This article describes how to create a cross-browser identifier by exploiting vulnerabilities in four popular browsers: Tor Browser, Safari, Chrome, and Firefox. Demo links , source code .
Two months ago, while researching the Safari browser, I accidentally stumbled upon a vulnerability that allows me to check for a specific application on a user's computer directly from the browser using JavaScript.
24 24- . . , , .
, IDE Python, PostgreSQL . , , - , , Tor Browser. ?
, . , :
Linux. xdg-open, . Firefox - ;
, 8% ;
15% . , ;
-
. - Tor Browser PR .
. .
, . Deep Linking.
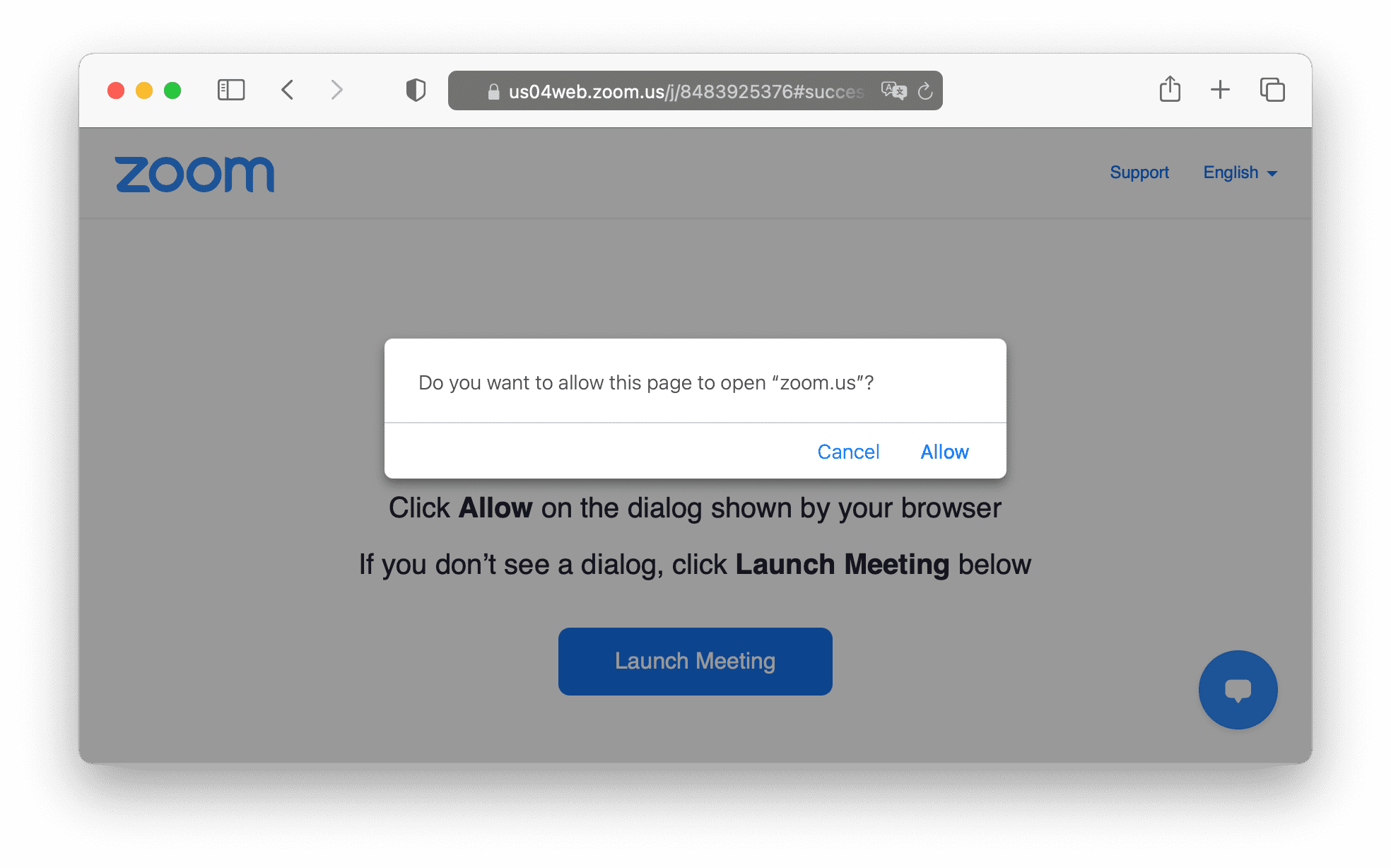
- , , .
Chromium
. ( ). ( ), .

, Extension () . , Extensions ( mailto:) . .
Chrome PDF Viewer, Extension. PDF .
:
location.replace();
input . , , ;
PDF , ;
1-3 , .
Firefox
same-origin policy. . , , JavaScript. about:blank, .
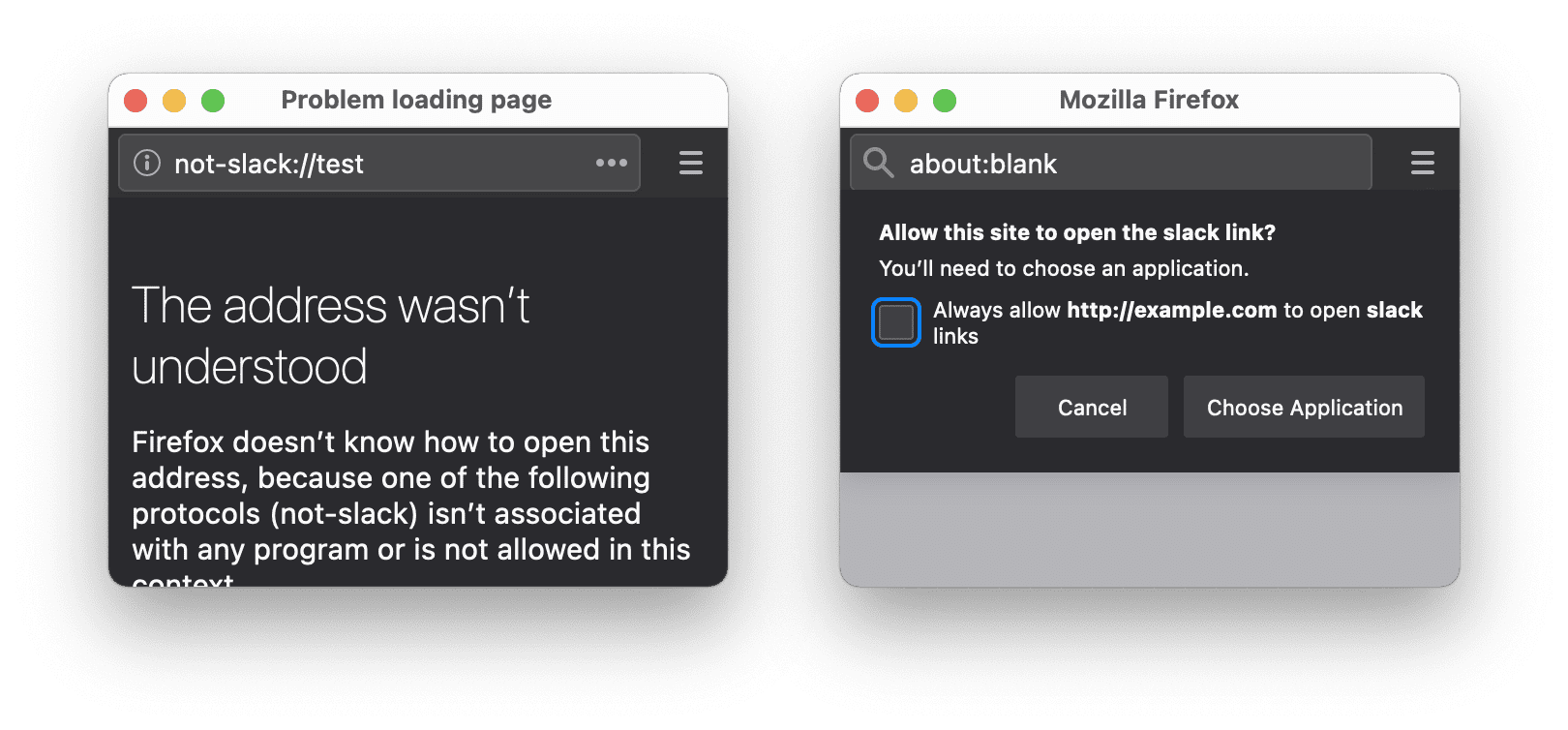
:
window.open;
location.replace;
document . , ;
2-3 .
Safari
, Firefox. , ( location.reload) .
Tor Browser
, -, . , .
No additional windows are needed here. We'll just use iframe elements and check the same-origin policy .

You can check passively: we check every 10 seconds in the background without requiring user actions.
You can do it actively: show a 24-character captcha and check it after each keystroke.
conclusions
This vulnerability has existed for several years, and many browser developers are aware of it, judging by the bug reports. However, I have not been able to find sites that use it.
Links: