For future students of the course " Administrator Linux. Professional " and all those interested, we prepared an article by Alexander Kolesnikov.
The purpose of this article is to show what projects exist today for the automatic analysis of executable files for Linux. The information provided can be used to deploy a test bench for analyzing malicious code. The topic may be relevant for administrators and malware researchers.
Linux sandboxing features
The main problem of Linux sandboxes for analyzing applications is the limited support for the processors on which the operating system is running. Since it is very expensive to use its own physical machine for each architecture. How virtualized solutions like Hyper-V, VMWare or VBox are used as a compromise. These solutions do their job well enough, but they only allow virtualization on the architecture on which the main host is running. To run code for ARM, MIPS, and other architectures, you will have to turn to other products that can emulate the required processor instructions. Let's try to collect as many projects as possible and see what processor architectures are supported.
Cuckoo sandbox
Cuckoo. . , . , . :
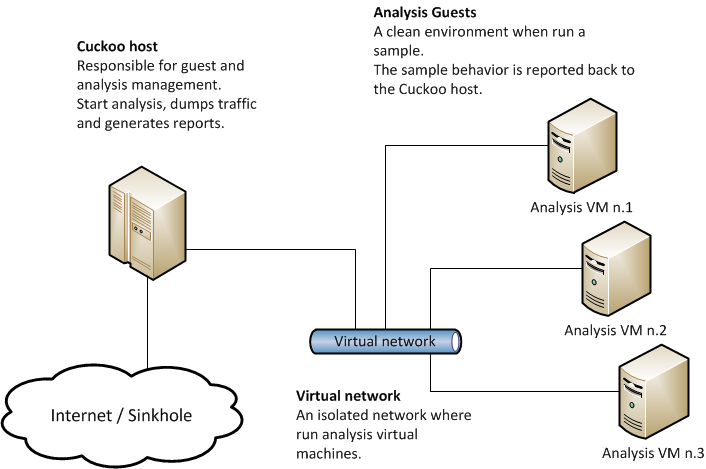
Windows. , Linux. , Windows, Linux. .
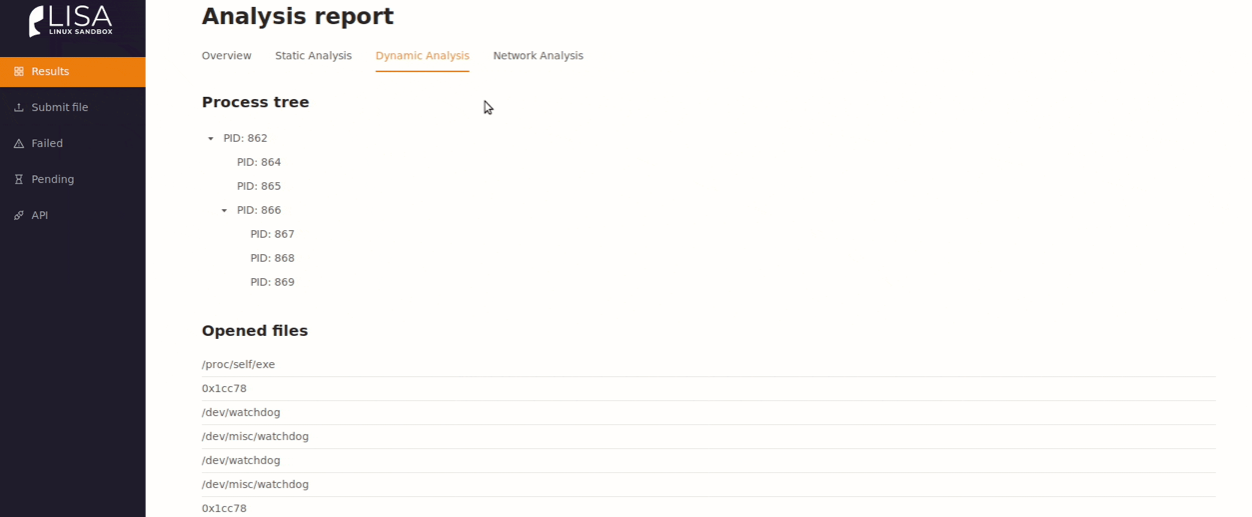
LiSA Sandbox
Opensource Linux. . , :
x86_64
i386
arm
mips
aarch64
- Qemu. . radare2, , : , , . , . , IoT . , , .
