
In this article, we'll take a look at Dockle , a container image security scanning tool that you can use to find vulnerabilities. In addition, it can be used to perform Best Practice compliance checks to ensure that the image is actually being created from the saved command history.
Installing Dockle
There should be no difficulties when installing the utility:
Installation on OSX
$ brew install goodwithtech/r/dockle
Installing on Linux
# RHEL $ VERSION=$( curl --silent "https://api.github.com/repos/goodwithtech/dockle/releases/latest" | \ grep '"tag_name":' | \ sed -E 's/.*"v([^"]+)".*/\1/' \ ) && rpm -ivh https://github.com/goodwithtech/dockle/releases/download/v${VERSION}/dockle_${VERSION}_Linux-64bit.rpm #Ubuntu $ VERSION=$( curl --silent "https://api.github.com/repos/goodwithtech/dockle/releases/latest" | \ grep '"tag_name":' | \ sed -E 's/.*"v([^"]+)".*/\1/' \ ) && curl -L -o dockle.deb https://github.com/goodwithtech/dockle/releases/download/v${VERSION}/dockle_${VERSION}_Linux-64bit.deb $ sudo dpkg -i dockle.deb && rm dockle.deb
After installing the utility, all you need to do is specify the name of the image. You don't need to configure anything else, you don't even need Docker.
Dockle example
Run the utility by specifying the name of the image. If there are no problems, a message will be displayed in the console PASS
, and if problems or vulnerabilities are found, detailed information about them will be displayed :
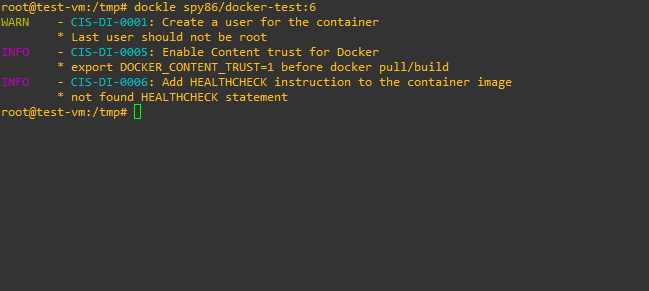
Let's try to run Dockle in Docker, the screenshot shows that the utility works fine:

Key features and benefits of Dockle
search for vulnerabilities in images,
help building the correct Dockerfile,
ease of use, you only need to specify the name of the image,
support for CIS Benchmarks.
Comparison with other tools
, : Docker Bench Hadolint. Dockle :

Dockle DevSecOps
, — Dockle. CI, DevSecOps.
, CI / CD Dockle: