According to history, the owner of the laptop gave us his IP address, SSH key and login. In the SSH config, access only by keys was configured so that the participants could not waste time guessing the password. The public key was like this:
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIDMyK0W5OMnzJFszo5ClCVbqAQ6s1NWYeast+WjIyWF7
The main goal was to get on our friend's laptop and download an NFT gif with a cat from it until the piano falls on the laptop. But soon, after the start of the operation to rescue the cat, it turned out that hackers had already trampled on the laptop, so the participants could not get on the laptop - the private key did not fit. A group of hackers called themselves sp0rk b4gel
They were interested in the source code belonging to the company where the hero of our story worked. They leaked the code, and along with it they accidentally grabbed the cat, without even noticing it. After that, hackers began to blackmail our friend, threatening to publish his work, which threatened him with legal prosecution.
To securely save the changed SSH key, the hacker group divided it according to Shamir's scheme into 10 parts, of which 8 were necessary to log into the laptop. 9 keys were distributed among the "hackers", and the 10th, bonus, we inserted outside the plot (more on that below). And the participants had to solve several problems, receiving for each of them a fragment of the correct private key. The tasks themselves were in the form of random "blunders" by hackers.
Since the participants had no other leads besides the name of the hacker group, they had to turn to Google first.

In the search results, they found the hacker manifesto . The manifest text on textbin.net was successfully indexed by Google and found by title . At the end of the manifesto, the nicknames of the hackers are indicated, for each of which it was possible to find the corresponding task - "digging" under the hacker, because they simply would not give the changed key, right?
▍ Task 50n1c4h0
Part of the key:
ssss-01-5dc6284446d3f3ae3d2b9e12167a118708f08686474e6471d178703938e3bc043796c79f72853a2cd77d2e956e41490b9b961a526f4911527bfe14c24f0022ce31a52f5fc118ca1dd1c1f0
Job category: crypto, re
Google nickname, as a result we find a photo album (links to it on Pinterest or Juxtapost indexed during the quest ) and the site https://50n1c4h0.netlify.app/ according to one of the photos in the photo album, which recommends using this site:

The site is a "protector" to protect confidential data. Inside it is a homebrew 16-bit virtual machine with bytecode, slightly covered with an obfuscator. The program for this machine is an implementation of the RC4 stream cipher with a key
4c524338f5169e91e0cc05971f5b9b6e
(hex). The photo from the photo album shows the result of the protector's work on the desired part of the key (we decode from the QR code :)
6efb5c8eaf511770715681cac161b49f45ad9c12837ae41b35639653fcbc03e55e16a5d4953ba1fee6f8d4a3606b0751fd6d6a0b8e14200f4ed78943d4553d0bebfabcb8c0e30fa3580ab08899edbadd878b6e7c033febf6679558d1511c74f8d9ca54ef4c646a08f1bfeefe1a3b7884d3f2c94ee14649dcdc11591b8a8b0a005c80a8ce4b7c3dde988d59065ec574ad194fdc204137fc6748994942237e
.
Since the algorithm is reversible, you can use any implementation of the RC4 cipher, substitute the key and get the original plaintext - this is a reverse way of solving the problem.
It was possible to go another, cryptanalytic way: noticing that the output byte of the ciphertext depends only on the position and value of the input byte and does not change (for example, byte
0x41
at position 1 will always be converted to
0x39
, byte
0x42
- to
0x5F
, etc.), it was possible to select the input data by byte for the output known from the QR code, thus also obtaining the desired part of the key, byte by byte.
▍ GemmadohA Quest
Part of the key: Quest
ssss-02-8e8425381bc24f44cbdefdae711d91c0a733350e949827f66a0ee00a5301afc3f68aad0a69e1b3d93465e70db0675089dd27fd993efe39bc881ad00b19d6055b856e9853af0b681213cb81
category: almost pwn
We could not leave aside the last quest (read more about it here ) and decided to use the Sokol studio website as a tribute to those participants who tried to save money from the jaws of the gluttonous shredder day and night.
We go to the site https://ooosokol.ru/ (a hint of this project was in the message of hackers). We see that the site has already been hacked by the hacker GemmadohA. He also left a web shell there (there is a comment in the deface page, so as not to forget). Login and password for the web shell:
gemmadoha:gemmadoha
almost like a classic one
admin:admin
.
The hacker also created an account on the hacked server. The private key from it was not removed from the server (
/home/gemmadoha/.ssh/id_rsa
), since it was generated on it. We read the private key with the web shell, go to the ooosokol.ru server via SSH.

We see that the hacker is still hanging (hint "what if the hacker is still on the server, he just recently hacked him" in Discord) via SSH (with IP 194.87.236.30), something is digging in the files. The SSH agent socket is hanging for him
/tmp
, you can find it by simply looking for all the files owned by the hacker (and in order not to waste time trying to elevate privileges, Discord was given a hint "what you are looking for is not on this server" ).
Using the command:
SSH_AUTH_SOCK=/tmp/ssh-5j3MjI6mby/agent.23577 ssh gemmadoha@194.87.236.30
we use his SSH agent against himself (we hack the hacker, a prompt “hack the hacker” was given in Discord) and go to his server. There is another secret.txt in the home folder.
▍ Quest thereane777
Key part:
ssss-04-44ed995def2ab783d02fdd783c528a347f29adc494130b65827721002fe47d0b5d3f29cf55620b596c49f23652cb4648cb3c7b5c605d5a9e2f0f3c46f32894c9980d028a7e7b33f8c8c48b
Job category: misc
Google nickname, we get into topics on hacker forums where this hacker is registered.
The hacker profile description contains a link to Yandex.Disk for “useful information”: https://disk.yandex.ru/d/kQ9MPqO3anRiTA
On the disk, among all useful programs (ICQ clients), there is a password-protected icons.zip archive. Password from him:
v1pPGOuPS8HXFrS
(long and hard to guess). Without knowing the password, you can see that the archive contains two .png files (pictures) and an interesting secret.txt file.
The task is solved without knowing the password using a little-known, but still relevant zip method known plaintext attack with bkcrack (successor to pkcrack ). To implement this attack, the archive contains two random PNG images (their contents are unknown to the participants, and this is not required, but you can also find them on the Internet), since their header, the first 16 bytes of which are the same for any PNG file, and is sufficient (only 12 bytes are enough there, and even not necessarily sequential) to carry out an attack.


