DDoS (Denial of Service) Attack is a common model of harassing competitors. Its simplest option is to maximize the load on the network channel so that real users either cannot reach the server or receive annoying delays. A more sensible approach is to artificially load services that willingly consume server resources. For example, a flurry of queries that cause calls to the database and other resource-intensive computational operations that overload the machine.
There are many services whose task is to protect clients from suspicious network activity from the outside. As a rule, they uncover and analyze even encrypted traffic, as well as perform some analytical actions with the user's browser in order to be sure to recognize the malicious load. As a result, the attacker receives a captcha, or does not have the ability to access the target resource at all.
What about hidden networks, where users do not have an IP address, and the analysis of encrypted traffic is unacceptable at the level of the technology concept? In this article, we will consider a unique way to protect against a DDoS attack in an I2P network and, in general, we will analyze the technology of lissets with authorization.
«.i2p», , . , : , , ? , , , DDoS- .
, , . , .. .
: , , , . , , , , . , – .
I2P : . , . , . – .
, . . . – .
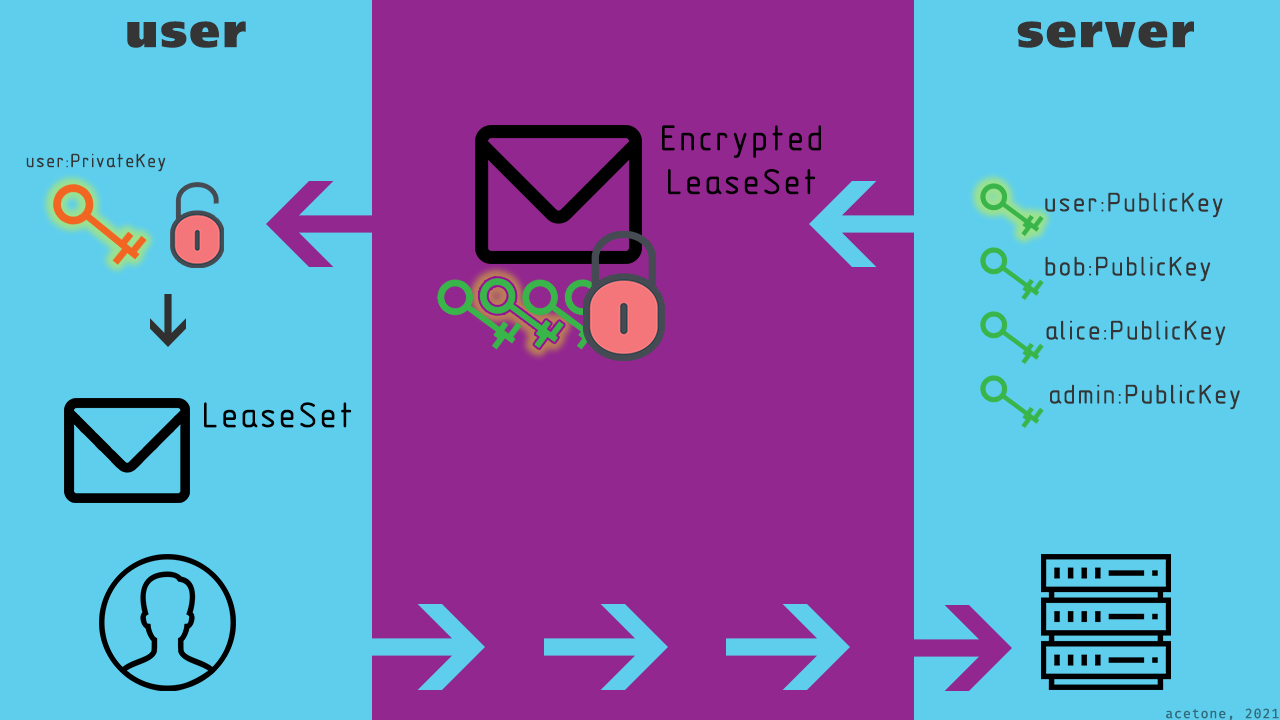
:
[SUPER-HIDDEN-SERVICE]
type = server
host = 127.0.0.1
port = 8080
inport = 80
keys = site.dat
signaturetype = 11
i2cp.leaseSetType = 5
i2cp.leaseSetAuthType = 1
i2cp.leaseSetClient.dh.NNN = User:PublicKey
i2cp.leaseSetClient.dh.NNN = User:PublicKey
NNN – ( )
User – ( )
PublicKey – base64
i2cp.leaseSetAuthType
«2», . : i2cp.leaseSetClient.psk.NNN = User:Password
. base64 .
x25519, i2pd-tools.

, , i2cp.leaseSetPrivKey = PrivateKey
, base64.

I2P-. – . , , - . .

. – . .
. , , . , . , .
- ITSOFT.