We decided to share our vision of how to manage such risks in the context of cybersecurity. Since the topic is vast, we will not try to grasp the immensity in one post, but we will make a cycle of several parts. Today we will talk about what the Digital Risk Protection process is and analyze one of its components - monitoring digital traces.

What is Digital Risk Protection
Digital risks cannot be called any fundamentally new challenge for information security services. But the development of social networks and the Dark Web is pushing information security specialists more and more often to go beyond perimeter protection and turn their eyes to the outside of the barricades. Digital Risk Protection (DRP) will help you meet digital threats fully armed. It is a proactive strategy for countering external threats, which is based on monitoring the organization's digital footprint in various segments of the Internet.
The starting point of the DRP process is considered the "Digital footprint", that is, the collection of data about the actions of the subject in the digital space. These are the very examples with which we started this article. Digital footprints can be active or passive. The former includes information posted by the company on purpose, as in the example of a vacancy with redundant details about the technology stack used. The latter can be divided into two types: information published by the company unintentionally, for example, if a colleague opened ports on the Internet, and published by third parties - the same client database hosted by cybercriminals, or a site backup made publicly available on GitHub by a contractor.
When organizing the DRP process, the security service needs to focus on monitoring the passive digital footprint as less manageable by the organization, but at the same time, the danger of an active digital footprint should not be underestimated.
DRP goes hand in hand with cyber intelligence, i.e. Threat Intelligence (TI). In some organizations, the DRP process is even partially or fully implemented as part of the TI strategy. Despite the differences in these processes, in our opinion, it is not so important in which paradigm the DRP is implemented. The main criterion for success will be precisely the quality of its implementation. In addition, it will be much clearer for the business why to invest in separate DRP areas than in separate TI components.

DRP and TI processes. Source: securityboulevard.com
In search of the digital footprint: monitoring
DRP includes three main procedures: monitoring (detection), analytics and response (mitigation). Discovery is the basis of the whole process, it is at this stage that it is necessary to determine the answers to three key questions: what, where and how to search?
What to look for?
The first place to start is to create a list of information or digital assets that are most at risk. These can be any digitally owned or related entity. When compiling such a list, it is necessary to take into account the scope of the company, its main business functions and the technologies used.
For greater structuring, it is convenient to divide assets into three types:

Where to look?
All three parts of the Internet should be considered as a source for searching: the Open / Surface Web, the Deep Web, and the Dark Web.
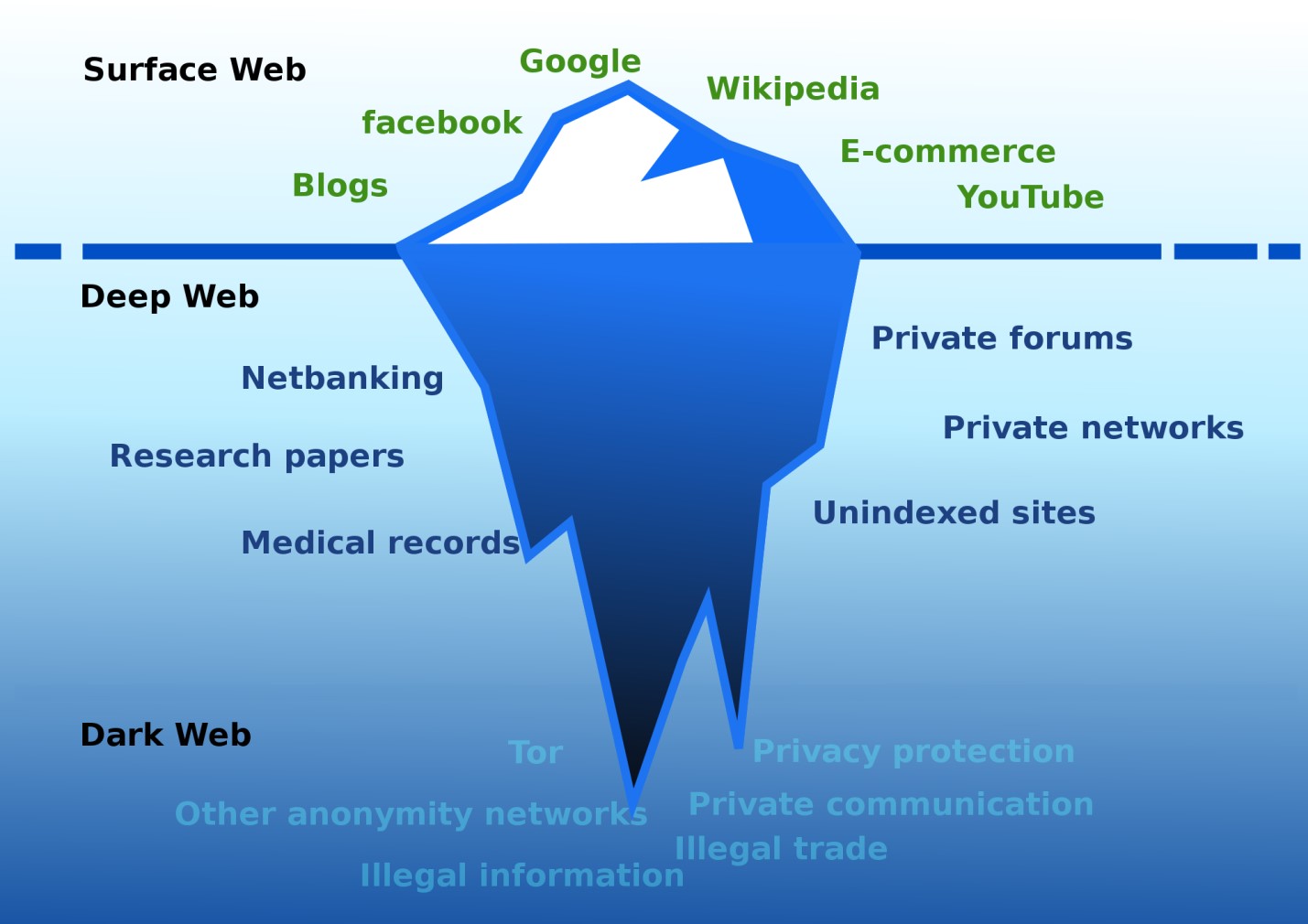
Different segments of the Internet. Source: wikimedia.org
Spoiler "Three parts of the Internet"
Open / Surface Web - an indexed part of the Internet, available for search through standard search engines.
The Deep Web is a non-indexable part of the Internet that is searchable through standard search engines. It contains several times more information than the Open Web.
The Dark Web is a non-indexable part of the Internet, accessible through specialized software.
Where exactly in them to look for digital footprints that pose the greatest threat? In our experience, it is worth covering all areas in which digital assets or elements of an organization's digital footprint can be found. In some cases, sources of information can be hidden behind a certain technological solution.
So, here's what a list of common sources of information might look like:
- Search engines
- Social media (social networks, messengers)
- Elements of external infrastructure
- Industry and crime forums
- Job Posting Sites
- Dark web (I2P, ToR, etc.)
- Specialized databases
How to search?
At this stage, you need to go to the direct collection of information of interest for subsequent analysis. Conventionally, there are two methods of obtaining information: with the use of automated tools and without their use.
"Manual" search does not mean that you need to select a person who will analyze the selected data sources day and night. The key feature of the method is that employees of the organization will be the main source of information. First of all, it is necessary to connect the marketing and HR departments, that is, specialists who directly interact with the "outside world", to the DRP process. Establishing a transparent process of communication to obtain information about potentially fraudulent sites and negative discussions on social networks is not expensive and can be useful as no other solution.
It is practically impossible to organize the DRP process at the proper level without the use of automated means of finding a digital footprint. For these purposes, you can use both paid and free tools. In addition to the quality of the information received, it is important to pay attention to the possibility of integration. At a minimum, you need to configure email notifications, the best option would be to integrate monitoring tools with the solutions used to create a single entry point for receiving information about incidents.
Using publicly available automated digital footprint tools allows an attacker to look at an organization. It is important for information security specialists to understand the techniques and techniques used by attackers at the reconnaissance stage, that is, in the process of collecting information. To do this, it is useful to study the MITER ATT & CK matrix, namely the Reconnaissance and Resource Development parts, which were previously part of a separate PRE-ATT & CK domain. These tools will help build a permanent process of gathering intelligence information, which will cover some of the techniques of the reconnaissance stage, or at least be with the attacker on equal terms.
The main advantage of paid tools is ease of use, a wider accumulated base and the ability to easily integrate with existing solutions. In our experience, some sources of information will be difficult to cover without the use of paid funds. Dark Web monitoring is a prime example of this.
Choosing tools for monitoring
For completely "manual" control of the company's presence on the Internet, information security specialists simply do not have enough hours a day. A whole market for Digital Risk Protection (DRP) solutions and services has emerged to make it faster and easier to find digital footprints. Its target audience, according to Gartner, will grow to 10% in the next five years - from 1% in 2020. Class solutions provide visibility to various network segments to identify potential threats and provide contextual information about the participants in these threats, tactics and processes used to carry out illegal actions. Providers of such solutions mainly provide access to a web portal that aggregates information about an organization's digital presence. DRP products typically support integration with a variety of protections and minimize analytics and response costs.

Choosing tools through a service provider
One way to choose a DRP solution is to contact the MSSP. In this case, it is possible to implement on a turnkey basis many unique and complex queries without the need to search and test tools, as well as the content of a team of analysts.
For us, as an MSSP, the starting point in the search for tools and the creation of custom solutions was to identify the main DRP areas that are interesting to the market. In our opinion, such areas are:
- (Brand Protection) — ( , , ..), . , DRP — , . , , , , , .
- (Sensitive Data Monitoring) — « » (Open/Deep/Dark web), .
- (Assets monitoring) — , (, , ).
- OSINT — , DRP-, , .
conduct an independent market analysis, test selected tools, integrate with existing information security / IT systems (SIEM, ticketing / IRP systems), etc.
The approach to finding tools for an organization that performs this process on its own will be different, since the tasks they face are more specific.
The best option would be to adhere to a tracking global strategy:
- if it is necessary to implement a complex task affecting all areas, the optimal solution would be to use a DRP solution as the main tool for monitoring external sources;
- if it is necessary to cover certain areas, use:
- specialized monitoring systems (Dark Web monitoring tools, Brand protection tools, External asset monitoring tools, Data leakage detection tools, etc.)
- Open source (including OSINT tools)
OSINT-tools in their pure form are considered primarily as a means of enriching information, conducting complex investigations, but in some cases and in the absence of ready-made solutions, they can be used as a means of monitoring or situational awareness.
Overview of publicly available tools
Let's list the popular publicly available tools (in some cases, shareware) and solutions that can be used to monitor an organization's digital footprint:
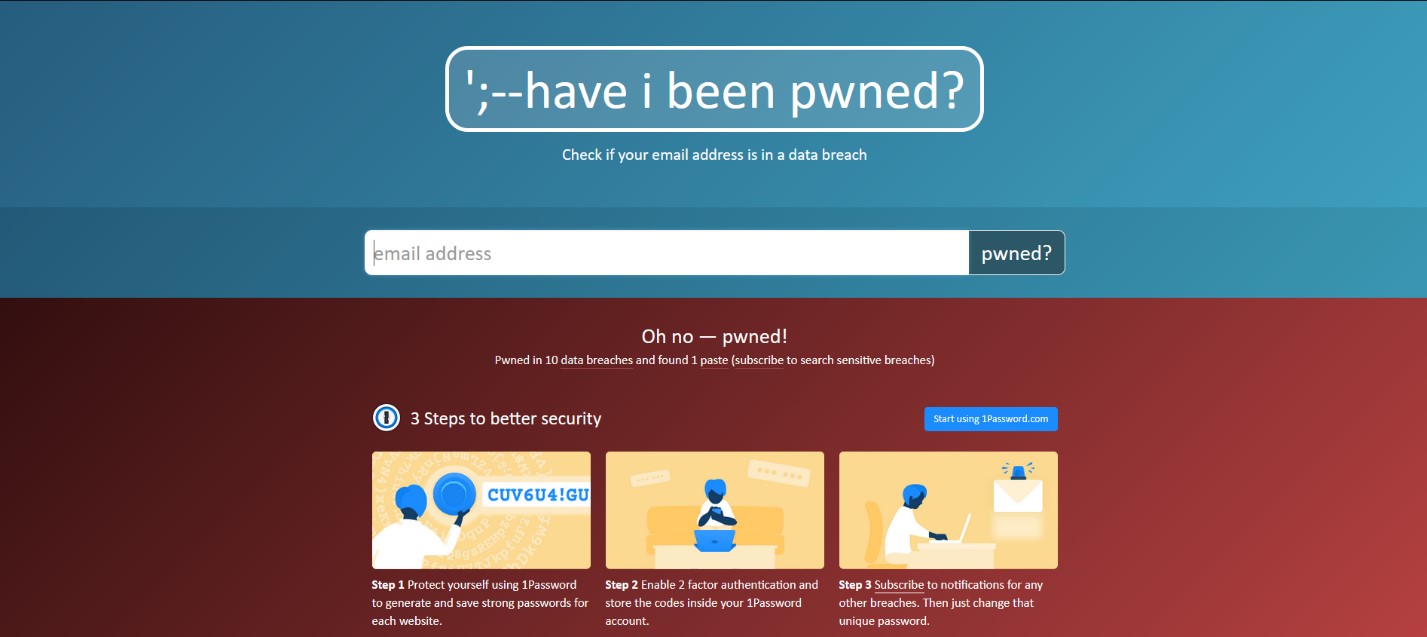
Have I Been Pwned - a service that allows you to get information about the fact of compromised credentials with the ability to monitor a domain name (when confirming the rights to it ownership). The presence / appearance of an employee's account in the database does not mean the fact of compromise. When an organization uses complex and frequently changing passwords, the likelihood of an employee using it is significantly reduced. In any case, the fact that employees have accounts in public databases is a good reason to revise the information security awareness policy.
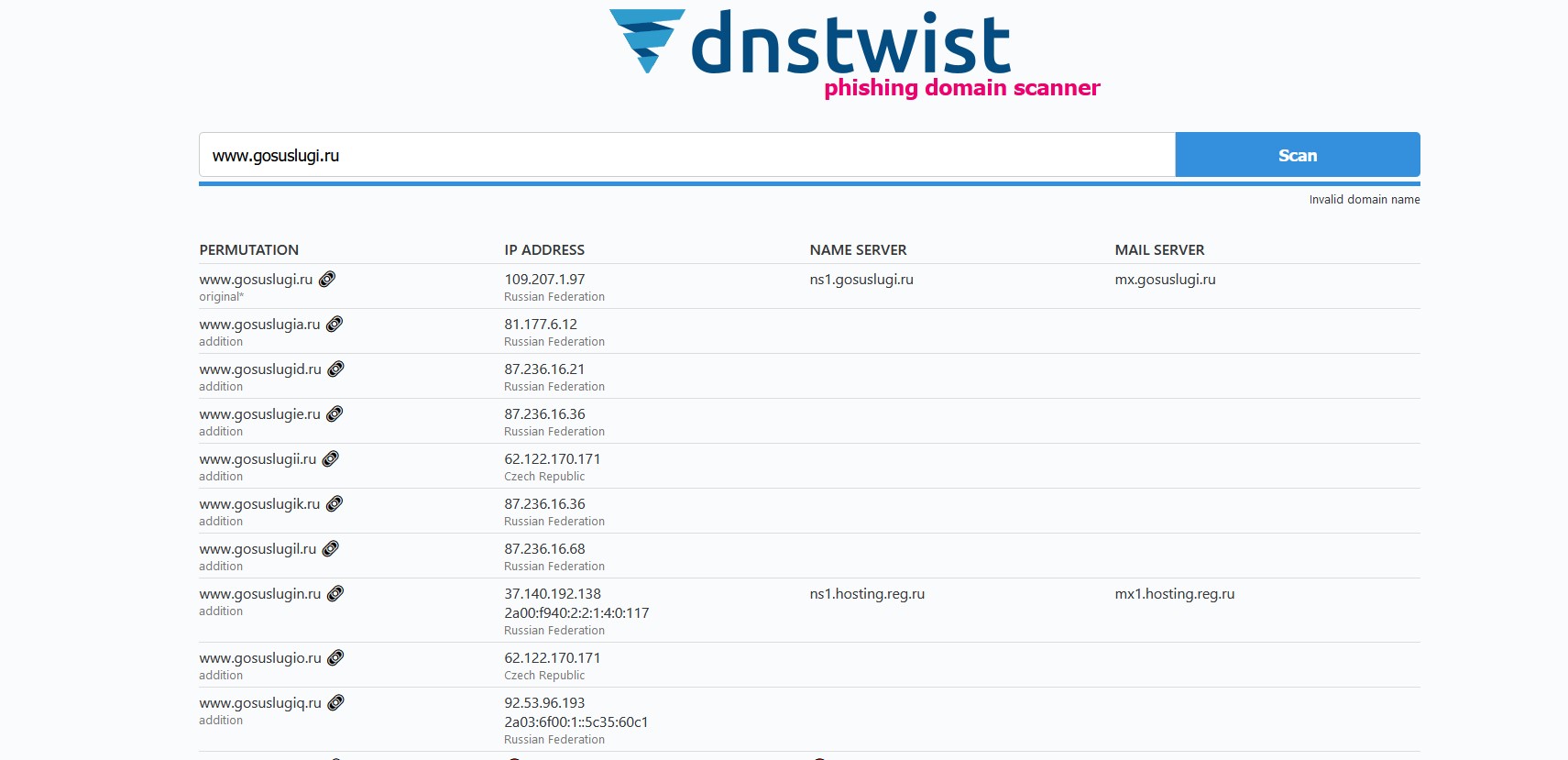
With the help of search tools for similar domain names, you can get up-to-date information about the facts of cybersquatting, fraud, planned target / phishing campaigns. An example of a tool of this kind is dnstwist (https://github.com/elceef/dnstwist, dnstwist.it ).
As part of the implementation of the Brand Protection strategy, it is necessary to monitor social networks, mobile applications, search results for fraudulent activities. For such purposes, you can use specialized tools for monitoring the Internet space. An example of such a tool is Social Searcher .
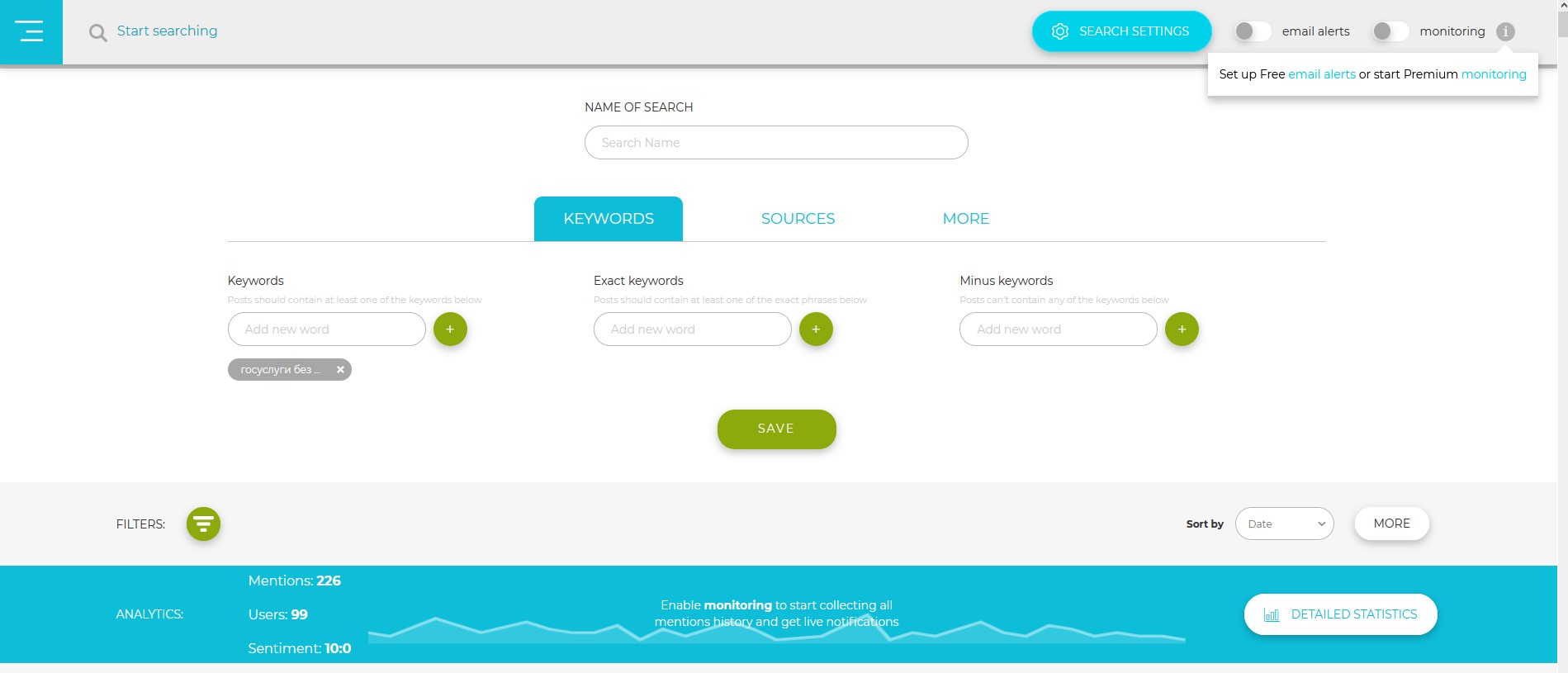
These kind of tools can cover not only marketing needs, but also be an excellent solution to identify illegal actions that affect the company's reputation / profit. In some cases, the number of offers / service cost can become one of the performance metrics of the information security department (the same can be attributed to offers on darkweb).
Unfortunately, not all freely available tools can cover the necessary information sources (specific to the Russian market) - in this case, you can use free web crawling frameworks (Scrapy, BeautifulSoup), which automatically collect the necessary information from web pages for later analysis. With the proper level of automation, you can analyze search results, social media, GitHub for traces of compromise, fraudulent activities. Already implemented crawlers can be found on github.com using "googling skills".
