When conducting a penetration test on an internal network of an enterprise, one of the first attack vectors to consider on Windows networks is to find and compromise unsupported operating systems with known and public exploits. Most often, the SMB service is used. Another problem for system administrators is the lack of network documentation. A pentester and / or network information security analyst may face black-box network intelligence in a busy situation or with outright negligence of the staff responsible for the operation. In particular, administrators (the thesis is confirmed by the research of colleagues from Positive Technologies ).
We will formulate and slightly expand the case
It is necessary for an adequate time to find all unsupported Windows operating systems on the local network of an enterprise with more than 10 thousand hosts, presumably with public SMB exploits.
A limitation of the method can be network segmentation, when some subnets are closed from the researcher's host.
Who cares, welcome under the cat ...
ATTENTION! The masscan application used in this article can kill the entire network, it is a very powerful tool. Pre-test your network at different rate parameters.
- The list of all possible private IP addresses can be recorded with three masks 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16
We enter them into a file.
root@debSec:~/search_old_os# vim subnet.lst
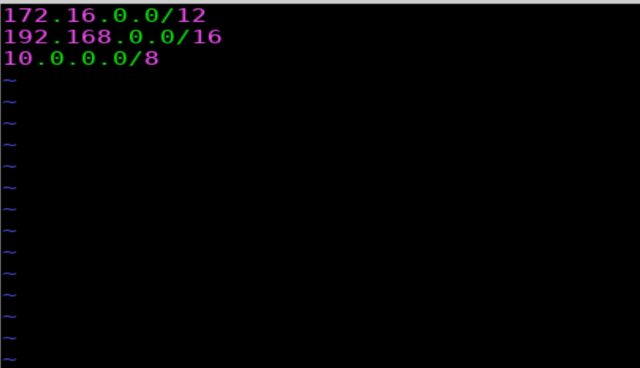
To quickly determine all used subnets, we use masscan in ping scan mode.
root@debSec:~/search_old_os# masscan --ping --rate 10000 -iL subnet.lst -oX fast_ping_scan.xml
30 . .

: , . , .
root@debSec:~/search_old_os# masscan --ping --rate 1000 -iL subnet.lst -oX fast_ping_scan.xml
.
root@debSec:~/search_old_os# cat fast_ping_scan.xml|grep -Eo '([0-9]{1,3}\.){3}[0-9]{1,3}'

, masscan rate 10000 . rate , 24.
root@debSec:~/search_old_os# cat fast_ping_scan.xml|grep -Eo '([0-9]{1,3}\.){3}'|sort|uniq|sed -e 's/$/0\/24/'>target_subnet.lst
499 .

masscan c rate, , 1000 .
root@debSec:~/search_old_os# masscan --ping --rate 1000 -iL target_subnet.lst -oX target_ping_scan.xml
2 , 28 . , rate 100. 20 .
, 10296 .
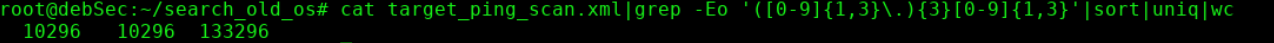
, , 99.91% . , .
.
root@debSec:~/search_old_os# cat target_ping_scan.xml|grep -Eo '([0-9]{1,3}\.){3}[0-9]{1,3}'|sort|uniq >target_ping_scan.lst
, , .
SMB. , 139,445.
msscan , .
root@debSec:~/search_old_os# masscan --port 139,445 --rate 100 -iL target_ping_scan.lst -oX ip_smb.xml
SMB, , IP.
root@debSec:~/search_old_os# cat ip_smb.xml|grep -Eo '([0-9]{1,3}\.){3}[0-9]{1,3}'|sort|uniq >ip_smb.lst
?
. : nse nmap.
root@debSec:~/search_old_os# nmap -Pn --script smb-vuln* -p139,445 -iL ip_smb.lst -oA nmap_smb_vuln
nmap 71 ~10 .




11 .
nmap, OS SMB.
root@debSec:~/search_old_os# nmap --script smb-os-discovery.nse -p 445,139 -iL total_smb.lst -oA all_os
( , , nmap )
, .
, .
OS. , :
root@debSec:~/search_old_os# cat all_os.nmap |grep -B 10 -E 'Windows v1|Windows Server v2|Windows v3|Windows v4|Windows v5|Windows v6' >FINAL_TOTAL_OLD_WINDOWS_FULL.lst
IP.
root@debSec:~/search_old_os# cat FINAL_TOTAL_OLD_WINDOWS_FULL.lst|grep -Eo '([0-9]{1,3}\.){3}[0-9]{1,3}'|sort|uniq >FINAL_TOTAL_OLD_WINDOWS_FULL.lst
65 .
metasploit . . .
, .
:
- .
- - .
- "", RedTeam.
- ( ).
:
- . — , .
- ActiveDirectory.
- . , , Nessus. , ( ).
The method is not the only one and not the best, but in my conditions it was the only acceptable one. I hope someone will come in handy ...