
Our today's story is about several major data leaks and financial thefts in the history of the World Wide Web.
The tragic story of a young talent

The name of the prodigy Jonathan Joseph James is associated with one of the darkest chapters in the history of hacking. A fifteen-year-old teenager hacked into the networks of his own school, the telecommunications company Bell South, bypassed the security of NASA servers and stole a lot of valuable information, including the source codes of the ISS, also in the list of James's crimes, penetration into the servers of the Ministry of Defense of his home country.
The young man himself has repeatedly spoken out that he does not trust the government and that users themselves are to blame for the vulnerabilities of their computers, in particular, James stated that ignoring software updates is a direct path to being hacked one day. Someone had already hacked outdated programs, so he believed. The hacker treated the developments of large ministries and companies with a share of contempt, believing that they were overvalued.
The damage caused by Jonathan's attacks was estimated in millions of dollars, and his story ended tragically, in 2008, at the age of 24, a hacker committed suicide.
Many linked it to the massive 2007 hacker attacks, including the theft of credit card information from millions of TJX customers, but James denied this. Because of those events and the sad ending, many believe that in fact the hacker could have been killed.
The collapse of the cryptocurrency exchange

Not so long ago, the rapid jump in the value of bitcoin worried netizens.
Albeit belatedly, but I would like to recall the history of the bankrupt Mount Gox exchange, which went bankrupt as a result of several hacker attacks. As of August 2013, about 47% of all transactions in the Bitcoin network were made through this platform, and the trading volume in dollars exceeded 80 percent of the global turnover of cryptocurrencies; in January 2014, the service ranked third in terms of trading volume in the market, which speaks of its value in crypto trading at that time.
In fact, it was not only about hacking, Mount Gox had neither version control, which makes it difficult to track code vulnerabilities, nor an accounting system that allows it to track financial transactions, which is an example of an "open door" here. The attack on the vulnerability discovered in 2014 was only a matter of time. As a result of the actions of the attackers, which lasted for about 3 years, the exchange lost over half a billion dollars.
Insane financial and reputational costs completely destroyed Mount Gox, and subsequent transactions brought down the Bitcoin price. As a result, due to the actions of hackers, a huge number of people lost their savings stored in virtual currency. As Mark Karpeles (CEO of Mt.Gox) later stated in a Tokyo court, "technical problems in the platform opened access for the illegal seizure of funds from our clients by hackers."
The identity of all the criminals has not been identified, but in 2018 Alexander Vinnik was arrested and charged with laundering money obtained by criminal means in the amount of "from four to nine billion dollars." It is in such amounts (depending on the current exchange rate) that 630 thousand bitcoins, lost as a result of the collapse of Mt.Gox, are estimated.
Hack Adobe Systems
In 2013, the largest hacker theft of user data took place.

Developer Adobe Systems reported that the criminals stole the source code of the software and the data of nearly 150 million people.
The delicacy of the situation was created by the company itself, the first signs of damage inside the system were discovered 2 weeks before the hack, but Adobe experts considered them not related to hackers. The company later released smoothed loss figures, citing a lack of hard evidence. As a result, hackers stole the data of almost 3 million bank cards of users from 150 million accounts, some fears were caused by the theft of the code, possessing the source code, the attackers could easily reproduce expensive software.
Everything turned out to be a slight fright, for some unknown reason the hackers did not use the information they received. There are many ambiguities and understatements in history, information that differs tenfold depending on the time and source of information.
Adobe got off with public censure and the cost of additional protection, otherwise, if the criminals decided to use the obtained data, the losses of the company and users would be colossal.
Hackers are moralists
The Impact Team destroyed the Avid Life Media (ALM) sites.
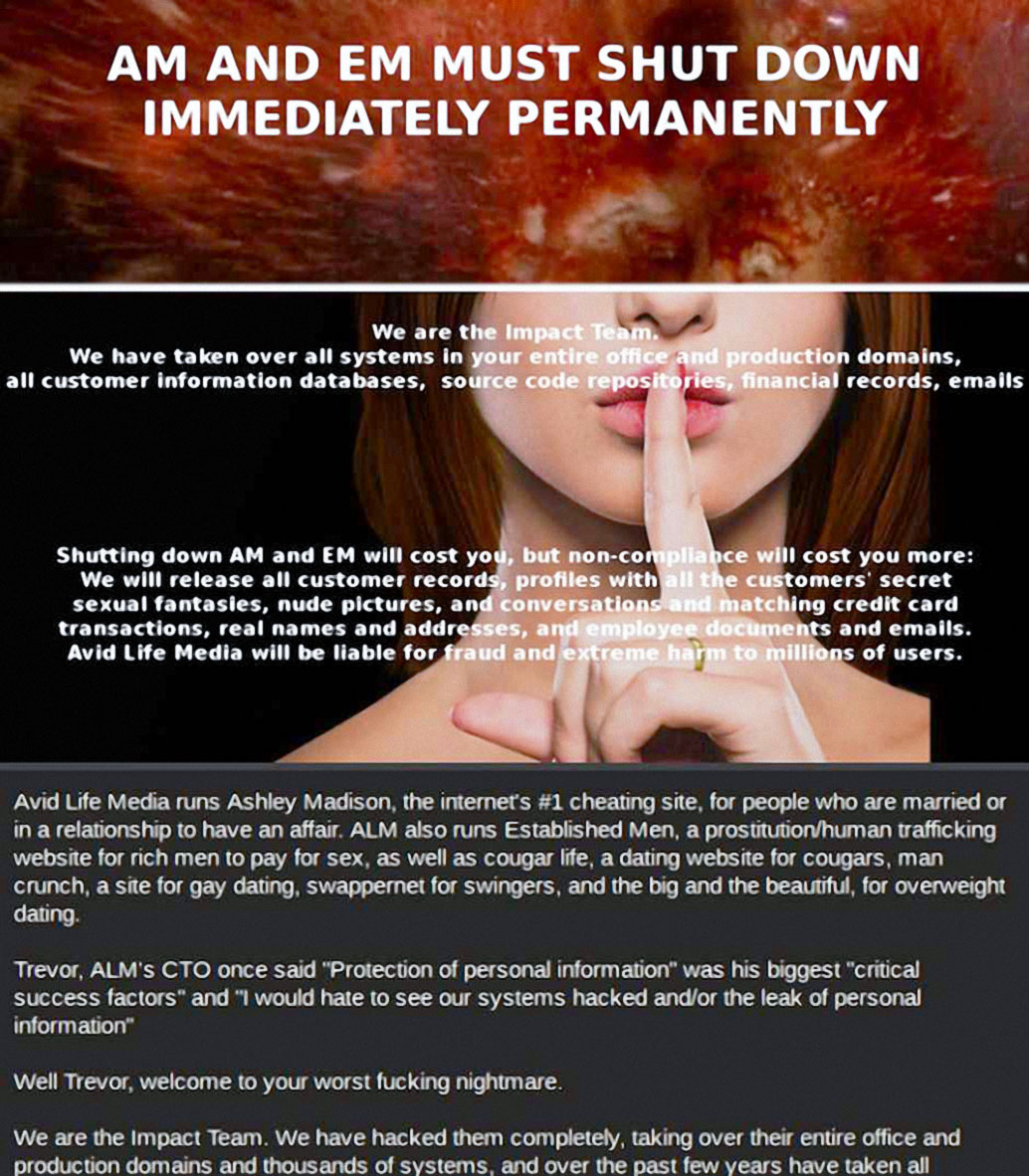
In most cases, cybercriminals steal money or personal data of users for use or resale; the motives of The Impact Team were different. The most famous case of these hackers was the destruction of sites owned by Avid Life Media. The firm's three sites, including the Ashley Madison portal, were a meeting point for people interested in adultery.
The specific focus of the sites was already a subject of controversy, but the fact remains unchanged, the servers of Ashley Madison, Cougar Life and Established Men stored a huge amount of personal information of people who cheated on their soul mates. The situation is also interesting because ALM's management was also not averse to hacking competitors; in the correspondence between the CEO and CTO of the company, the hacking of their direct competitor Nerve was mentioned. Six months earlier, ALM wanted to partner with Nerve and buy out their website. The Impact Team demanded that the site owners completely cease their activities, otherwise all user data will be made publicly available.
Avid Life Media decided that the hackers were bluffing and ignored them. When the announced time, 30 days, expired, The Impact Team fulfilled the promised in full - the data of over 30 million users appeared on the network, containing their names, passwords, email addresses, external data, and correspondence history. This led to a flurry of divorce proceedings, high-profile scandals and even possibly ... several suicides.
It is difficult to say whether the motives of the hackers were pure, because they did not ask for money. In any case, such justice hardly cost human lives.
Seeing no boundaries in pursuit of UFOs
Gary McKinnon broke NASA, Department of Defense, US Navy and Air Force servers.

I would like to finish our story on a funny note, they say that "a bad head does not give rest to his hands", Gary McKinnon, one of the hackers who encroached on NASA, this saying fits in full. The reason why an attacker hacked into the security systems of almost a hundred computers with classified data is staggering, Gary is convinced that the US government and scientists are hiding information about aliens from citizens, as well as about alternative energy sources and other technologies that are useful for ordinary people, but not profitable for corporations. ...
In 2015, Gary McKinnon was interviewed by Richard D. Hall on RichPlanet TV.
He said that for several months he collected information from NASA servers while sitting at home and using a simple Windows computer and got access to files and folders containing information about the existence of a secret program of the state government on interplanetary flights and space exploration, anti-gravity technologies, free energy, and far not an exhaustive list of information.
McKinnon is a true master of his craft and a sincere dreamer, but was the chase for a UFO worth the trial? Due to the losses caused to the US government, Gary was forced to remain in the UK and live in fear of extradition. For a long time, he was under the personal patronage of Theresa May, who at that time was the British Home Secretary; she, by direct order, forbade it to be transferred to the US authorities. (By the way, who believes in the philanthropy of politicians? Maybe McKinnon really is a bearer of valuable information) Let's hope that the hacker will always be so lucky, because in America he faces a 70-year prison term.
Most likely, somewhere there are hackers who go about their business out of a desire to help someone or love for art, alas, such an activity is always a double-edged sword. Too often, the pursuit of justice or other people's secrets jeopardizes people's well-being. Most often, the victims are people who have nothing to do with hackers.
If you are interested in any of the topics raised in the article, write in the comments, perhaps we can reveal it in more detail in one of the following materials.
Follow the rules of network security and take care of yourself!
Advertising
Epic servers are secure VDS with protection against DDoS attacks, which is already included in the price of tariff plans. The maximum configuration is 128 CPU cores, 512 GB RAM, 4000 GB NVMe.
