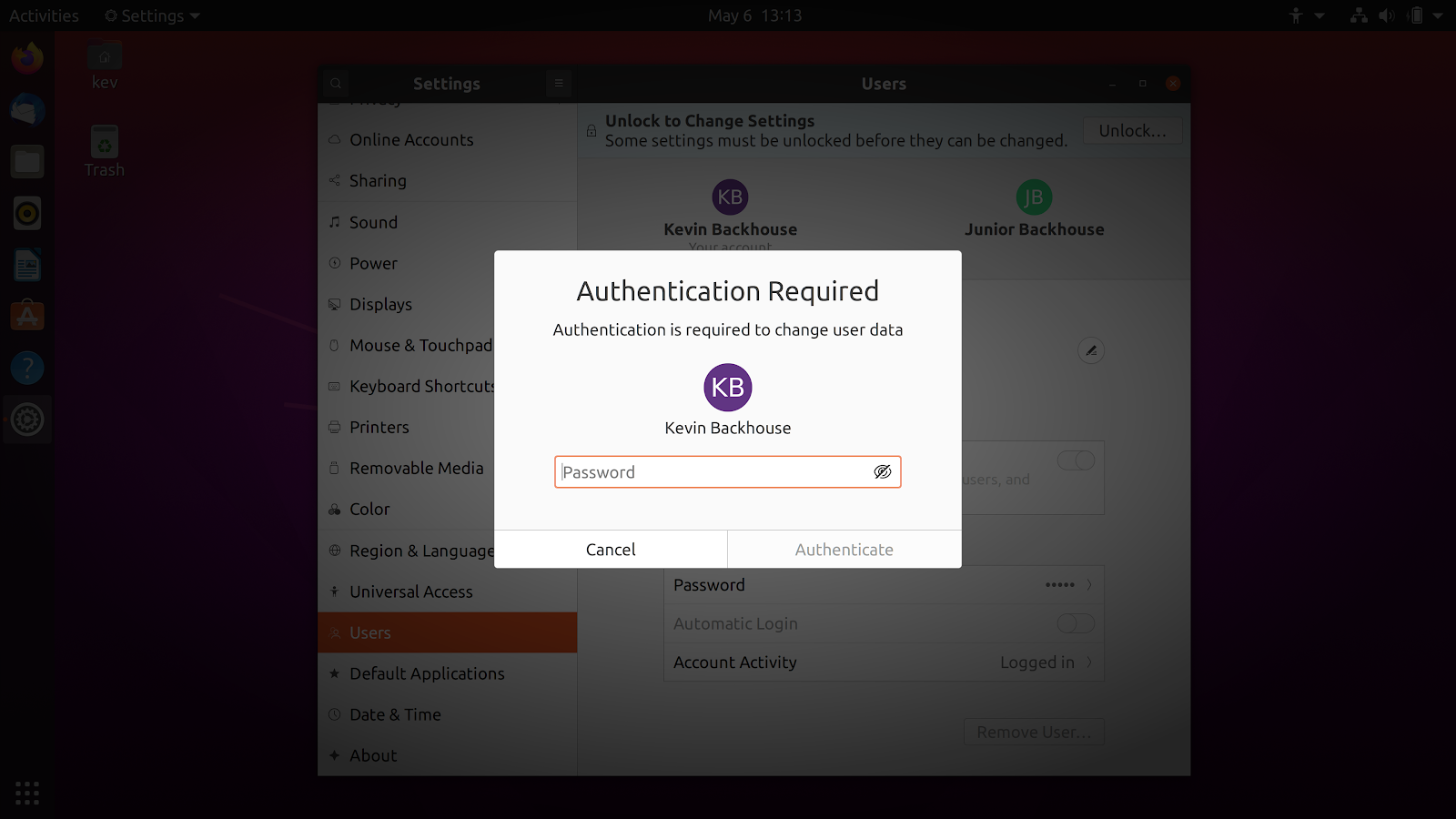
The polkit service is responsible for authorizing the user, it checks for the necessary rights to execute the command, and in the graphical interface its work is usually limited to a window asking for a password. It is used by the systemd system software; polkit can also be invoked via the command line. The vulnerability is exploited through a simple set of commands. If, at a good moment, "kill" the process with a request to create a new user, an error in the polkit code will not only create a new user, but also add him to the sudo group.
Then everything is simple: we create a password for the user (we do not have the right to do this yet, but we are using the vulnerability again) and gain unlimited control over the system. The sequence of commands is described in Beckhouse's article and shown in this video:
The problem lies in incorrect error handling when connection to a process that requires user rights verification is no longer available (hence the need to "kill" the process). Instead of dying, polkit processes the request as if it came from the superuser. The error got into the program code 7 years ago. Distributions such as Red Hat Enterprise Linux 8, Fedora 21, and Ubuntu 20.04 are affected. Since some builds use a fork of polkit, which the vulnerability sneaked into later, they are safe. This applies, in particular, to the stable version of Debian 10. On the CVSS v3 scale, the problem received a score of 7.8 points out of 10, a patch for a number of distributions is already available .
What else happened
Hijacking of large companies continues. Last week it became known about the theft of game source codes and other information from EA. Later, the details of the hacking appeared: according to the Vice publication (see also translation in Habré), a private chat in Slack became the entry point to the corporate network. The hackers bought a token for access to it on the black market for $ 10, and then, through social engineering, penetrated directly into the local network.
Another leak last week occurred at Volkswagen: the data of more than 3 million customers lay in the public domain on the server of one of the contractors.
The June patch set for Android fixes several critical vulnerabilities that allow you to take control of your mobile device.
A zero-day vulnerability has been closed in the Google Chrome browser . It worked together with another bug , already on Windows. According to Google, this kit was being sold by one of the commercial brokers.
Another actively exploited vulnerability, closed in a fresh set of Microsoft patches, is described in detail by Kaspersky Lab specialists.
The information stolen from the developer CD Projekt Red in February was made publicly available .