendre PRNG. 32 . , (, ).
, . , . , , . , — . , , .
, , . , . , .
, :
- Bleichenbacher’s e=3.
- .
- .
- CRC32.
- .
, .
, , , . - Linux Usermode Kernel CryptoAPI .
, : . SIMD, . , , : . .
, . , : . — . , . . , .
, . , , , :
- .
- , , .
- - .
- .
:
(, ) .
, . .
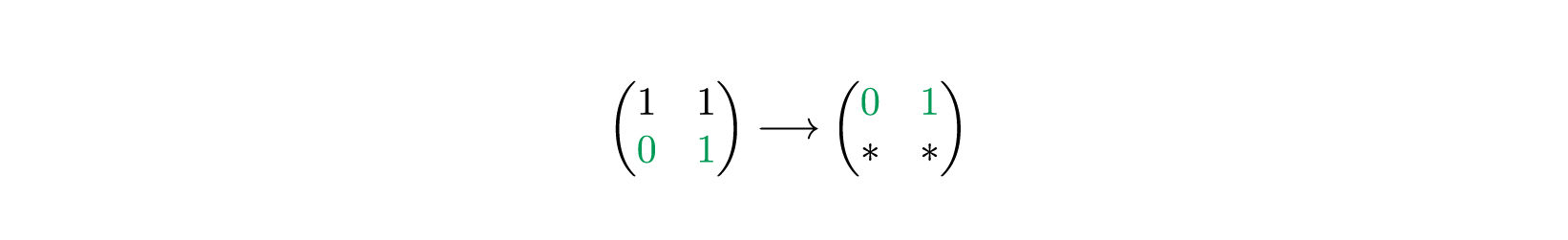
. .
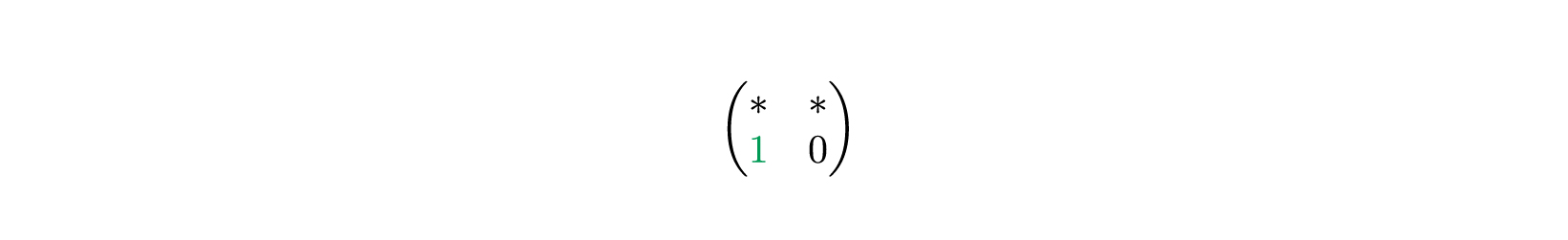
, .
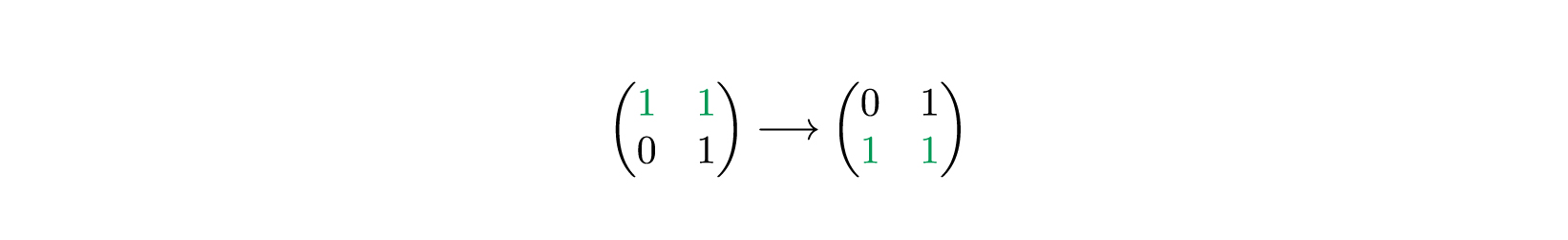
.
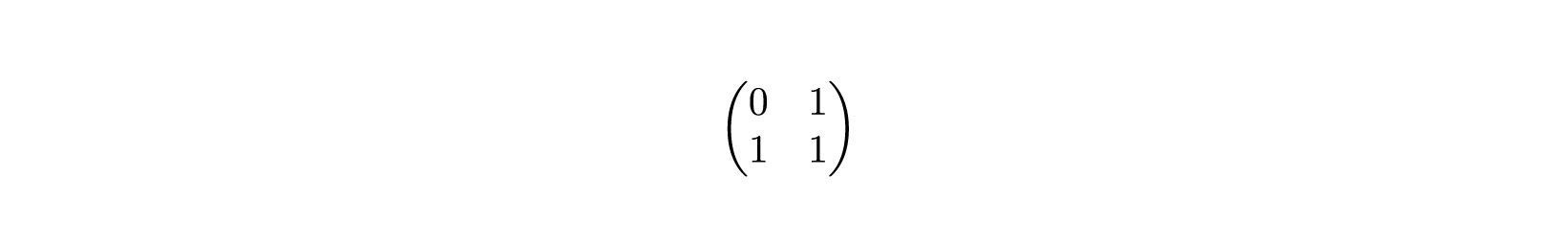
, , , - . , memcpy , SIMD, memcpy . .
- . Zero Knowledge , Python, PEM. , , , .
, .
24 , , . CryptoAPI: AF_ALG, .
, - . .
, , .
, , . , pwn :)
, :
- -, C , . ASAN (Address Sanitizer), .
- -, , , . , . Libfuzzer , .
: . /dev/urandom randrand, ( Legendre PRF, ) srand(0). , . - AES- .
, . , .
, , . , , — : , , .
Legendre PRNG . , . , .
Proof of Knowledge, . , , . , :
- . , . - , SLA ( ).
- , , . . . - , SLA.
- . . , , , . , , . SLA.
(Bushwhackers) SLA 65%, . , scoreboard, .
, , . .
, , . , , . , .
, https://github.com/bi-zone/CTFZone-2020-Finals-LittleKnowledge. , . , ( ) . . , , . , - CTF.
, , !