We are at a turning point in the development of a culture of DevOps and CISO relationships. CISOs need to protect organizations at all costs, and DevOps is all about flexibility, so they tend to choose a good enough security solution and sometimes strongly oppose the proposed protections. ...

What does this mean for business and cybersecurity?
Radware conducted research among the DevOps and DevSecOps communities to find out how widespread DevOps is and how it impacts security decision-making. Radware researchers interviewed nearly 300 professionals from companies of various sizes around the world. Below is a summary of the results.
Companies implement innovative technologies and concepts
In general, companies are well aware that the introduction of new standards and solutions in the transition to digital technologies requires an objective attitude (and a large budget), so they try and / or purchase additional security tools.
For example, 67% of surveyed companies use microservices / containers, and 53% have already implemented container protection technology. 43% use a dedicated serverless runtime protection solution to avoid crashes and data leaks.
All of this looks promising, but it seems that companies are using trial and error and applying multiple technologies without ensuring their compatibility. They hope that the availability of a variety of technologies will provide effective protection.
As microservices and container management are still emerging technologies, it is imperative that companies explore which solutions and practices are appropriate for new infrastructure and data flows. Unjustified reliance on existing security models leads to unforeseen security breaches and, as a result, data leaks.
Companies apply mandatory security measures
They not only strive to introduce new protection technologies, but also widely apply established practices. For example:
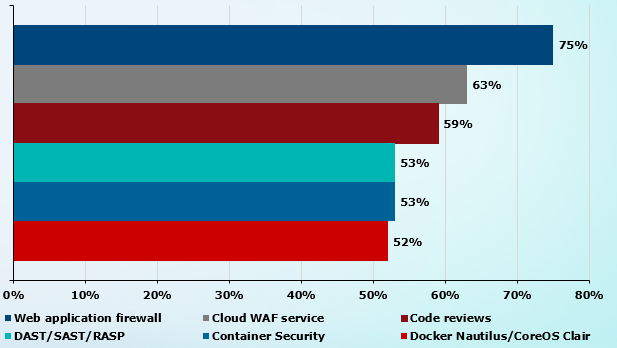
- 70% of companies control West-East traffic;
- more than half review code along with security testing and WAF solutions;
- 52% consider the quality of security to be the main criterion for choosing a technology to protect applications.
This is confirmed by the use of API protections. In the diagram below, you can see that companies are aware of the security threats posed by the API and are actively working to eliminate them. The correct approach, given that APIs are currently linking tools, applications, systems, and environments.

Applying basic security practices, DevSecOps, and application security technologies create a sense of confidence. (Over 90% of organizations have already established DevOps or DevSecOps teams, and 58% reported a DevSecOps to development talent ratio of 1: 6 to 1: 10.)

... And yet applications are hacked
Hackers are winning so far, and application attacks continue to pose a threat. 88% of respondents reported attack incidents to Radware during the year, of which 90% were affected by data breaches. Respondents experienced daily access violations, session hijacking, cookie spoofing, SQL injection, denial of service attacks, protocol attacks, cross-site scripting, cross-site request forgery, API manipulation, and more.
56% of those surveyed noted that it is difficult for companies and cloud service providers to delineate security responsibilities. Many organizations face different types of application attacks on a weekly basis.

API gateways don't seem to help with the problem. Typically used for authentication (37%), IP filtering (30%), and basic load balancing (28%), they obviously cannot block all API manipulation attempts.
In general, solutions based on static rules and rigid heuristics do not provide an adequate level of protection for constantly changing applications. Half of the respondents noted that their applications are constantly changing, sometimes several times a day. In such cases, a person is simply not able to keep everything under control. This requires identifying a change, setting up a policy, approving and executing it, which is impossible without automation.
Because of the rapid pace of change, responsibility shifts to others who are responsible for agile development, delivering applications and microservices, creating SLDC environments, and choosing tools. DevOps and DevSecOps are beginning to have a greater impact on security decisions. It was this hypothesis that Radware wanted to test.
Who makes the decisions?
Not security experts. The IT department is mainly influenced by the choice of tools, policy setting and implementation of application protection. (The IT department controls the budget, but 70% of the CISOs do not have a casting vote.)

Digital transformation is not just digital transformation
A Radware study found that the success of attacks is due to the fact that enterprises do not fully consider the impact of digitalization.
In this process, technology initiates change. The simplest thing is to acquire and implement new technologies and platforms, but the technologies will not start working on their own. Despite organizations striving to follow security rules, attackers continue to successfully attack. Why? Because companies are not taking the second - non-digital - step of this transition: acquiring new competencies, adapting business processes, redistributing roles and responsibilities.
This is a weak point in application security. If security professionals can do their job and make security a defining factor in the business, perhaps we will finally see how the evolution of security systems will match the speed of the business.