
In the last article, we talked about Nemesida WAF Free , a free tool for protecting websites and APIs from hacker attacks, and in this article we decided to review the popular Wapiti vulnerability scanner .
Scanning a site for vulnerabilities is a necessary measure, which, together with an analysis of the source code, allows you to assess the level of its protection against threats of compromise. You can scan a web resource using specialized tools.
Nikto, W3af (written in Python 2.7, whose support has ended) or Arachni (no longer supported since February) are the most popular solutions presented in the free segment. Of course, there are others, for example, Wapiti, on which we decided to stop.
Wapiti works with the following types of vulnerabilities:
- file expansion (local and remote, fopen, readfile);
- Injections (PHP / JSP / ASP / SQL Injection and XPath Injection);
- XSS (Cross Site Scripting) (Reflected and Persistent);
- detection and execution of commands (eval (), system (), passtru ());
- CRLF injection (split HTTP responses, session fixation);
- XXE (XML ) ;
- SSRF ( );
- ( Nikto);
- .htaccess, ;
- , ( );
- Shellshock;
- ;
- HTTP, (PUT).
:
- HTTP, HTTPS SOCKS5;
- : Basic, Digest, Kerberos NTLM;
- (, , , URL-);
- URL;
- (: ifor, );
- URL- ( );
- URL- (: URL logout);
- cookie ( wapiti-getcookie);
- / SSL;
- URL JavaScript ( JS-);
- HTML5;
- crawler’a;
- ;
- HTTP- User-Agent.
:
- (HTML, XML, JSON, TXT);
- ( SQLite3);
- ;
- ;
- / .
Wapiti 2 :
Wapiti .
Wapiti sites.vulns.pentestit.ru ( ), (Injection, XSS, LFI/RFI) -.
. !
:
# wapiti -u <target> <options>, :
--scope —
URL scope, , , , .
-s -x — URL-. , URL- .
--skip — , . , - , .
--verify-ssl — .
Wapiti . , , , , -m . , . :
# wapiti -u http://sites.vulns.pentestit.ru/ -m sql,xss,xxe, SQL, XSS XXE . , . -m “xss: get, blindsql: post, xxe: post”. xss , GET, blibdsql — POST- .. , - , , , Ctrl+C , .
Wapiti - -p -a. : Basi, Digest, Kerberos NTLM. . , ( User-Agent) .
wapiti-getcookie. C cookie, Wapiti . cookie :
# wapiti-getcookie -u http://sites.vulns.pentestit.ru/login.php -c cookie.json: , :
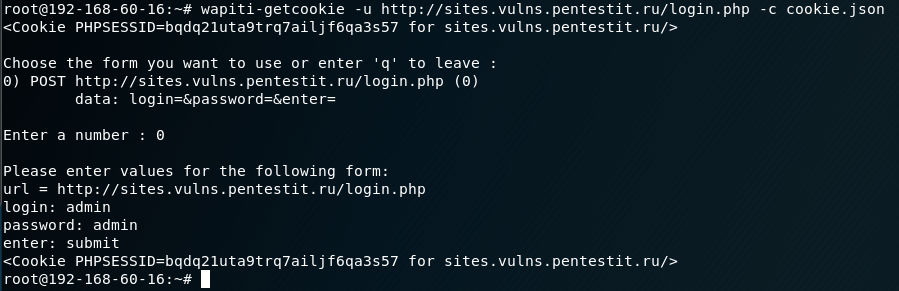
JSON. — -d:
# wapiti-getcookie - http://sites.vulns.pentestit.ru/login.php -c cookie.json -d "username=admin&password=admin&enter=submit":
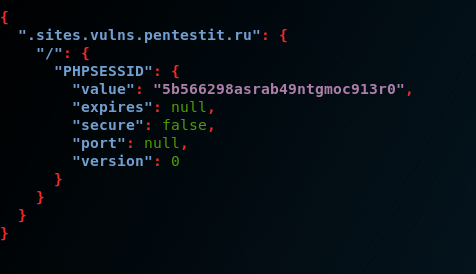
, - :
# wapiti --level 1 -u http://sites.vulns.pentestit.ru/ -f html -o /tmp/vulns.html -m all --color - cookie.json --scope folder --flush-session -A 'Pentestit Scans' -p http://myproxy:3128:
-f -o — ;
-m — — , .. ;
--color — Wapiti;
-c — cookie, wapiti-getcookie;
--scope — . folder URL, . URL ( );
--flush-session — , ;
-A — User-Agent;
-p — -, .
