There are already many articles on this topic on the Internet . I conducted a short research, during which I found that most of them use the standard VeraCrypt settings, which have long been worked out by cybercriminals and cannot be considered safe. Since with the development and appearance on the market of powerful user devices, the demand for superior enterprise equipment is growing.
Today, I'll show you how we will build a line of defense to protect data on a Windows device.
This material is inspired by Oleg Afonin 's article "How to Strengthen Vera. Making VeraCrypt Encrypted Containers Impenetrable". If you want to delve into the topic of information security, you can donate and subscribe to it.
Important
There is a small chance that your processor (old or inexpensive) does not support AES accelerated decryption technology. In this case, decrypting the disk when the device is turned on will take minutes instead of seconds (the time from entering the password to the start of the OS boot will take more).
You can find out in advance whether your technology supports this technology on the vendor's official website. For example Intel:

Or you can check it on third-party sites, an example is here .
VeraCrypt. —> ... .

"" , "/" — .
. Downloads, (Installer for) , Windows.
. , .
VeraCrypt . , :
.
VeraCrypt . :
" "
—
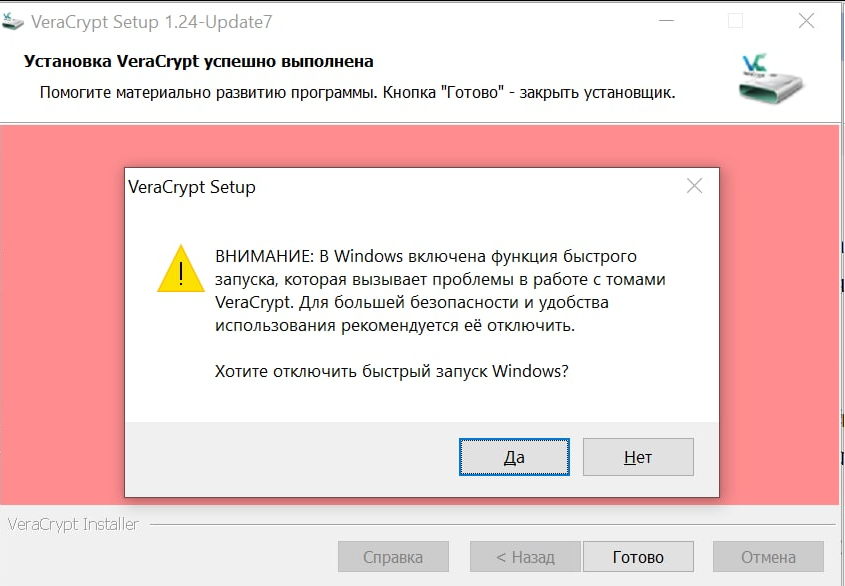
— , " Windows" " ". , .
— " ", .
, .
AES, .
, AES SHA-512, . : , .
Whirlpool.
, Streebog, ( "")
. . : , . - . "" .
" PIM" .

PIM (Personal Iterations Multiplier)
PIM, . — , . , .
, :
PIM (485):

500:

1000:

, , , PIM, (1,2,3 ... n) . , , .
. 1234 / 2012 / 1939 / / / . , .
, PIM , . 1709.
, , .
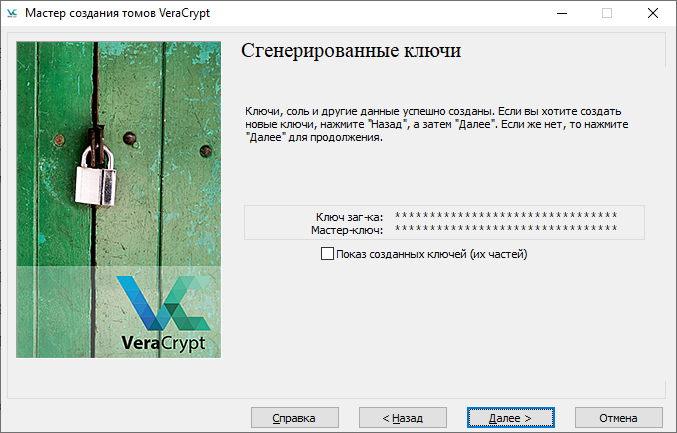
. , . , . — . , . .
. , , 3 .
-
, , -, , Windows , PIM. .
- ( PIM 5 ) . ESC Windows. VeraCrypt - . .
—> /. .

VeraCrypt , - , , , Encrypt, 15 .
. - .
:
— 1 ?
— , , . VeraCrypt . , .
— - PIM?
- If you approach it from a purely computational point of view, it will. The reality is that most attacks are carried out with default settings. Programs that can use attacks with a non-standard PIM value can be counted on the fingers of one hand, and even fewer programs that can automate attacks with a custom range of PIM values.