
Introduction
web-. , , . , - « ». , , , « ?» « — », «» .
. « », .
, , - , . SQLi, RCE, XXE, XSS, . SQL injection ( SQLi). , id, - . , , :
$id = $_GET['id']
$query = "SELECT * FROM some_table_name WHERE id=$id"
:
SELECT * FROM some_table_name WHERE id=1
, , «'», :
SELECT * FROM some_table_name WHERE id=1'
, - , SQLi. , , , , . , - HackerOne, 2019-2020 SQLi. Acunetix , - 2019-2020 , SQLi 8% , .
, , , ?! , . . Injection, __wakeup(). , $some_data.
<?php
class Injection {
public $some_data;
function __wakeup(){
if( isset( $this->some_data ) ){
eval( $this->some_data );
}
}
}
if( isset( $_REQUEST['data'] ) ){
$result = unserialize( $_REQUEST['data'] );
// ...
}
?>
<?php
class Injection {
public $some_data;
function __wakeup(){
if( isset( $this->some_data ) ){
eval( $this->some_data );
}
}
}
$inj = new Injection();
$inj->some_data = "phpinfo();";
echo( serialize( $inj ) );
?>
, :
O:9:"Injection":1:{s:9:"some_data";s:10:"phpinfo();";}
- , , phpinfo().
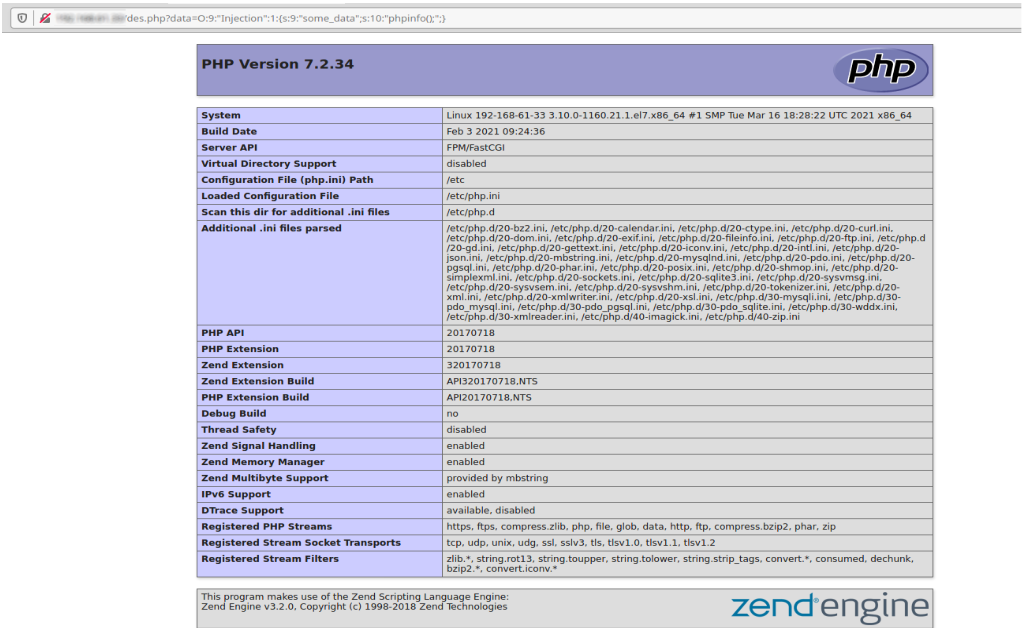
, , , . :
$LINK = new mysqli($DB_HOST, $DB_USER, $DB_PASS, $DB_NAME);
$user_name = $_GET['login'];
$user_password = $_GET['password'];
$query = $LINK->prepare("select id from user where login = '$user_name' and user_password='$user_password'");
$query->execute();
, , , « », 123456789. , : $123456789 123456789#. - , .
NordPass, , - 123456, — 123456789, , ( 200 ), « » .
-, .
. , , , , , , . , ?!
CMS WordPress «». , , . , , . - , - , .
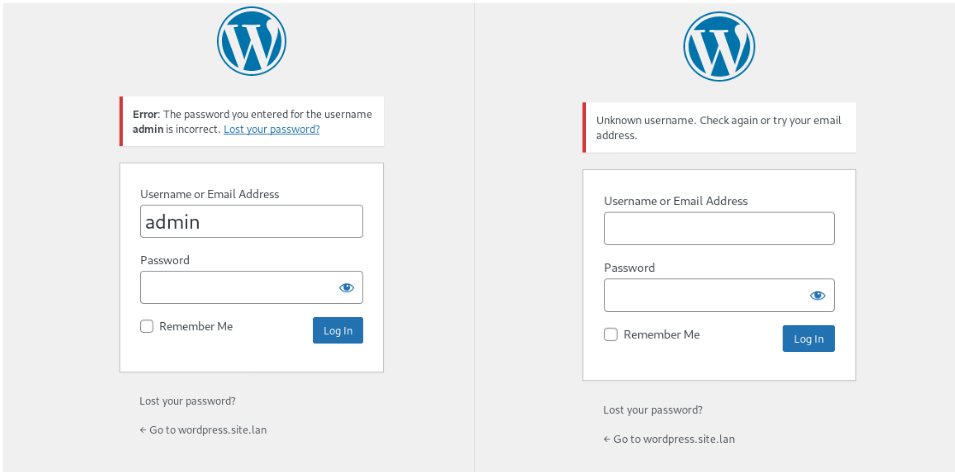
! , — -, . , :
. , - ;
-, .
ngnix:
http {
autoindex on;
include etc/nginx/mime.types;
default_type application/octet-stream;
:
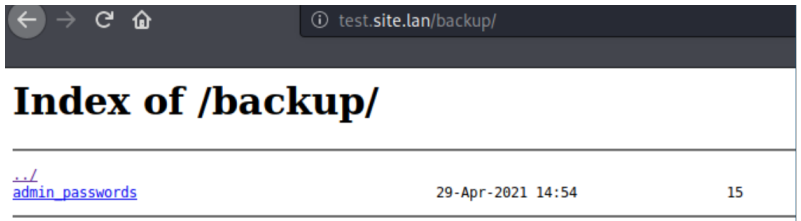
- . , .
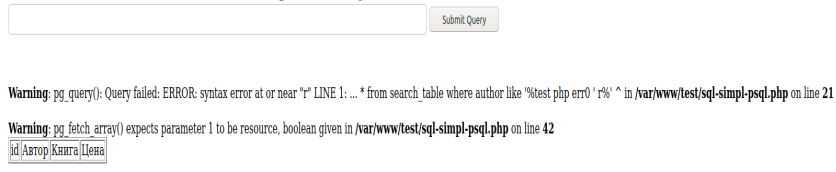
? 90% , . «» , , , . Linux . Unix- , - , , - . « - !».

- 1024. .
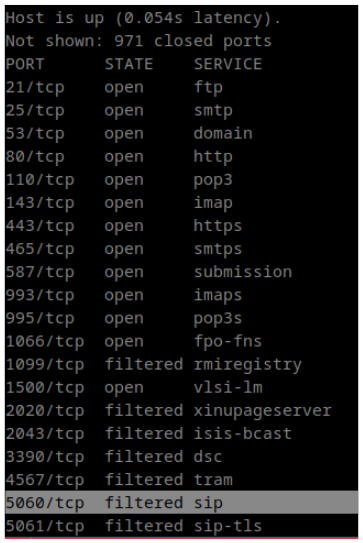
, . , , , -, . , ? — ! !
, web-, , .
.
- - (WAF). , , , WAF. WAF . Nemesida WAF — , . Nemesida WAF .