What's your favorite PC game? Lineage, Doom, Cuphead, WOW, other? I love playing old games for Dendy or Sega consoles, for example, in Mario, where, passing level after level, you get to the final boss. The game plot of most console games is generally structured in the same way: overcome all obstacles, "suffer" and do not turn off the console for weeks to force the boss to give you the princess.
In real life, earning maximum bonus points is most often obtained from the first level: hacking personal devices / accounts of key executives of companies is a quick way to get what you want: strategic plans of the company, financial data, unlimited access to accounting systems.
While building defenses around business systems, overlapping with monitoring and protection means, many companies forget about one thing: the most "tasty" and often less secure data are usually concentrated in the hands of several people: the top management of the company.
I work on a team that specializes in information security audits, and our customers pay us to hack into their infrastructure. And we constantly have to "blur" in our reports screenshots with confidential information found on desktops / network folders / mailboxes of executives, which we were able to access.
Your bosses can be easily hacked too. How? Under the cut I will tell you about the most common attack vectors, as a rule, leading to a successful hack, i.e. allowing you to start the game and finish it almost immediately. There you will also find guidelines for protecting the data of your company's management.

, , . «» , - . , :
|
|
- — |
- — |
: , ( , .) |
«» |
, « » |
Hardening : , GPO, , BIOS . |
VLAN, , «» GPO |
MacOS Windows- |
: , . |
, |
« hard, » |
: SandBox, anti-spam, . |
VIP- , s-mime |
|
Endpoint protection: , MDM . |
EDR |
«» , « » |
: « » , LAPS . |
, , |
vnc, |
? « » — , .
( — « »)
«» (OWA- , MS Office 365, , confluence ..) . :
«» ;
«» ;
().
, , , «» . — , : (ERP, CRM, BI .), «» . — VIP-fishing (aka Spear-phishing).
? . , , — . VIP-phishing — , : , , . .
- , , , . , « », .
: , «», ( «»). : , , .
— . , ( ). / .
, — -. , blue team & read team . , «» : , . , .
, : , , , . OSINT. OSINT . OSINT- , . : reverse photo location — .
«»: « » , DPD, PonyExpress WhatsApp . «» .
, . , « » () , :
OSINT - ( , );
;
.
— . , : , -, , .
, . «» — , «» : /. .
, : , , , . «», : , -: event@example.com, .
, : , , - . , .
( — « »)
(VNC, TeamViewer .) , «» . , ( ) . .
: « », « Mac», « » . : - ( «»). : , VNC SYSVOL , , .
, . : , , , .
? — : , , . - Windows (RDP).
, :
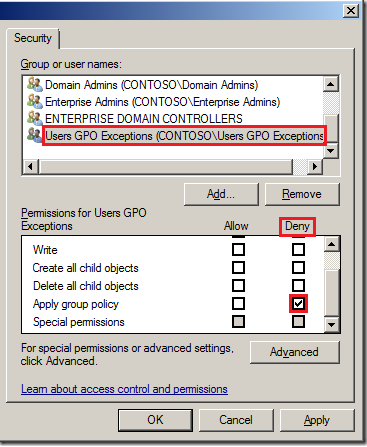
AD / (Group Policy). . — «» .
, , — SMS . , «» AD — Fine-Grained Password Policies — . : Windows , , .
? , «», . , : , : - ?
, , , , . : : , , .
— . - « » . All Domain Users «read/write» — , «», «Finance», «Buh».
? — ? ? , , « » .
mimikatz . Mimikatz , LSASS.EXE.
? , RD Session host (MS RDS), BI-.
, . , :
LM NTLM,
,
Protected Users,
,
debug,
.
, , , . . , « » .
— « » baseline . , . , , , .
?