HTML-, . , , , curl , . , :
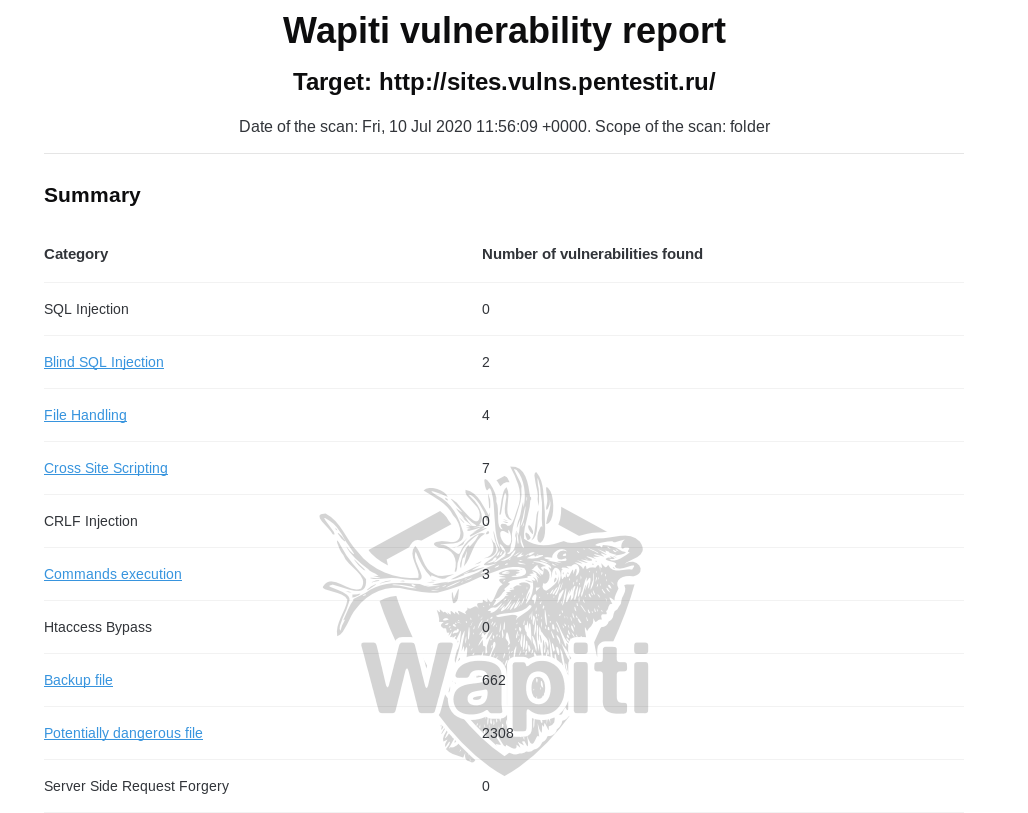
— -, , . . « » « ». , :
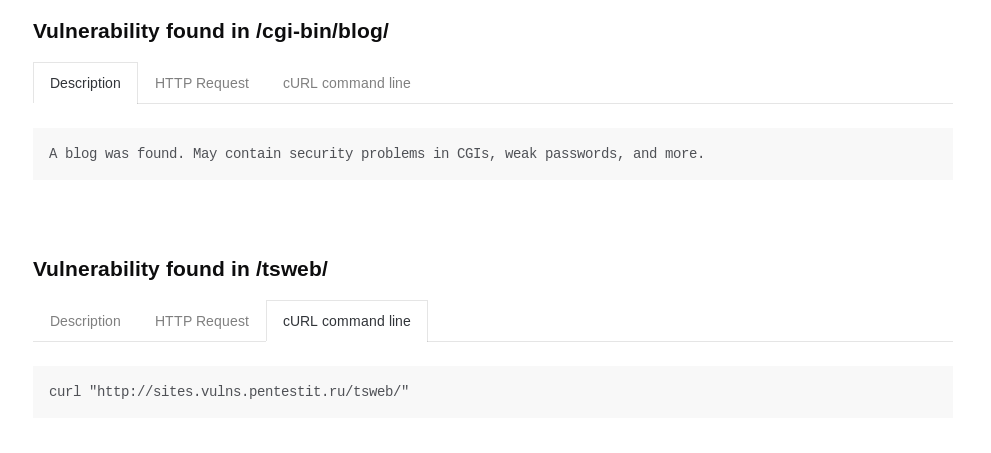
, . ( ), . , — --color :

.
SQLi
C SQLi. SQL- , , :
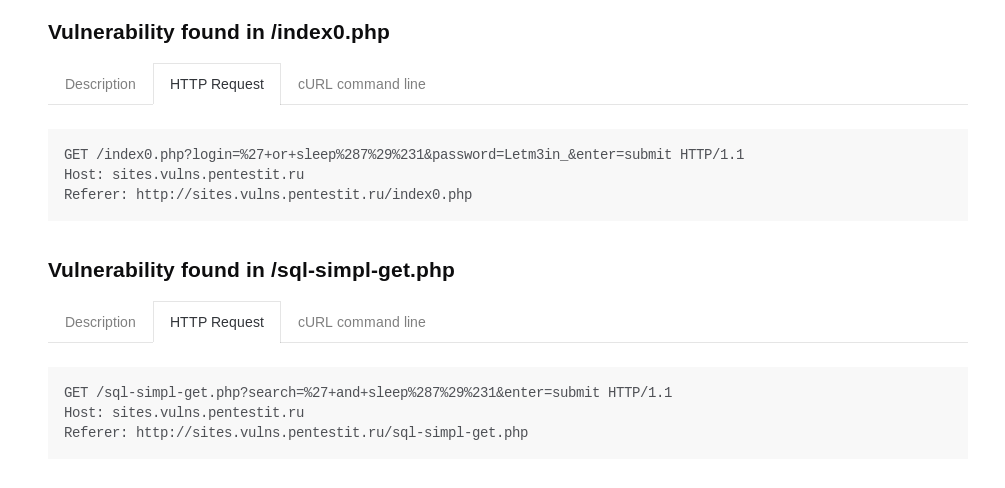
, , cookie, " " cookie . , , -x, . . , , - .
XSS
:

LFI/RFI
The scanner found all inherent vulnerabilities:
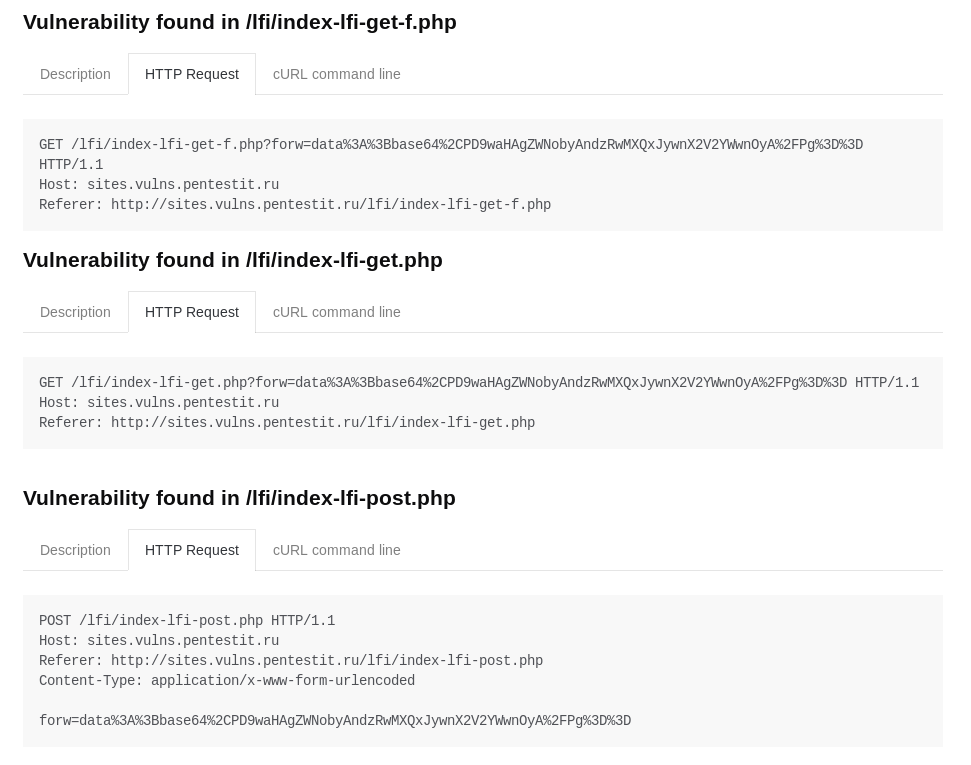
Overall, despite false positives and missing vulnerabilities, Wapiti, as a free tool, shows pretty good results. In any case, it is worth recognizing that the scanner is quite powerful, flexible and multifunctional, and most importantly, it is free, therefore it has the right to use it, helping administrators and developers to get basic information about the security status of a web application.
Stay healthy and protected!