The principle of I2P anonymity is the unknown location of a hidden service. Each hidden service (for example, a website or a user who visits it) interacts with other resources exclusively through anonymizing tunnels. Tunnels are built through the routers of the network participants in the same way as other users build tunnels through our router. This model creates many direct connections between I2P routers, in which it is impossible to determine on which router a particular tunnel started or ended: thousands of simultaneous encrypted connections do not provide this opportunity.

, (LeaseSet), . , , (Floodfill) – , . , , .. , I2P . ( « » «destination») .
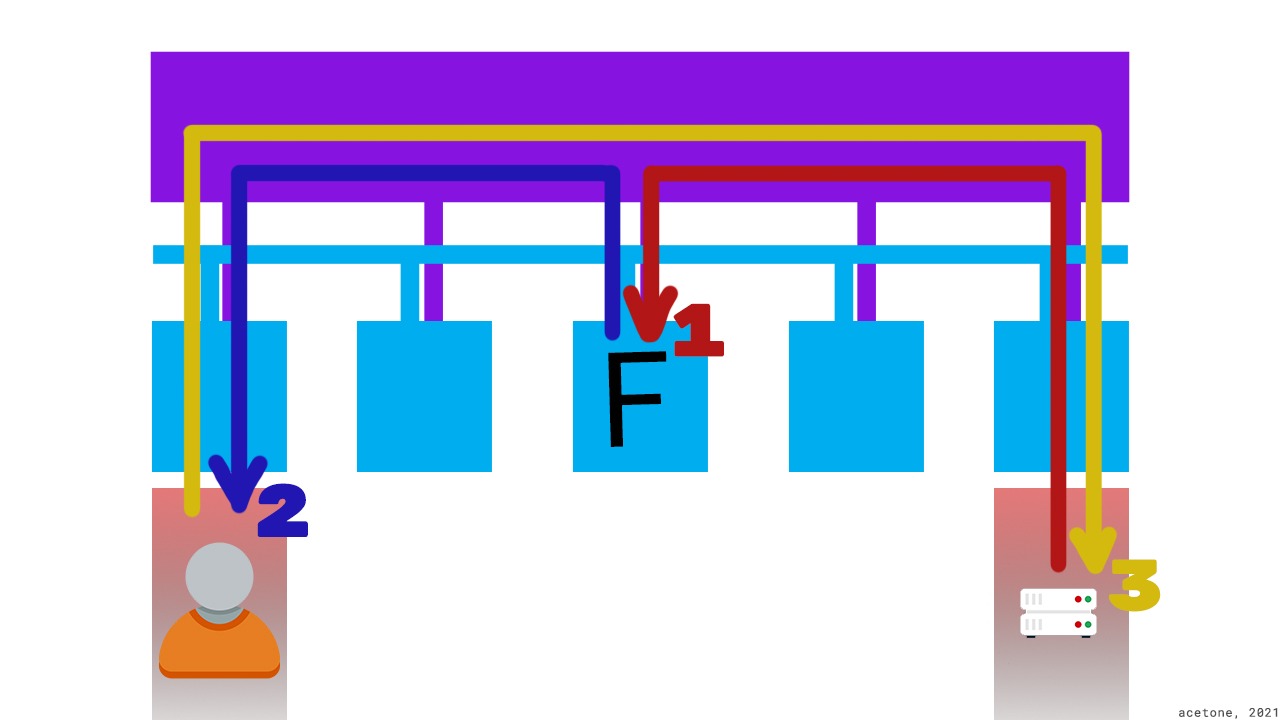
– , «.b32.i2p». , . I2P , - , – !
