
Task - Root Certificate of AD-CA Certificate Authority on Linux
Condition 1 . raise PKI-AD, while the root certification authority must be installed on a separate ROOT-CA station.
Condition 2 . since the ROOT-CA station is used for an extremely limited time and only for the release of CRT and CRL, then 99% of the station is in a disconnected state, the budget for this station is zero.
Reflections
The thoughts are very simple: to save the budget, PKI-AD will be installed directly on the Active Directory server, but ROOT-CA needs to be raised on Linux.
Further in the text:
ROOT-CA - station or root center certificate.
PKI AD-CA - station with the role "Active Directory Certificate Services"
Decision
ROOT-CA preparation. (CentOS7)
The root certificate ROOT-CA, we will issue on CentOS, there we will also sign the certificate for PKI AD-CA.
To solve this problem on a Linux machine, you need to install the easy-rsa package , which is contained in the epel-release tutor
yum install epel-releas
yum install easy-rsa
More details on the documentation for easy-rsa can be found on GitHub / OpenVPN
easy-rsa .
( root)
, - PKI
mkdir -p ~/ROOTca
easy-rsa ROOTca,
dir /usr/share/easy-rsa/
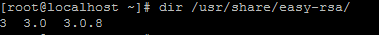
3.0.8. .
easy-rsa ROOTca
cp -R /usr/share/easy-rsa/3.0.8/* ~/ROOTca
vars,
cat > ~/ROOTca/vars
vars
vars, :
# A little housekeeping: DON'T EDIT THIS SECTION ( )
# Easy-RSA 3.x doesn't source into the environment directly.
if [ -z "$EASYRSA_CALLER" ]; then
echo "You appear to be sourcing an Easy-RSA 'vars' file." >&2
echo "This is no longer necessary and is disallowed. See the section called" >&2
echo "'How to use this file' near the top comments for more details." >&2
return 1
fi
#
set_var EASYRSA "$PWD"
set_var EASYRSA_PKI "$EASYRSA/pki"
set_var EASYRSA_OPENSSL "openssl"
set_var EASYRSA_DN "org"
set_var EASYRSA_TEMP_FILE "$EASYRSA_PKI/extensions.temp"
set_var EASYRSA_EXT_DIR "$EASYRSA/x509-types"
set_var EASYRSA_SSL_CONF "$EASYRSA/openssl-easyrsa.cnf"
set_var EASYRSA_BATCH ""
#
set_var EASYRSA_REQ_COUNTRY "RU"
set_var EASYRSA_REQ_PROVINCE "Russia"
set_var EASYRSA_REQ_CITY "Moscow"
set_var EASYRSA_REQ_ORG "CompanyName"
set_var EASYRSA_REQ_EMAIL "ca@companyname.ru"
set_var EASYRSA_REQ_OU "CompanyName.ru"
set_var EASYRSA_NS_SUPPORT "yes"
set_var EASYRSA_NS_COMMENT "CompanyName Certificate 2021"
#
set_var EASYRSA_KEY_SIZE 4096
set_var EASYRSA_ALGO rsa
# (20 )
set_var EASYRSA_CA_EXPIRE 7300
#
set_var EASYRSA_CERT_EXPIRE 365
# ~
set_var EASYRSA_CRL_DAYS 92
#
set_var EASYRSA_DIGEST "sha256"
, !
! , ROOTca
cd ~/ROOTca
./easyrsa init-pki

, ROOT-CA
./easyrsa build-ca
ROOT-CA
( , 4 )
, vars, .
!!! - “Common Name”.
Common Name (eg: your user, host, or server name) [Easy-RSA CA]: CompanyName Certificate 2021.

ROOT-ca PKI
/root/ROOTca/pki/ca.crt
c PKI AD-CA
PKI AD-CA (Windows Server)
PKI AD-CA
ca.crt
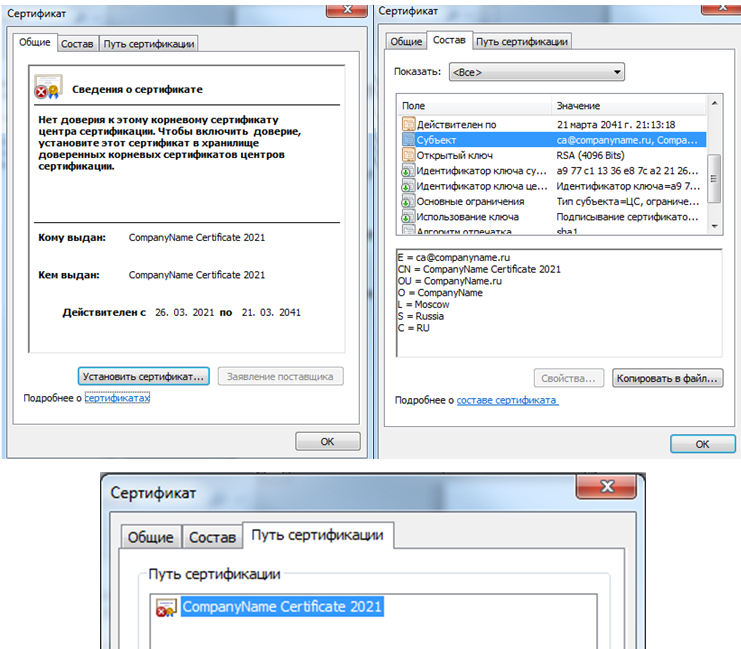
! ca.crt ROOT-ca.crt, - . Windows.
“ Active Directory”
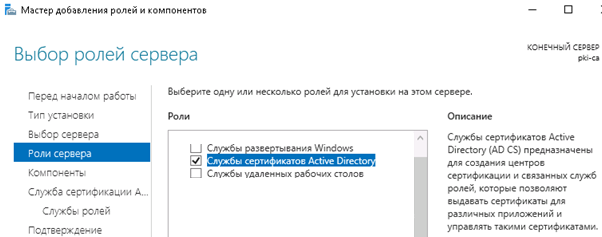
- Active Directory
docs.microsoft.com
:
-

-


-

CA

- REQ

:
, pki-ca_PKI-CA-CA.req
Linux ROOT-ca /root/ROOTca/pki/
PKI AD-CA
req PKI
./easyrsa import-req /root/ROOTca/pki/pki-ca_PKI-CA-CA.req CompanyName-AD

CompanyName-AD – PKI AD-CA
./easyrsa show-req CompanyName-AD

CompanyName-AD
./easyrsa sign-req ca CompanyName-AD
“ ” ca, server.
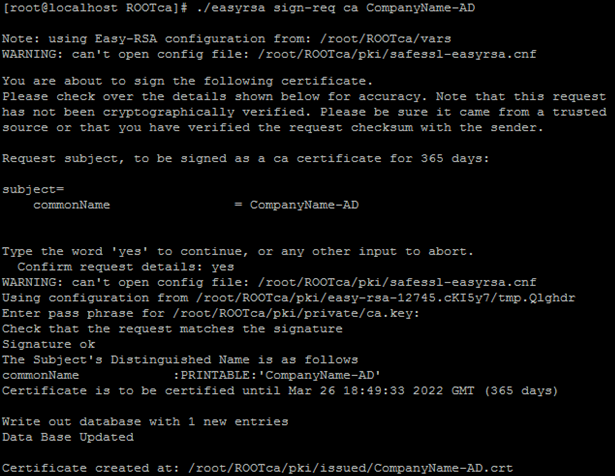
PKI AD-CA /root/ROOTca/pki/issued/CompanyName-AD.crt
PKI AD-CA
CRL,

/root/ROOTca/pki/crl.pem
( 92 vars, 92 CRL)
crl.pem AD-PKI
PKI AD-CA (Windows Server)
, .
:
: ROOT-ca.crt
CA : CompanyName-AD.crt
: crl.pem
ROOT-ca
ROOT-ca.crt Windows, , , , .

MMC- “” .
: \ \
ROOT-ca.crt " "
“” ->

ROOT-ca.crt .

, ROOT-ca.crt

- !
( , AD)
CRL.
, crl.pem ROOTca.crl
( ROOTca.crl)
ROOT-ca.crt
PKI AD-CA
CA PKI AD-CA
" "

CA, CDP AIA
CA
PKI AD-CA > >

, CompanyName-AD.crt .
, CA .
CompanyName-AD.crt P7B .
CompanyName-AD.crt ROOT-ca.crt OpenSSL :
openssl crl2pkcs7 -nocrl –certfile ROOT-ca.crt -certfile CompanyName-AD.crt -out CompanyName-AD.p7b
PKI AD-CA
PKI AD-CA > >
we received a working PKI - Active Directory and can start issuing certificates for users, stations, servers. At the same time, ROOT-ca is located on a station with Linux, and we did not have to give a separate server with Windows for this task.