As a result, we get a ZipCrypto key
dd8d62b4 83fed681 6761bbc1
, with which we open the archive and get the contents of the secret.txt file, which contains the required part of the key.
▍ Job y4n4naby5
Part of the key: Task
ssss-05-9b5f9fef9cf5d85d206ed65b4a645888f6409b79c956309a2f1860daa0c4d8cd23113fdcee5fa5575ff7e9398d061eed52c62eee743f77c569c861fb1ade55a2149dc05a9f2e4f2e18bad5
category: forensics
Google nickname, we find (during the quest there was) a topic on the forum asking for help in opening the Wi-Fi network named "DIR-615 y4n4naby5" (apparently the Wi-Fi of the desired hacker). The report is attached to dump traffic , which is necessary for the selection of the password to the Wi-Fi network (fourfold WPA-handshake).
The forum thread contains a dump of Wi-Fi network traffic, and there is even more information in the dump than is necessary to guess the password. The password is selected according to the old, very well-known (it is even included in the most famous Pentester distribution Kali Linux) and used at the first opportunity for almost any selection by the RockYou dictionary . This password is
fireheart79
(was successfully picked by a forum member). Selection will take no more than an hour on a modern processor (no video cards are needed) using the same hashcat .
Knowing the password will also allow and decrypt "unnecessary" WiFi traffic using the same Wireshark, and see what kind of data the hacker was transferring. In addition to garbage (data exchange with Alibaba and Google servers), you can notice an interesting connection via FTPS (FTP over SSL / TLS) to the soclose.numbers.com server (such a name is not registered, it doesn't matter, but the IP is generally "faked" on one from Google IP). TLS is known to be an encrypted protocol, but the parameters without any additional special settings (the server was vsftpd , and the client was andftp ) turned out to be like this (TLS 1.2 without using the Diffie-Hellman shared secret ) that only the server's private key is needed to decrypt traffic from the dump (if the Diffie-Hellman scheme was used, this would be impossible without the client or server memory dumps). The server key parameters (RSA-2048) are chosen so (p and q are close to each other) to be susceptible to the Fermat factorization attack . This is hinted at in the server name ("so close numbers"). The attack is carried out instantly using the same RSACtfTool , and gives
133205738301055492415292455053957573761950370019465363197330018804911429748841372623440097998280840848577224963374030102174633719338576372412863025595291812898461741802590180711710007911941796139236802646966981084378380345280502967196789430710224184344783160032007107024729298554505470658071546418304653261811 p =
q = 133205738301055492415292455053957573761950370019465363197330018804911429748841372623440097998280840848577224963374030102174633719338576372412863025595291812898461741802590180711710007911941796139236802646966981084378380345280502967196789430710224184344783160032007107024729298554505470658071546418304653247279
A, respectively, and the private key:
-----BEGIN RSA PRIVATE KEY----- MIIEoAIBAAKCAQEAjI7G8TjcvnASyKj8jlnIC8mj2BjCISJRKa91xVC2ATA6dgJQ Vq12wxCJ/4tvG/GHv4mtTF3T5EASTUD+KSIjGPxakcXFEF13VfNS6C0TwyBH5+yZ /f5AdzTPDqF2ScZQ1J461NVOscZN9eXU5JGO/b+NpP/QZ2Od4E3WBTfP1zpBSAno VOLs3TjWSAfW1AY6uEBS2NKT0VMRSya2u57ZdPkC2+pH1NG9GW6CR4KR2RVT2vdF COEyMNSixhklBdVNNIHkZYQH0NMt4FUfY5bE9W6wBvUtzIEVqNXCQv3IC6tmPYIg vy8FquGNln1mFr7+H4TMaoIlz4LYdK2UwtBanQIDAQABAoIBAHTRZT6uh6gu9S2Y ZO7aZ4yEdYvwZ8eqAdKnZTYssleigbP6kFK5sG7GnCqq9BlBUBU8k69Ye/bD2XIj hhkhqhHmClAFEpdbVwc0R793V2lgtuJmnkWevm1UkpISV4FRNXTAXRzue4z8x2aL MbkV0MXMIij0A30qKdh2WF3V2QOCx9dLjuL5AZ6B4keOYz3mKbp1fzU/xWzEgSaJ qBtcf4qZcj/c3Kov+3i3/WDXu4phCYVi/JpBok0zTKiMLFJ+xqISabd8yZJb5hVi VSu9YRyu4H1rg3N6a5Ukdgp56F3kW4sur6KsftQmLShdgGctF+SBF7ZiKcfkT9oX tQ0guvECgYEAvbD27ue9r5qmuBX4WdqtbM6tEGm5q914wKnpbTb1ZNp2fzoSU3ti cfpUpxvsFQy8P8SB0Lv6sTzC6wfPhGVMnXa4HE5NrZ4jtXdk1dxaC/TvaYGeHpTj /fGARDDRXBlbXVFgnPnC3EOUATWD5obWtaJg5HOSZwMFJB1ehPWc+/MCgYEAvbD2 7ue9r5qmuBX4WdqtbM6tEGm5q914wKnpbTb1ZNp2fzoSU3ticfpUpxvsFQy8P8SB 0Lv6sTzC6wfPhGVMnXa4HE5NrZ4jtXdk1dxaC/TvaYGeHpTj/fGARDDRXBlbXVFg nPnC3EOUATWD5obWtaJg5HOSZwMFJB1ehPWcwy8Cf0Kv9CAJWKZjuDj/gFAWkOGv xyf+A0holAsnsOi0aZELPJ19zPOMbQ+k8h3NszGzSHsimoDHlVq6Acye8lWZR1YU ZqWM4cIn1mX1k32b+gw6D/EHoI8fyQd935oZj4DRaU1lTpHhPKAzIdVK+xQQU2uH qoimGNIePbB0osYbkxUCgYBwECTBnNx96pJFvIz8oGjGGA873AnZk7xrrbV+VPKC A2Hv5aG/+et9xFLQanl9Mgngbjn206bVoDzS1slswN+TQvifmE7hm8Qix4clpMj5 uVja7r03+eP7OPn6zxBQJZbJOXMnKZJJyA6e7DuhK9WadnRhYjmCa9FUtZkKWYOj 9wKBgCzJOfLSMgROqzznGTesCXueTI0NnecG7WvZehtRc0LHEAiC12e9YvCqj7Ao JsZBfec+IGk2vX8AunUKvYUZL2J7WfCyp57Kj1YgnEyikTVPsOEwjb5lALK1FwIT xTH7xPD8OVIW0eQPvmhczoMKYPQG0mtZk+QkPr9dv0YcvwNB -----END RSA PRIVATE KEY-----
With it, we decrypt the TLS traffic (again with the same Wireshark) and get the contents of the secret.txt file uploaded via FTPS, which contains the required part of the key. That is, we perform two steps: hack WPA and hack TLS.

