
Domain Name Server (DNS) spoofing is a cyberattack in which an attacker directs victim's traffic to a malicious site (instead of a legitimate IP address). Attackers use DNS cache poisoning to intercept Internet traffic and steal credentials or confidential information. DNS cache poisoning and DNS spoofing are identical concepts, often used synonymously. The hacker wants to trick users into entering personal information on an insecure website. How can he achieve this? By poisoning the DNS cache. To do this, the hacker spoofs or replaces the DNS data for a specific site, and then redirects the victim to the attacker's server instead of the legitimate server. Thus, the hacker achieves his goal, because wide opportunities open up before him: he can carry out a phishing attack , steal data, or even inject malware into the victim's system.
What is DNS spoofing and cache poisoning?
Before we start talking about DNS cache poisoning, let's first take a look at what DNS and DNS caching are. DNS is the worldwide directory of IP addresses and domain names. We can say that this is a kind of Internet telephone directory. DNS translates user-friendly addresses like varonis.com into IP addresses like 92.168.1.169, which are used by computers to work on the network. DNS caching is a system for storing addresses on DNS servers around the world. To speed up the processing of your DNS queries, the developers have created a distributed DNS system. Each server maintains a list of DNS records it knows, called a cache. If the DNS server closest to you does not have the desired IP address, it queries upstream DNS servers until it finds the address of the website you are trying to reach.Your DNS server then stores this new entry in your cache to get a faster response next time.
Examples and consequences of DNS cache poisoning
The DNS concept is not tailored to the specifics of the modern Internet. Of course, DNS has evolved over time, but now it is still enough to have one misconfigured DNS server to make millions of users feel the impact. Example - attack on WikiLeakswhen attackers used DNS cache poisoning to intercept traffic, redirecting it to their own clone of the site. This attack was designed to steal traffic from WikiLeaks, and it achieved some success. DNS cache poisoning is not easy for ordinary users to detect. DNS is currently built on trust, and this is its weak point. People trust DNS too much and never check if the address in their browser matches what they really want. Attackers use this carelessness and inattention to steal credentials and other important information.
How does DNS cache poisoning work?
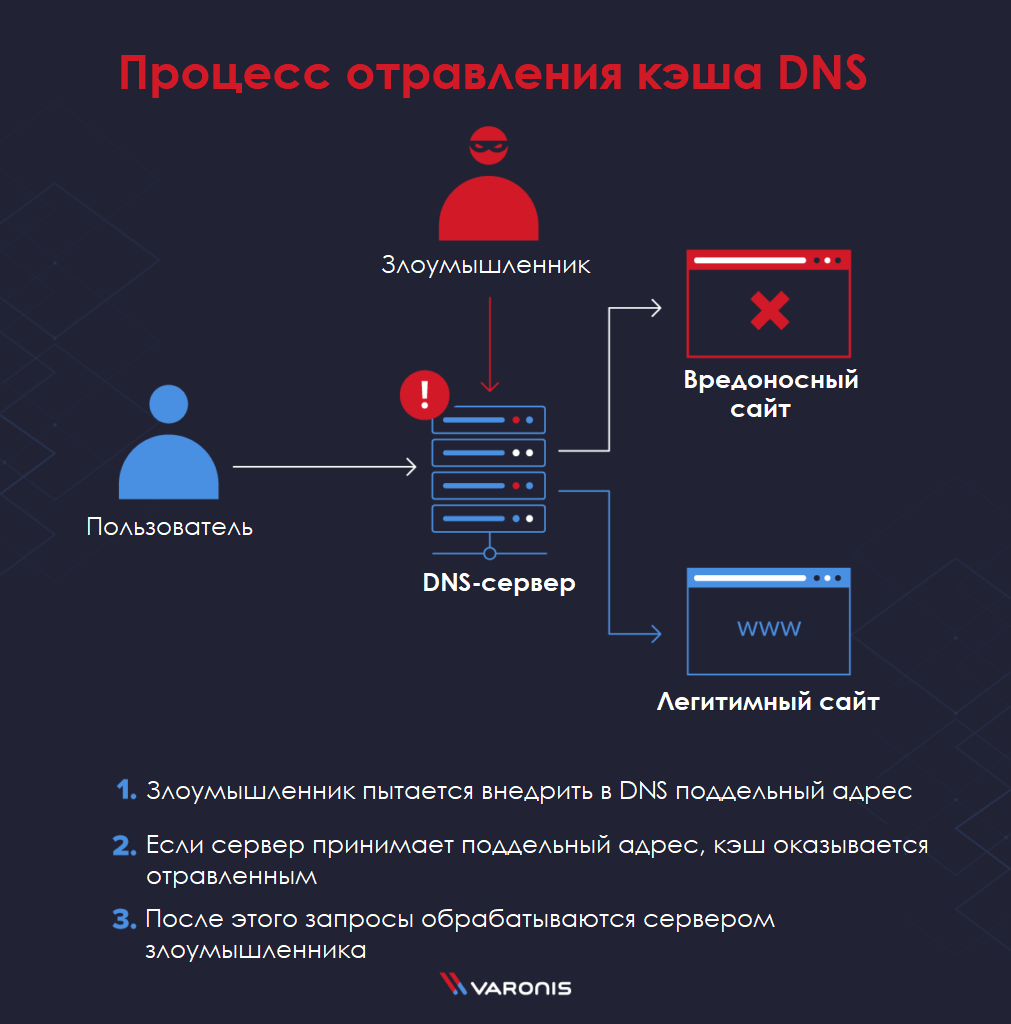
Poisoning the DNS cache means that the DNS server closest to you contains a record that sends you to the wrong address, which is usually controlled by an attacker. There are a number of techniques that attackers use to poison the DNS cache.
Intercepting LAN Traffic Using ARP Spoofing
You will be surprised how vulnerable a local network can be. Many administrators can rest assured that they have blocked all possible access, but, as you know, the devil is in the details.
One of the common problems is employees working remotely . How can you be sure that their Wi-Fi network is secured? Hackers can crack a weak Wi-Fi password in a matter of hours.
Another problem is open Ethernet portsaccessible to everyone in the corridors, lobbies and other public places. Just imagine: a visitor can connect an Ethernet cable to their device for the lobby display. How can a hacker use access to your local network obtained in one of the above ways? First, he will be able to create a phishing page to collect credentials and other valuable information. Then he can host this site either on a local network or on a remote server, and for this he only needs one line of Python code. The hacker can then start spying on the network using special tools like Betterrcap. At this point, the hacker examines the network and makes reconnaissance, but the traffic is still going through the router.An attacker can then tamper with the Address Resolution Protocol (ARP) to change the structure of the network from within. ARP is used by network devices to associate a device's MAC address with an IP address on a network. Bettercap will send messages, forcing all devices on the network to think of the hacker's computer as a router. With this trick, a hacker will be able to intercept all network traffic passing through the router. Once the traffic is redirected, an attacker can launch the Bettercap module to spoof DNS. This module will search for any requests to the target domain and send false responses to the victim. The false response contains the IP address of the attacker's computer, redirecting all requests to the target site to a phishing page created by the attacker. The hacker now sees traffic destined for other devices on the network,collects entered credentials and injects malicious downloads.
If the hacker cannot access the local network, he will resort to one of the following attacks.
Forging answers with a birthday attack
DNS does not authenticate responses to recursive queries, so the first response is cached. Attackers use the so-called birthday paradox to try to predict and send a bogus response to the requester. The birthday attack uses mathematics and probability theory to predict . In this case, the attacker tries to guess the transaction ID of your DNS request, and if successful, the fake DNS record reaches you before a legitimate answer. The birthday attack is not guaranteed to succeed, but in the end an attacker will be able to cache a bogus response. After the attack is successful, the hacker will be able to see traffic from the fake DNS record to the end of the lifecycle (TTL) of the DNS record....
is a variation of the birthday attack. Dan Kaminsky, who discovered this vulnerability, first presented it at the BlackHat conference in 2008. The essence of the exploit is that the hacker first sends a DNS resolver request for a non-existent domain, for example fake.varonis.com. After receiving such a request, the DNS resolver redirects it to an authoritative name server to obtain the IP address of the fake subdomain. At this point, the attacker overwhelms the DNS resolver with a huge number of bogus responses in the hope that one of these bogus responses will match the transaction ID of the original request. If successful, the hacker spoofs the IP address in the DNS server cache, for example, as in our example with varonis.com. The resolver will continue to respond to all requestors that the fake varonis.com IP address is real,until the DNS record expires.
DNS?
How to detect if the DNS cache is poisoned? To do this, you need to monitor your DNS servers for indicators of a possible attack. However, no one has the computing power to handle such volumes of DNS requests. The best solution is to apply data security analytics to your DNS monitoring. This will distinguish normal DNS behavior from malicious attacks.
• A sudden increase in DNS activity from one source against one domain indicates a potential birthday attack.
• An increase in DNS activity from a single source, which queries your DNS server for multiple domain names without recursion, indicates an attempt to pick a record for subsequent poisoning.
In addition to DNS monitoring must also monitor Active Directory events and file system behavior in order to detect abnormal activity in time. Better yet, use analytics to find the relationship between all three vectors. This will provide valuable contextual information to strengthen your cybersecurity strategy.
Methods to protect against DNS cache poisoning

In addition to monitoring and analytics, you can make changes to the DNS server settings:
- Limit recursive queries to guard against potential targeted cache poisoning.
- store only data related to the requested domain;
- limit responses to only those related to the requested domain;
- require clients to use the HTTPS protocol.
Make sure you are using the latest BIND and DNS software and thus have all the latest vulnerability fixes. If possible, for example in the case of remote workers, arrange so that all remote computers are connected via a VPN. This will protect traffic and DNS requests from being snooped locally. In addition, encourage employees to create strong passwords for Wi-Fi networks to mitigate risks as well.
Finally, use encrypted DNS queries. Domain Name Service Security Modules (DNSSEC)Is a DNS protocol that uses signed DNS queries to prevent spoofing. When using DNSSEC, the DNS resolver needs to verify the signature with an authorized DNS server, which slows down the entire process. Consequently, DNSSEC has not yet gained widespread acceptance.
DNS over HTTPS (DoH) and DNS over TLS (DoT)are competing specifications for the next version of DNS and, unlike DNSSEC, are designed to secure DNS queries without sacrificing speed. However, these solutions are not ideal as they can slow down or completely make it impossible to locally monitor and analyze DNS. It is important to note that DoH and DoT can bypass parental controls and other DNS-level blocks set on the network. Regardless, Cloudflare, Quad9, and Google have public DNS servers with DoT support. Many new clients support these modern standards, although support is disabled by default. You can find more details on this in our post on DNS security .
DNS spoofing replaces the legitimate IP address of the site with the IP address of the hacker's computer. It is very difficult to detect the substitution, because from the point of view of the end user, he enters an absolutely normal website address in the browser. Despite this, such an attack can be stopped. Risks can be mitigated by using DNS monitoring, for example from Varonis , and the DNS over TLS (DoT) encryption standard.
Cache Poisoning: Frequently Asked Questions
Check out common DNS spoofing questions and answers.
DNS cache poisoning and DNS cache spoofing (spoofing) the same thing?
Yes, the same type of cyberattack is called cache poisoning and cache spoofing.
How does DNS cache poisoning work?
Cache poisoning tricks your DNS server into storing a bogus DNS record on it. After that, the traffic is redirected to the server chosen by the hacker, where the data is stolen.
What security measures can be applied to protect against DNS cache poisoning?
Site owners can perform monitoring and analytics to detect DNS spoofing. In addition, you can update your DNS servers to use Domain Name System Security Modules (DNSSEC) or another encryption system such as DNS over HTTPS or DNS over TLS. The widespread use of full end-to-end encryption such as HTTPS can also prevent DNS spoofing. Cloud Access Security Brokers (CASB) are extremely useful for these purposes. End users can flush a potentially spoofed DNS cache by periodically flushing their browser's DNS cache or after connecting to an insecure or public network. Using a VPN can protect against DNS spoofing on the local network. Avoid suspicious links. This will help avoid the risk of contaminating your browser cache.
How can you check if you've been hit by a cache poisoning attack?
Once the DNS cache has been poisoned, it is difficult to detect. A much better tactic is to monitor your data and protect your system from malware to protect yourself from data leaks due to DNS cache poisoning. Visit our interactive cyber attack lab to see how we use DNS monitoring to detect real-world cybersecurity threats.
How does DNS communication work?
When an end user enters a URL such as Varonis.com into their browser, the following happens:
- The browser will first check its local cache for already stored DNS data.
- If this data is missing, it will query the upstream DNS server, which is usually your router on the local network.
- DNS, , DNS, Google, Cloudflare Quad9.
- DNS- .
4.1. , DNS-, DNS « .com».
4.2. .com, « Varonis.com», URL.
4.3. « IP- Varonis.com», IP- . - The DNS data is then sent back up the chain until it reaches the end user's device. Along the entire route, each of the DNS servers will write the received response into its own cache for further use.
How do attackers poison the DNS cache?
There are many ways to poison the cache, and here are the most common ones: forcing the victim to click on a malicious link that uses embedded code to change the DNS cache in the user's browser; Hacking a local DNS server using a “middleman attack”. The aforementioned "middleman attack" uses Address Resolution Protocol (ARP) spoofing to redirect DNS requests to an attacker-controlled DNS server.
What is DNS Cache Poisoning?
DNS cache poisoning is the act of replacing an entry in the DNS database with an IP address leading to a malicious server controlled by an attacker.
How is DNS spoofing performed?
A hacker performs a DNS spoofing attack by gaining access and altering the DNS cache or by redirecting DNS queries to his own DNS server.
What is DNS Spoofing?
DNS spoofing means that the URL that the user enters into a browser, such as varonis.com, does not actually lead to the correct official IP address associated with that URL. Instead, the user is redirected to a malicious server controlled by the hacker.
Why is DNS spoofing dangerous?
DNS spoofing is dangerous because, by its very nature, Domain Name System (DNS) is believed to be reliable, so it is often not protected by any kind of encryption. This leads to the fact that hackers can spoof records in the DNS cache to further theft of data, injecting malware, phishing and blocking updates.
The main threat posed by a DNS spoofing attack is data theft through phishing pages. In addition, there is a risk of malware being introduced under the guise of downloadable files that look real. Also, if the system is updated via the Internet, an attacker can block the update by changing the DNS records so that they do not lead to the desired site.