Faced with the need for a hidden I2P service , most are forced to use the services of hosting providers. For example, because there is no way to provide a good resource uptime on your home computer. Using data center services implies trust: we hope that staff will not abuse their position and someone will not try to steal data from disks.
Alas, confidence in a serious project is not enough, because even banal hacking of the system from the outside can never be ruled out. There is no absolute safety, but after any incident you probably want to recover as quickly as possible. This tutorial will show you how to use temporary keys so that the address of your hidden resource cannot be stolen even if the server is compromised.
Formation of an intranet I2P address
When creating a server tunnel that brings a local service to a hidden network, you must specify a file with keys (if a non-existent one is specified, a new file with random keys is created).

The key file contains cryptographic identifiers. A total of 391 bytes of public information and secret keys that are not published. The hash from the block of public information contained in the key file forms the intranet address.

(391 ) «.b32.i2p», «.i2p», : , . , , – , .
, I2P, , . – (391 ), . , . , .
I2P - (offline keys), . , , , . , , , .
. . - , . , , . , , , . , , , , .

i2pd-tools. offlinekeys : <output file> <keys file> <signature type> <days>
. , .
, ED25519-SHA512 ( 7), 365 , . , .
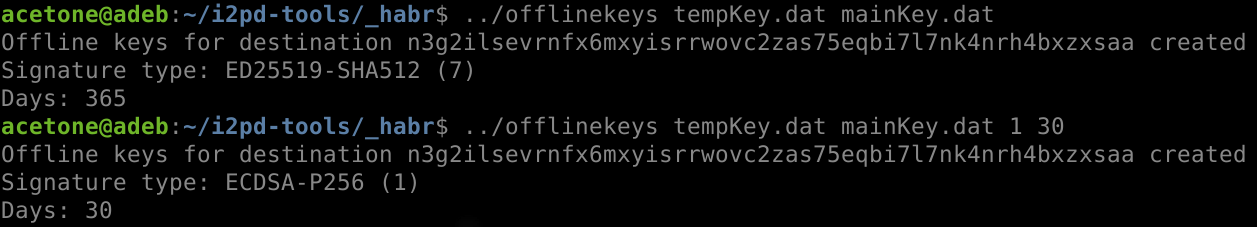
, , . – . , .
- ITSOFT.