
Software reverse engineering is the procedure for obtaining information about an algorithm. At the same time, obtaining this data directly depends on how much information there is about the application in the documentation, and on what method was used to create the file. It gets even more complicated if the algorithm borrows fragments from other applications or the operating system. This article will discuss the mechanisms that are inherent in the Windows operating system, thanks to which the process of reverse engineering can become a very complex process.
- . , , . , / . , .
- , , . , , , , .
Windows , . WinAPI. , , .
WinAPI , , , , . , , . Windows . , , . Component Object Module.
COM , — . Windows:
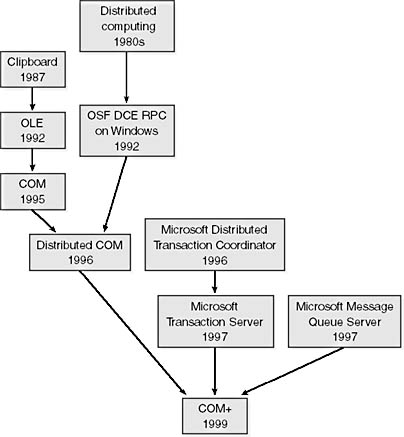
, . , . OLE, COM+, DCOM, , .
, , , 22 . , , , , .
COM . , . , . .
OLE - . , . Excel Word .
DCOM - , COM .
COM+ - , . COM, , . , .
, . OLE. , . .
. docx , , , . : , OLE , "word/embeddings". :
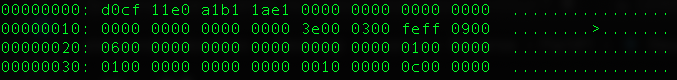
, oletools.
OLE , . oleobj, , txt . , :
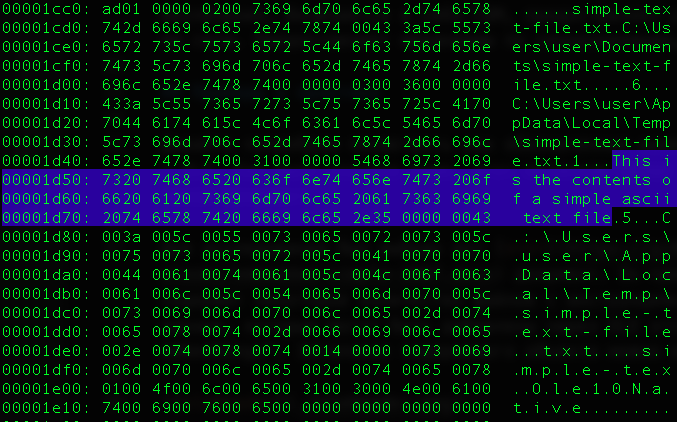
COM - , WinAPI CoCreateInstance. - COMView. :
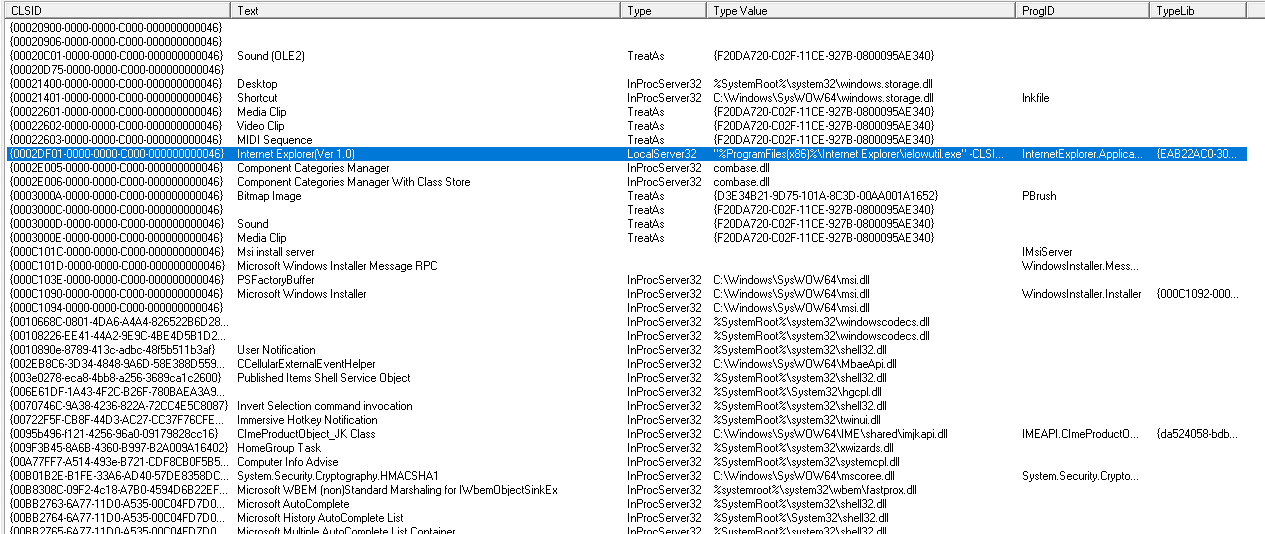
, , COM .
COM+? COMView , IUnknown, COM+ . :
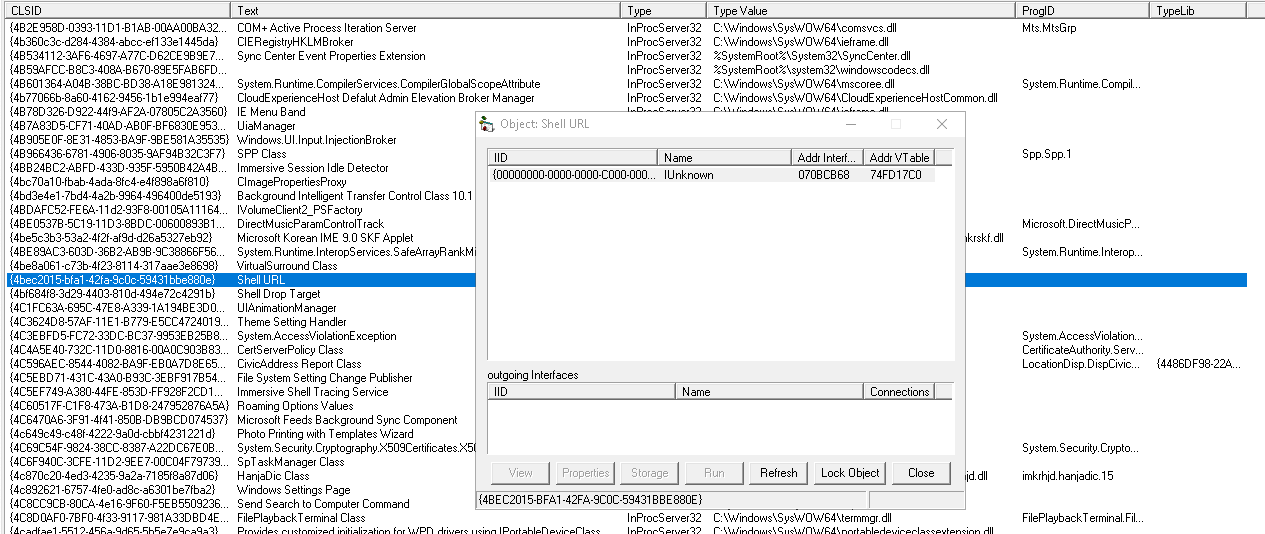
, , . , COMView.
"Reverse-Engineering. Professional". , , .