Hello colleagues.
I found it interesting to share information about the internal structure of Apple technology with the community, since there are very few articles on this topic. I decided to start with the iPhone. Therefore, I suggest that you, together with me, try to understand the work of this mysterious device.
I will try to target the most recent models. I would be glad if your comments point out errors and help us all to better understand how the devices that surround us work.
Introduction
I don't know if this will surprise anyone or not, but launching an iPhone is not much different from the process of launching an IBM-PC- compatible computer in the form of a system unit under a table, about which a lot has already been written. This is probably why there are so few articles on this topic related to mobile devices.
If you look at the process of launching the iPhone, as a whole picture, then it is a chain of trusting transitions from one stage of the download to another, which is called the "Chain of trust" . In general, there are 3 independent programs involved in the process: Boot ROM , iBoot, and the XNU kernel (in order of execution). The transfer of control from one to another occurs after the identity of the person to whom control should be transferred is verified. Each of them has Apple's cryptographic signature . A reasonable question arises: how is the authenticity of the first step verified? Answer: no way .
The very first gets control of the Boot ROM. It is an unchangeable component of the system, it is stitched at the factory and does not change anymore. It cannot be updated (unlike BIOS and UEFI). Therefore, there is no point in verifying its authenticity. Therefore, it has the appropriate status: "Hardware root of trust" . The Apple Root certificate authority (CA) public key is embedded in the Boot ROM , which is used to verify the authenticity of the iBoot. In turn, iBoot verifies the authenticity of the XNU kernel with its key. This chain of checks allows you to run only trusted software.
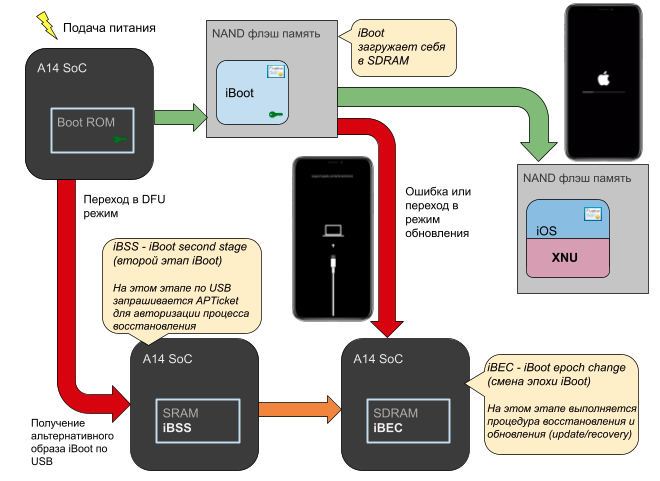
, Boot ROM. , Jailbreak ( ). Boot ROM . , . 150 . , . Boot ROM iBoot . . (AES, ANC, USB), ( , ), (env, libc, image), ( SoC, MMU, NAND). , . iBoot , , ..
.
|
|
|
|
|
|
1. Boot ROM |
|
|
BIOS, UEFI, coreboot |
SRAM |
2. iBoot |
|
|
GNU GRUB, Windows Bootmgr, efibootmgr |
SDRAM |
3. XNU |
|
|
Linux, NT kernel, GNU Hurd |
SDRAM |
4. iOS |
|
|
Ubuntu, Windows, Android |
SDRAM |
. ( , , , ). (PMIC — Power Management Integrated Circuit). PMIC , , Lightning, ( ). . . , .
PMIC Power-On. : ( ). — .
, . , - . , . , , . , , . PMIC Side-Button , , , : ( ). , PMIC PMIC. D- . CLR . , RC-, .