▍ Job m0x143y
Part of the key: Task
ssss-06-ad1a38b7f24f17489ef204207f7c3b8cf17032b316d5cb9d123619d209676ad6e7ba567c33ac41376876265a70f45f73a991cb6e9100b0df4b8b102a51a147dc6d641cf8bbbecd07321e0b
category: forensics
Google nickname, we find (during the quest there was) a topic on the forum with a request to check the error when opening a TrueCrypt volume:

A forum post says that there is a problem opening a specific TrueCrypt volume. A screenshot of the error and links to file sharing services are given , on which the container itself and a memory dump are located for debugging the problem. Password on the length of the container and nepodbiraemy:
uBocLXywprQ9VJ6jxpYP
. However, there is a memory dump, and, for example, using the truecryptmaster volatility plugin, you can extract the TrueCrypt master key (truecryptsummary will report that the volume was mounted and the paths to it, but truecryptpassphrase will not give anything, because the default TrueCrypt setting is not to cache passwords). It will be like this:
Container: \??\C:\Users\m0x143y\Documents\encrypted.tc Hidden Volume: No Removable: No Read Only: No Disk Length: 66846720 (bytes) Host Length: 67108864 (bytes) Encryption Algorithm: AES Mode: XTS Master Key 0xfffffa801b57f1a8 84 2c 3d a3 24 7d 9a 37 d6 53 7e ac 1f 3c 2c 7f .,=.$}.7.S~..<,. 0xfffffa801b57f1b8 de 61 85 de 81 a9 84 2a 4d 3c d9 57 df 81 c7 29 .a.....*M<.W...) 0xfffffa801b57f1c8 8f 56 fc e1 80 4e cf 2a ce 44 5b 9f a6 10 6f 98 .V...N.*.D[...o. 0xfffffa801b57f1d8 15 e2 50 1f 49 38 f0 a9 62 a7 96 4a db d3 53 9f ..P.I8..b..J..S.
The KDBG address for volatility is
0xf80002a45120
, the profile will do
Win7SP1x64_23418
(i.e.
volatility --kdbg=0xf80002a45120 --profile=Win7SP1x64_23418 -f mem.raw truecryptmaster
). Then, using, for example, MKDecrypt, you can decrypt the container in its raw form using the received master key (without knowing the password, it is no longer needed). For what? The file you are looking for
secret.docx
(made so that it does not go entirely into memory in MFT and does not greatly simplify the solution due to its small size) removed from the container (hint "there is nothing important there anymore" in the piano), as promised in the message (and in Discord it was a hint is given "was there any important information?"), there is only any garbage (pentest programs and empty Monero wallets). However, with a "raw" decrypted container and almost any program for recovering data from FAT partitions, for example, R-Studio, photorec or DMDE, the file "deleted" from the encrypted container with a part of the key is restored.