— Docker. . :
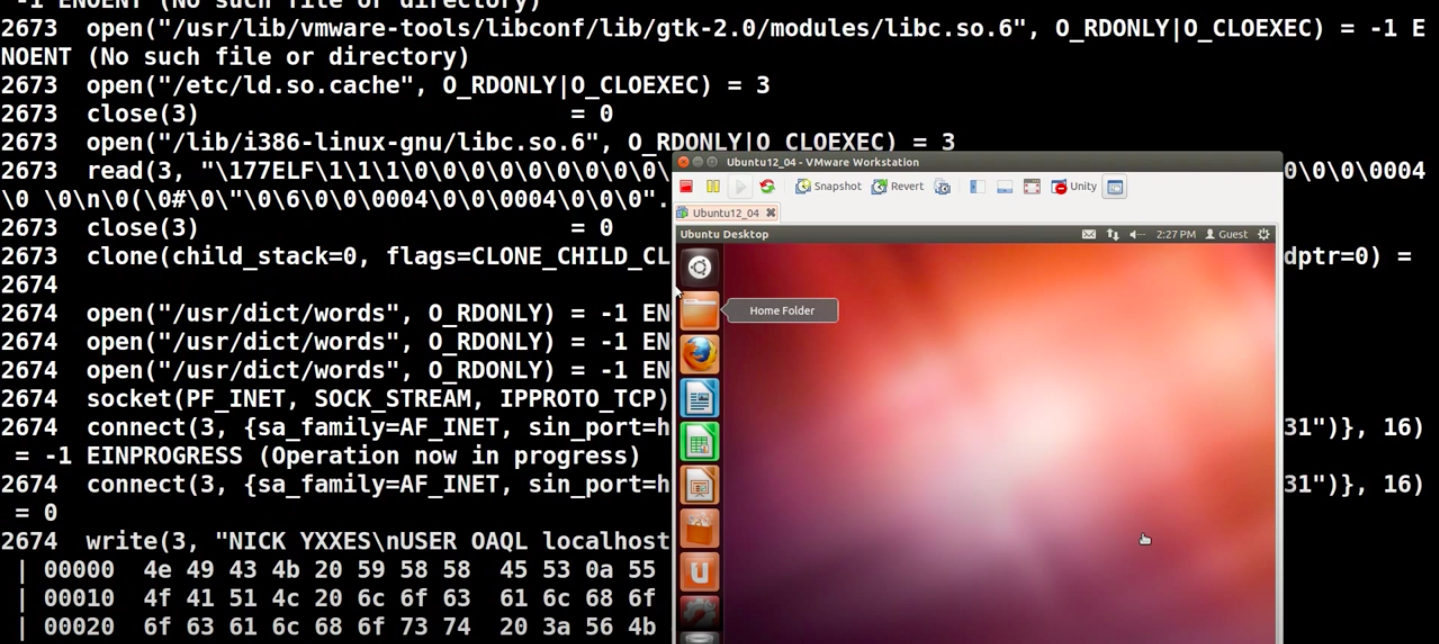
Limon Sandbox
, . .( ). , Python. . :
Yara
ssdeep
ldd
strace
Inetsim
tcpdump
volatility
sysdig
, . :
drakvuf Sandbox
. , . . , . , . , - . , . , json.
Detux
. . :
86
86_64
ARM
MIPS
MIPSEL
Qemu. . . , json.
, - . , :
radare2
Volatility
Yara
.
, , .
"Administrator Linux. Professional".
« Ansible ». , ansible . , , .. , . !