We continue to acquaint you with the consequences of the activity of cybercriminals, because as Praemonitus, praemunitus said in ancient times, forewarned is forearmed.
Only by knowing what the enemy looks like can you prepare for his meeting.
Today we would like to talk about large DDoS (distributed denial-of-service) attacks in the first half of 2020.

On June 21, Cloudflare was subjected to a high-volume DDoS attack, which reached 754 million packets per second. The attack lasted four days, starting on June 18th and up to June 21st: attacking traffic was sent from over 316,000 IP addresses to a single Cloudflare IP address, which was mainly used for websites on the free plan.
During these four days, the attack used a combination of three TCP attack vectors: SYN floods, ACK floods, and SYN-ACK floods. The attack continued for several hours at rates exceeding 400-600 Mpps and peaked several times over 700 Mpps with a maximum peak of 754 Mpps. Attackers tried to suppress routers and devices in the data center with high packet rates.
Cloudflare said they were able to mitigate the attack, although some reports suggest it was only a red herring for a massive data theft or a test before the attack a few days later.

Cloudflare — , CDN, DDoS-, DNS. Cloudflare .
: (2009 .–)
: 287 USD (2019 .)
-: -, ,
: 2009 ., -, ,
: , ,
Also on June 21, Akamai suppressed the largest PPS (packet per second) DDoS attack previously recorded on the platform. The attack generated 809 Mpps (millions of packets per second), targeting a large bank from Europe. According to company representatives, this is a new industry record for PPS targeted attacks.
A feature of this attack was the explosive growth of source IP addresses. This suggests that the traffic was highly distributed, besides, in addition to the volume of addresses, the peculiarity was that almost all traffic came from IPs who did not participate in attacks until 2020, which signals the emergence of a new botnet.
Unusually, 96.2% of original IP addresses were discovered for the first time (or at least not tracked as part of attacks in recent history). The team observed several different attack vectors originating from 3.8% of the remaining original IP addresses, matching one attack vector seen in this attack in concert with others. In this case, most of the original IP addresses were identified in the major ISPs, which means the compromised computers of the end users.
The June 21 attack differed not only in its size, but also in the speed with which it reached its peak. The attack skyrocketed from normal traffic to 418 Gbps almost instantaneously, reaching its peak size of 809 Mpps in about two minutes. In total, the attack lasted almost 10 minutes.

Akamai Technologies — -, . 240 000 .
-: , ,
: 2,894 USD (2019 .)
: 1998 .
: (1 . 2013 .–)
: , , ,
Earlier, Amazon AWS Shield repaid a BPS attack with a capacity of 2.3 TB / sec. The attack on Akamai 418 Gbps does not look so grand from this perspective, but do not forget that these are different types of attacks, before that the record traffic volume of PPs attacks was only 293.1 million packets per second, which is 2, 7 times less than the Akamai incident.
The AWS Shield Threat Landscape Report did not reveal which AWS client the attack was targeting, but mentions that the DDoS was organized using compromised CLDAP web servers. The repulse of the attack lasted three days until it died out.

Amazon — , - .
:
: 5 1994 ., , ,
: ( 1996 .–)
-: , ,
: 280,522 USD (2019 .)
2020 is being held under the banner of combating the COVID-2019 coronavirus epidemic, which affected both the way we work and do business, communications between users, and the goals and methods of attacks by cybercriminals.
Due to the increased activity in the use of delivery services, educational platforms, game servers, means of remote communication, an increased interest in information resources of a medical nature, the emphasis in attacks on the network has also changed.
In particular, in March there was an attempt to block the work of the US Department of Health and Human Services (HHS), some online thugs, as the representatives of the Ministry colorfully put it, the benefit of HHS, in preparation for responding to the epidemic, established additional protection and added capacity to its resources to prevent interruptions in work.
Also in March, the Assistance Publique - Hôpitaux de Paris (APHP) network of hospitals in Paris, which consists of 44 institutions, came under attack, some systems were unavailable for several hours, although this caused inconvenience in the work of staff, in particular, remote employees , but in this case the attack was repulsed.
Less fortunate food delivery service Takeaway.com (Lieferando.de), criminals attacked them at a time when the number of orders increased sharply, but they could only accept orders, and a distributed denial of service attack on the site interfered with processing. For stopping the siege, the criminals extorted 2 bitcoins. Jitse Groen, founder and CEO of Takeaway, then tweeted a post with a screenshot of their message.
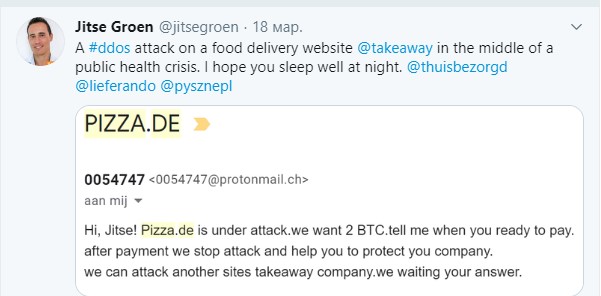
The cybercriminals were not paid the ransom, but due to the size of the delivery network, which is more than fifteen thousand restaurants in Germany, the consequences of the DDoS attack were significant both for customers and restaurant owners and for the service itself. Lieferando also had to compensate users for paid but unfulfilled orders.
The same situation was with the Dutch delivery service Thuisbezorgd.
Ddosili in March, the online platform Mebis in Germany, which targets the online education of Bavarian schoolchildren.
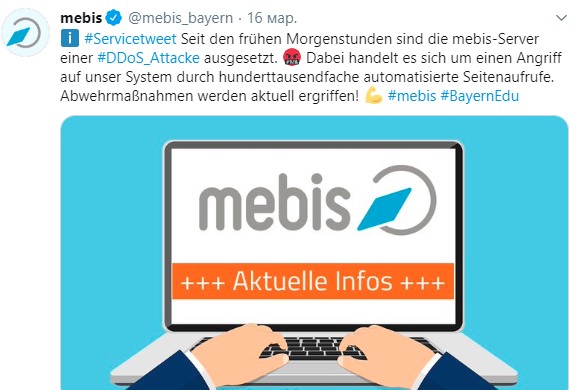
On the very first day of switching to distance learning, hundreds of thousands of automatic page views put the site down for several hours.
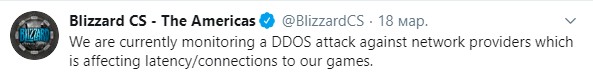
Problems were also observed on gaming platforms, in particular, Blizzard and the multiplayer game EVE Online, the latter was especially unlucky, it was under the onslaught of a DDOS attack for nine days.
In January, Wargaming servers were subjected to a prolonged DDoS attack. World of Tanks, World of Warships and World of Warplanes players had problems logging in and out of the server.
They also attacked the servers of government agencies in Greece, the websites of ministries, emergency services and even the country's police were out of order.

The FBI reported that a US voter registration site was attacked in February. The hackers used a pseudo-random attack on subdomains (PRSD) technique, queries occurring for at least one month at intervals of approximately two hours, with query rates peaking at around 200,000 DNS queries.
The list of attacks is far from complete, but not all of them deserve mention, and we are well aware that in some cases, under the guise of DDoS, companies may hide their incompetence in supporting an increased number of users, without foreseeing additional capacities in equipment and their services.
Advertising
Servers with free DDoS protection - that's about us! All servers out of the box are protected from DDoS attacks.
