Valid certificates and DNS for services in local networks without a certification authority
This post will cover the installation and use of the http://local-ip.co/ service with valid certificates and DNS like xip.io, nip.io.
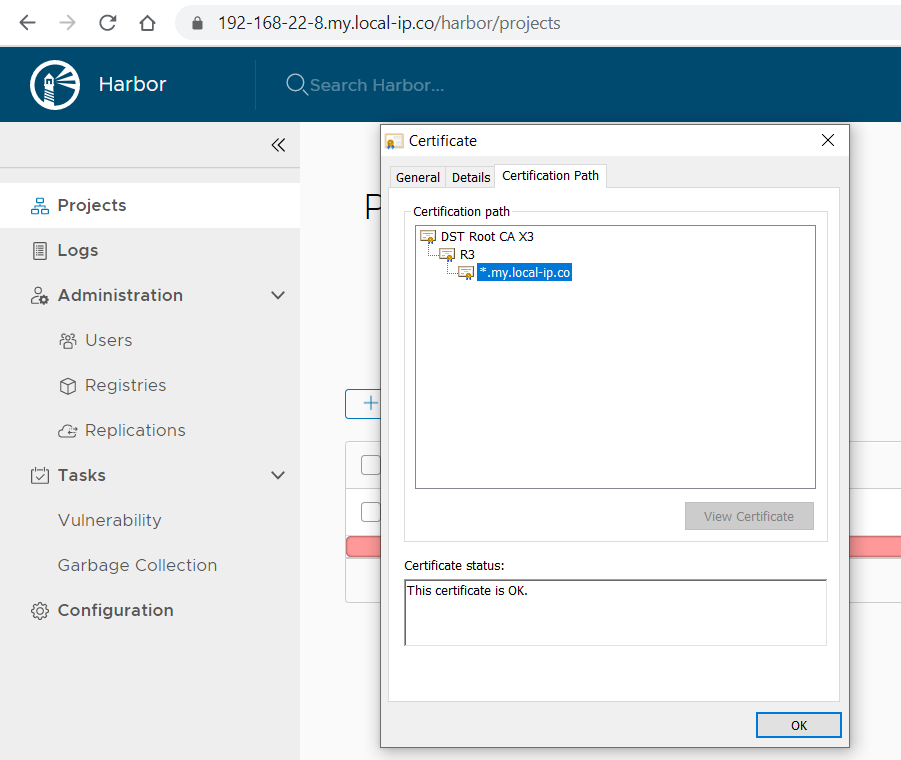
You can use a certificate for the domain *.my.local-ip.co
- certificate http://local-ip.co/cert/server.pem
- intermediate certificate http://local-ip.co/cert/chain.pem
- certificate key http://local-ip.co/cert/server.key
You will need to contact something like this:
- https://127-0-0-1.my.local-ip.co
- https://192-168-0-1.my.local-ip.co
- https://172-16-0-1.my.local-ip.co
- https://10-0-0-1.my.local-ip.co
Below is an example of installing harbor with a valid certificate.
Requirements:
Install docker and docker-compose
Downloading harbor
wget https://github.com/goharbor/harbor/releases/download/v2.2.1/harbor-online-installer-v2.2.1.tgz
Unpacking the harbor
tar xvf harbor-online-installer-v2.2.1.tgz
We prepare certificates from the project http://local-ip.co/
mkdir -p /data/cert/ cd /data/cert/ wget http://local-ip.co/cert/server.pem wget http://local-ip.co/cert/chain.pem wget http://local-ip.co/cert/server.key
Create a certificate chain
cat server.pem chain.pem > bundled_cert_file.pem
Rename the certificates to the domain name that you need.
cp bundled_cert_file.pem 192-168-22-7.my.local-ip.co.crt cp server.key 192-168-22-7.my.local-ip.co.key
Copying the config template to the config
cp harbor.yml.tmpl harbor.yml
Configuring hostname in harbor.yml
hostname: 192-168-22-7.my.local-ip.co
We indicate the certificate and key in harbor.yml
certificate: /data/cert/192-168-22-7.my.local-ip.co.crt private_key: /data/cert/192-168-22-7.my.local-ip.co.key
Start downloading images
./prepare
Launching harbor via docker-compose
docker-compose up -d
Or run the installation
./install.sh
Installing harbor via Ansible
To install harbor via ansible, we use the role https://galaxy.ansible.com/manueliglesiasgarcia/ansible_vmware_harbor
Downloading the role
ansible-galaxy install manueliglesiasgarcia.ansible_vmware_harbor
Below is the playbook for installing harbor via ansible
--- - name: Install harbor become: yes hosts: harbor pre_tasks: - name: update apt apt: update_cache=yes cache_valid_time=3600 when: ansible_pkg_mgr is defined and ansible_pkg_mgr == "apt" ignore_errors: true - name: Creates directory {{ playbook_dir }}/certs file: path: "{{ playbook_dir }}/certs" state: directory delegate_to: localhost become: no - name: Download http://local-ip.co/cert/server.pem get_url: url: http://local-ip.co/cert/server.pem dest: "{{ playbook_dir }}/certs/server.pem" delegate_to: localhost become: no - name: Download http://local-ip.co/cert/chain.pem get_url: url: http://local-ip.co/cert/chain.pem dest: "{{ playbook_dir }}/certs/chain.pem" delegate_to: localhost become: no - name: Download http://local-ip.co/cert/server.key get_url: url: http://local-ip.co/cert/server.key dest: "{{ playbook_dir }}/certs/server.key" delegate_to: localhost become: no - name: merge certificate shell: cat server.pem chain.pem > bundled_cert_file.pem args: chdir: "{{ playbook_dir }}/certs" delegate_to: localhost become: no vars: # Add a registry harbor_registry: - registry_name: "Test Harbor" registry_url: https://192-168-22-8.my.local-ip.co/ # Schedule an automatic scan of the docker images every hour harbor_schedule_scan: - cron: "0 0 * * * *" # Schedule an automatic garbage collection every hour harbor_schedule_gc: - cron: "0 0 * * * *" #Storge harbor installation file harbor_install_tmp: /root/harbor harbor_extras: - clair #Folder installed harbor harbor_install_dir: /opt/harbor # The cert and key path is located in your ansible master, not the target hosts # The default path for certs is controlled by this role See roles/default/main.yml harbor_ssl_cert: "{{playbook_dir}}/certs/bundled_cert_file.pem" harbor_ssl_cert_key: "{{playbook_dir}}/certs/server.key" #ends up in harbor.yml harbor_hostname: 192-168-22-8.my.local-ip.co harbor_db_password: admin roles: - manueliglesiasgarcia.ansible_vmware_harbor
Launching the playbook
ansible-playbook -i inventory.ini install-harbor.yml -e "harbor_admin_password=password_for_harbor"
Where password_for_harbor is the password for harbor.
Screenshot: