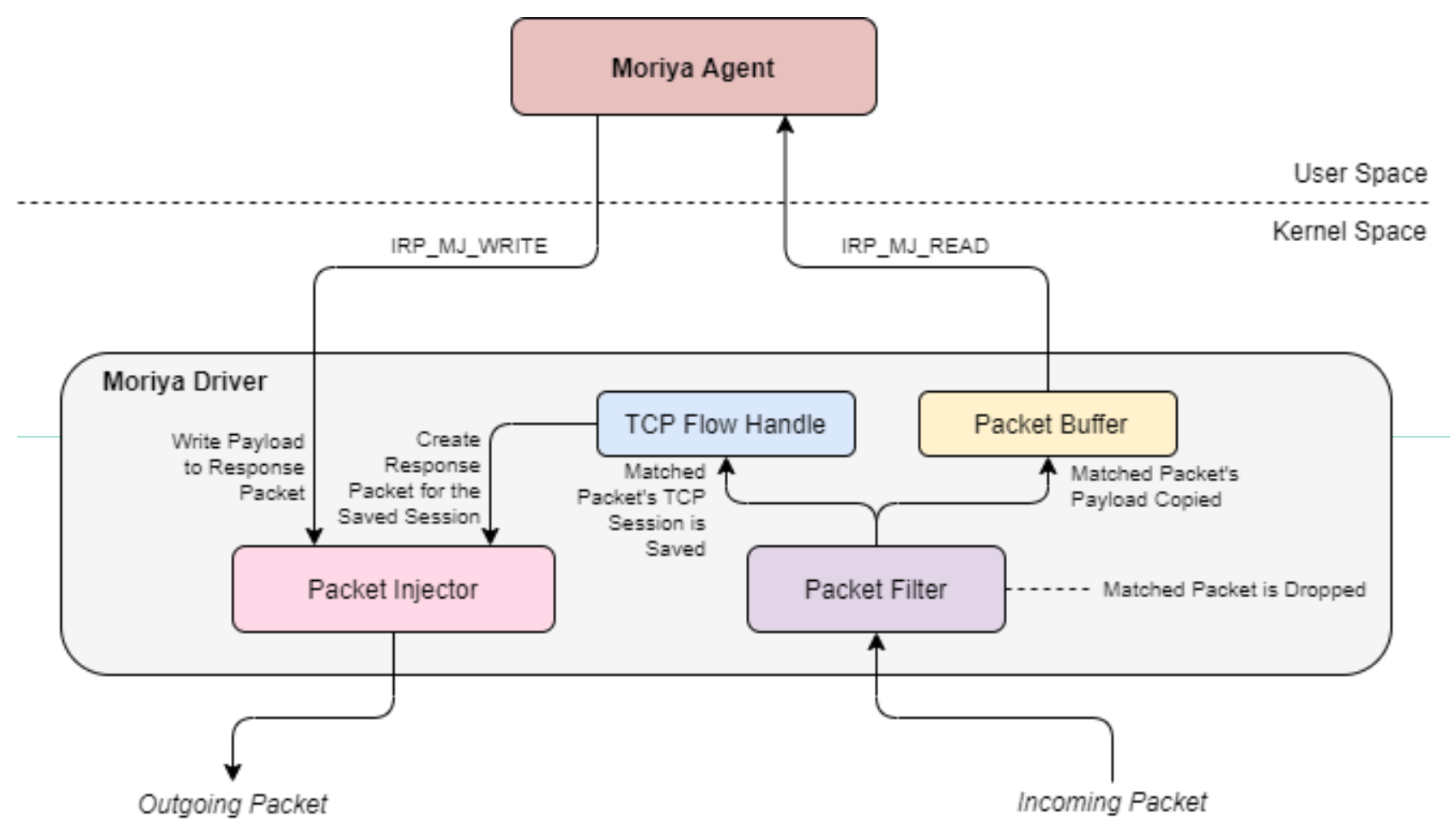
As Windows security systems evolved, the number of rootkits decreased: it became more difficult to run malicious code with kernel privileges. The reason for this is the introduction of mandatory driver signatures and the PatchGuard mechanism, which causes a crash in the "blue screen" when trying to penetrate the system core. Moriya (the name comes from the name of the malicious driver) bypasses this protection using a mechanism known since 2015 that uses the driver for the Virtualbox virtual machine.
Driver injection using VBoxDrv.sys is detailed in Virus Bulletin in relation to the Turla malware campaign. A similar method was used in the Lamberts and Equation attacks. The driver for Virtualbox is digitally signed, but it adds and runs another unsigned driver, MoriyaStreamWatchmen.sys. The latter's task is to monitor incoming network traffic and process instructions from the C&C server, marked with a special sequence of characters:

Thus, the rootkit is a passive backdoor and is designed to run on an infected server with direct Internet access. Kaspersky Lab experts also describe other malicious modules responsible for scanning the internal network traditional for such attacks, as well as infecting other computers and servers. Moreover, unlike many incidents, the initial method of penetrating the server is known. This is a vulnerability in the Microsoft IIS web server, discovered in 2017 and relevant in an outdated version of Windows Server 2003. Apparently, the presence of such software on the side of a potential victim was the reason for the development of the rootkit.
What else happened
In the ongoing legal battle between Apple and Epic Games , new details have emerged from 2015. Then hundreds of applications with malicious code were found in the official Apple store. All of them were created using a pirated version of the official Apple Xcode developer software. Illegal IDE version known as XCodeGhost, added malicious code to the build of a regular application (its task was to steal accounts). The internal correspondence of Apple of those years, disclosed during the proceedings, clarifies the scale of the problem: at least one trick app was installed by 128 million iOS users. A lot of infected apps were missed by the vendor's quality control system. In addition, Apple at that time decided not to notify every victim, limiting itself to a short message on the company's website. These documents have surfaced in court due to efforts by Epic Games to prove that the App Store is far from being secure.
Big news from the beginning of this week - cyberattackwith extortion against a major supplier of gasoline and petroleum products on the east coast of the United States, Colonial Pipeline.
Bleeping Computer journalists write about the Ryuk ransomware attack on a research institute. The vulnerable link was the laptop of a student who had access to the internal network of the institution: he tried to "cure" an unregistered copy of Windows using a "crack".
The research paper describes (PDF, also website ) a new vulnerability allowing DDoS attacks on root DNS servers.
Vulnerabilityin radios Qualcomm makes potentially vulnerable up to 30% of smartphones. In theory, using a modem communication interface, it is possible to execute arbitrary code inside a poorly controlled "telephone part" on the OS side.
Maintainers Exim mail server closed the 21 vulnerabilities affecting most versions until 2004.

In July 2021, Microsoft plans to complete the process of forced removal of the Adobe Flash plug-in from all supported versions of Windows, including Windows 10, Windows 8.1 and Windows Server 2012.
A serious vulnerability has been discovered in the driver for Dell laptops .