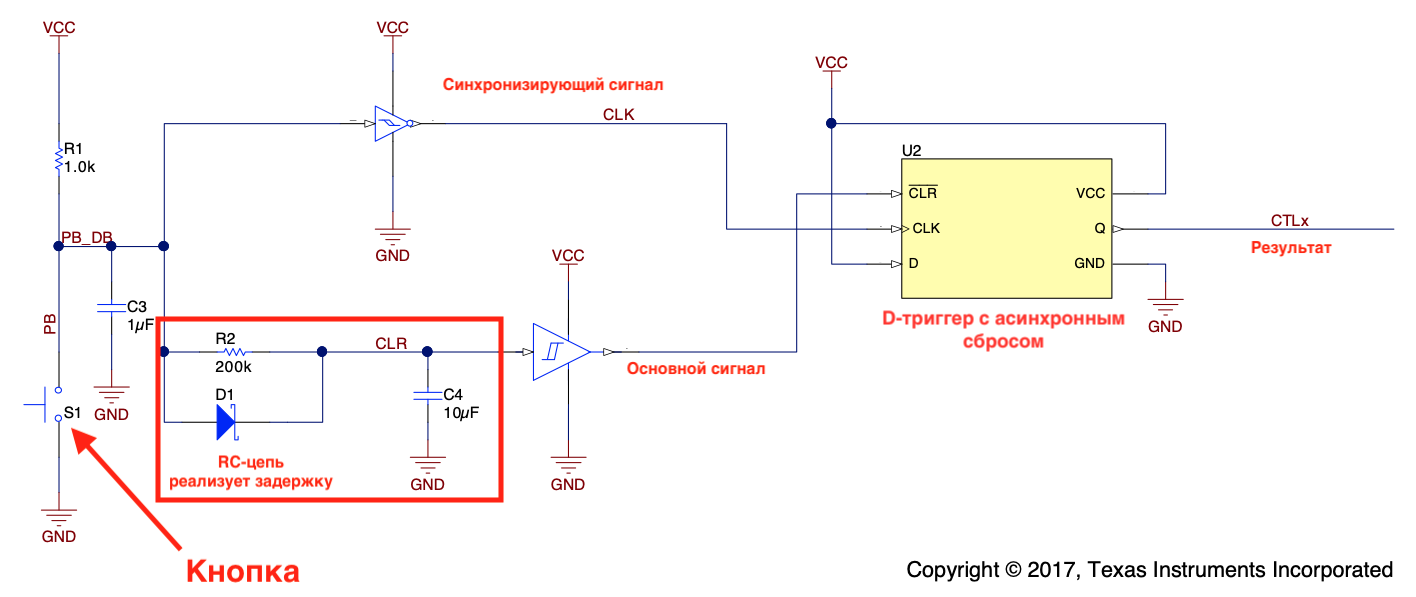
, CTLx -. . CLR , CLK , CTLx , PMIC .
SoC CPU
. , , , , . - . (System on a Crystal — SoC) Apple — TSMC (Taiwan Semiconductor Manufacturing Corporation). Apple , , . , - . , Apple.
SoC . , , , , , -, . . SoC . . (Power-on reset / PoR generator). : , . PoR , .
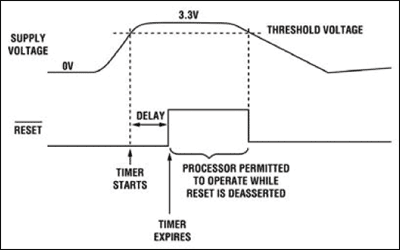
, , RC- . ( ), PoR , .
. , . PoR - ( ). (Program Counter/PC register) . (Reset vector). , 0×100000000
. ( , ). .
, , . , , (primary core), . .
(Read only memory — ROM). SoC. ( ) ( ). . , Boot ROM. .
Boot ROM
, Boot ROM — , SoC. -. Apple. C , - . Boot ROM, , -, — _start
. , , arm64. :
(L2 cache) ( 2 MiB).
, . , .
main
( C) LR.ret
main
.
. , , .
.
,
main
.
, , C.
main
CPU.
, , Exception Levels (EL): EL0, EL1, EL2, EL3. . — . ( ). . , , .
CPU .
(Secure Configuration Register - SCR): (FIQ IRQ).
.
(System Control Register: SCTLR): , (Memory Management Unit - MMU, CPU), , ( Execute Never / XN — NX- x86 ), .
.
main
, .
:
.
(DVFS - Dynamic voltage and frequency scaling).
, BootROM.
BootROM.
(PLL - Phase Lock loop).
(SEP - Secure Enclave processor).
(sepOS), . .
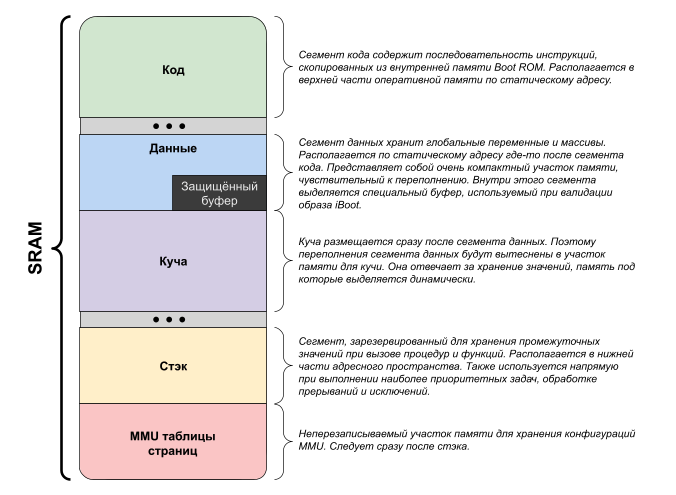
( -). (Static Random Access Memory — SRAM). , . (Dynamic Random Access Memory — DRAM). , SRAM , DRAM . . , . , . SRAM ( , ), DRAM ( , ). SoC GPIO (General Purpose Input/Output) . , , , DFU (Device Firmware Upgrade mode — ). , .
/ (BIOS), Boot ROM : ( ) (heap). . , Boot ROM.
: , SoC. iPhone :
GPIO
, . DFU . , , DFU , , .
, . DFU , USB, - ( NAND ).
if (dfu_enabled)
boot_fallback_step = -1;
while (1) {
if (!get_boot_device(&device, &options))
break;
process_boot(device, options);
if (boot_fallback_step < 0)
continue;
boot_fallback_step++;
}
reset();
, ( ). , USB. , «».
Apple — IMG4 ( ). DER ASN.1.
sequence [
0: string "IMG4"
1: payload - IMG4 Payload, IM4P
2: [0] (constructed) [
manifest - IMG4 Manifest, IM4M
]
]
sequence [
0: string "IM4P"
1: string type - ibot, rdsk, sepi, ...
2: string description - 'iBoot-6723.102.4'
3: octetstring - the encrypted/raw data
4: octetstring - containing DER encoded KBAG values (optional)
sequence [
sequence [
0: int: 01
1: octetstring: iv
2: octetstring: key
]
sequence [
0: int: 02
1: octetstring: iv
2: octetstring: key
]
]
]
(UtilDM — Utility Device Manager), ANC (Abstract NAND Chip) . NAND , iBoot. IMG4.
, . , . . — (environment) . , , , Boot ROM (Apple Root CA public key).
, Boot ROM. -, iBoot. , , - , , , ..
iBoot , .
. iPhone — iBoot.
.
:
Apple: Boot process for iOS and iPad devices
Apple: Hardware security overview
Design & Reuse: Method for Booting ARM Based Multi-Core SoCs
Maxim integrated: Power-on reset and related supervisory functions
The iPhone wiki
ARM: Documentation
Jonathan Levin: MacOS and *OS internals
Wikipedia
: iBoot address space
Harry Moulton: Inside XNU Series
Ilhan Raja: checkra1n
Texas Instruments: Push-Button Circuit
iFixit: iPhone 12 and 12 Pro Teardown
SecureROM iBoot, 2018