Creation of unique malware requires a lot of resources, so many hacker groups use massive, often publicly available malware in their attacks. Widespread use inevitably leads to the fact that such a tool gets on the radar of antivirus companies, and its effectiveness decreases.
To solve this problem, hackers use packaging, encryption and code mutation techniques. Such techniques are often implemented by separate tools - "crypters" or simply "packers". In this article, using the RTM banking Trojan as an example, we will look at what “packers” can be used by cybercriminals and how these “packers” complicate malware detection.
The full version of this study is available here .
Packer-as-a-service
The hacker group behind the distribution of RTM regularly carried out mass phishing emails with malicious attachments until the end of 2020. This process, apparently, took place automatically.
Each of these attachments contained significantly different files, while the final payload remained virtually unchanged.
— «». , RTM, «», 2020 .
- , . , , packer-as-a-service. , . .
Rex3Packer
RTM, , 2019 . , , — 2020 .

- , : (recursion), (reverse) PE- (reflection) — Rex3Packer.
:
VirtualAlloc , .
( , .text).
.
PE- ( ). ebx. . , , PE- , .
.
VirtualProtect RWX PE-.
.
.
PE .
— PE-. PE-, .
. : , .
16 , 4 4 :
,
(PE-),
(*), ,
(1, 2, 4).
:
( , 10011000 00011001).
(1, 2, 4), N = 9, 5, 3 . — (N – 1) ( 8, 4, 2).
N-1 : . , 00000001, 00010001 01010101 . . OR , .
, 4 . .

4. PE-, (*) . , , . (*) .
, :
WinAPI. , , , .
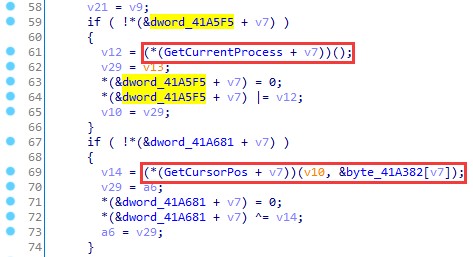
— ( ), .
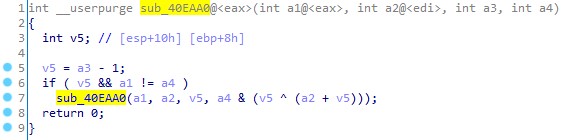
. , .
RTM, Rex3Packer , .
|
SHA256 |
|
|
6e9c9b72d1bdb993184c7aa05d961e706a57b3becf151ca4f883a80a07fdd955 |
|
|
8d44fdbedd0ec9ae59fad78bdb12d15d6903470eb1046b45c227193b233adda6 |
|
|
3be91458baa365febafb6b33283b9e1d7e53291de9fec9d3050cd32d98b7a039 |
|
|
9b6af2502547bbf9a64ccfb8889ee25566322da38e9e0ccb86b0e6131a67df1e |
|
|
d1060835793f01d1e137ad92e4e38ef2596f20b26da3d12abcc8372158764a8f |
|
|
18cc92453936d1267e790c489c419802403bb9544275b4a18f3472d2fe6f5dea |
HellowinPacker
2020 RTM — HellowinPacker, 2021 . . , .
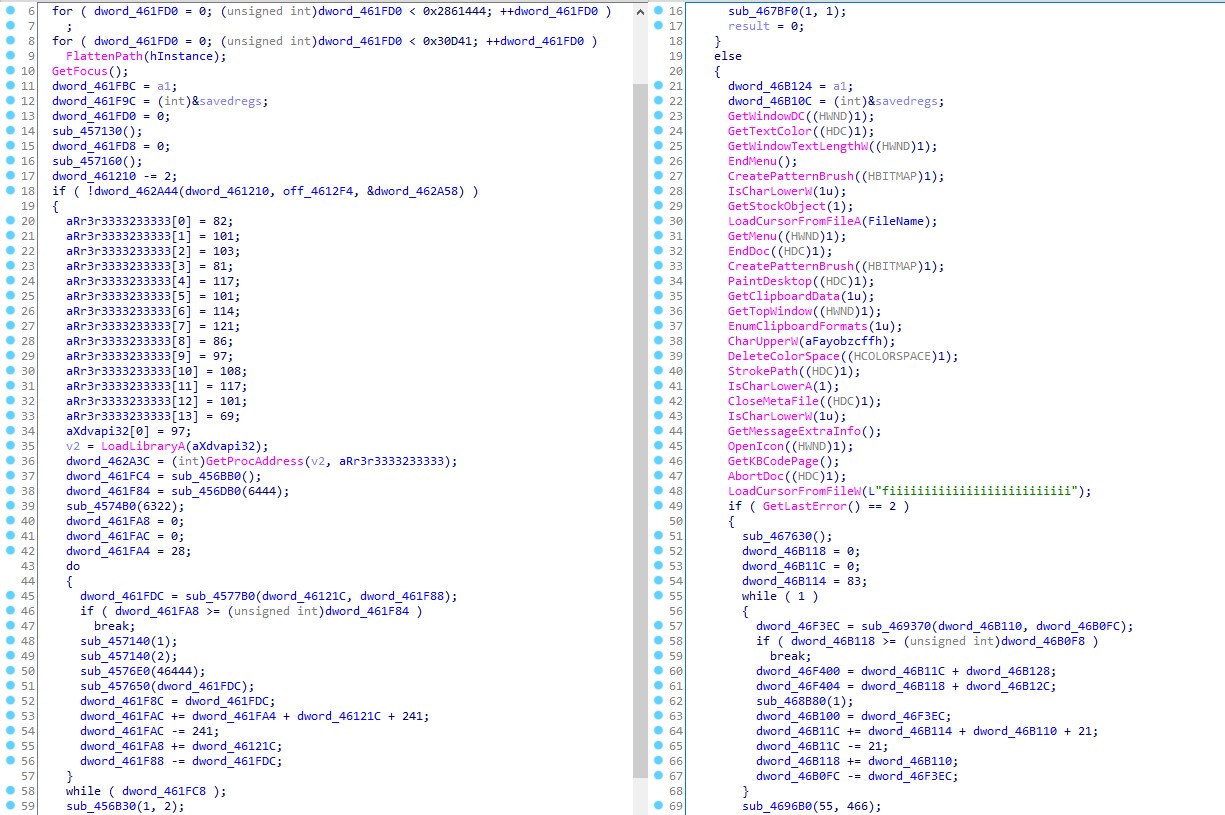
. . .

, Rex3Packer, HellowinPacker . , , . , , — .
, — HKEY_CLASSES_ROOT\Interface\{b196b287-bab4-101a-b69c-00aa00341d07} ( ) (Default). .
GUID .
, .
, (, ). VirtualAlloc RWX. X . Y .

4 :
(DWORD),
,
xor , Z.
Rex3Packer, HellowinPacker WinAPI, . . , .
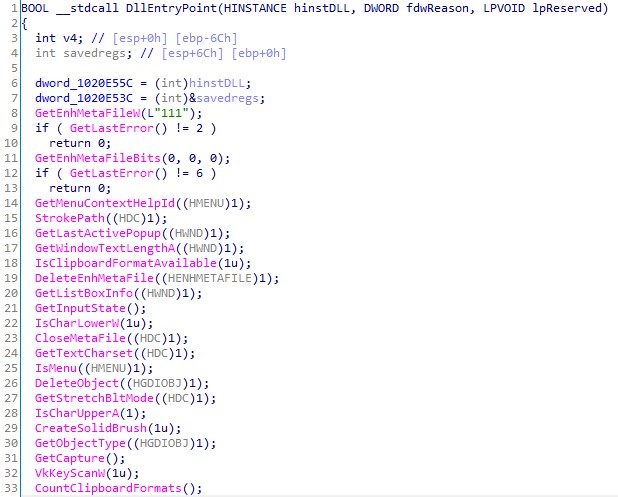
WinAPI imphash.
: ( ). WinAPI, (, 0 ).
HellowinPacker 2014 . . :
|
SHA256 |
|
|
1e8b814a4bd850fc21690a66159a742bfcec212ccab3c3153a2c54c88c83ed9d |
|
|
44ede6e1b9be1c013f13d82645f7a9cff7d92b267778f19b46aa5c1f7fa3c10b |
|
|
f5dfbb67b582a58e86db314cc99924502d52ccc306a646da25f5f2529b7bff16 |
|
|
54ff90a4b9d4f6bb2808476983c1a902d7d20fc0348a61c79ee2a9e123054cce |
|
|
c2482679c665dbec35164aba7554000817139035dc12efc9e936790ca49e7854 |
, . , («») . . : .
, , . : . . , , (, PT Sandbox) . , . , — , PT Network Attack Discovery.
: