- Availability;
- Safety;
- Automation.
The research results are shown below. Since 2019, the functionality of the Cisco Catalyst 9800 Series Controllers has been significantly improved - these points are also reflected in this article.
You can read about other benefits of Wi-Fi 6 technology, examples of implementation and applications here .
Solution overview
Cisco Catalyst 9800 Series Wi-Fi 6 Controllers
The Cisco Catalyst 9800 Series Wireless Controller series, based on the IOS-XE operating system (which is also used for Cisco switches and routers), is available in a variety of options.

The older model 9800-80 controller supports wireless bandwidth up to 80 Gbps. One 9800-80 controller supports up to 6,000 access points and up to 64,000 wireless clients.
The mid-range model, the 9800-40 controller, supports bandwidth up to 40 Gbps, up to 2,000 access points, and up to 32,000 wireless clients.
In addition to these models, the 9800-CL Wireless Controller (CL stands for Cloud) was also included in the competitive analysis. The 9800-CL runs in virtualized environments on VMWare ESXI and KVM hypervisors, and its performance depends on the dedicated hardware resources for the controller virtual machine. In its maximum configuration, the Cisco 9800-CL controller, like the older 9800-80 model, supports scalability up to 6,000 access points and up to 64,000 wireless clients.
In the study with controllers, we used a Cisco Aironet AP 4800 series that supports 2.4 and 5 GHz with the ability to dynamically switch to dual 5-GHz mode.
Test stand
As part of the testing, a stand was assembled consisting of two Cisco Catalyst 9800-CL wireless controllers operating in a cluster and Cisco Aironet AP 4800 series access points.
Dell and Apple laptops and an Apple iPhone were used as client devices.
Accessibility testing
Accessibility is defined as the ability of users to access and use a system or service. High availability means continuous access to a system or service, independent of certain events.
High availability has been tested in four scenarios, the first three scenarios are predictable or scheduled events that can occur during business hours or after business hours. The fifth scenario is a classic glitch, which is an unpredictable event.
Description of scenarios:
- Bug fixing - micro-update of the system (bugfix or security patch), which allows you to fix this or that error or vulnerability without completely updating the system software;
- Functional update - adding or expanding the current functionality of the system by installing functional updates;
- – ;
- – ;
- – .
Often, in many competitive solutions, patching requires a complete update of the wireless controller system software, which can result in unplanned downtime. In the case of a Cisco solution, patching is performed without stopping the product. Patches can be applied to any of the components while the wireless infrastructure continues to operate.
The procedure itself is quite simple. The patch file is copied to the boot folder on one of the Cisco wireless controllers, and then the operation is confirmed through the GUI or command line. In addition, through the graphical interface or the command line, you can still undo and remove the patch, also without interrupting the system.
Functional update
Functional software updates are applied to activate new features. One such enhancement is an update to the application signature database. This package was installed in Cisco controllers as a test. As with fixes, feature updates are applied, installed, or uninstalled without downtime or disruption to the system.
Full update
At the moment, a complete update of the controller software image is performed in the same way as a functional one, that is, without downtime. However, this feature is only available in a clustered configuration when there are more than one controller. A full update is performed sequentially: first on one controller, then on the second.
Adding a new access point model
Connecting new access points that were not previously operated with the used controller software image to a wireless network is a fairly frequent operation, especially in large networks (airports, hotels, production facilities). Quite often in the solutions of competitors, this operation requires updating the system software or rebooting the controllers.
When connecting new Wi-Fi 6 APs to a Cisco Catalyst 9800 Series Controller Cluster, these issues are not observed. Connecting new points to the controller is carried out without updating the controller software, and this process does not require a reboot, thus not affecting the wireless network in any way.
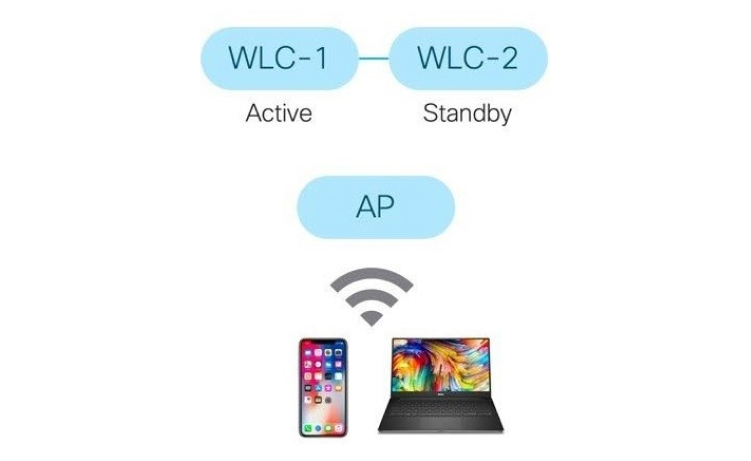
Controller failure
In the test environment, two Wi-Fi 6 controllers (Active / StandBy) are used and the access point has a direct connection to both controllers.
One wireless controller is active, and the other, respectively, standby. If the active controller fails, the backup controller takes over and its status changes to active. This procedure occurs without interruption for the access point and Wi-Fi for clients.
Safety
This section discusses security aspects, which are extremely important in wireless networks. The safety of the solution is assessed according to the following characteristics:
- Application recognition;
- Tracking traffic flow (Flow tracking);
- Analysis of encrypted traffic;
- Intrusion detection and prevention;
- Authentication tools;
- Client device protection tools.
Application recognition
Among the various products in the enterprise and industrial Wi-Fi market, there are differences in how well the products identify traffic across applications. Products from different manufacturers can identify a different number of applications. At the same time, many of the applications that are indicated by competitive solutions as possible for identification are, in fact, websites, and not unique applications.
There is another interesting feature of application recognition: solutions vary greatly in identification accuracy.
Taking into account all the tests carried out, we can responsibly state that the Cisco Wi-Fi-6 solution performs application recognition very accurately: Jabber, Netflix, Dropbox, YouTube and other popular applications, as well as web services, were accurately identified. Also, Cisco solutions can dive deeper into data packets using DPI (Deep Packet Inspection).
Tracking traffic flows
Another test was performed to find out if the system can accurately track and report data streams (such as large file movements). To test this, a 6.5 megabyte file was sent over the network using File Transfer Protocol (FTP).
Cisco's solution was up to the task and was able to track this traffic thanks to NetFlow and its hardware capabilities. Traffic was detected and identified immediately with the exact amount of data transferred.
Analysis of encrypted traffic
User data traffic is increasingly being encrypted. This is done in order to protect it from being tracked or intercepted by intruders. But at the same time, hackers are increasingly using encryption to hide their malware and conduct other dubious operations such as Man-in-the-Middle (MiTM) or keylogging attacks.
Most enterprises inspect some of the encrypted traffic by first decrypting it with firewalls or intrusion prevention systems. But this process is time consuming and does not benefit the overall performance of the network. Moreover, once decrypted, this data becomes vulnerable to prying eyes.
Cisco Catalyst 9800 series controllers successfully solve the problem of analyzing encrypted traffic by other means. The solution is called Encrypted Traffic Analytics (ETA). ETA is a technology that currently has no analogues in competitive solutions and which detects malware in encrypted traffic without the need to decrypt it. ETA is a basic IOS-XE feature that includes Enhanced NetFlow and uses advanced behavioral algorithms to detect malicious traffic patterns lurking in encrypted traffic.
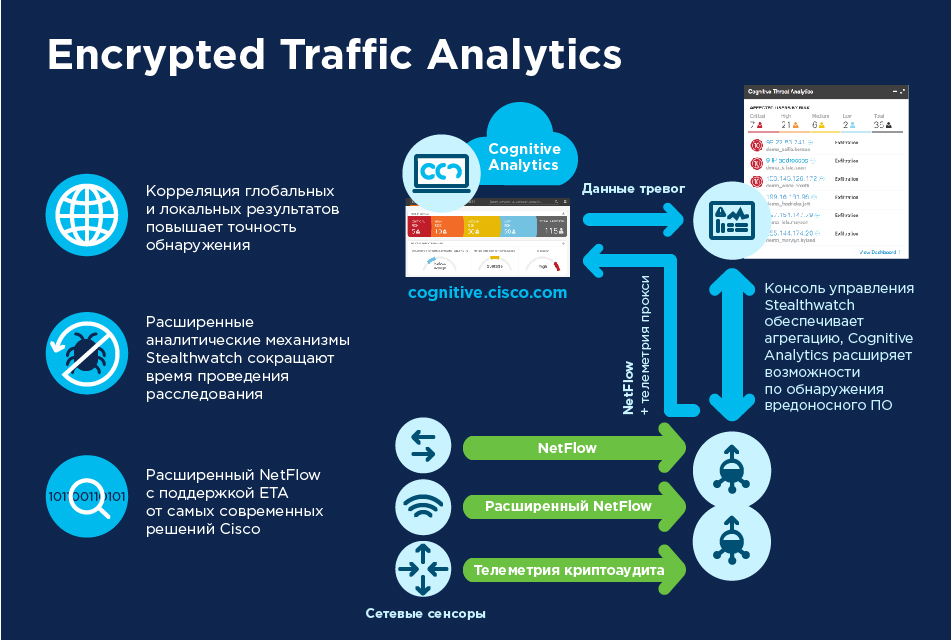
ETA does not decrypt messages, but collects metadata profiles of encrypted traffic streams - packet size, time intervals between packets, and more. The metadata is then exported in NetFlow v9 records to Cisco Stealthwatch.
The key function of Stealthwatch is continuous traffic monitoring and creation of baseline indicators of regular network activity. Using the encrypted stream metadata sent to it by ETA, Stealthwatch applies multi-layered machine learning to identify traffic behavioral anomalies that could indicate suspicious events.
Last year, Cisco hired Miercom to independently evaluate the Cisco Encrypted Traffic Analytics solution. In this assessment, Miercom separately dispatched known and unknown threats (viruses, Trojans, ransomware) in encrypted and unencrypted traffic across large ETA and non-ETA networks to identify threats.
For testing, malicious code was launched on both networks. In both cases, suspicious activity was gradually detected. The ETA network initially detected threats 36% faster than the non-ETA network. At the same time, in the course of work, the productivity of detection in the ETA network began to increase. As a result, after several hours of operation on the ETA network, two-thirds of the active threats were successfully detected, which is double the same indicator in the non-ETA network.
ETA functionality is well integrated with Stealthwatch. Threats are ranked by severity, displayed with detailed information, and options for corrective action once confirmed. Conclusion - ETA works!
Intrusion detection and prevention
Cisco now has another powerful security tool, the Cisco Advanced Wireless Intrusion Prevention System (aWIPS), a threat detection and prevention engine for wireless networks. AWIPS works at the controller, access point, and management software of the Cisco DNA Center. The Threat Detection, Alert and Prevention process combines network traffic analysis, network device and network topology information, signature-based techniques, and anomaly detection to ultimately deliver high accuracy and prevention of wireless threats.
Full integration of aWIPS into your network infrastructure allows you to continuously monitor wireless traffic on both wired and wireless networks and use it to automatically analyze potential attacks from many sources to identify and prevent potential attacks as comprehensively as possible.
Authentication tools
At the moment, in addition to classic authentication means, WPA3 support is available in Cisco Catalyst 9800 series solutions. WPA3 is the latest version of WPA and is a set of protocols and technologies that provide authentication and encryption for Wi-Fi networks.
WPA3 uses Simultaneous Authentication of Equals (SAE) to provide the most secure user protection against brute force attacks by third parties. When a client connects to an access point, it performs an SAE exchange. If successful, each of them will create a cryptographically strong key from which the session key will be obtained, and then they go into the confirmation state. Thereafter, the client and the access point can enter acknowledgment states each time a session key needs to be generated. The method uses forward secrecy, in which an attacker can crack one key, but not all other keys.
That is, the SAE is designed in such a way that an attacker intercepting traffic has only one attempt to guess the password before the intercepted data becomes useless. To organize a long-term password guessing, you will need physical access to the access point.
Client device protection
The primary customer protection for the Cisco Catalyst 9800 Series wireless solutions today is the Cisco Umbrella WLAN, a cloud-based, DNS-based network security service that automatically detects both known and emerging threats.
The Cisco Umbrella WLAN provides client devices with a secure connection to the Internet. This is achieved through content filtering, that is, by blocking access to resources on the Internet in accordance with enterprise policy. Thus, client devices on the Internet are protected from malware, ransomware, and phishing. Policy enforcement is based on 60 continuously updated content categories.
Automation
Modern wireless networks are much more flexible and complex, so traditional methods of configuring and retrieving information from wireless controllers are not enough. Network administrators and security professionals need automation and analytics tools, which prompts wireless network vendors to offer such tools.
To address these challenges, the Cisco Catalyst 9800 Series Wireless Controllers support the RESTCONF / NETCONF network configuration protocol with Yet Another Next Generation (YANG) data modeling language along with the traditional API.
NETCONF is an XML-based protocol that applications can use to query information and change the configuration of network devices such as wireless controllers.
In addition to these methods, the Cisco Catalyst 9800 Series controllers provide the ability to acquire, fetch, and analyze flow data using NetFlow and sFlow.
For security and traffic modeling, the ability to track specific flows is a valuable tool. To solve this problem, the sFlow protocol was implemented, which allows you to capture two packets out of every hundred. However, sometimes this may not be enough for analysis and adequate study and assessment of the flow. Therefore, the alternative is NetFlow, implemented by Cisco, which allows 100% collection and export of all packets in a specified stream for further analysis.
Another feature, although only available in the hardware implementation of the controllers, that automates the wireless network in the Cisco Catalyst 9800 series controllers, is built-in Python support as an add-on for using scripts directly on the wireless controller itself.
Finally, the proven SNMP v1, v2, and v3 is supported for monitoring and management operations in the Cisco Catalyst 9800 Series Controllers.
Thus, in terms of automation, the Cisco Catalyst 9800 Series solutions fully meet today's business needs, offering both new and unique. and time-tested tools for automated operations and analytics in wireless networks of any size and complexity.
Conclusion
With solutions based on the Cisco Catalyst 9800 Series controllers, Cisco has performed well in the high availability, security, and automation categories.
The solution fully meets all high availability requirements such as failover in less than a second during unplanned events and zero downtime for scheduled events.
The Cisco Catalyst 9800 Series controllers provide comprehensive security that provides deep packet inspection to recognize and manage applications, full visibility into data streams and identification of threats hidden in encrypted traffic, and advanced authentication and client protection mechanisms.
For operations automation and analytics, the Cisco Catalyst 9800 Series is powerful using popular standard models: YANG, NETCONF, RESTCONF, traditional APIs, and embedded Python scripts.
Thus, Cisco once again confirms its status as the world's leading manufacturer of network solutions, keeping up with the times and taking into account all the challenges of modern business.
For more information on the Catalyst family of switches, visit the Cisco website .