Containers and microservices have triggered a tectonic shift in application infrastructure, and Kubernetes technology is rapidly taking over the world as a tool to help automate the management of these new application building blocks. Infrastructure dramatic changes brought security along with them, and new tools and processes were needed to protect the cloud-based application stack. Today, in the Kubernetes world, it is not enough to protect only containers and images; you need a comprehensive solution that ensures the security of the Kubernetes environment as a whole.
At the end of April 2021, Red Hat announced a new revision of its OpenShift platform - OpenShift Platform Plus, which includes the Red Hat Advanced Cluster Security for Kubernetes solution based on StackRox technologies. Today we will tell you what security tasks OpenShift closes this product, as well as analyze the advantages of the Kubernetes-oriented approach implemented in it to protect container applications.
Benefits of Kubernetes-Oriented Security
Traditional, container-oriented security solutions for cloud infrastructures have three critical flaws:
Visibility - These solutions only see images, image components, and running containers, but are not aware of the Kubernetes environment itself.
– - , , , ( ) CVE (Common Vulnerabilities and Exposures).
– , - , Kubernetes.
Red Hat Advanced Cluster Security for Kubernetes - . Kubernetes, , , . , Kubernetes- Kubernetes .
, Kubernetes, . , , . OpenShift, Kubernetes- .
(visibility)
, . , OpenShift: , , , . , , , , .
Red Hat Advanced Cluster Security for Kubernetes, OpenShift , , CVE .
, Kubernetes, , runtime-, .

OpenShift – , , , . , , , , .
CI/CD, , , .
Red Hat Advanced Cluster Security for Kubernetes . Kubernetes , , . , , , .
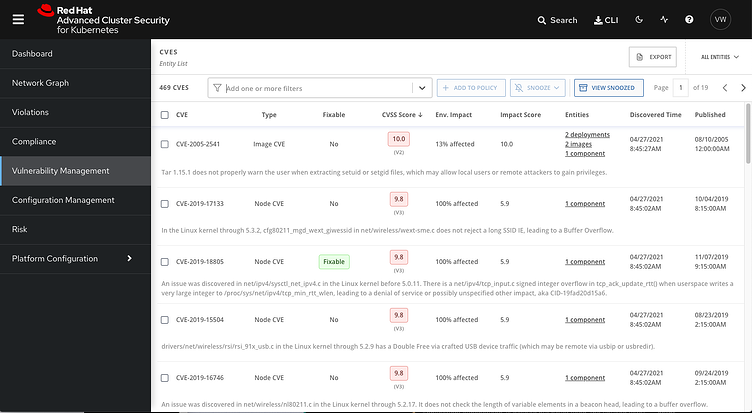
DevOps . , , DevOps. , , , .
, , .
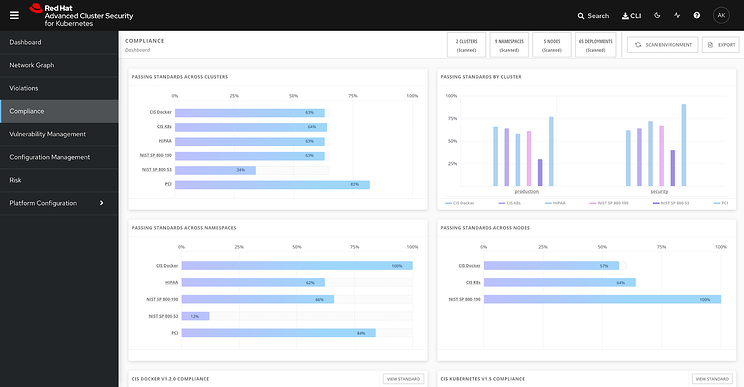
Kubernetes- CIS Docker Kubernetes, , PCI, HIPAA, NIST SP 800-90 SP 800-53. .
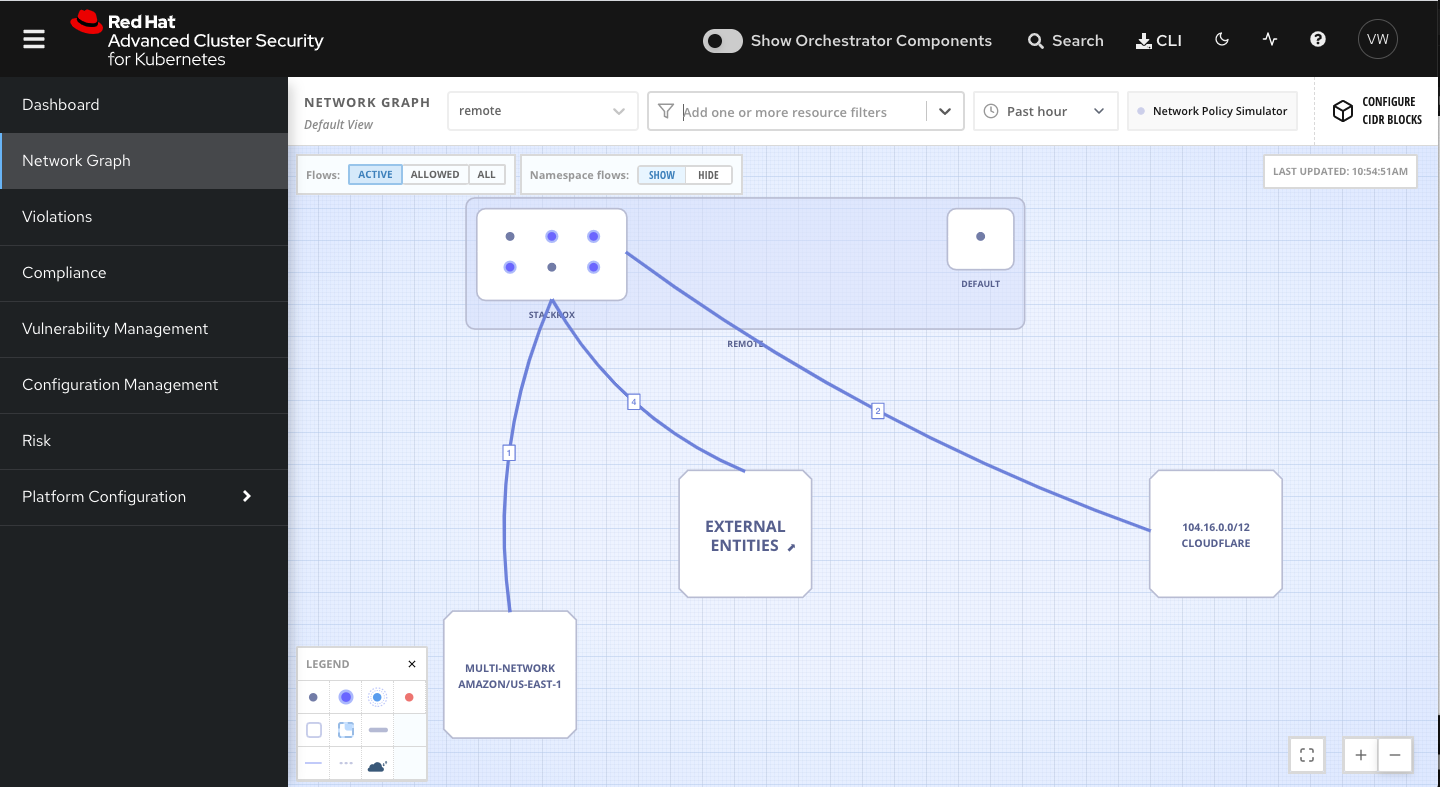
( east-west) ( north-south). . , .
Kubernetes Network Policies, , Kubernetes. , , , , - .
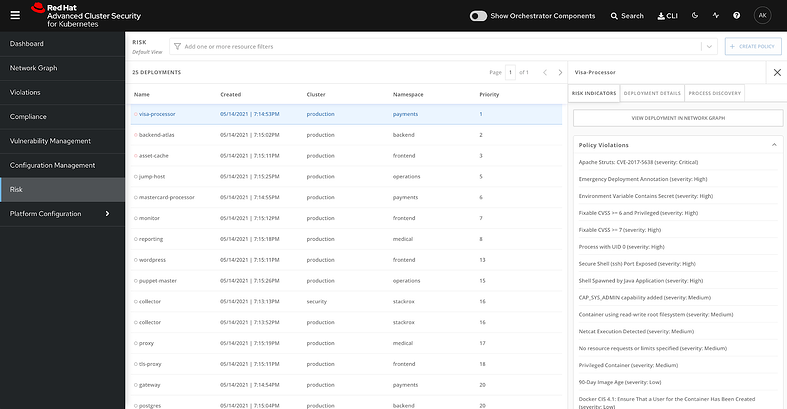
, – . , , , , , , - .
Red Hat Advanced Cluster Security for Kubernetes , . , , .
Kubernetes , . Kubernetes .
CIS Benchmark Docker Kubernetes, , , . , .
Red Hat Advanced Cluster Security for Kubernetes - , , , , . , RBAC, , . , , .
, , CI/CD, , admission control.
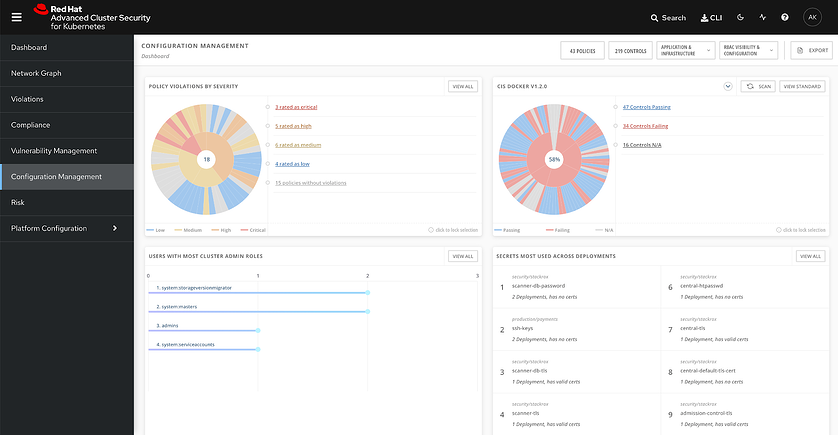
, , . – , .
Red Hat Advanced Cluster Security for Kubernetes . (behavioral baselining) .
, , . Kubernetes , , , , .
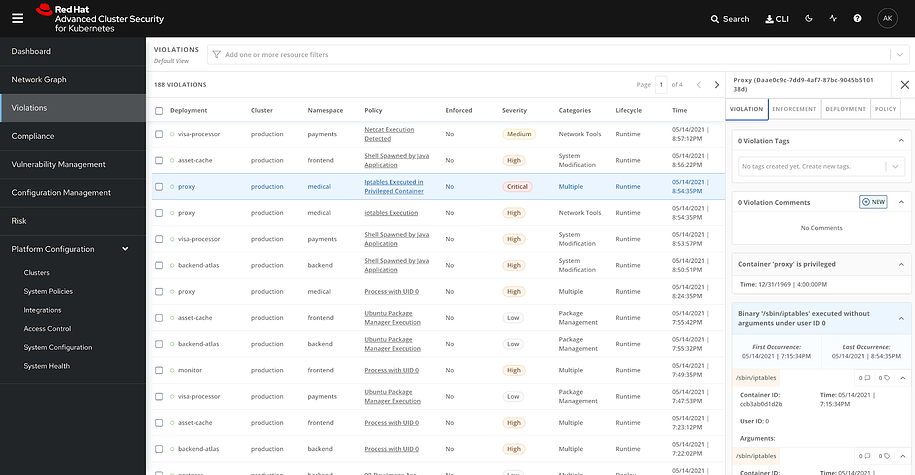
, Kubernetes , . . Red Hat Advanced Cluster Security for Kubernetes – , , Kubernetes. Kubernetes, , , , . , Red Hat Advanced Cluster Security for Kubernetes.