▍ Task 3r1or0l3r
Part of the key:
ssss-07-7931b90aace8673aa4d6162c3e729b7c89152de5e9bed9ab9fb9ff8eb1fbe8307bd985f728de99123980abee36d0495fbad93cf52d990a9a0fdbb82b62c7b141f3642e051dfa8112b56833
Category of the task: stego
Google nickname, we find his "creativity": https://textbin.net/hzbmlkhzjg

Text steganography by the method of chains (which was hinted at in Discord "connected by one chain" and "the text is connected, not random, makes sense" in the video) Markov: An Approach for Text Steganography Based on Markov Chains (hint in Discord 1409.0915). Implementation of this idea: http://jthuraisamy.github.io/markovTextStego.js/
In the text of "creativity" (the first chapter of the cyberpunk novel) there are obviously found proper names, for example, "McCoy Pauley" or "Bobby Quine", taken from the first known book in this genre: "Neuromancer" by William Gibson... As a specific text corpus for Markov chains, the first chapter of this book is used (which is hinted at in the title of the "story", and there are no other words and sentences except from the first chapter), freely available here .
We enter the text of the first chapter of the "Neuromancer" as a corpus, enter the text of the first chapter of the hacker's "creativity" as a ciphertext and get the required part of the key. Yes, with steganography you always have to guess a little and pick up options.

▍ Quest VenchamoSs
Part of the key:
ssss-08-6fe2d9b400840e44d5f20e15043cc4739ed97879110790350dd2e5e67f0b56b6e11607bb9e99f0cb1c57ede4d309e9f85363168f2ff1d2f316c9c89a8179110a759140a911075a0547f908
Job category: osint
We find (the same osint) the hacker on the same github: https://github.com/VenchamoSs .
The second nickname is indicated on the github - aka welAnty. The turnips you like are gpg, which means that the hacker uses and is interested in PGP / GPG solutions. We find a hacker on keybase.io (a well-known site where GPG users exchange private keys), there is a public key with email welanty@forexrobotexperts.now.im . And also an instruction not to use the old key with ID 0xF6B246D4. If you search for this ID on the most famous and oldest site for key exchange, then you can find the same old key with email eukx@forexrobotexperts.com . According to it, the ANTIPUBLIC leak (included in Collection # 1 , the largest compilation of leaks in the last few years) has a password
N4syZRJ843.
We use the password on SSH (the only service open on the server) welanty@forexrobotexperts.now.im , we take part of the key.
▍ Job -velashic-
Part of the key:
ssss-09-be6c314465393225739da1e65200657df7d4a15e66e606c9619ef51a88d5b4015353ac2f089f3dfcd3f86757e89e404dfc2552fe59218310f94b8834d7a82d47b68669aa31eb0860a95d26
Category of the task: osint, forensics
Google nickname, find the topic on the Cyberforum forum in the section about Arduino. Everything is described there: the hacker asks for help due to his incorrectly working Arduino and attaches a dump of USB traffic, because he suspects that it is "too Chinese" and something goes wrong when uploading the firmware. The firmware code should play the songMetallica's Master of Puppets. In addition to uploading the firmware to the Arduino, the dump also included communication with a USB flash drive (a common situation, since there are fewer USB interfaces in Wireshark than USB ports on a computer, because their number corresponds not to ports, but to USB hubs on the motherboard). A file with the same song is read from the flash drive for listening, and the password-protected secret.7z archive is also written. During extraction, we see that there is a write to the NTFS partition on the USB flash drive, and NTFS has a fixup concept , so do not forget to correct (as the hint was given in the piano) 2 bytes at offset 142 (hit the sector boundary) from
0600
to
708f
according to the USN / USA table (Update Sequence Array) FILE records. The password to the archive is guessed from the obvious interest of the hacker - the group "metallica" (also in the well-known RockYou dictionary ), the archive contains secret.txt with the required part of the key.


▍ Quest chyrgerillll
Part of the key:
ssss-10-132faac795e60a0f9457167c3db3f1b1efd25cdd5049329e68fd43ce884e606d17fb14e70c897bd3308aaa213443952522c95b2e3c29d68dca9611a12e6f3d8a660113370c2f6753fc0643
Job category: crypto, re
Find a github account with a single repository: https://github.com/chyrgerillll/mymnemonicgen The repository contains an implementation of the generator of mnemonic phrases used to remember access to crypto wallets "in the head" according to the BIP39 standard . This standard is used in almost all cryptocurrencies and in almost all implementations of their wallets, not only in Bitcoin. The generation of private keys for wallets from these mnemophrases is described by the BIP44 standard , which is also used by most implementations of crypto wallets , which is hinted at in the repository... Seed data from the entropy stored in the mnemophrase is generated for it according to BIP32 (a list of all three standards in the first tip from the video). An example of how all this is generated can be seen here: https://iancoleman.io/bip39/ (the last tip given in Discord; the standard generation path used is also suggested
m/44’/60’/0’/0/0
).
There, in the repository, there is also the address of the wallet in the testnet Ropsten of the Ethereum cryptocurrency, for accepting donations to continue the development of the generator. There are several test broadcasts on it.... The repository also contains a hint of what is required to complete the task: try to break the wallet generated by this homebrew implementation of the generator and let the author know about it (or even "take away" test ethers). The hacker's email ( chyrgerillll@rambler.ru ) required for communication can be found by cloning the repository to yourself and seeing how it was lit up in one of the commits (also an unobvious and frequent problem for git users).
The generator uses a standard Python PRNG (Mersenne vortex), as a seed for it - the current time. It is taken from the transaction with the deposit of funds (and selected ± 30 seconds, since the time on the hacker's computer might not be perfectly correct, which was hinted at in Discord - only 60,000 options). Thus restored state PRNG (seed 1621586183221, 05/21/2021 08: 36: 23.221 GMT) to give the desired seed-phrase «try process bubble call spell peanut pear valve boring stumble inject turn», and through it and a private key (s
0x702ca34414cc046ed2f63857a098b166541c3f477d7679a19e51de901d0df471
), which gives access to the wallet.
If you send the received information and the key (as confirmation that the generator is really vulnerable) to the hacker by mail, then he will offer a deal: the participant no longer touches his wallet, but in return receives the desired part of the key.

On the third day of the piano hovering, we gave the participants a hint that helped them solve this problem. The clue is encrypted at the end of this video:

An interesting fact: the actress was not going to break the plaster skull, but she got used to the role so much that she did it very expressively, successfully reviving the video. It's good that the number of skulls was habitually reserved according to the N + 1 scheme, and we were able to record a couple more takes.
So, we decided to take this funny moment, loop it and encrypt the hint into it. An audio - encoded RTTY message (to which Discord gave hints that the sound is similar to the "sound of an old modem" or even a "teletype") could be decoded, for example, using the Fldigi program, well-known in narrow amateur radio circles :

The message thus gave hints on tasks for the hackers 3r1or0l3r and chyrgerillll.
▍ The result of completing tasks by the winner
If you collect the parts of the key obtained when solving tasks in the ssss program (it implements the separation of the secret according to Shamir's scheme, a hint of this program is contained in the text of all parts), then the participant receives a link (encrypted pastebin): https://0bin.net/paste/YrFxYqMg # ZVK78BWtOhtncw3-xwJe9dw5rGBOboTBOJhEaop8tge
This link contains the private part of the key required to log into the laptop.
▍ Bonus key (10th).
In the post about musical monograms , we have a description of one of the encryption algorithms (German method, 18th century). The task is simple: the participant needs to dial the encrypted RUVDS monogram on the piano:

On the website, on the keyboard, we had the following inscriptions:

In order to dial RuVDS, it was necessary to play the following sequence on the piano:
4 7 1 4 5
The result of this will be a message that comes to the Telegram of the one who played this melody:
“Congratulations! You cracked one of the 8 parts to reveal the secret (SSH key)!
Here it is: ssss-11-2ff9228ea4b6b1fe9361a28e506ca2d35699652cc2a5838d185b075ebe9b60ce4d6e1345f6a0ebe55f5a097218265bb35a3fea2632cc569a5bb64f207591138c71

Answering the questions of the participants, yes, it was a bonus key, its presence is not necessary for the completion of the quest, so it stands out from the general scenario of the quest's narration (lore).
Note to the hostess: the term "lore" comes from the English word "lore", which in the context of quests means "knowledge, tradition".
We added a bonus key in order to give those participants for whom the main plot is too difficult to try themselves and get at least some key.

In addition, we monitored the participants' progress in the quest on Discord and gave them additional tips. If the participants guessed to play the coded nicknames of the hackers on the piano, they received such messages via the Telegram bot:
1 5 5 1 5 1 2 3 (-velashic-, task 9)
“Well done! Here's a hint for the nickname -velashic-:
check the integrity of the extracted archive.
6 1 3 2 5 4 4 or 6 3 4 (m0x143y)
“Well done! Here's a hint for the nickname m0x143y:
Before posting on the Internet about his problem, he said that there is no longer any private information ...

▍Winners and prizes
We have already announced the names of the winners who managed to download the cat. But after the fall of the piano, the participants had five more days to solve all the tasks, this time only out of sports interest. And we congratulate once again everyone who did not give up and also got to the gif with the cat!
Made it to the end
Alexander
not-alone
lofarter
Herman
Ildar
not-alone
lofarter
Herman
Ildar
And also, according to the results of voting in Discord, we decided to reward the not-alone participant for their great help in solving problems together: we give him a certificate for $ 200 for renting a virtual server in any of the 11 RUVDS data centers, as well as a box of our branded foam Smart Admin.
To all winners who reach the end, we give a promotional code for a 50% discount on Hacker .
❒ For further prizes please refer to @Johurn .
And finally, we want to share some funny quotes from the participants:




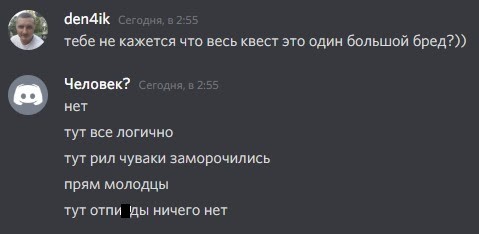
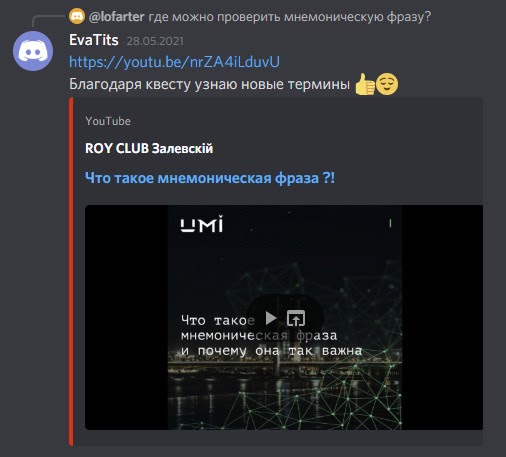
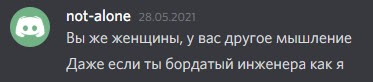







A few more funny pictures from the discord:







