The problem is, these are not really leaks. Both databases contain only publicly available information about users. No hacking happened, as reported by the affected (exclusively from negative PR) organizations ( Clubhouse statement, LinkedIn statement ). Someone even suggested writing search engines to hackers - they regularly extract and store the same databases on their servers,
As a result, there was a discussion of terminology all week: what can even be considered a data breach? In particular, Troy Hunt, the owner of Haveibeenpwned, does not consider the public database of Clubhouse users a leak :
At the same time, he also added a Facebook database to his service. To do this, it was necessary to introduce verification not only by e-mail, but also by phone number, since relatively few mail addresses were leaked two weeks ago (2.5 out of 500 million). The discussion was fueled by Facebook's announcement that the social network will not notify users whose data has become public.
The management of the service can be understood: it is one thing when an incident is discussed in a crowd of IT specialists, and another thing when half a billion users know about it. There is also a more weighty argument. Yes, having gained access to the database, someone can find out your phone number, address, place of work and other information, even if you have hidden it in your profile. But there are no passwords in the database. There is no direct threat of account hacking, only an indirect danger that the data will be used against you, your accounts in any services, your bank account.
Let's say your data is leaked - what to do? It is not necessary to change the password. Reissue a credit card? Change your first and last name? Phone number? Find another job? Move? Perhaps the only thing that a user of social networks is able to do in such a situation is not to transfer actual personal information to network services. But even this is not easy to achieve: in some difficult cases, the same Facebook requires not only a phone number, but also a scan of an ID. Don't use social media at all? Yes, but there is evidence of long-deleted accounts in the Facebook database, and even information about people who have never used the social network at all.
What else happened
The Kaspersky Lab blog has published a detailed history of ransomware , up to the first such attack back in 1989.
The APKPure application, which allows you to install applications on smartphones running Android, bypassing the official Google Play store, has been distributed for some time with an appendage in the form of a Trojan. Most likely, the application was compromised through an ad SDK.
Microsoft analysts are investigating a malicious campaign that uses feedback forms on websites. The organizers of the attack sent through them requests to remove unlicensed photographs on behalf of the angry copyright owners.
Sophos introduces the funny term beg bounty. This article describes examples where a simple scan of websites or mail servers found trivial vulnerabilities (or even just not ideal settings, such as the absence of DMARC). After that, the discoverers demand money or gifts from the server owners, or well, at least something .
The software update servers of Gigaset (a brand of a smartphone manufacturer that survived numerous resales of Siemens / BenQ mobile brands) were hacked , and malicious applications were distributed from them for some time.
HackerNews reports that it sends malicious files on LinkedIn under the guise of job offers.
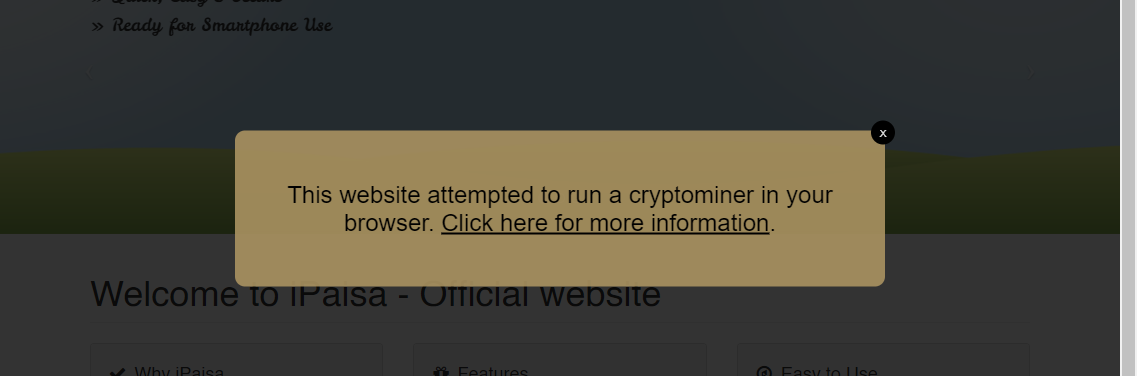
Troy Hunt took control of the Coinhive domain. Before closing in 2019, Coinhive offered publishers an extremely dubious way to make money: the Monero digital currency was mined on the computers of website visitors, if the service code was inserted into it. Naturally, the closure of the service did not remove the code from tens of thousands of sites, the owners of which may not even be aware of its existence. Hunt made it easy for them to find the problem: a request from a Coinhive script now results in a huge banner on top of the content.