
How can you monitor the number of attacks against the company's infrastructure? One way is to install special systems called honeypots. A honeypot is a trap that allows you to record, in whole or in part, a sequence of actions that are performed by an attacker. In this article, we will try to select and configure a honeypot, and we will use the ELK stack as a monitoring system.
Choosing a honeypot
. , TOP 25 MITRE. . , , .
. - , . , :
-
, , . , OpenSource.
, -. CMS. - , . . , :
Symfony2 EoHoneypotBundle;
Python Share;
nodeJS ;
c Drupal CMS;
ELK.
, . , . :
, . Ubuntu 20.04, Virtual Box. , Image, Docker Hub. Image Google :
honeypot ELK inurl:hub.docker.com
Docker Hub , Image. Image ELK Image ELK .
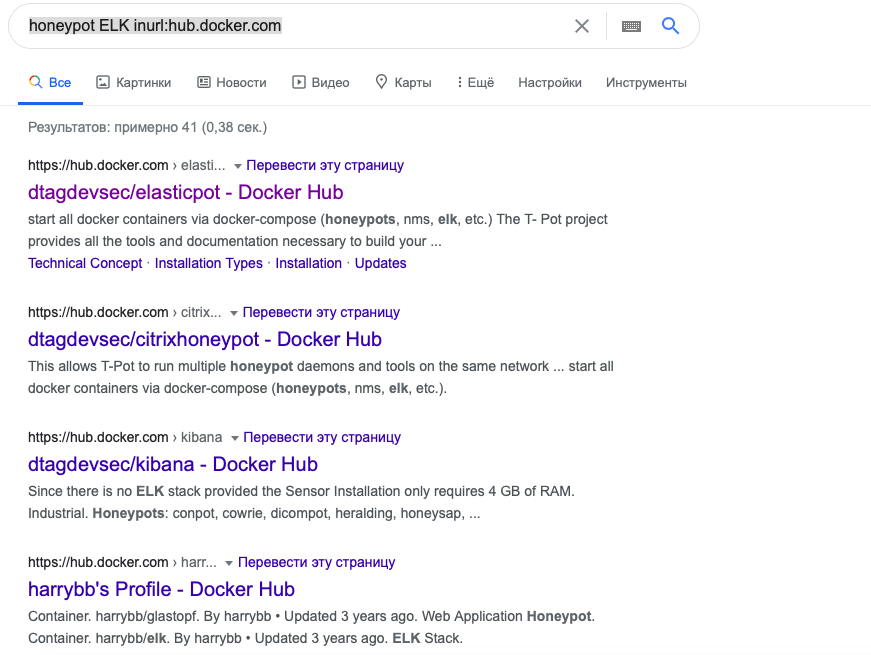
. ELK+honeypot. Docker:
git clone https://github.com/kobadlve/underworld.git
:
docker-compose build docker-compose up
FROM logstash
MAINTAINER kobadlve
USER root #<= new line
ADD conf/ /root/conf
...
. , nmap:
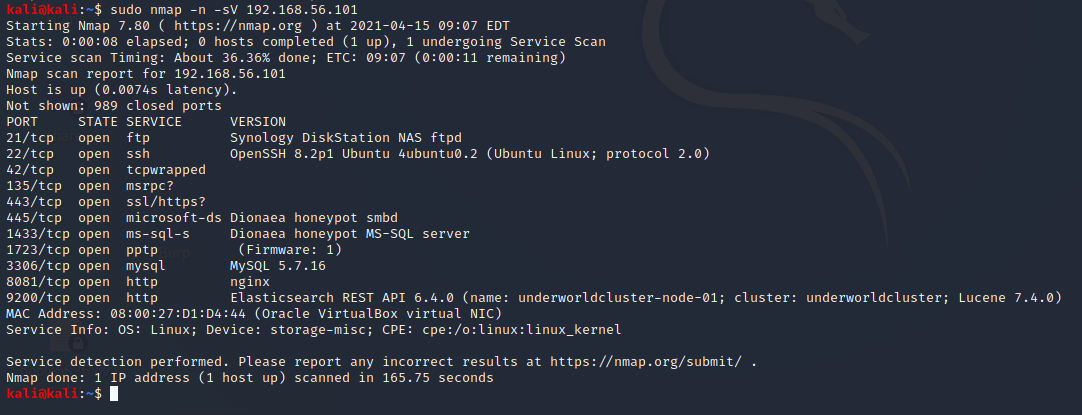
Kibana ( 5601). , . , .
OTUS " : Zabbix, Prometheus, ELK". .