Comments under the fake Microsoft Authenticator browser extension indicate that the reviews for these apps are either positive or highly negative, and this, in fact, makes it clear that it is fraudulent.
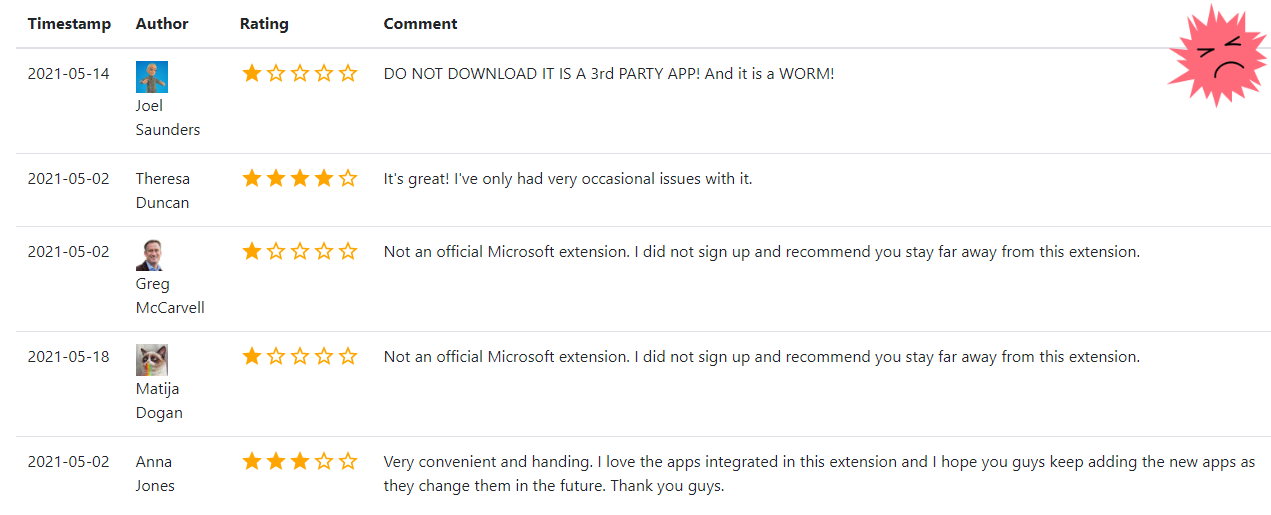
After hearing from our reader about the fake Microsoft Authenticator extension appearing in the Google Chrome Store , we began to investigate the account that created it. Before the extension was removed, it had five reviews under it: three Google users gave it one star, warning people not to use it, but two commenters gave it three and four stars.
“Great extension!” Theresa Duncan's Google account enthusiastically writes . “There were almost no problems with him”
“Very convenient and enjoyable,” says Anna Jones' expansion incomprehensibly .
The Google Chrome Store reported that the email address associated with the account that published the fake Microsoft extension has also released another extension called iArtbook Digital Painting . Before it was removed from the Chrome Store, the iArtbook extension had 22 users and three reviews. As with the fake Microsoft extension, all three reviews were positive, and all were created by accounts with first and last names like Megan Vance , Olivia Knox , and Alison Graham .
Searching for reviewers is not easy in the Google Chrome Store. To do this, I used the chrome-stats.com service developer Hao Nguyen . The service indexes an array of attributes associated with Google extensions, allowing them to be searched.
While studying Google accounts that left positive reviews about the already blocked extensions Microsoft Authenticator and iArtbook, we noticed that each of them left reviews for several more extensions, which were also removed.
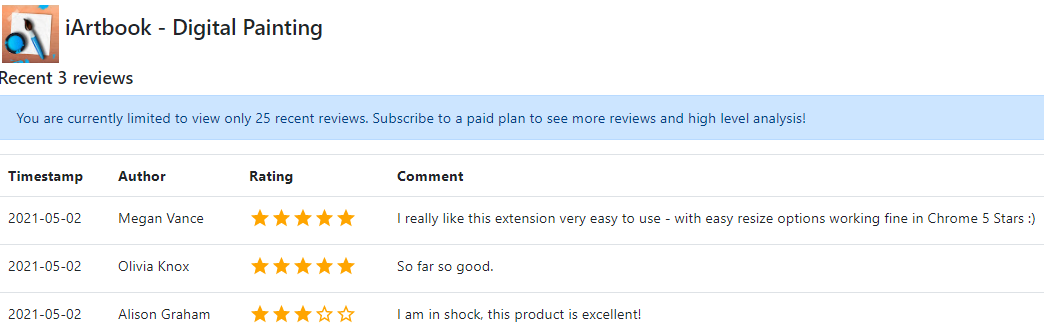
Feedback for the iArtbook extension came from apparently fake Google accounts, each of which provided feedback on two other extensions, one published by the same developer. The same pattern is observed in 45 more blocked extensions.
Like an ever-expanding Venn diagram , extension reviews left by each new fake account led to new fake accounts and extensions being opened. In approximately 24 hours of research using chrome-stats.com, more than a hundred positive reviews were found that are clearly fraudulent extensions on the network.
These reviews, in turn, led to a fairly simple identification:
- 39 , ,
- 45 , 100
- 25 , .
The extensions have been mimicked by many consumer brands, including Adobe , Amazon , Facebook , HBO , Microsoft , Roku, and Verizon . After examining each of these extensions, we in turn found that many of their developers were associated with multiple apps promoted through the same fake Google accounts.
Some of the fake extensions had only a dozen downloads, but most had hundreds or thousands. Fake Microsoft Teams extensionIn about two months of presence in the Google store, it received 16,200 downloads. The fake version of the professional video editing package CapCut received about 24,000 downloads in almost the same period.
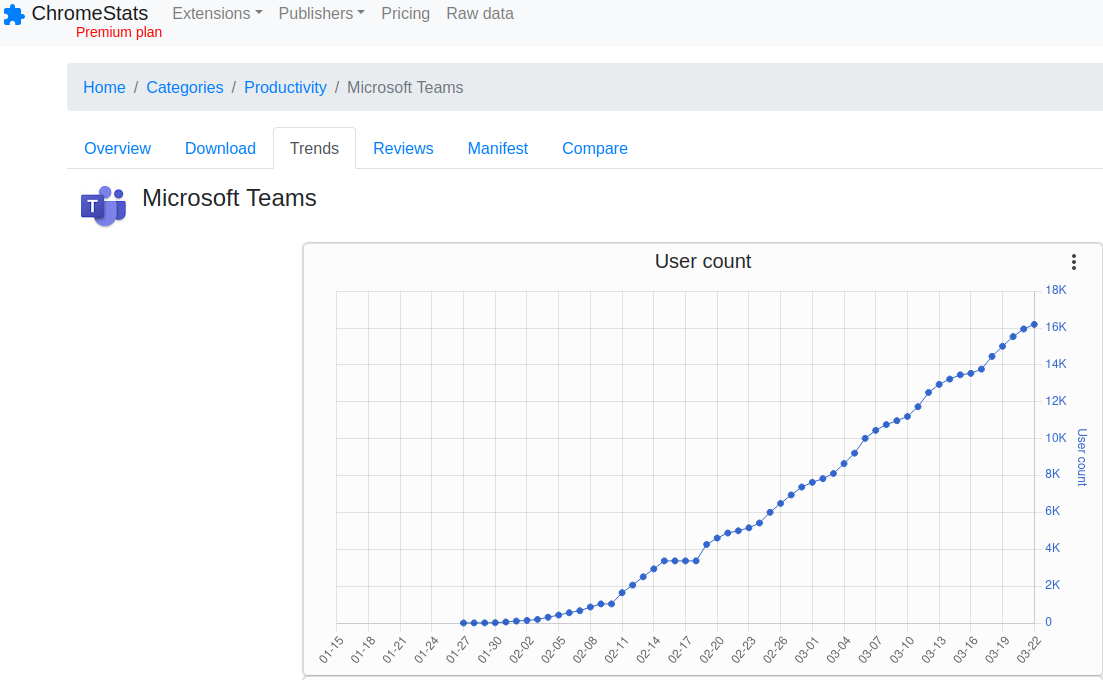
More than 16 thousand people have downloaded the fake Microsoft Teams browser extension in the two months it was in the Google Chrome store.
Unlike malicious browser extensions that can turn your PC into a botnet or collect cookies , none of the extensions examined ask users for special permissions. Once installed, however, they invariably ask users for personal and financial information, pretending to be associated with major brands.
In some cases, fake accounts and fake extension developers in this scheme have the same name, for example, in the case of brook ice- A Google account that praised the malicious extensions Adobe and Microsoft Teams. The email address brookice100@gmail.com was used to register an account for the developer who created two more fake extensions we examined in our review (PhotoMath and Dollify).
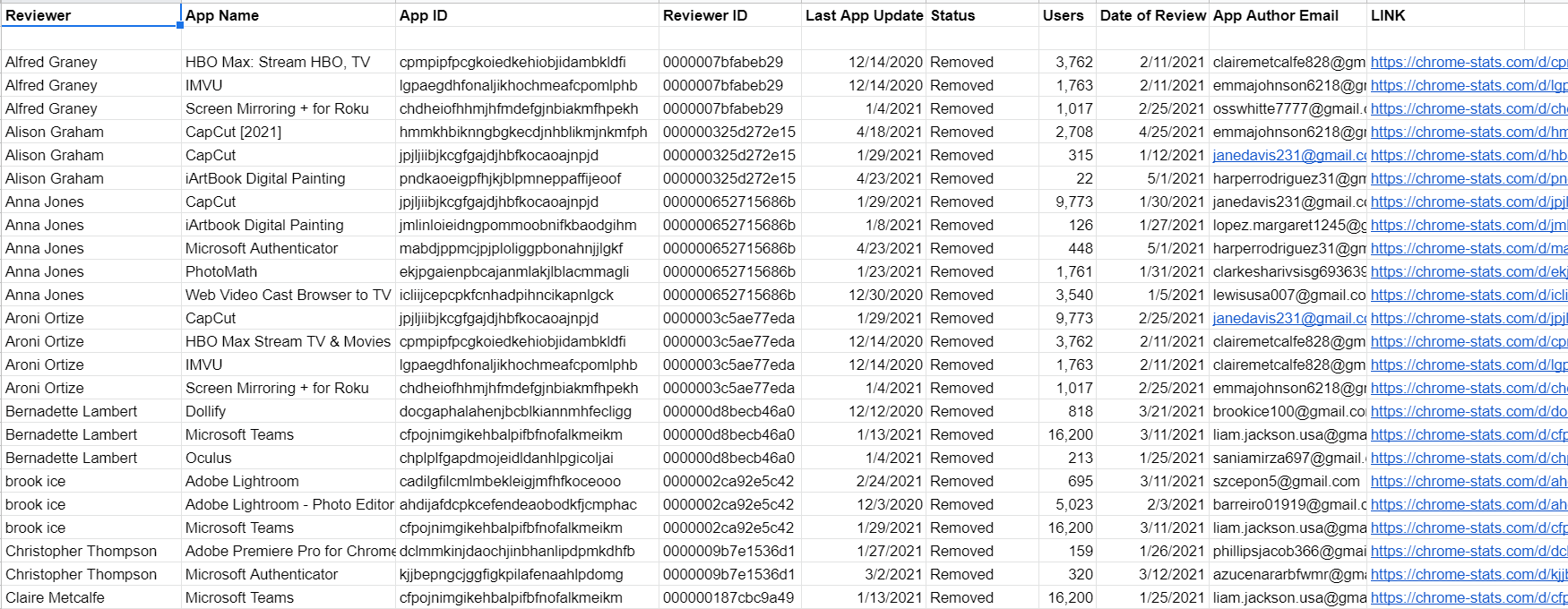
Some of the data that served as the basis for our report. A link to the full table is provided at the end of the article.
As we can see from the above snippet of the spreadsheet, many Google accounts that left feedback on apparently fake extensions left comments on multiple apps over the course of one day.
In addition, Google Account recovery tools show that many developer email addresses associated with the extensions described in this article share the same recovery email address. This makes it clear that the entire scheme is controlled by a limited number of anonymous users. When you sort the data from the above spreadsheet by the email address of the extension developer, the grouping of reviews by date becomes even more obvious.
We shared our findings with Google and will update the article if the company responds to us. Be that as it may, Google has already identified all of these extensions as fraudulent and removed them from the store.
However, we will probably write a post about how long it takes to find and remove bad extensions. In general, most of these extensions were available in the store for two to three months.
I have done this research mainly out of interest. I thought they would be curious to share with others . In addition, I was fascinated by the idea that all you need to do to find fake apps is to detect and track fake commentators. I'm sure the network of rogue extensions is wider than the one described in this article.
As we can see from this story, it pays to exercise some common sense when installing extensions. Even aside from the apparently rogue extensions, many useful extensions their developers stop supporting or sell them to questionable marketers , so it makes sense to only trust actively supported extensions (those that have a critical mass of users that can make noise when something undesirable happens to the program).
According to chrome-stats.com, most of the extensions (over 100,000) are, in fact, abandoned by their authors or have not been updated for over two years. In other words, there are many developers who are willing to sell their creation along with their user base.
Information from this report can be found in this Google spreadsheet .
Advertising
VDSina offers secure VDS with daily payment, the ability to install any operating system, each server is connected to an Internet channel of 500 Megabits and is protected from DDoS attacks for free!
Join our Telegram chat .
