A package with certificates from Habr
Wireshark is a very famous program for capturing and analyzing network traffic, an indispensable tool for a hacker, network engineer, programmer, security specialist . In general, any curious person who wants to study in detail the traffic from his or someone else's mobile phone, fitness bracelet, TV.
Wireshark captures network packets in real time and stores them, for example, in pcap files (Packet Capture). They are then used to study traffic, recover information, analyze network performance, and detect attacks. It is an alternative and addition to the standard utility
tcpdump
, with a graphical interface, filters and more features.
Practical use cases
Wireshark has a million functions, but literally everyone with minimal knowledge can use it to their advantage. Below are examples of basic networking tasks.
SSL / TLS traffic decryption
Chrome and Firefox can write session key logs, which are used to encrypt SSL / TLS traffic. Our task is to enable the recording of these logs, and then upload them to Wireshark for analysis. It is assumed that we have physical access to the computer of the user whose traffic we want to decrypt. Or to a server that establishes an encrypted connection with the user.
First, enable key recording.
Older Windows 10 builds
The old method works in older builds of Windows 10. Go to Control Panel → System and Security → System . On the "Additional system parameters" tab, click the "Environment Variables" button.

Add a new variable for the user
SSLKEYLOGFILE
and specify the path to the file.

As a result, we get logs with keys, the beginning of the file:
# SSL / TLS secrets log file, generated by NSS CLIENT_HANDSHAKE_TRAFFIC_SECRET 2f80c7dfd9f1bd5f4cf0084b9c814006178a06b820c5cab264f3727fac1abb23 dcfc82758fbb587e526daaab9fdc0bcaaab2768e SERVER_HANDSHAKE_TRAFFIC_SECRET 2f80c7dfd9f1bd5f4cf0084b9c814006178a06b820c5cab264f3727fac1abb23 d807f4757db1f9ba8df434d8b0005d07e4987459c1d14c7ea793e4c4f5b240dc CLIENT_TRAFFIC_SECRET_0 2f80c7dfd9f1bd5f4cf0084b9c814006178a06b820c5cab264f3727fac1abb23 40186c6b1c925c63cd57e8fa235ba9d0bf14eb29c21cbb6494ef944e1e7a4cc3 SERVER_TRAFFIC_SECRET_0 2f80c7dfd9f1bd5f4cf0084b9c814006178a06b820c5cab264f3727fac1abb23 a0a377f26a0962eceae55bec94fcd7549d9b1d5d1e9b70c45627299ca2b9b129 EXPORTER_SECRET 2f80c7dfd9f1bd5f4cf0084b9c814006178a06b820c5cab264f3727fac1abb23 ...
Windows 10
In newer versions, after installing Windows 10, the old way of adding environment variables may no longer work. Then there is an alternative option using a command in PowerShell .
Set variable:
[Environment]::SetEnvironmentVariable("PATH", "C:\TestPath", "User")
The first parameter is the name of the variable, the second is the value, the third is for which level the variable is (user or system).
In our case:
[Environment]::SetEnvironmentVariable("SSLKEYLOGFILE", "D:\wireshark", "User")
Linux and Mac OS X
Under Linux and Mac OS X, you can use this command to change the environment variable and keep logs - starting the browser from the same terminal window, since environment variables always work within the same session.
# export SSLKEYLOGFILE=/Users/username/sslkeylogs/output.log
# open -a firefox
# wireshark
After accumulating the log, launch Wireshark.

We go to the "Parameters", there, on the "Protocols" tab, we find the TLS section (earlier it was called SSL) - and specify the path to the file with the logs and the key that was used in the symmetric encryption session: (Pre) -Master-Secret log filename .
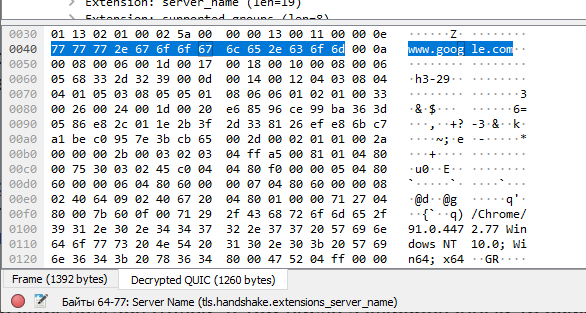
For example, when a user logs into the Gmail server in the QUIC packet inspection window, we see regular QUIC packets encrypted with a TLS key.

But a new Decrypted QUIC tab appears at the bottom of the screen , which shows the decrypted contents of these packets.
This method of decrypting client traffic does not require installing Wireshark on his computer, it is enough to download a dump with keys and then use it together with the traffic dump.
Under modern Russian law, providers are required to store user traffic for some time, including encrypted TLS / SSL traffic. Now it is clear what kind of mechanism can be used to decipher and analyze it. An attacker must have session keys for symmetric encryption. The largest Russian Internet companies such as Yandex and Mail.ru obediently comply with the requirements of Russian legislation - and provide these keys (see FSB order No. 432 of 08/12/2016 on the procedure for obtaining encryption keys).
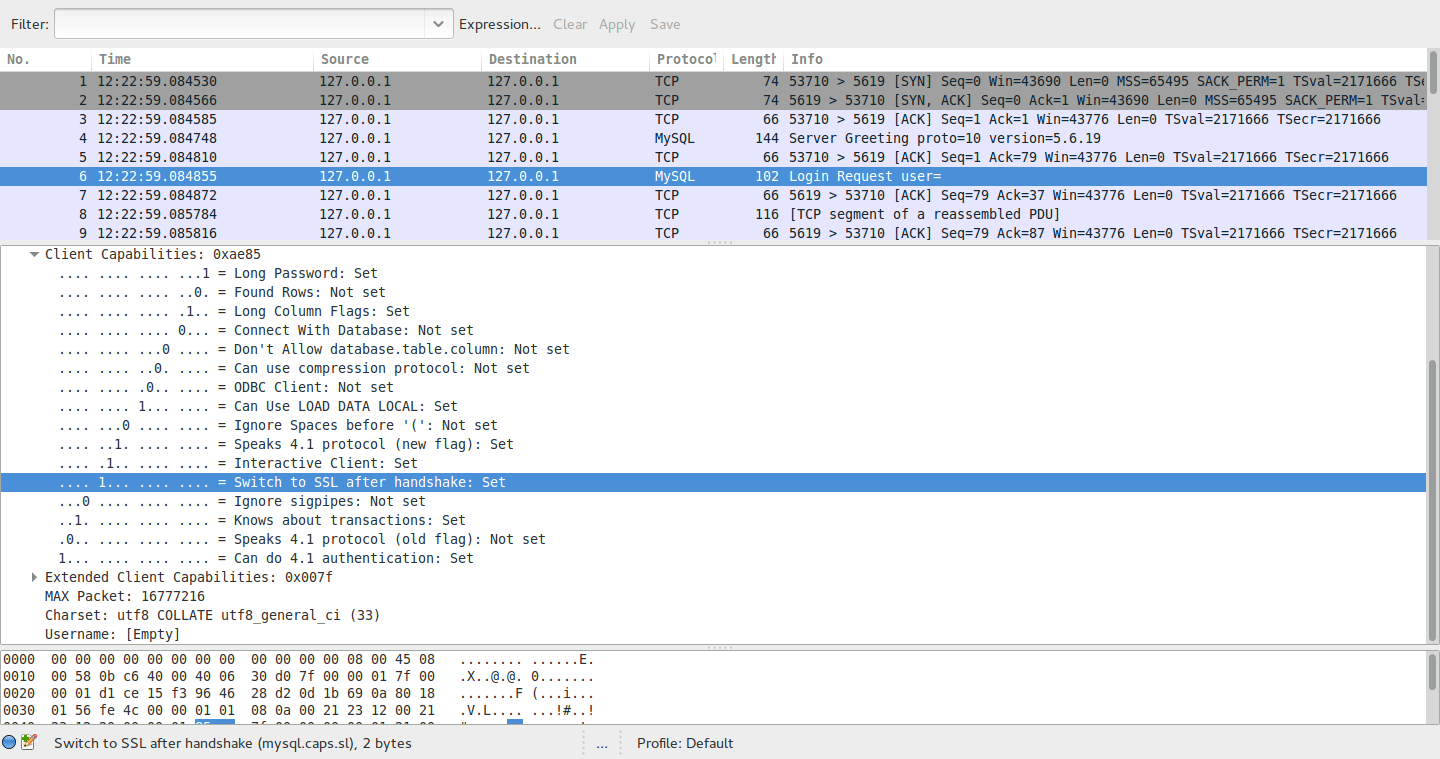
Note... This method is not limited to HTTP only. Similarly, you can intercept and decrypt SSL / TLS traffic in other streams. For example, encrypted traffic from the MySQL server .
Analyzing traffic from another computer
If you need to deal with the server in production, it is convenient to copy pcap files from there - and analyze the traffic on your personal computer.
We write packages on the server using the tcpdump packet sniffer, which is included in the standard * nix package:
tcpdump port 443 -w output.pcap
Then we copy the files to our computer:
scp host:~/output.pcap
Here we are already launching Wireshark and opening the resulting file.