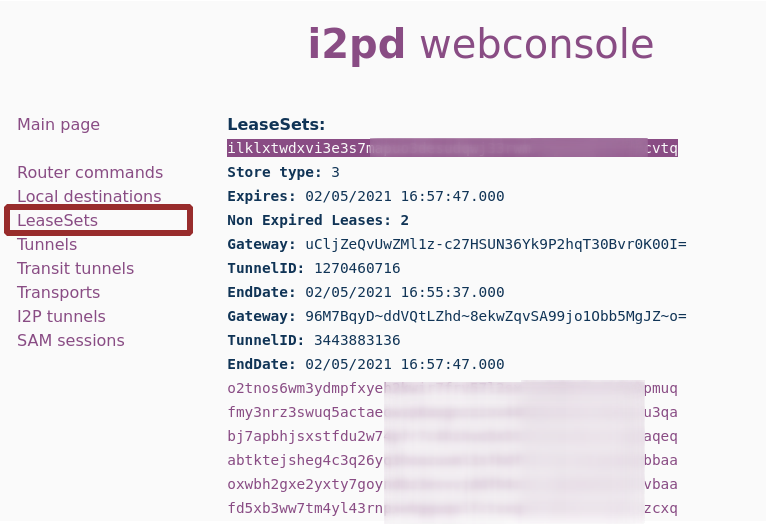
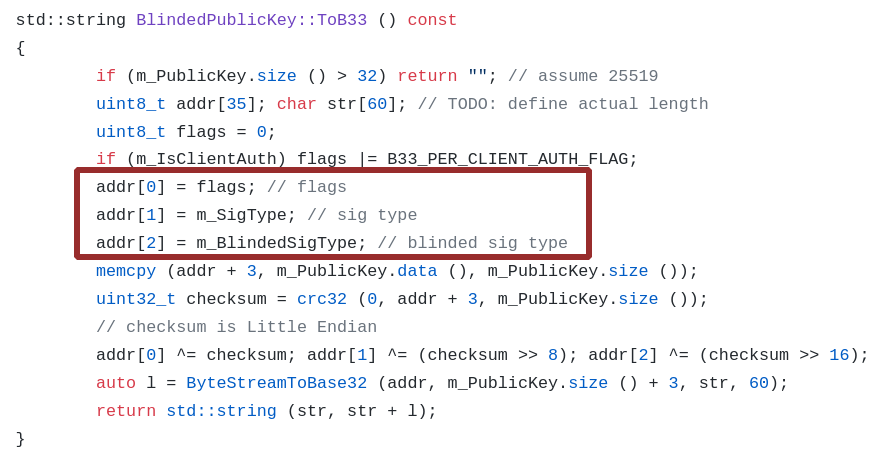
blinding («»). : «bb32» – blinded-b32. «b32» base32, , . , bb32 – . .
bb32 ( ) , . bb32 «i2p». – . bb32-, I2P- , , , .
( , ), – , : , .
, .. , , . : EDDSA_SHA512_ED25519 ( 7) REDDSA_SHA512_ED25519 ( 11), . i2pd , .. .
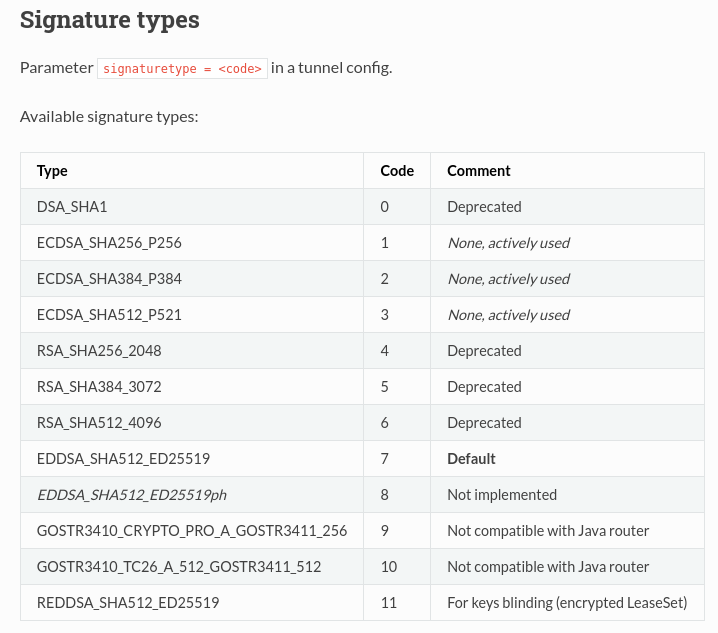
, , -, 11 , -, 7 . , .. - , . - , , , . , , 11, , .
bb32 ( - b33, - ) ( ):
[SUPER-HIDDEN-SERVICE]
type = server
host = 127.0.0.1
port = 8080
inport = 80
keys = site.dat
signaturetype = 11
i2cp.leaseSetType = 5
, . , , . i2cp.leaseSetAuthType
. : , , – , , , . ( i2cp.leaseSetPrivKey
, i2cp.leaseSetClient.dh.nnn
, i2cp.leaseSetClient.psk.nnn
).
- ITSOFT.