The MITER ATT & CK knowledge base is an extremely valuable tool. It helps drive the development of the entire cybersecurity industry and formalizes the approaches attackers use in their attacks. Based on this database, MITER experts conduct security product testing. The latter imitated the tactics of two popular cybercriminal groups - Carbanak and FIN7, and a large bank and hotel chain became the model targets. During testing, the Trend Micro Vision One TM platform was able to quickly identify 94% of attacks carried out by hackers. In this post, we will share how the study was conducted and what conclusions users can draw from its results.
MITER and her goals
MITER is a non-profit organization that appeared in the United States in 1958. Its main goals are the leadership of federal research centers, systems engineering and various scientific research. Among other things, MITER regularly conducts MITER ATT & CK surveys that help assess the ability of various cybersecurity tools to detect and analyze hacker attacks. For these purposes, the emulation of the methods of certain cybercriminal groups, which are called APT (from the English advanced persistent threat, that is, "developed persistent threat"), is used. These are large and successful teams of hackers who regularly carry out attacks on a global level and have attracted the attention of various services, but so far they have avoided being caught.
The MITER ATT & CK program is not used to assess the quality of software and compile ratings of the most successful vendors. Its goal is to give companies the most transparent vision of how a specific solution helps to detect attacks and specific groups of threats. For convenience, all attacks during the simulation are considered in terms of the number of detected "steps" of the attackers, analytics, which allows you to obtain additional data on their tactics, telemetry and general visibility of the attack. Cybersecurity professionals can use the results of MITER ATT & CK to conduct an internal audit of the infrastructure and find security gaps. They can then match the vendors who have done the best in filling those gaps during their research.Testing also helps to detect overly protected (if it is in principle possible in modern conditions) nodes and optimize the company's cybersecurity costs.
, 2021 , .
Carbanak FIN7
MITRE APT-. Carbanak, , — FIN7, . , , - . , , .
(Carbanak) - , Carbanak . , Carbanak, FIN7 PoS Pillowmint Tirion. , MITRE ATT&CK , .

/. . — . .

, , , . ,
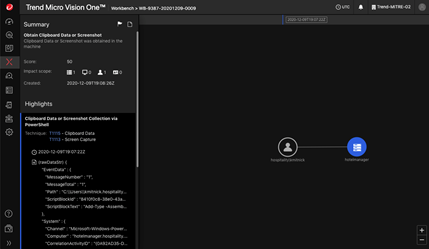
, , . «» , — .

, , , . Carbanak, Fin7 .
, «» — , . . , , , «» .
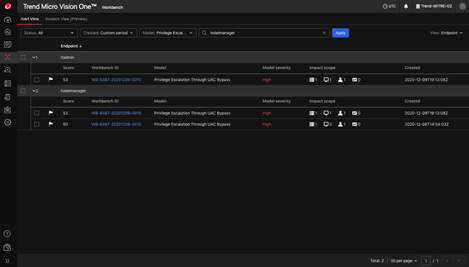
Trend Micro Vision One: . , — , , , .
Carbanak. , , . , , . , .
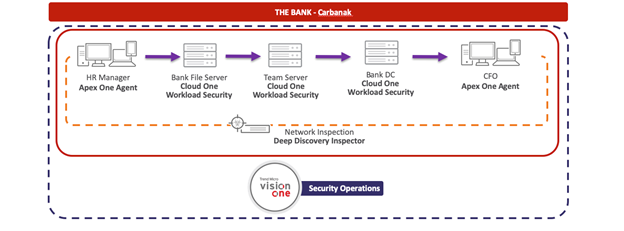
, Fin7, . . , «». -, .
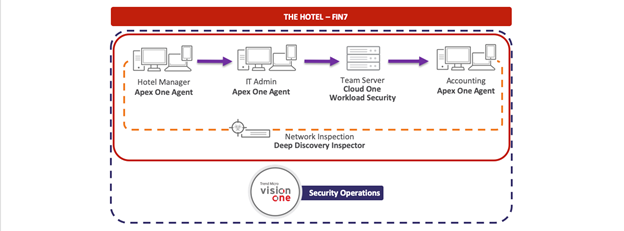
10 96 . , . , , . , , .

Trend Micro
Trend Micro , , . Trend Micro Vision One ( ) :
94% , 167 177 , «» , — ;
, , «», Linux — , 100% (14 14) ;
Trend Micro Vision One 139 , ;
90% . , , - .
: MITRE ATT&CK
, MITRE ATT&CK . :
« » (None): , , MITRE Engenuity ;
« » (Telemetry): , , ;
« » (General): , , ;
« » (Tactic): (, , );
« » (Technique): , , (, Credential Dumping).
, , , . , MITRE ATT&CK . . : , , , «».

, - «» . , , . Trend Micro . , , . MITRE ATT&CK .
Trend Micro Vision One , . 167 «» 139 , , .
. 17 29 , . Trend Micro , 90% . Linux. Trend Micro Vision One 14 .
MITRE Engenuity ATT&CK, . Trend Micro Vision One .