There is an option to monitor server traffic in real time from your home / work computer. For example, all traffic except ports 22 and 53:
ssh root@host tcpdump -U -s0 'not port 22 and not port 53' -w - | wireshark -k -I -
Roughly the same from a Windows computer:
plink.exe -ssh -pw password root@host "tcpdump -ni eth0 -s 0 -w - not port 22" | "C:\Program Files\Wireshark\Wireshark.exe" -k -i -
Looking for problems
To select a specific TCP connection, we find any packet of interest, right-click on it, and apply the dialog filter.
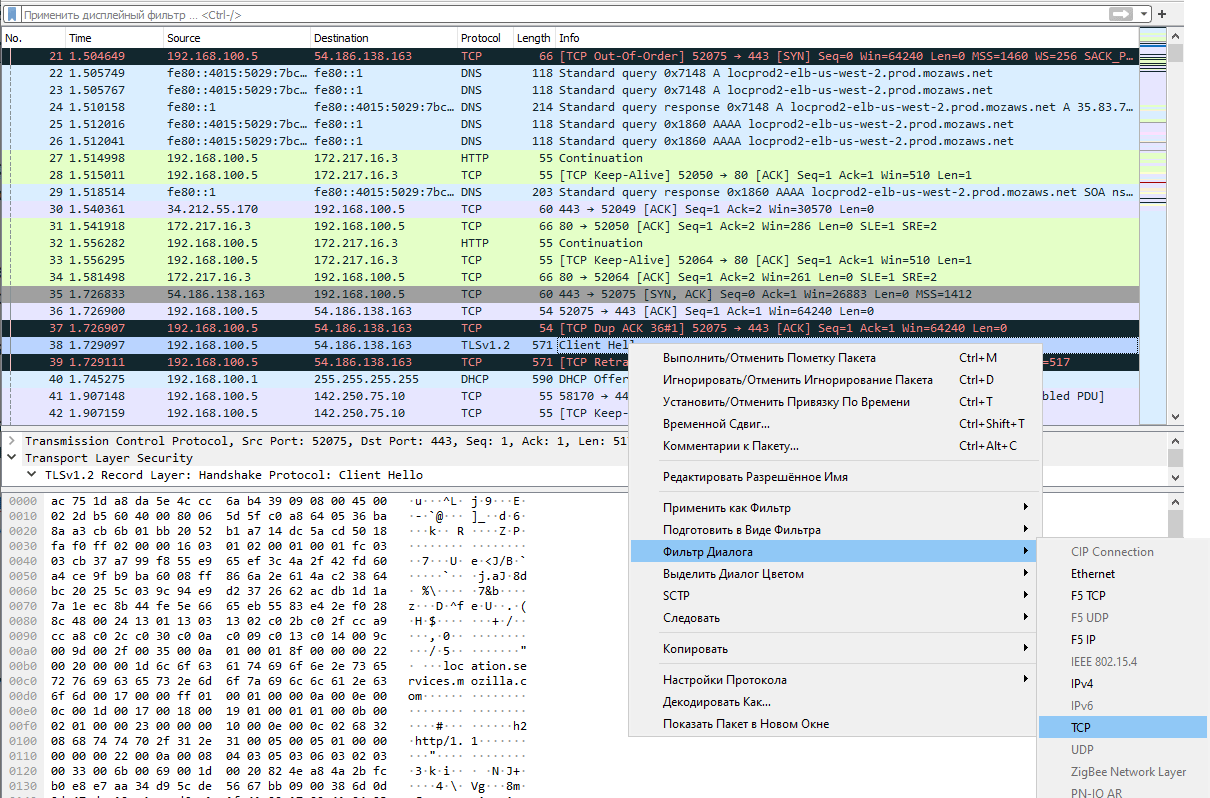
Now, of all the recorded traffic, only packets that belong to this particular connection remain.
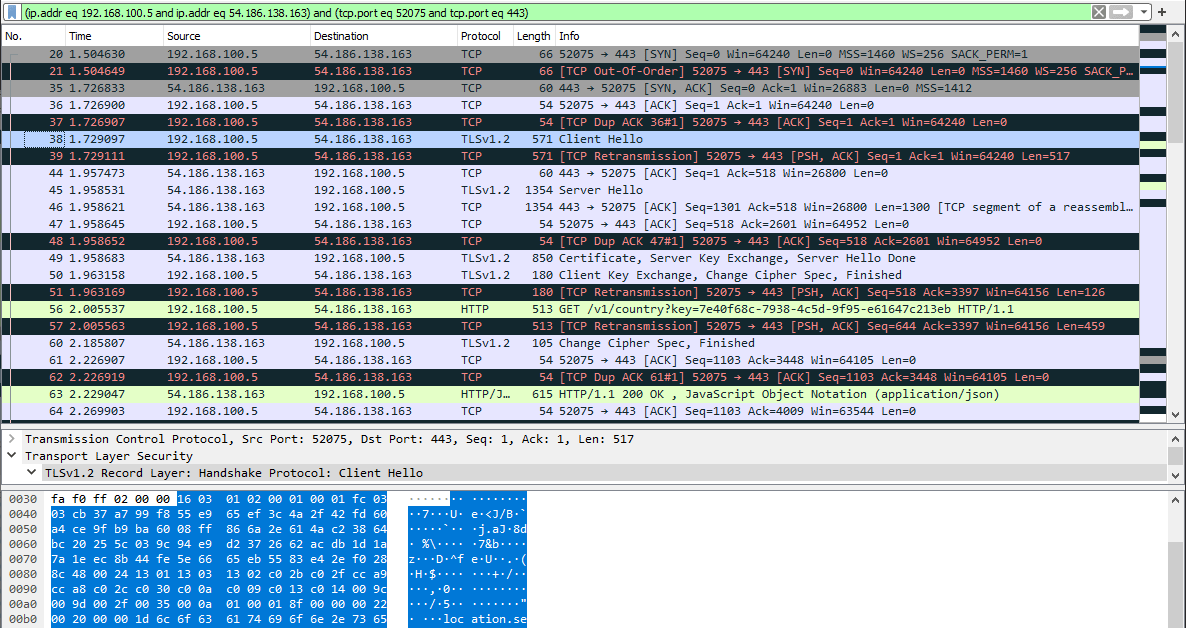
In the screenshot, we see the packets from the beginning of the TLS connection establishment: a packet with a client greeting, a response packet with a server greeting, a presented certificate, a list of ciphers, and so on. The contents of each package can be examined separately. Very comfortably.
A typical pattern is to use Wireshark to diagnose specific problems. For example, if the TLS connection is broken, we can go in and see who broke it (client or server), at what stage it happened and for what reason.
Package content
The byte content of each packet is magic. Specifically, this functionality of Wireshark allows you to identify the most serious bugs. For example, a few years ago it was revealed that Intel 82574L Gigabit Ethernet controllers are disabled if a specially designed packet with a specific sequence of bytes is sent to them - the so-called "death packet" . It was thanks to Wireshark that it became clear which specific bytes in the packet lead to the guaranteed disconnection of the network card.
Here is an entry for specific packages: pod-http-post.pcap and pod-icmp-ping.pcap . We can download them, open them in Wireshark and see them with our own eyes.
The Intel network interface is disabled if the address 0x47f is 2 or 3, that is, 32 HEX or 33 HEX. If there is 4, then everything is fine.
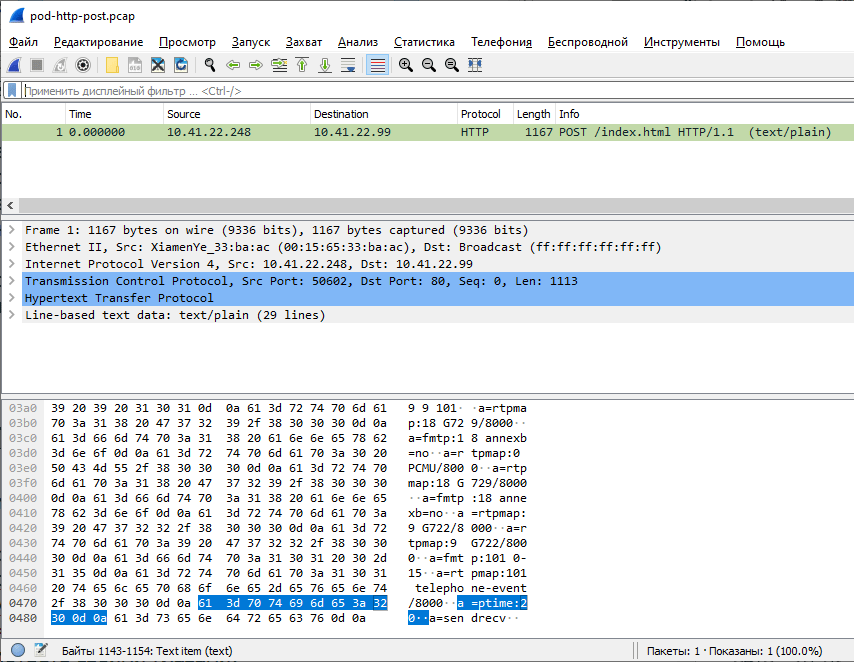
Any packet was suitable for the attack: HTTP POST, ICMP echo-request, etc. For example, a 200 response can be configured on a web server to "kill" the network interfaces on the client machines. Quite a curious situation.
