
ESET experts spoke about new malware targeting HPC clusters around the world. It is interesting for several reasons. Despite the rather small size of the code base (the samples analyzed were 25 KB in size), the malware is complex enough to carry out attacks on Linux, BSD, and Solaris and, potentially, can be suitable for attacks on AIX and Microsoft Windows. Another distinguishing feature is the ability to transform infected servers into new C&C at the operator's command. Due to the many tricks and small size of the code, the researchers named it Kobalos - after the mischievous ancient Greek spirits who once robbed Hercules and adored to deceive and frighten people.
The study published by experts describes the estimated initial vectors of compromise, authentication and distribution mechanisms, built-in functions, and provides a technical analysis of the malicious code. After that, the experts point out the signs of compromise and the applied methods of MITER ATT & CK.
We had the idea that people who have a poor command of English, but are not indifferent to current research in the field of information security, in particular, to the analysis of malware, would be interesting and useful to translate the analysis of such, in our opinion, unusual malware.
ESET Research analyzed Kobalos, a previously unknown, complex, multi-platform malware designed to run on Linux, FreeBSD and Solaris. Given that the victims are mainly well-known organizations, there is no doubt that they were targeted by the software. When deployed, Kobalos gives access to the compromised host's filesystem and remote terminal, allowing attackers to execute arbitrary commands.
Kobalos has remarkable networking capabilities. It can work either in passive mode or as a bot, actively connecting to its C&C servers. It is curious that these servers themselves have been compromised by Kobalos: the code for their use is in all samples of this malware.
Through extensive network research, ESET Research was able to identify and notify Kobalos victims. It is unknown when this software was developed, but its first known activity, confirmed by a victim, was recorded at the end of 2019. The group of attackers running Kobalos continued throughout 2020. Linux attack techniques continue to evolve, and malware authors put a lot of effort into improving their designs. Kobalos is one such program.
Main conclusions
- Kobalos is a multi-platform backdoor that runs on Linux, FreeBSD and Solaris. There are indications that this software may exist on AIX and even Windows.
- Kobalos , , , -. Kobalos , .
- Kobalos , .
- Kobalos C&C- . , .
- OpenSSH. Kobalos.
- Kobalos. , , - . , SSH.
If you have followed ESET Research in recent years, you may have noticed that we prefer to search and document server-side malware developed for Linux and other less common operating systems. One of the first such reports is dedicated to Operation Windigo and describes several software families that work together to redirect Internet traffic, send spam, and other malicious activities. Operation Windigo is based on Ebury, an OpenSSH backdoor that steals credentials. Ebury can compromise SSH client and server without modifying the OpenSSH executables. Instead, it modifies the library they are loading and patches functions to be able to start and steal credentials after loading the backdoor. The task is not easy, but the authors of Ebury managed to solve it.
After Operation Windigo, we discovered and described several other malicious programs for Linux, such as Mumblehard , Moose , Shishiga , and also described dozens of backdoors for OpenSSH in The dark side of the ForSSHe report .
Until now, we have not come across Linux malware that has been as difficult to analyze as Ebury. But this time the situation is different: unlike Ebury, the actions of Kobalos do not look so large-scale. The number of cars compromised by them is in the tens, and in the case of Ebury - tens of thousands. This article provides a complete technical analysis of Kobalos, the targets of attackers, and indicators of compromise that can help potential victims find malware and get rid of it.
Victims
After analyzing the malware, ESET conducted an extensive Internet scan looking for Kobalos victims. We were looking for specific backdoor behavior, which is characterized by establishing a TCP connection with a compromised host from a specific outgoing port.
Given the complexity of this software, we were surprised by the very small number of victims found. However, the goals themselves were clearly not chosen by chance: these are high-performance computers (HPC) and servers that are part of scientific and research networks. One of these computers had at least 512 GB of RAM and nearly petabyte disk storage. We also found other well-known victim organizations, such as an endpoint security vendor (not us!).
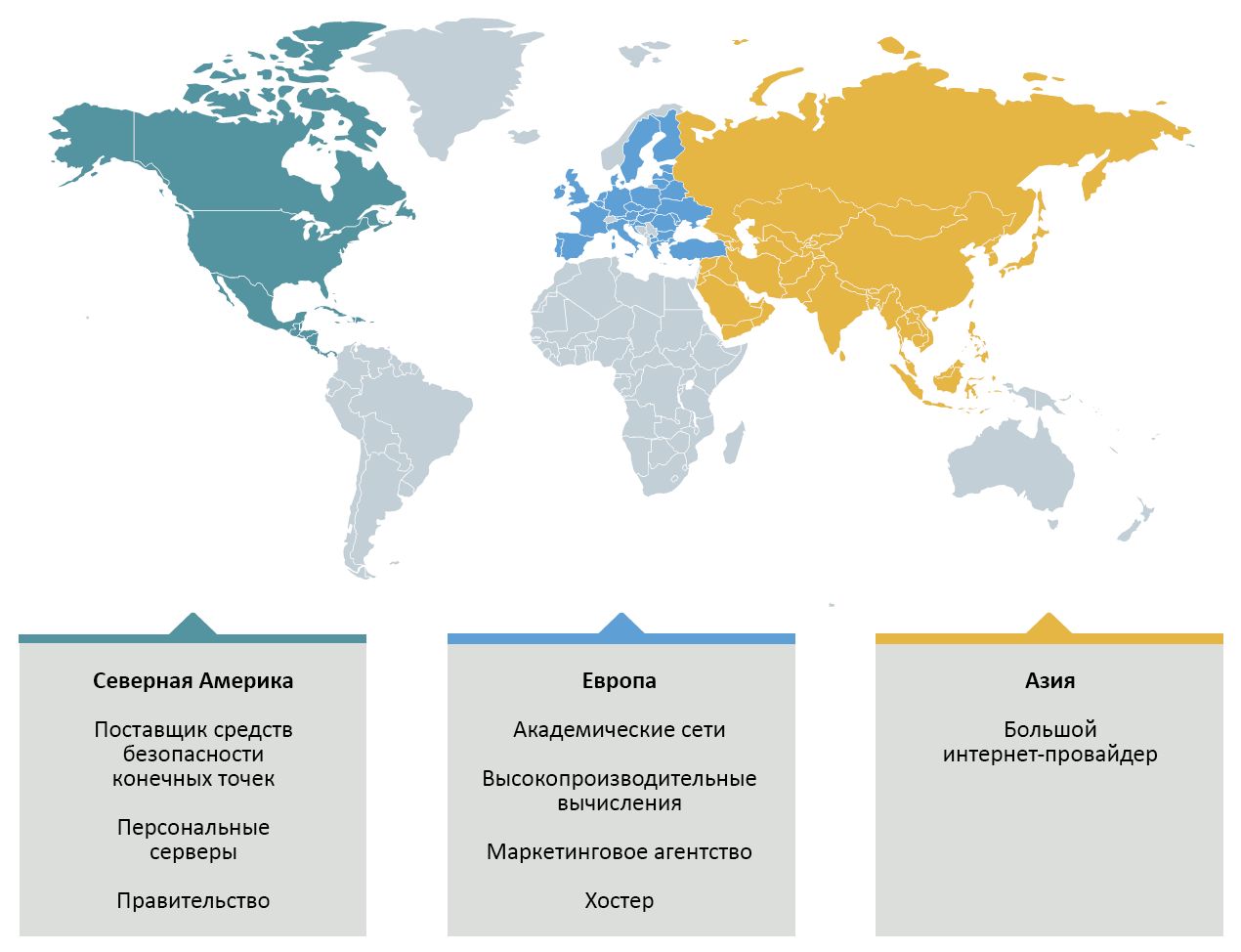
Figure 1. Industries and regions to which the compromised organizations belong.
In some organizations, multiple servers were infected at once. We notified all victims we found and worked together to remove the malware. Thanks to everyone who responded and shared information that helped us in this study.
Initial vector of compromise
We know not first-hand how the systems were compromised so that attackers could gain administrative access to install Kobalos. We can only speculate based on the evidence collected.
On the compromised machines whose sysadmins took part in the investigation, we discovered that the SSH credential stealing program was presented as a Trojanized OpenSSH client. File
/usr/bin/ssh
was replaced by a modified executable that recorded the username, password, target hostname and saved them to an encrypted file. Therefore, we believe that identity theft was one of the ways Kobalos was distributed. It could also explain why many academic networks were compromised: if any SSH client was used by students or researchers from several universities, then credentials for all these third-party systems could be stolen.
Another possible entry point could be the exploitation of a known vulnerability: some compromised machines were running old, unsupported or unpatched OS and applications, so the option using a known exploit is most likely. But you also should not exclude the possibility of using a currently unknown vulnerability.
Attack on networks for high performance computing
ESET has shared information with organizations that play an important role in resolving incidents in research and academic systems, such as the CERN Computer Security Team. They confirmed that from late 2019 to mid-2020, the HPC community was hit by a wave of three different attacks, some of which were publicly announced .
After many months of investigation, it is still unclear if these three waves were related to each other, or if it was just an unexpected coincidence. Malware operators used different tactics, techniques, and difficulty levels. On the other hand, it is strange that in different attacks some IP addresses coincided.
- The first wave used Kobalos, which is described in this study.
- The second wave focused on mining cryptocurrencies with a very different set of tools.
- The third wave was the largest, but its payload has not yet been determined.
Indirect signs of compromise as a result of the second and third waves were described by the European Grid Infrastructure Computer Security Incident Response Team in the form of incidents # EGI20200421 and # EGI2020512 .
It is unclear why the HPC community is dominant among the victims of these attacks. HPCs are of interest, of course, but they are usually more difficult to penetrate than other R&D servers. Through a distributed community-based incident response process, CERN and other teams involved have identified a number of outdated architectures and suboptimal security practices that have played a key role in the proliferation of attacks. In addition, most of the victims from the HPC community were ill-equipped to conduct investigations, especially in terms of monitoring system activity.
Kobalos Review
Kobalos has numerous capabilities to access compromised systems and hide traces of their use.
Access to compromised systems
First, Kobalos has general commands for reading and writing to the file system, as well as for starting a terminal and executing arbitrary commands. Unfortunately, there is no specific payload in the program that would suggest the intentions of the authors. Most likely, operators run a command shell through the terminal and execute the commands they need.
Availability
Secondly, Kobalos has a number of features that allow you to establish a network connection between operators and the malware being executed. The software provides its external accessibility in several ways:
- Opens a TCP port and waits for an incoming connection (this mode is sometimes called a passive backdoor).
- Connects to another Kobalos instance that is configured as a C&C server.
- Waiting for connections to an already running legitimate service, outgoing from a specific TCP port.
The latter method requires replacing the running service with another that contains the Kobalos code. In all cases where we noted the use of this method, the attackers had to modify the running OpenSSH server. The file was
sshd
completely replaced, so that the program continued to work even when the service or system was restarted.
Authentication and network encryption
Third, to run the backdoor, you need to authenticate its clients, which must have a private RSA-512 key and password. After checking them, Kobalos generates and encrypts two 16-byte public key keys using the RSA-512 algorithm and sends them to the attackers. These two keys are used for RC4 encryption of subsequent inbound and outbound traffic.
Port change
Fourthly, during authentication, the operator can continue to interact over another TCP connection. Upon request, Kobalos can start listening to the desired port and transfer all subsequent communication to it. Data passing through this channel is encrypted using RC4 keys that were created during authentication.
Proxying to other compromised machines
Fifth, Kobalos can be used as a proxy to connect to other servers it compromises. This is not an ordinary TCP proxy: it requires encapsulation of data in special packets, and also supports the above port change: for this, a command is sent that "switches" the connection.
Proxies can be chained, which means operators can use multiple Kobalos compromised machines to connect to target servers.
A set of possibilities
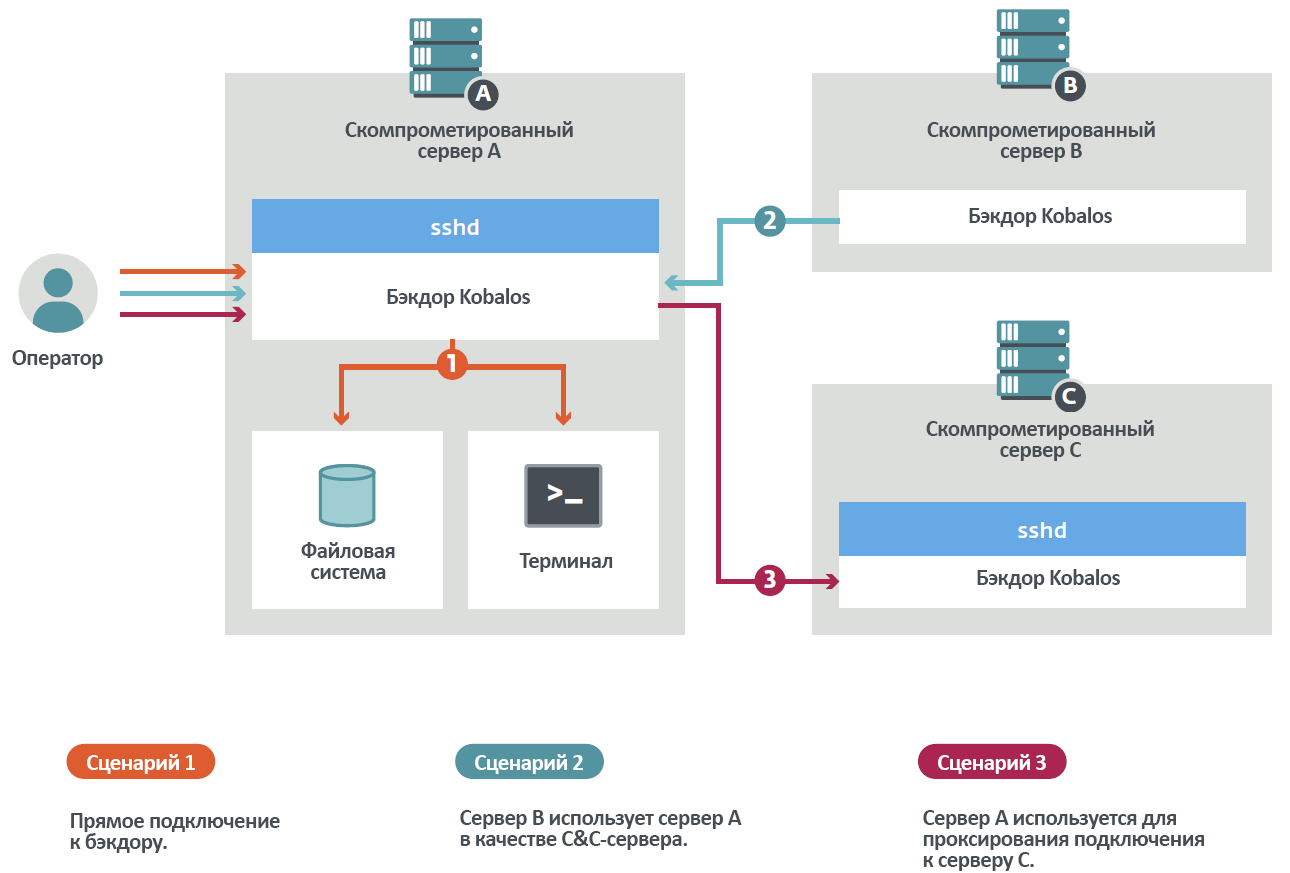
Figure 2. Overview of Kobalos capabilities and possible scenarios for accessing compromised servers.
The first scenario is a direct connection to compromised servers to access their resources. In the diagram, the backdoor runs inside the OpenSSH server process and expects the connection to have a source port. The operator must use the correct source TCP port to communicate with the backdoor.
The second scenario is arguably the most challenging, but there are some unique features of the Kobalos associated with it. The operator can run the C&C server from any server running this software. No additional code is needed for this, all functionality is already built in. After its launch, the C&C server checks the list of connected bots, and the operator can connect to any of them. The last node requires authentication, and enforces end-to-end encryption using RC4 key exchange. To ensure such a scheme of work, the Kobalos instance on server B must have the IP address and port of the C&C server running on server A. Server B exchanges traffic only with server A, hiding the operator's IP address.
In the third scenario, Server A is used to proxy the connection to Server C. This also applies authentication and forced end-to-end encryption. The operator can set the source port when connecting from Server A to C. This means that Server A can be used to connect to Kobalos instances that are waiting for a connection from a specific port.
Kobalos Technical Analysis
For the first time, we analyzed a trojanized OpenSSH server. The size of the malicious code and data of Kobalos is quite small: about 25 KB for x86-64 samples. Curiously, all the code is packed into one function. There is only one call to this function in the legitimate OpenSSH code.
Kobalos is complex software. Obviously, its developers put a lot of effort into its creation. The authors have implemented numerous features and implemented their own obfuscation.
Obfuscation
Exceptional flattening of control flow
The fact that the code fits into one function does not mean that the control flow is linear. Kobalos recursively calls its function to perform the required subtasks.
Figure 3. Kobalos control flow graph.
The first parameter to the function is the action to perform. Kobalos can perform 37 actions. These are listed in the Kobalos Built-in Features appendix , which helps you analyze the current and likely future versions of this software. The function also serves as a signal handler
SIGCHLD
to gracefully terminate the child process and
SIGALRM
to handle the connection timeout.
As far as the Kobalos source code is concerned, it might be like compiling the C code below. Part of the conversion can be automated by function inlining by the compiler, but assigning numeric identifiers to all functions and handling the same number of arguments in functions requires manual work or special tooling.
| Before | After |
|---|---|
|
|
Figure 4. This C code shows what the Kobalos source code might look like after aligning the control flow.
Encrypted string values
Kobalos code and data do not contain plain text string values. Only a few short strings encrypted with RC4 are used here. They are decrypted immediately after the initial interaction with the program, but before authentication. For all the samples we analyzed, one key is used -
AE 0E 05 09 0F 3A C2 B5 0B 1B C6 E9 1D 2F E3 CE
.
Decoded string values:
- % s% s
- / dev / ptmx
- ptem
- ldterm
- ttcompat
- / dev / tty
- % s
- % d
- /
- \
- % d.% d
- win3.11
- win95
- winNT
- win ??
- \\. \ pipe \ 2
- % s% s.% s
- / dev / ptc
In the Kobalos samples we analyzed, only the bold values (1 and 6-9) are used. Others are not mentioned, although they may be used in some other versions. In particular:
- Lines 10 and 12-16 appear to be Windows-specific.
- Line 18 is the path to the pseudo-terminal device driver on AIX.
- Lines 3-5 are used by Solaris pseudo-terminal system calls.
We cannot exclude the option of trying to misinform researchers about the existence of versions for other operating systems. Given that we have confirmed support for three operating systems, it should come as no surprise if there are more. On the other hand, Windows 3.11 and Windows 95 are over 25 years old. Are there versions of Kobalos for these legacy systems?
Opposing an investigation
Once authenticated, some techniques are applied to the backdoor process to hinder investigation:
- The value
RLIMIT_CORE
is cleared to prevent a kernel dump from being generated in the event of a process crash. - Most of the signals are ignored to make it harder to interrupt the process.
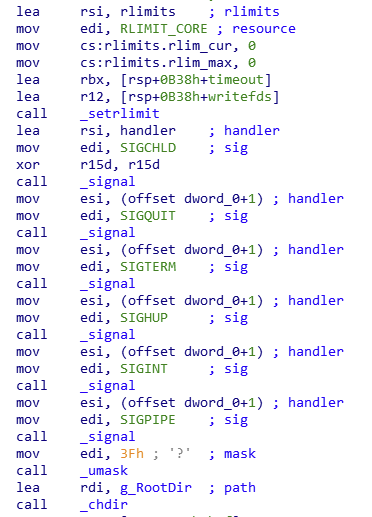
Figure 5. Kobalos avoids kernel dumps on crash and ignores most of the signals.
It is important to note that the configuration
RLIMIT_CORE
does not hurt to dump the process manually, for example, using
gcore
gdb. This limit is used by the kernel to determine the maximum size of a memory dump when a process crashes.
Time stamps
An analysis of the file system of compromised servers showed that after setting, the timestamps of replaced files (such as
ssh
for adding a credential theft module or
sshd
for deploying Kobalos) are tampered with to avert suspicion.
Configuration
Kobalos has a static configuration that enables or disables software functions. Table 1 lists the fields that we consider to be part of the configuration. Figure 6 shows a real-world example.
Table 1. Structure of static configuration Kobalos:
| Size (bytes) | Description |
|---|---|
| 2 | Probably a version number. Transmitted on successful authentication. In all found samples, it matters 0xB03
(considering that it is transmitted in the format from the highest to the lowest, like all other Kobalos data). |
| 320 | RSA public key module. Encrypted in a special binary format. |
| 2 | TCP port to listen on. If set to zero, then Kobalos will not listen on ports, but will use other methods to wait for a connection to the backdoor. |
| 2 | C&C-, . , — . |
| 2 | . ( ) ( ). |
| 4 | IP- C&C- . Kobalos . |
| 2 x 16 | TCP-, C&C-. |
| 16 | MD5- , . |
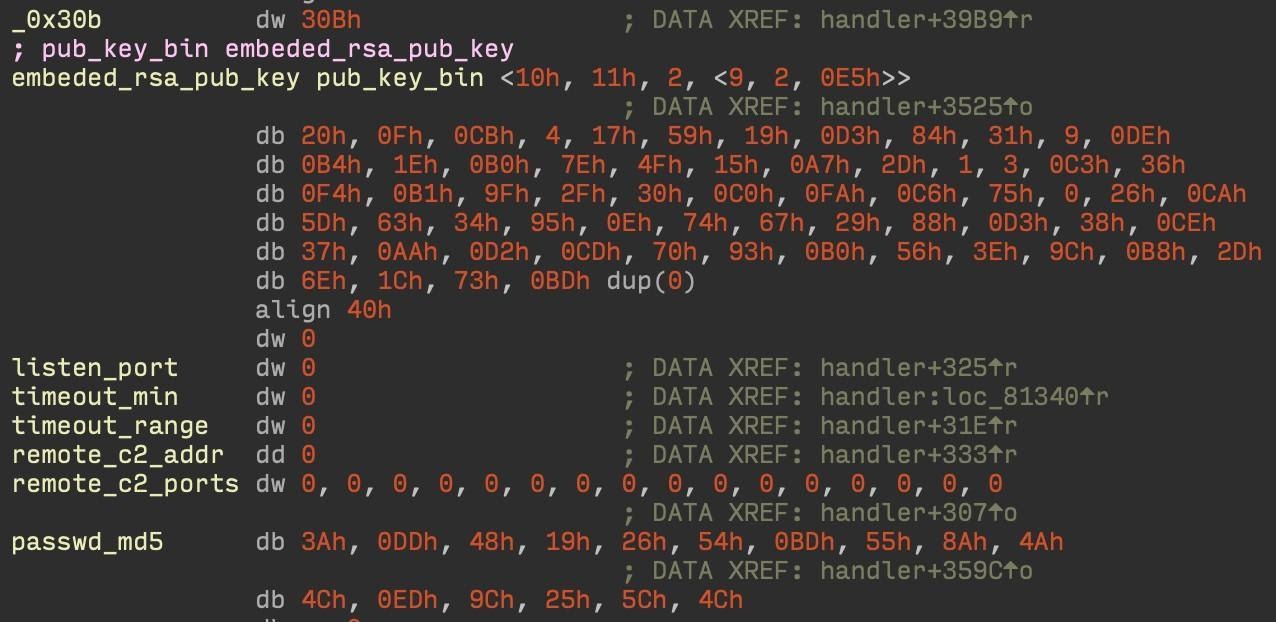
Figure 6. Sample configuration of the Kobalos sample embedded in sshd.
Some of the configuration will be different if Kobalos is executed internally
sshd
or as a separate executable file. In the latter case, the address of the remote C&C server (
remote_c2_addr
) or the listening port (
listen_port
) is required .
Deployment and preservation
If Kobalos is deployed to run as part of an OpenSSH server, the file
sshd
must be recompiled to add malicious code. We compared the Trojanized version of OpenSSH and the one that should be installed on the system, for example, from the package manager. It looks like the operator is compiling Kobalos based on the correct source OpenSSH already installed on the server. The infected executable is likely to be compiled on the victim's machine before replacing the original. Most likely, such a scheme was chosen for the sake of ensuring the safety of the software by preventing version mismatches, due to which incompatibility of the library may arise.
It should be noted that to replace
sshd
needs root privileges. However, there are versions of Kobalos as separate files that connect to the C&C server or listen on the TCP port. You do not need administrator privileges to run them, but access to the file system and the set of commands will be limited to the current user's access level.
Backdoor interaction
Backdoor connection
One of the notable features of Kobalos is the flexibility in establishing connections between operators and compromised hosts. This can be done in three ways:
- Listening to the specified TCP port (passive mode).
- By connecting to the C&C server (active mode) and waiting for the operator to connect through this server.
- By replacing the existing service that listens on TCP ports, and waiting for a connection from a specific source TCP port.
With the static configuration of Kobalos, several methods can be activated at once, however, in each sample we analyzed, only one was activated.
The latter method requires modifying the executable daemon. The trojanized version calls the Kobalos code every time it accepts a new TCP connection, as shown in Figure 7. The backdoor can accept it if the connection comes from a specific TCP port. If the port number matches, the function returns nothing, and the subprocess ends when the connection is closed. If the port does not correspond to the prescribed one, then the program does nothing and transfers the work to the code of the legitimate service, which continues to work properly.
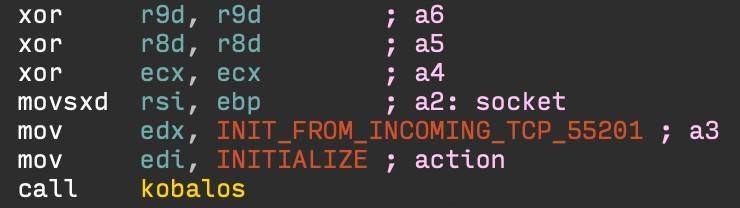
Figure 7. Calling a function from a trojanized OpenSSH function after accepting a new TCP connection. This is the method we've seen most often and has only been abused by the OpenSSH server. However, the data may be erroneous, because this is the way we could detect when scanning the Internet. As shown in Figure 8, Kobalos is listening on TCP port 55201.
kobalos
main
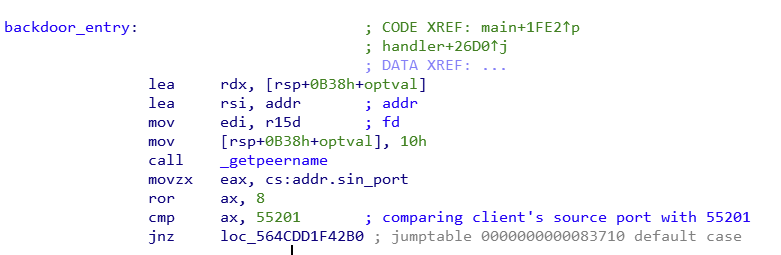
Figure 8. Source port comparison with 55201.
Kobalos implements an additional method for filtering incoming TCP connections, comparing the source port with a list of 16 ports:
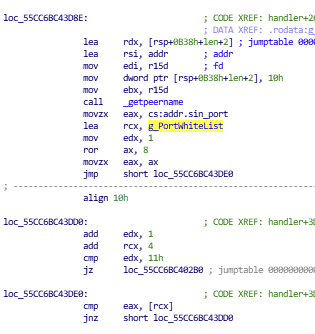
Figure 9. Comparison of a source port with a list of 16 ports.
List of 16 ports:
| twenty | 567 | 2734 | 22392 |
| 21 | 982 | 5392 | 33921 |
| 53 | 1821 | 11568 | 44983 |
| 230 | 1912 | 19678 | 55201 |
However, none of the found samples used this filter. It may have been used in a previous version of the backdoor.
Authentication
After the connection is established, authentication is performed. For further work, you need a private RSA key and a 32-byte password. The Kobalos client sends an initial 320-byte packet to the infected server, the structure of which is described in Table 2.
Table 2. The structure of the authentication packet (encrypted using the private RSA key) :
| Size (bytes) | Description | Value |
|---|---|---|
| four | Mysterious parameter | 0x7FFF000A
|
| 2 | Binding port | If 0x0000
, then Kobalos chooses a random port. If 0xFFFF
, then it uses an existing TCP connection. |
| one | Communication channel identifier | Seems to always be set as 0xFF
. |
| 32 | Password | The password value matches the MD5 hash in the static configuration. |
| 280 | Filling |
The first 64 bytes of the packet are decrypted using the configured RSA-512 public key modulus and exponent
0x10001
(see Figure 11). Then, as shown in Figure 10, MD5 hashing is applied to the 32-byte password, and the result is compared with the information from the static configuration.
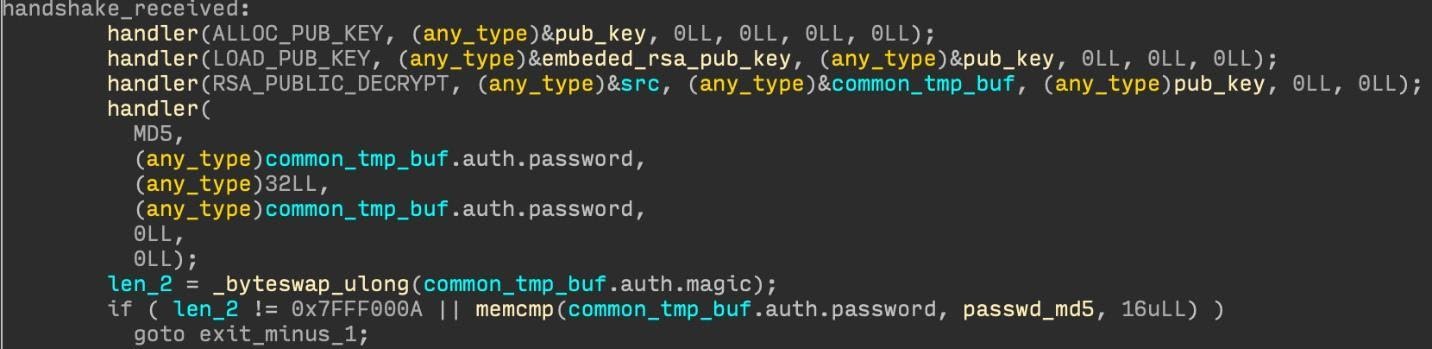
Figure 10. After receiving 320 bytes, authentication is performed.
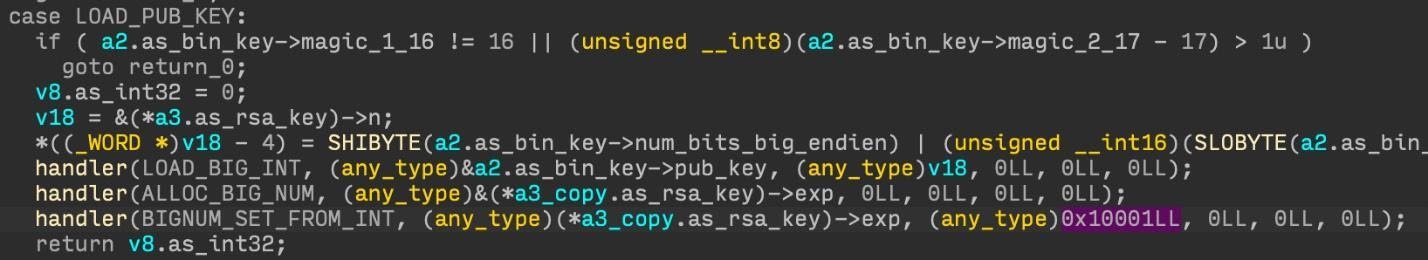
Figure 11. Loading an RSA-512 public key.
Using the public RSA key, Kobalos encrypts and sets RC4 keys that are used for further communication: one for incoming traffic, another for outgoing traffic. Kobalos sends encrypted keys in its response.
Table 3. Structure of Kobalos response (encrypted with RSA public key) :
| Size (bytes) | Description | Value |
|---|---|---|
| four | Mysterious parameter | 0x7FFF000A
|
| 16 | RC4 key for incoming traffic | RC4 key used for traffic to the compromised host. |
| 16 | RC4 key for outgoing traffic | RC4 key used for traffic from a compromised host. |
| 2 | Bound port | TCP port used as the active channel. The value 0xFFFF
means using the current connection. |
| 282 | Filling |
Active channel
After passing the authentication, the active channel can use a different port. You may have noticed that with client authentication, you need to provide a "bind port" in the encrypted message.
- If its value differs from
0xFFFF
, then Kobalos will start listening to the specified TCP port. - If the value is zero, then the backdoor will start listening to a random port above 1024.
As mentioned above, in the authentication response, along with the pair of RC4 keys, the number of the freshly opened port is transmitted. If desired, an additional TCP connection can be created: if a value is transmitted as the binding port
0xFFFF
, then the current connection is used.
Subsequent communication over these TCP connections is encapsulated in packets, the format of which is described in Table 4.
Table 4. Kobalos packet structure :
| Size (bytes) | Value |
|---|---|
| one | Mysterious meaning ( 0x7F
) |
| 2 | Payload |
| one | Communication channel identifier. |
| one | Communication channel identifier. |
| payload_size | Payload (encrypted with RC4). |
Kobalos is the first to send the packet to the connected operator. The package contains basic information about the machine, such as the hostname and kernel version. Figure 12 shows the levels of encapsulation in a package.
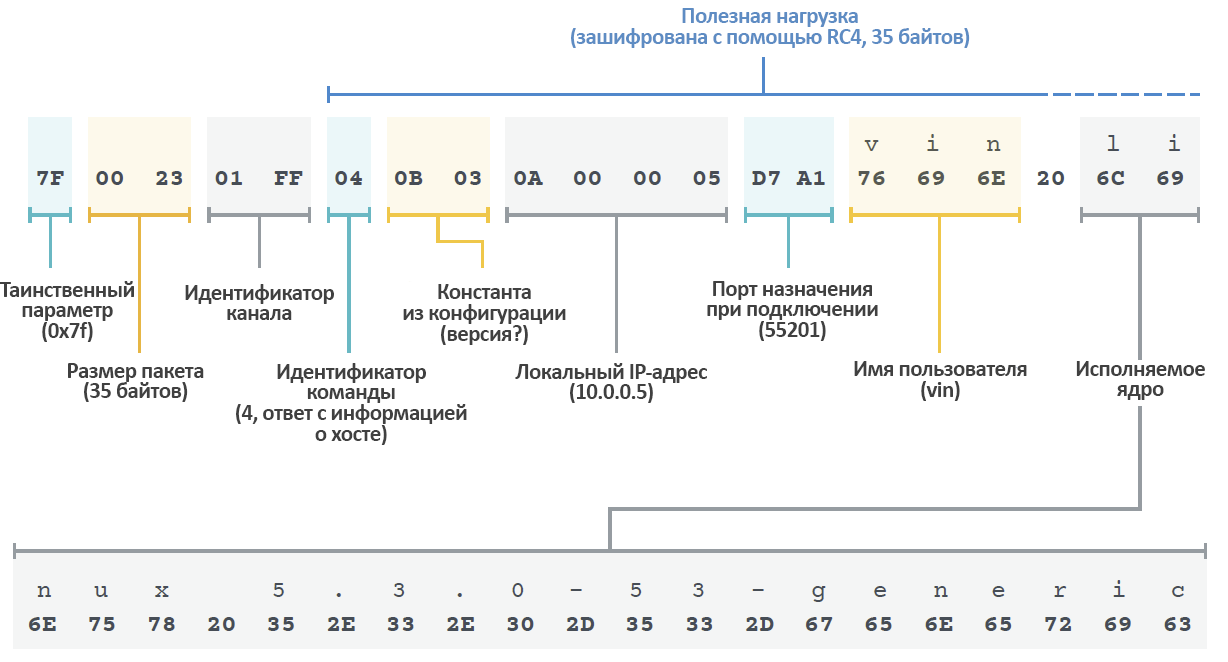
Figure 12. Information sent to the operator from a compromised host.
Figure 13 shows the communication process between Kobalos and its customer.
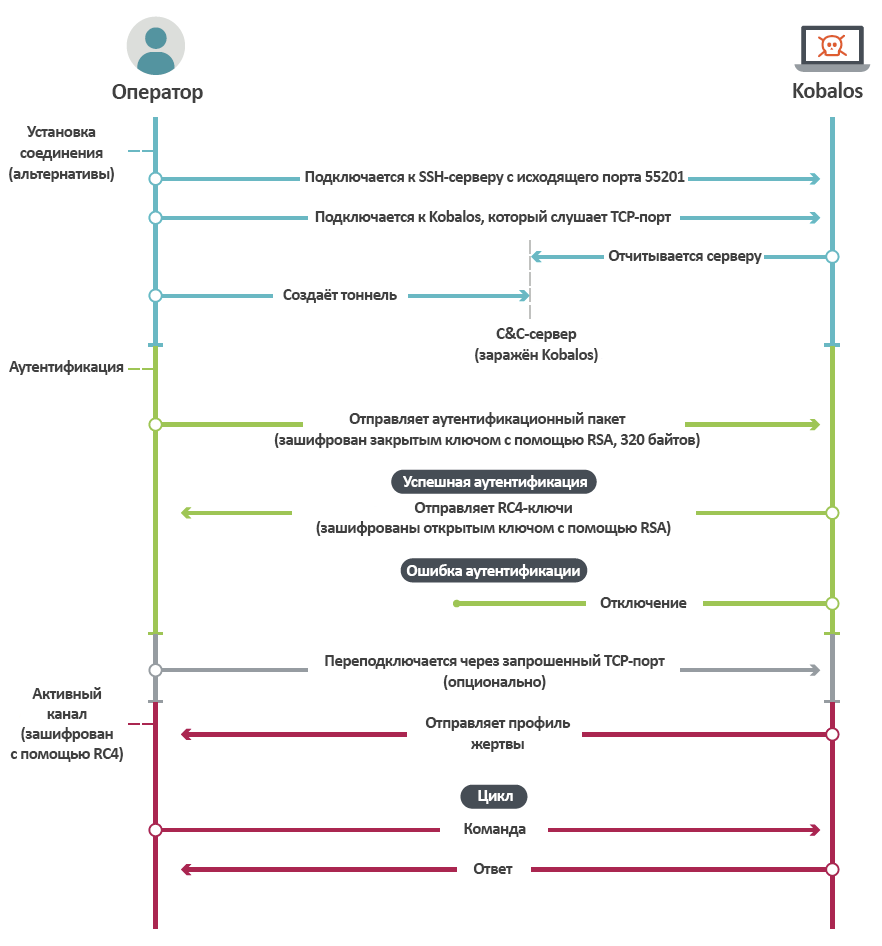
Figure 13. Kobalos network protocol sequence diagram.
Backdoor management
After authentication, the operator can issue different commands to the backdoor. We've divided them into categories:
- Connect to other servers infected with Kobalos and act as a proxy.
- Reading and writing any files to the file system.
- Launching and accessing a pseudo-terminal on a compromised host.
- Launching and managing Kobalos C&C servers with access to connected bots.
The commands are encapsulated in the active channel. They start with an identifying byte, followed by the parameters that are parsed by this command. The commands described in this work are processed by Kobalos, that is, the operator sends them to the compromised system using a special client. Kobalos replies in the same format, with the first identifier byte, and replies are processed by the same client. For example, after authentication, the command "send host information" (
0x04
) may be given .
Using as a proxy
Operators can use the Kobalos installed on the compromised machine to connect to other instances of the backdoor on other systems. Proxy mode uses the special packet size described above for authentication and encapsulation, that is, it is not a normal TCP proxy.
When connecting to a third party machine, the operator can select the source TCP port. This allows you to connect to Kobalos instances that are waiting for a connection from a specific port. Reconnecting the active channel through an alternate port is also supported. For this, a special command is given.
One of the tasks in this case is to ensure a certain level of operator anonymity. The end node only sees the IP address of the other compromised machine, not the operator's IP address. To further hide the operator's address, you can create chains of compromised proxy machines. Figure 14 shows such a scenario.
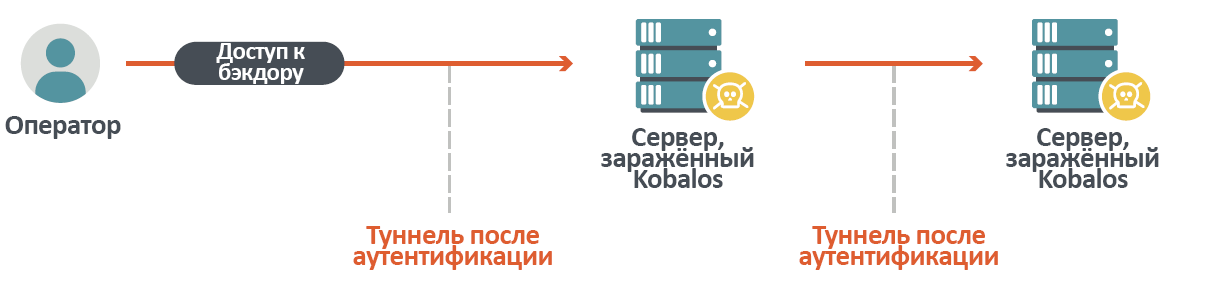
Figure 14. Kobalos is being used as a proxy.
Proxy control commands are described in Table 5.
Table 5. Commands for using Kobalos as a proxy :
| Command | Description | Options |
|---|---|---|
| 0x01 | Establishing a connection to another host compromised by Kobalos. | Remote address. Source port. End port. Authentication message (320 bytes). |
| 0x03 | . , TCP-. | . |
| 0x05 | . |
After authentication, the operator can read or write any files to the system. In the Kobalos networking protocol, the encapsulated payload is defined using a 16-bit integer. This means that the operator can only send 64K packets. For example, if he wants to write 200 KB to a file, he will have to execute four successful write commands. The read command has an even stricter limitation: only 1000 bytes can be read and sent at a time.
Table 6 describes the commands for working with the file system.
Table 6. Commands for reading and writing files :
| Command | Description | Options |
|---|---|---|
| 0x18 | Opening a file for writing; if not, then the file is created. | Search position. The path to the file. |
| 0x1A | Writing to a file. | Data to write. They will be overwritten from the search position. |
| 0x1C | Closing the file after recording. | |
| 0x1D | Opening and reading a file. | Search position. The path to the file. |
| 0x20 | Closing the file after reading. |
Creating a pseudo-terminal
This functionality allows an authenticated operator to create a shell in a new pseudo-terminal and execute arbitrary commands. To do this, use the commands from Table 7.
Table 7. Commands for creating and managing pseudo-terminals :
| Command | Description | Options |
|---|---|---|
| 0x12 | Launch of a new pseudo-terminal. | The path to the shell (for example /bin/sh
). Argument. |
| 0x0D | Specifies the size of the pseudo-terminal window. | Structure values winsize
accepted by TIOCSWINSZ . |
| 0x14 | Closing a pseudo-terminal. | |
| 0x16 | Writing to a pseudo-terminal. | Data to write. |
Data from the terminal is sent to operators, and after the data comes the closing command identifier
0x17
. It is implemented in the client that the operators use.
Use as a C&C server
One of the most unusual features of Kobalos is that the C&C server code is already built into the backdoor itself. This allows attackers to turn any infected machines into C&C servers (for other bots) with a single command. After starting the server, the operator can set its IP address and port in the configurations of future Kobalos instances that will be deployed on other hosts. This allows:
- Use compromised resources as C&C servers, rather than renting servers from regular providers. This reduces the likelihood of server unavailability.
- Use the C&C server as an intermediate node for machines behind firewalls with which there is no direct connection from the Internet.
When the operator sends the "transition to C&C mode" (
0x21
) command, the port number is passed as a parameter. Kobalos starts listening to it, and bots use this port to connect to the C&C server instance. In doing so, the backdoor also listens on the next higher port number. For example, if bots use TCP port 7070, then in C&C mode Kobalos also listens on 7071. The second port is used by the operator to control C&C functions, such as listing bots and establishing tunnels to them. The diagram is shown in Figure 15.
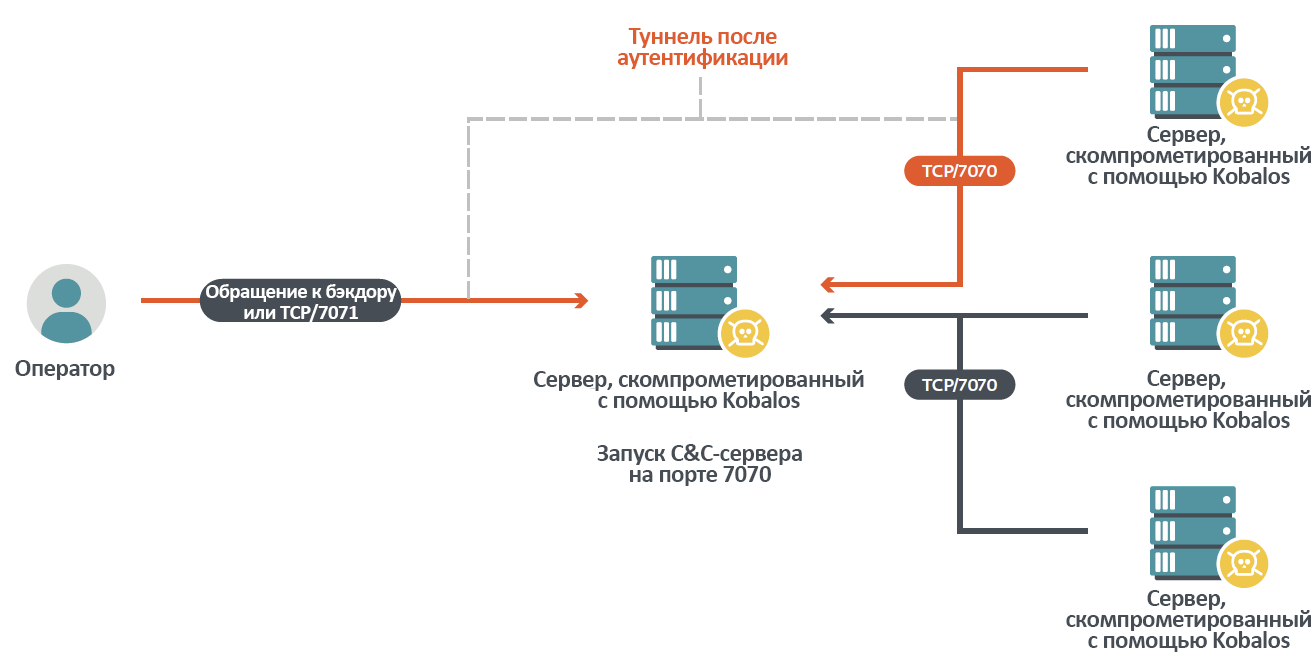
Figure 15. Operator Kobalos calls bots that reported themselves to the C&C server.
Table 8 describes the commands for controlling the capabilities of the C&C server.
Table 8. Commands for controlling the functions of the C & C server :
| Command | Description | Options |
|---|---|---|
| 0x21 | Launch of the C&C server. | TCP port for C&C server. |
| 0x23 | Get the number of active connections and the total since C&C started. | |
| 0x25 | List of all bots ready to execute commands. | |
| 0x29 | Disconnecting the C&C server. | |
| 0x2B | Connect to the bot. | Bot index from the list of bots ready to connect. Authentication message (320 bytes). |
| 0x2D | Connecting to a bot without authentication. | Bot index from the list of bots ready to connect. |
Commands
0x23
-
0x2D
processed by the C&C server subprocess. As shown in Figure 16, after being sent on an active channel, data is redirected over TCP to the loopback interface of the control port (one more than the port number used by the bots) of the C&C server.
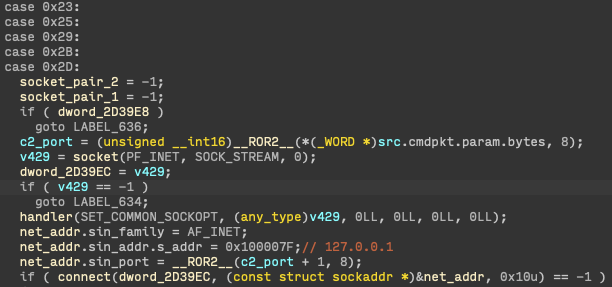
Figure 16. Packets related to C&C server management are forwarded over TCP to a subprocess.
Other commands
Environment variables
For the backdoor process, there is a command for setting environment variables. It takes a string as a parameter and simply passes it to putenv , which expects data in the format "VAR = value".
Table 9. Other commands that Kobalos understands :
| Command | Description | Options |
|---|---|---|
| 0x0E | Sets the environment variable for the session. | String to pass to putenv
. |
Empty operations
There are two more commands implemented, but they don't do anything. We have two explanations for this:
- The authors removed the functionality of the commands as they were used in previous versions and are no longer needed.
- The commands are platform specific and do not apply to the Linux and FreeBSD versions of Kobalos we analyzed.
Figure 17. Teams and do nothing. The second explanation looks more likely because we know the string values for Solaris, AIX, and Windows (see the Encrypted String Values chapter).
0x07
0x09
OpenSSH credential stealing program
On most systems compromised by Kobalos, the backdoor also deployed a program to steal SSH credentials via a Trojanized SSH client. We found different versions of these files, including Linux and FreeBSD. Unlike Kobalos, the capabilities of this program have hardly been obfuscated. Its main function is to steal the hostname, port number, and username and password to establish an SSH connection from a compromised host. The data is saved to an encrypted file. Newer versions of the Trojan can also transmit information over the network via UDP, but this feature was not activated in the configuration of most of the samples found.
But at the time of publication of our previous study of OpenSSH backdoors "The dark side of the ForSSHE", we did not know about this Trojan, so it is not mentioned in that work. We also cannot link it with any of the OpenSSH credential stealing programs described in open sources.
The location of the stolen data file depends on the version of the program. All samples created a
/var/run
file with the .pid extension in the directory . It is used in many of the files in this directory. You can see examples of file names and paths to them from different samples in the chapter "Signs of compromise".
All found samples encrypt the contents of the files using one simple cipher. As shown in Figure 18, the Trojan simply adds 123 to every byte of data that it stores.
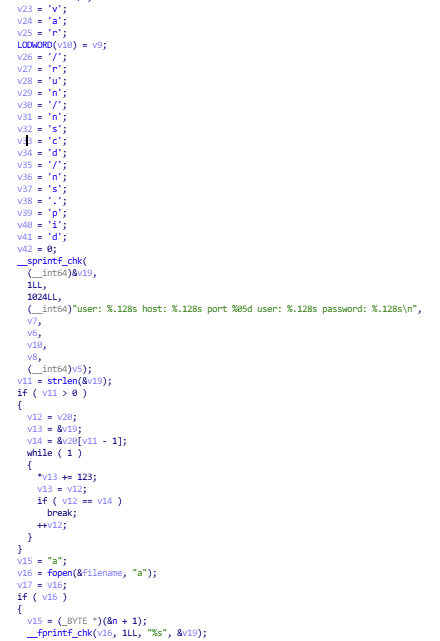
Figure 18. Encrypting and Writing Stolen SSH Credentials to the File.
The FreeBSD version uses the same format and cipher. However, they are implemented a little differently, for example, in the program, the path to the file is encrypted using a single-byte XOR.
Developing family of programs
After we notified one of the victim organizations, they discovered what appears to be a more recent version of a credential-stealing Trojan. It contains an encrypted configuration and allows stolen information to be transmitted via UDP to the remote host specified in the configuration. Ebury and other SSH credential stealing programs such as Bonadan, Kessel, and Chandrila also have this capability. Perhaps UDP was chosen to bypass firewalls and not make TCP connections to potentially untrusted hosts. The Trojan uses only one method of transmission - via a file or a network, because the name of the target host and the path to the file are stored in the same variable.
Figure 19 shows the decompiled code for sending data over UDP. And figure 20 shows the configuration from the found sample. It was configured to log the stolen information into
/var/run/sshd/sshd.pid
.

Figure 19. The Trojan sends credentials via UDP .

Figure 20. Example of a configuration that uses a file to capture stolen data.
Curiously, the configuration also contains the name of the victim's host. It is probably used by operators to denote a data source. It also means that each compromised server receives a unique instance of the Trojan.
Conclusion
Numerous well-implemented network circumvention features and techniques indicate that the Kobalos authors are far more skilled than many malware writers targeting Linux and other non-Windows systems. Targeting - fairly well-known organizations - also tells us that Kobalos operators are not aiming to infect as many systems as possible. Low traces and network bypass techniques could be the reason the backdoor went unnoticed until we informed the victims of the results of our network scan.
We cannot answer the question about the intentions of the attackers. The backdoor's capabilities allow you to use it to solve any problem. No additional software was found on the compromised machines except for a Trojan that steals SSH credentials. Therefore, we consider SSH as the entry point, and not the payload. According to information from the system administrators of the compromised HPC information systems from the system administrators of the compromised HPC systems, no one tried to mine cryptocurrencies or launch other tasks that require large computing power.
What are the attackers pursuing?
We were also unable to find out how long this software has been in use. We found lines related to Windows 3.11 and Windows 95 that came out over 25 years ago. Is there a Windows version of Kobalos? This program was created so long ago? We know of new infections in 2019 and 2020, but found no evidence of earlier use.
While the authors of this software appear to be well versed in the operation of their victims' network protocols and operating systems, Kobalos has several weaknesses. Firstly, the problems with cryptography are probably due to the development of this industry, if Kobalos really was developed for a very long time. Second, you might notice passively listening instances, especially if they require a specific source TCP port. We successfully took advantage of this feature and notified victims to reduce the number of infected hosts and better understand this newly discovered threat.
We also report on the work of Maciej Kotowicz from MalwareLab pl , who independently analyzed Kobalos and with whom we exchanged survey results. He told Oh My H@ck 2020.
. Kobalos
| 1003 | INITIALIZE | socket, filter | Kobalos , ( enum). |
| 1004 | START_LISTENING | C&C- . | |
| 1005 | START_C2_SERVER | socket_1, socket_2 | C&C-. |
| 1006 | SEND_PACKET | socket_fd, &channel_1,
&channel_2, data, data_len |
Kobalos socket_fd. |
| 1007 | RECV_PACKET | socket_fd, &channel_1,
&channel_2, data, data_len |
Kobalos socket_fd. |
| 1008 | GET_RANDOM_INT | random_int | 32- . PRNG . |
| 1009 | GET_HOST_INFO | out_buf, returns buf_len | , IP- . |
| 1010 | SET_COMMON_SOCKOPT | socket | SO_REUSEADDR SO_KEEPALIVE
true, SO_LINGER — 15 . |
| 1011 | RC4_DECRYPT_STRING_INPLACE | str, len | str RC4- . |
| 1012 | CLEANUP_THINGS | what_to_close, send_report | . . . |
| 1013 | RC4_INIT | context, key_size, key | RC4 . |
| 1014 | RC4_CRYPT | context, len, data_in, data_out | RC4- . |
| 1015 | MD5 | input, input_len, output_digest | MD5-. |
| 1016
to 1037 |
, . | ||
| 1038 | RSA_PUBLIC_DECRYPT | ||
| 1039 | LOAD_PUB_KEY | key_bin_data, public_key | Loads a BLOB with a public RSA key from key_bin_data to public_key. |
Signs of compromise
Names found by ESET
- Linux / Kobalos
- Linux / Agent.IV
- Linux / SSHDoor.EV
- Linux / SSHDoor.FB
- Linux / SSHDoor.FC
Samples
Kobalos
| SHA-1 | Target OS | Built into | Availability |
|---|---|---|---|
FBF0A76CED2939D1F7EC5F9EA58C5A294207F7FE
|
RHEL | sshd | Waiting for connection from source port 55201. |
479F470E83F9A5B66363FBA5547FDFCF727949DA
|
Debian | Stand-alone | Connects to
151.80.57 [.] 191: 7070 |
AFFA12CC94578D63A8B178AE19F6601D5C8BB224
|
FreeBSD | sshd | Waiting for connection from source port 55201. |
325F24E8F5D56DB43D6914D9234C08C888CDAE50
|
Ubuntu | sshd | Waiting for connection from source port 55201. |
A4050A8171B0FA3AE9031E0F8B7272FACF04A3AA
|
Arch Linux | sshd | Waiting for connection from source port 55201. |
Trojan to steal SSH credentials
| SHA-1 | Target OS | Writes in |
|---|---|---|
6616DE799B5105EE2EB83BBE25C7F4433420DFF7
|
RHEL | /var/run/nscd/ns.pid
|
E094DD02CC954B6104791925E0D1880782B046CF
|
RHEL | /var/run/udev/ud.pid
|
1DD0EDC5744D63A731DB8C3B42EFBD09D91FED78
|
FreeBSD | /var/run/udevd.pid
|
C1F530D3C189B9A74DBE02CFEB29F38BE8CA41BA
|
Arch Linux | /var/run/nscd/ns.pid
|
659CBDF9288137937BB71146B6F722FFCDA1C5FE
|
Ubuntu | /var/run/sshd/sshd.pid
|
Keys
RSA public key
-----BEGIN PUBLIC KEY----- MFwwDQYJKoZIhvcNAQEBBQADSwAwSAJBAOUgD8sEF1kZ04QxCd60HrB+TxWnLQED wzb0sZ8vMMD6xnUAJspdYzSVDnRnKYjTOM43qtLNcJOwVj6cuC1uHHMCAwEAAQ== -----END PUBLIC KEY-----
Static RC4 key for string values
AE0E05090F3AC2B50B1BC6E91D2FE3CE
YARA rules
rule kobalos { meta: = “Kobalos malware” author = “Marc-Etienne M.Léveillé” date = “2020-11-02” reference = «http://www.welivesecurity.com» source = «https://github.com/eset/malware-ioc/» license = «BSD 2-Clause» version = “1” strings: $encrypted_strings_sizes = { 05 00 00 00 09 00 00 00 04 00 00 00 06 00 00 00 08 00 00 00 08 00 00 00 02 00 00 00 02 00 00 00 01 00 00 00 01 00 00 00 05 00 00 00 07 00 00 00 05 00 00 00 05 00 00 00 05 00 00 00 0A 00 00 00 } $password_md5_digest = { 3ADD48192654BD558A4A4CED9C255C4C } $rsa_512_mod_header = { 10 11 02 00 09 02 00 } $strings_RC4_key = { AE0E05090F3AC2B50B1BC6E91D2FE3CE } condition: any of them } rule kobalos_ssh_credential_stealer { meta: = “Kobalos SSH credential stealer seen in OpenSSH client” author = “Marc-Etienne M.Léveillé” date = “2020-11-02” reference = «http://www.welivesecurity.com» source = «https://github.com/eset/malware-ioc/» license = «BSD 2-Clause» version = “1” strings: $ = “user: %.128s host: %.128s port %05d user: %.128s password: %.128s” condition: any of them }
MITER ATT & CK Techniques
The table was compiled using the eighth version of the ATT & CK framework.
| Tactics | Identifier | Name | Description |
|---|---|---|---|
| Sustainability | T1554 | Compromise ClientSoftware Binary | Kobalos OpenSSH- sshd
.Kobalos SSH- . |
| T1205 | Traffic Signaling | Kobalos TCP- . | |
| Defense Evasion | T1070.003 | Clear Command History | Kobalos , . |
| T1070.006 | Timestomp | Kobalos . | |
| T1027.002 | Software Packing | Kobalos . | |
| Command And Control | T1573.001 | Encrypted Channel: Symmetric Cryptography | RC4. |
| T1573.002 | Encrypted Channel: Asymmetric Cryptography | RSA-512. | |
| T1090.003 | Proxy: Multi-hop Proxy | Kobalos , Kobalos. |