Monitoring GitHub for "sensitive" information is more relevant than ever. GitGraber does an excellent job with this task .... This tool characterizes not only flexibility in settings, but also the provided integration with Discord, Slack, Telegram.

Maltego and Lampyre are popular tools to automate the collection of information in the framework of investigation, construction and analysis of connections between various subjects and objects. These tools allow you to visualize aggregated data from a variety of public and private sources. Comparison of these products is beyond the scope of this article, but we can say that with certain advantages of Maltego, Lampyre has more Russian context, a more transparent pricing system (the absence of Transforms - additional functions that expand the product's capabilities), the ability to purchase a paid version in the Russian Federation.
Of course, this is not a definitive list of all kinds of tools for organizing specific parts of the DRP process. To find free monitoring tools, we recommend that you refer to the numerous articles on the topic "OSINT Tools", many telegram channels discuss various techniques and techniques for obtaining information about an organization. One way to find free tools is to go to the online GitHub repository. By searching the topics for the keywords "typosquatting", "Osint", etc., you can find a large number of tools that are applicable to cover the indicated sources of information.
Be sure to check out the excellent OSINT Tools and Resources Reference located at i-intelligence.eu/uploads/public-documents/OSINT_Handbook_2020.pdf , where you are likely to find the right tool for your specific task.
We will tell you how to approach the process of digital threat analytics and build a response process next time.
See you soon!
Author: Igor Fitz, Analyst of the Center for Monitoring and Response to Incidents of Information Security Jet CSIRT, Jet Infosystems