Search packages by content
Above, we applied a dialog filter to return all packets for a specific TCP connection. However, filters can also be written manually. Here are some examples of requests:
frame contains "google"
- search for all packages with the word "google" anywhere in the package
tcp.port == 443
- port 443
dns.resp.len > 0
- all DNS responses
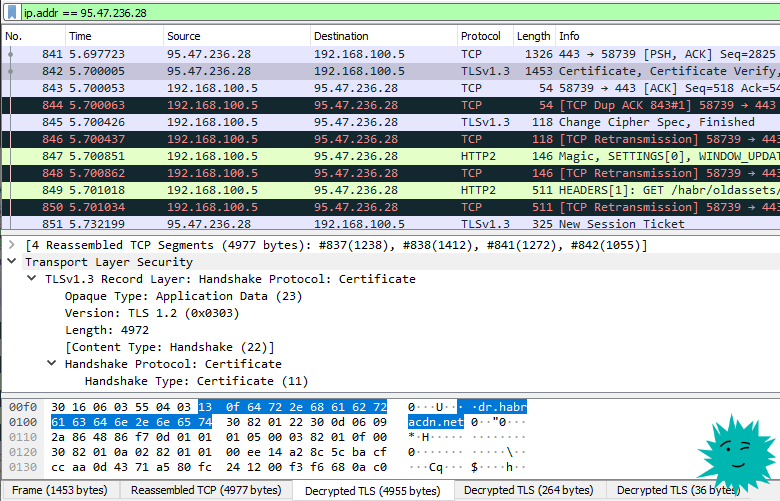
ip.addr == 95.47.236.28
- specific IP address for the recipient or sender
… etc. Filters are much richer than those of tcpdump, so it is better to do traffic analysis in Wireshark.
Mobile phone traffic
Similarly, you can analyze the traffic from the fitness watch via Bluetooth or the traffic of any mobile application for Android. To do this, you need to record PCAP packets on a mobile device - and transfer them for analysis to Wireshark on a working PC.
There are several mobile PCAP recording programs. For example, the
PCAPdroid application for Android:

PCAPdroid
In principle, it is possible not to transfer the recorded PCAP files, but to analyze them directly on the mobile device. Some mobile sniffers have rudimentary packet sniffing features, see Packet Capture and Termux (more on that below).
Packet Capture
Wireshark also has a direct Androiddump interface to pull data from the phone directly through the Android SDK.
Traffic from TV and other household appliances
To study the traffic from the TV, wife's smartphone or other household appliances that are connected to the home network via Ethernet and WiFi, you will have to record PCAP on the router. Sometimes the built-in tools are enough . If you have a router with DD-WRT firmware, you can run directly on the device
tcpdump
:
ssh root@192.168.1.1 -c "tcpdump -v -w - -i eth2" > mypackets.pcap
For the OpenWrt firmware, there is an option to mirror traffic using iptables-mod-tee .
Traffic can be mirrored and recorded using an additional physical hub or network tie-in. See the documentation for details .

Another way is to intercept WiFi wireless traffic using the Airodump-ng utility without connecting to a router. But this is more suitable for analyzing traffic on other people's hotspots.
Then everything is done on the knurled - load the files into Wireshark, run the filters.
By the way, Wireshark also supports USB traffic analysis: built-in USBPcap sniffer and importing packages from third party sniffers such as Npcap and RawCap .
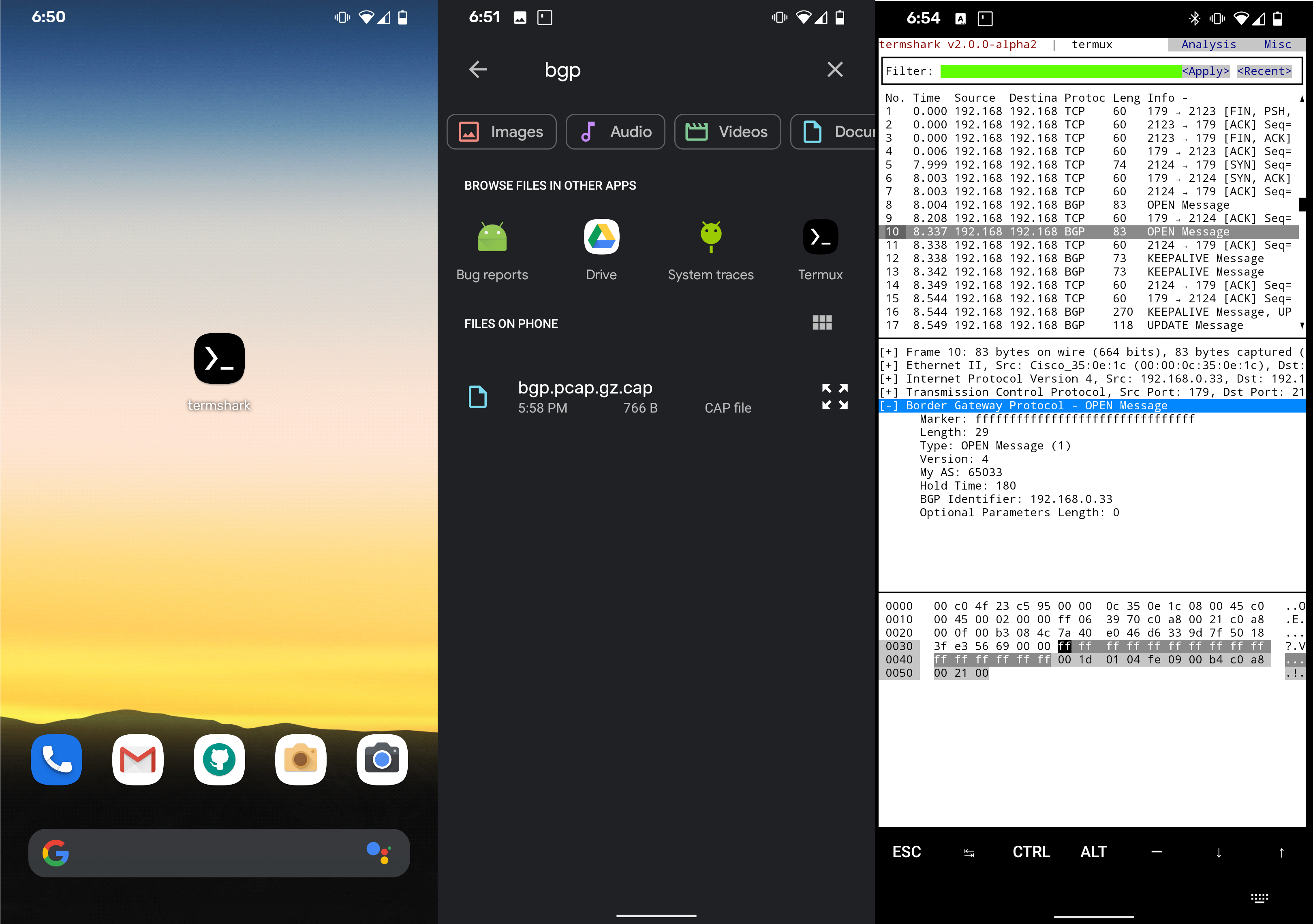
Termshark
If you analyze large logs on a remote server, but do not want to copy everything to your machine, Termshark may come in handy - a convenient user interface in the console for the TShark analyzer, which looks like Wireshark.
Functions
- Reading pcap files and listening to traffic from active interfaces in real time (where tshark is enabled)
- Filtering pcap or active interfaces with Wireshark display filters
- Reassembling and inspecting TCP and UDP streams
- View network sessions for each protocol
- Copying the selected packages from the console to the clipboard
- The tool is written in the Go language, on each platform it is compiled into a single executable file: there are already built versions for Linux, macOS, BSD variants, Android (termux) and Windows
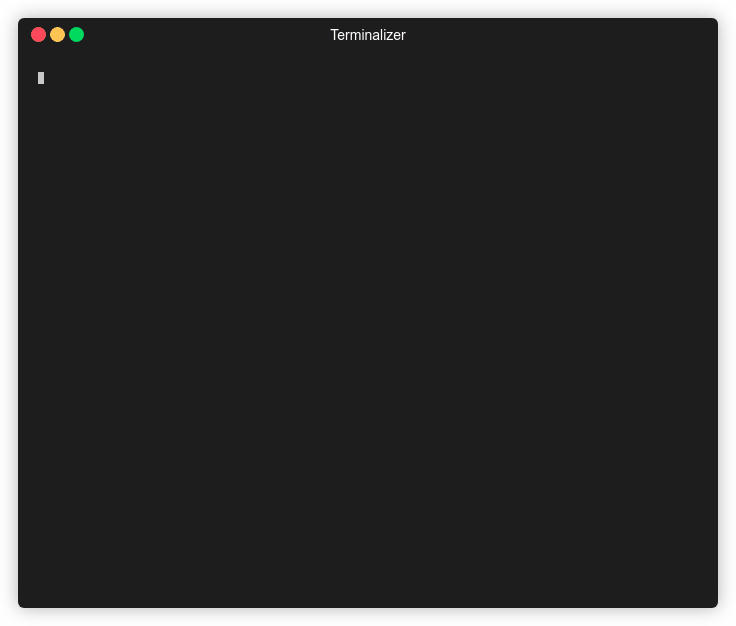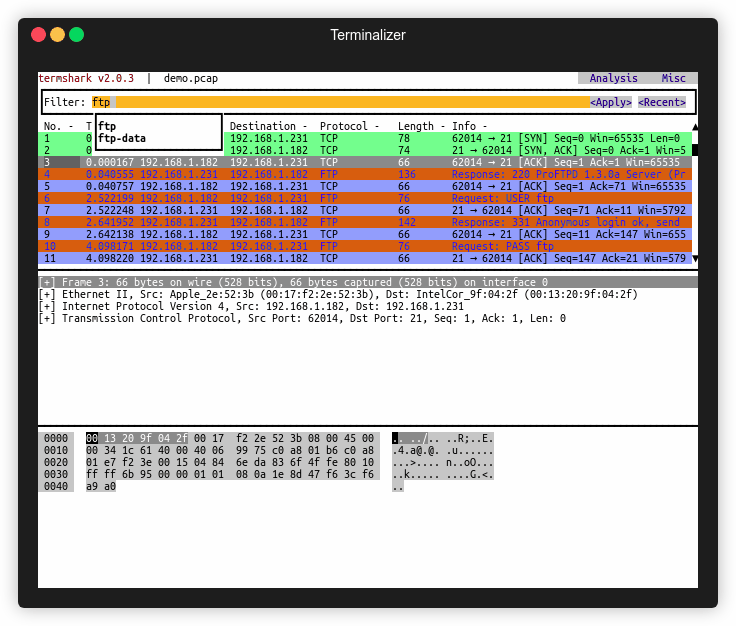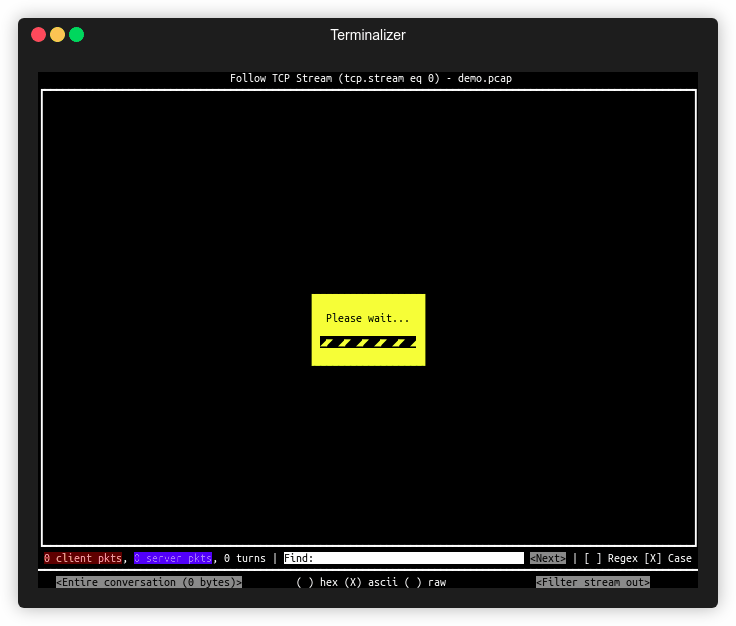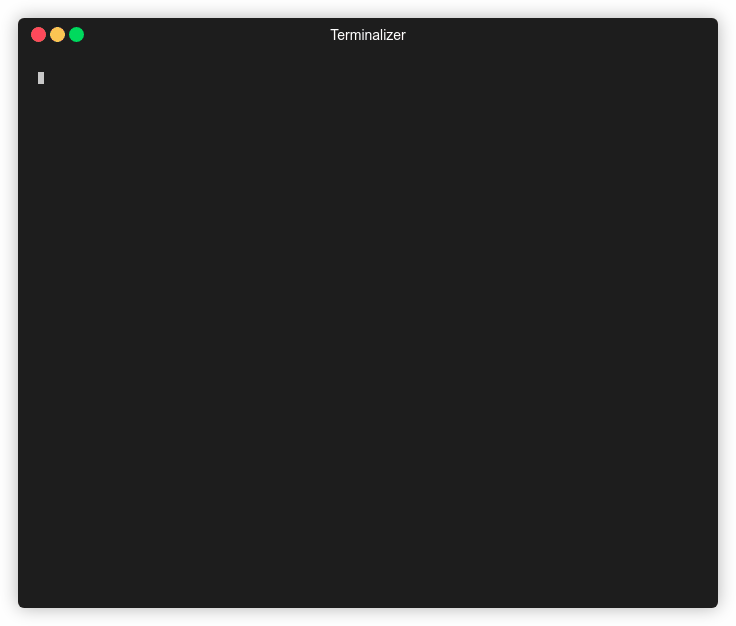
This is what the Android version looks like:
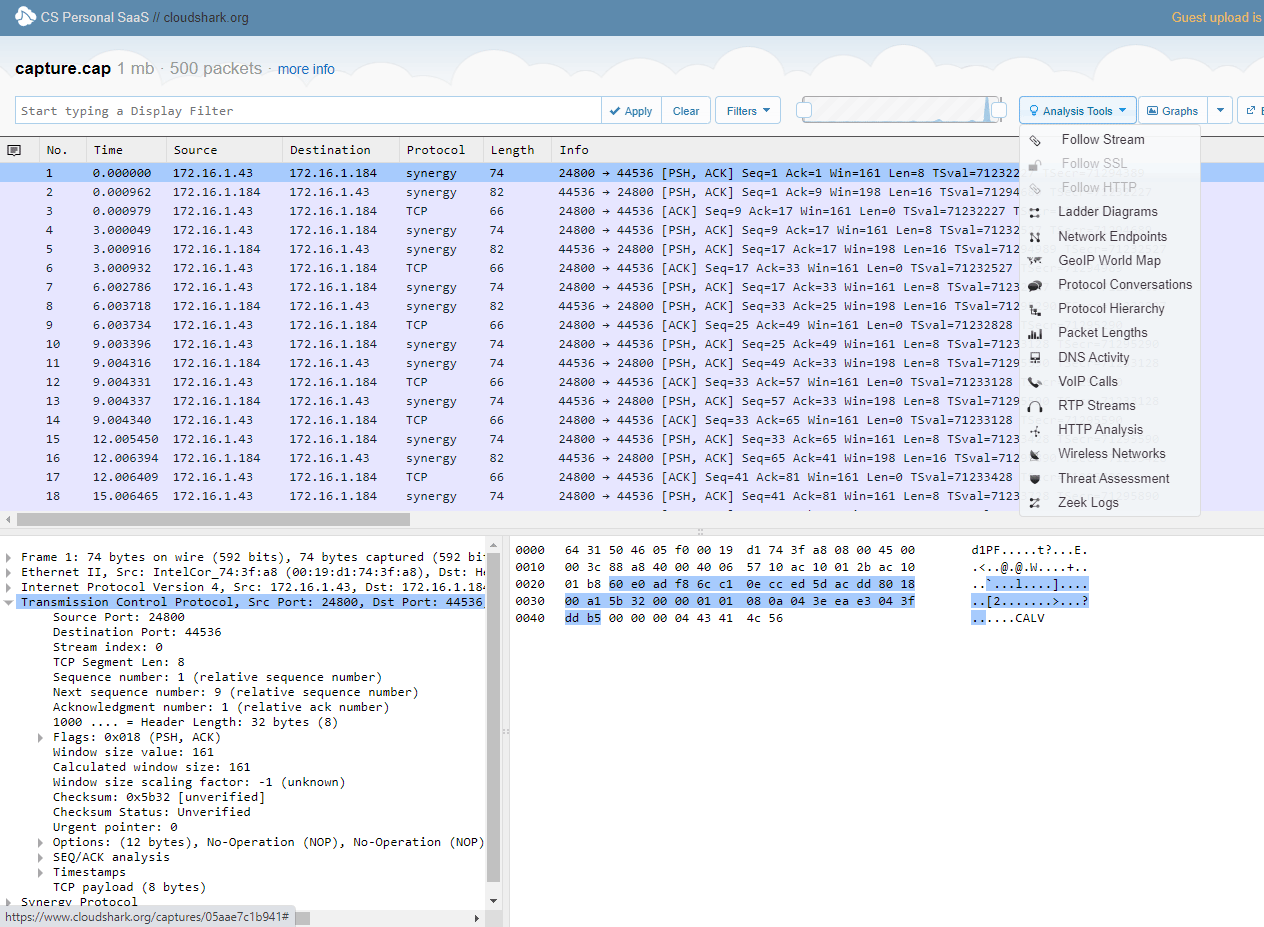
Wireshark as a web application
If for some reason you cannot run Wireshark on your local machine, you can use the CloudShark cloud service , which is surprisingly well made. The main function is to collaborate and publish package parses by URL. For example, cloudshark.org/captures/05aae7c1b941 . The files are uploaded to the cloud and analyzed in the browser. This is necessary if you want to ask for advice on the forum, share information with colleagues, or publish a package breakdown for a wide audience. By the way, it is convenient to use it from a mobile phone, because there are applications for capturing packets for Android, but there is no good analyzer. The service is paid, there is a 30-day trial period.
All in all, Wireshark is a fantastic program for all occasions.
In addition to the real practical use, the analyzer gives a rough idea of how DPI filtering works with Russian providers. Everything is arranged about the same there. The system scans traffic in real time, filters specifically packets from Twitter - and slows down their delivery to users in Russia. In particular, Roskomnadzor has been dealing with this lewdness since March 10, 2021 .
Advertising
If you need a server for rent on Linux or Windows for work , then you definitely come to us - activation of the service a minute after payment!
Join our Telegram chat .
