Traffic interception problems
In the process of penetration testing of mobile applications on Android, it is often necessary to find out how the application communicates with the server, what addresses it interacts with, what requests look like, what data is transmitted. But it is not always possible to do this.
Nowadays, the HTTPS protocol is used to communicate between the components of web applications, which is based on the HTTP and TLS protocols. It won't work just like that to intercept application traffic. it is encrypted. You can, of course, use a proxy server that, using its certificate, will be able to decrypt application traffic and see all requests. However, application protection tools do not stand still. Many mobile apps use SSL Pinning.
SSL Pinning is the embedding of an SSL certificate that is used on the server in the mobile application code. Thus, the application does not use the device's certificate store and will not work with the certificate that we slipped into it.

Application protection methods
In order to understand how to bypass protection, you must first figure out by what means this protection is carried out. There are several ways to do this.
Trust manager
For this method, you need to add a certificate file to the application files, then create a KeyStore and add our certificate to it.
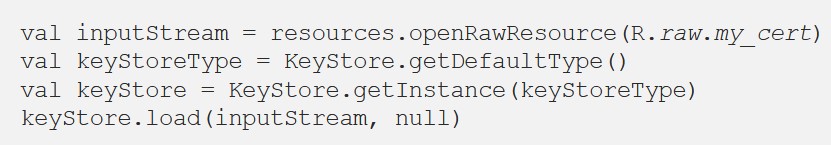
After that, we create the TrustManager itself, which will work with our KeyStore, which contains the required certificate.
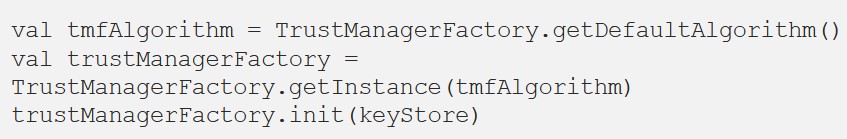
Next, we create an SSLContext that our TrustManager uses. Then we specify for the URLConnetction the SocketFactory from the created SSLContext.
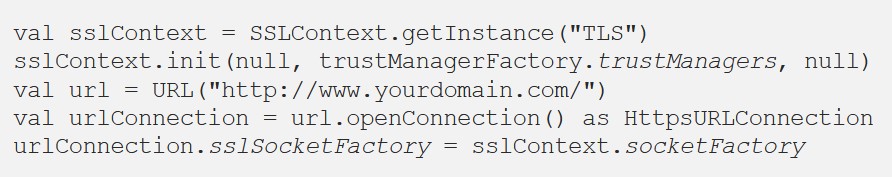
The main essence of this method is that we directly use the certificate file itself in the project, and then create a TrustManager that will work only with this certificate.
API , .
OkHttp CertificatePinner
OkHttp. CertificatePinner, fingerprint .
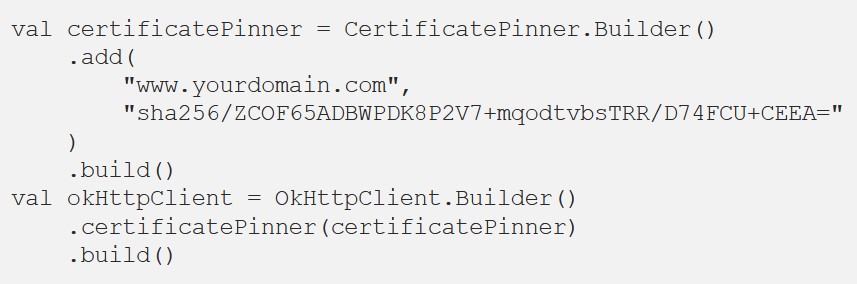
fingerprint , , .
.
Network Security Configuration
Android 7.0 . res/xml/ network_security_config.xml, fingerprints, OkHttp.
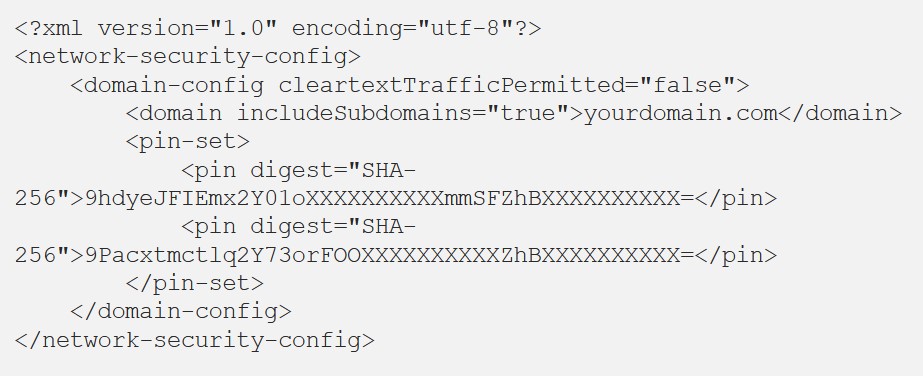
AndroidManifest.xml android:networkSecurityConfig.
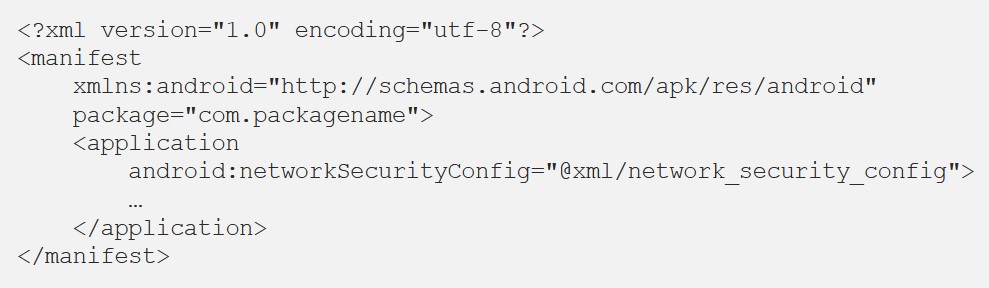
, .
Frida
Frida – . , , .
SSL Pinning Frida , TrustManager, . .

CertificateFactory X509Certificate .
FileInputStream BufferedInputStream .
KeyStore – KeyStore, .
TrustManagerFactory TrustManager, KeyStore.
SSLcontext – SSL, factory sslSocketFactory.

cert-der.crt, , .

keyStore, .

trustManager, keyStore .

Frida. SSLContext. , , . . , , TrustManager . , .
, TrustManager, , ( a , b TrustManager).
Frida , . Frida , OkHttp CertificatePinner.
– apk . , .
, Frida, frida-server , .
apk
, , SSL Pinning, .
apk . smali . Smali – android-. .smali , .
apktool. apk, Visual Studio Code ApkLab.
smali, Java-, . , .
ApkLab . .
: checkClientTrusted, checkServerTrusted, getAcceptedIssuers.
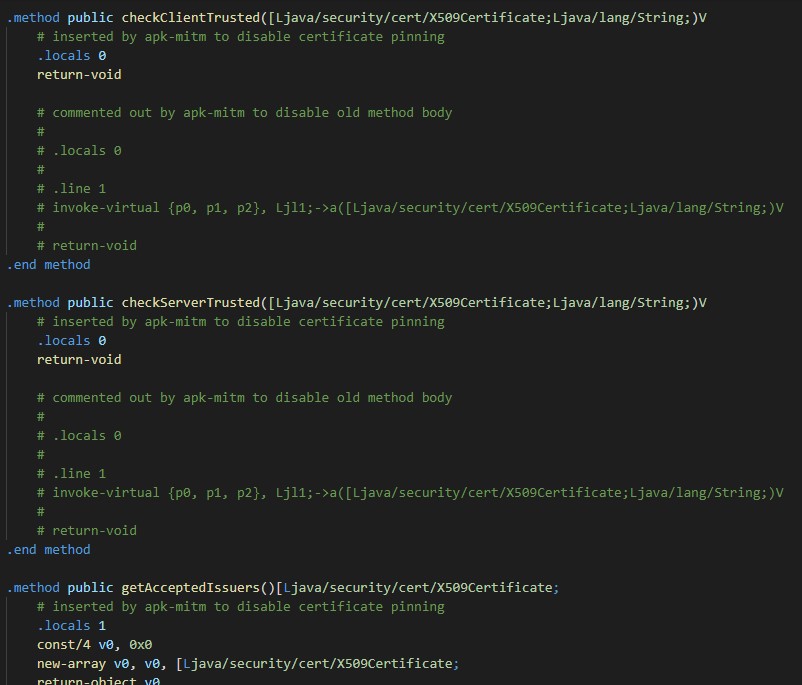
, , , , , . Java- .

, . mo9499a ( - ), , . , , , , . . , , .
getAcceptedIssuers . , , . : , keyStore ( m7931a), .

, .. . , - , , , smali. . - -.
OkHttp CertificatePinner. , OkHttpClient CertificatePinner. smali , , CertificatePinner OkHttpClient.
NSC (Network Security Configuration)
SSL Pinning.
, NSC, . NSC base-config domain-config.
base-config , .

domain-config .
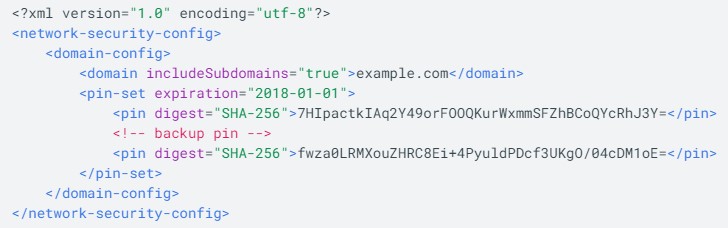
<domain-config>.
ApkLab NSC .
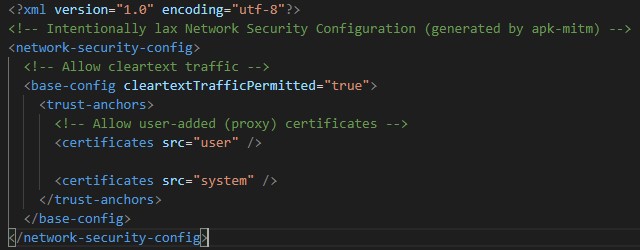
, AndroidManifest.xml.
, TrustManager, KeyStore, . KeyStore . .apk KeyStore /res/raw, /assets.

, .
, SSL Pinning , , , . , , , , , .
Frida , , . , Frida.
apk , SSL Pinning. . , , .
Network Security Configuration , . SSL Pinning , .
KeyStore . , , - (, -).
|
, |
Frida |
TrustManager, OkHttp CertificatePinner |
APK |
TrustManager, OkHttp Certificate Pinner, NSC |
NSC |
NSC |
|
TrustManager |
|
|
|
Frida |
,
|
, , Frida |
APK |
|
, |
NSC |
Android 7.0 |
, Difficulties can also arise if the application is protected from modification. |
Certificate file spoofing |
Easy to implement |
And this method is also inconvenient in the case of protecting the application from changes. |