
CC-BY-CA Vadim Rybalko, based on a meme
The IETF Internet Engineers Working Group has deprecated the TLS 1.0 and 1.1 encryption protocols. Relevant RFCs have officially received "historic" status with a note
deprecated
.
The flag
deprecated
indicates that the IETF strongly discourages the use of these protocols. For security reasons, it is required to disable support for TLS 1.0 and 1.1 wherever possible. This is stated in published RFC 8996 . Why it is impossible to support the TLS 1.0 and 1.1 protocols is explained in detail in paragraphs 3, 4 and 5 of this document.
As explained by the IETF, removing support for older versions from libraries and software "reduces the attack surface, reduces the potential for misconfiguration, and makes the library and product easier to maintain."
Along with the old versions of TLS, the Datagram TLS (DTLS) protocol version 1.0 (RFC 4347) is also deprecated, and only that, since version 1.1 did not come out.
TLS 1.0 is 22 years old this year. Since its adoption, it has become better understood how encryption protocols should be designed. Requirements for the reliability of ciphers have increased. Unfortunately, TLS 1.0 and 1.1 do not meet these requirements.
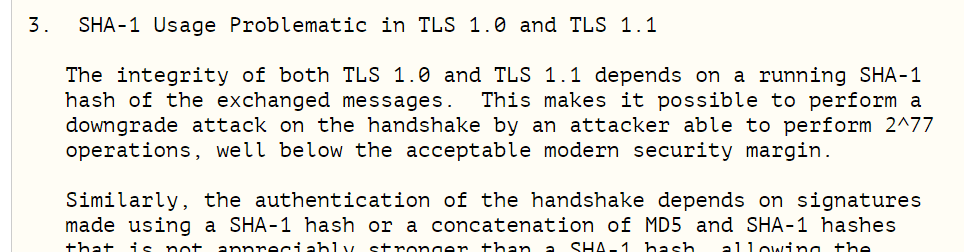
The worst thing is that TLS 1.0 and 1.1 do not support modern cryptographic ciphers. For example, when shaking hands, they necessarily use the SHA-1 hashing algorithm. In these versions of TLS, it is not possible to set a stronger hashing algorithm for ServerKeyExchange or CertificateVerify signatures.
A draft of this RFC 8996 was published on September 14, 2018. Among other things, it mentions that the SHA-1 algorithm with a cryptographic strength of 2 ^ 77 cannot be considered secure by modern standards: "2 ^ 77 operations [for an attack] are below the acceptable security limit."
We are talking about the BEAST (Browser Exploit Against SSL / TLS) attack on TLS 1.0 and 1.1, or rather, on block ciphers, where the initialization vector for the message
n
the last encryption block of the previous message is used
(n-1)
.
The developers of all major browsers immediately agreed to comply with the IETF recommendations.
The Chrome browser was the first to drop support for older versions of TLS in January 2019 . Starting with version 79, a warning was displayed for legacy protocols in the DevTools console, and a complete shutdown was planned for version 81 of Chrome in March 2020 (preview versions - from January 2020). At the same time, the abandonment of TLS 1.0 and 1.1 was announced by Microsoft , Mozilla and Apple .
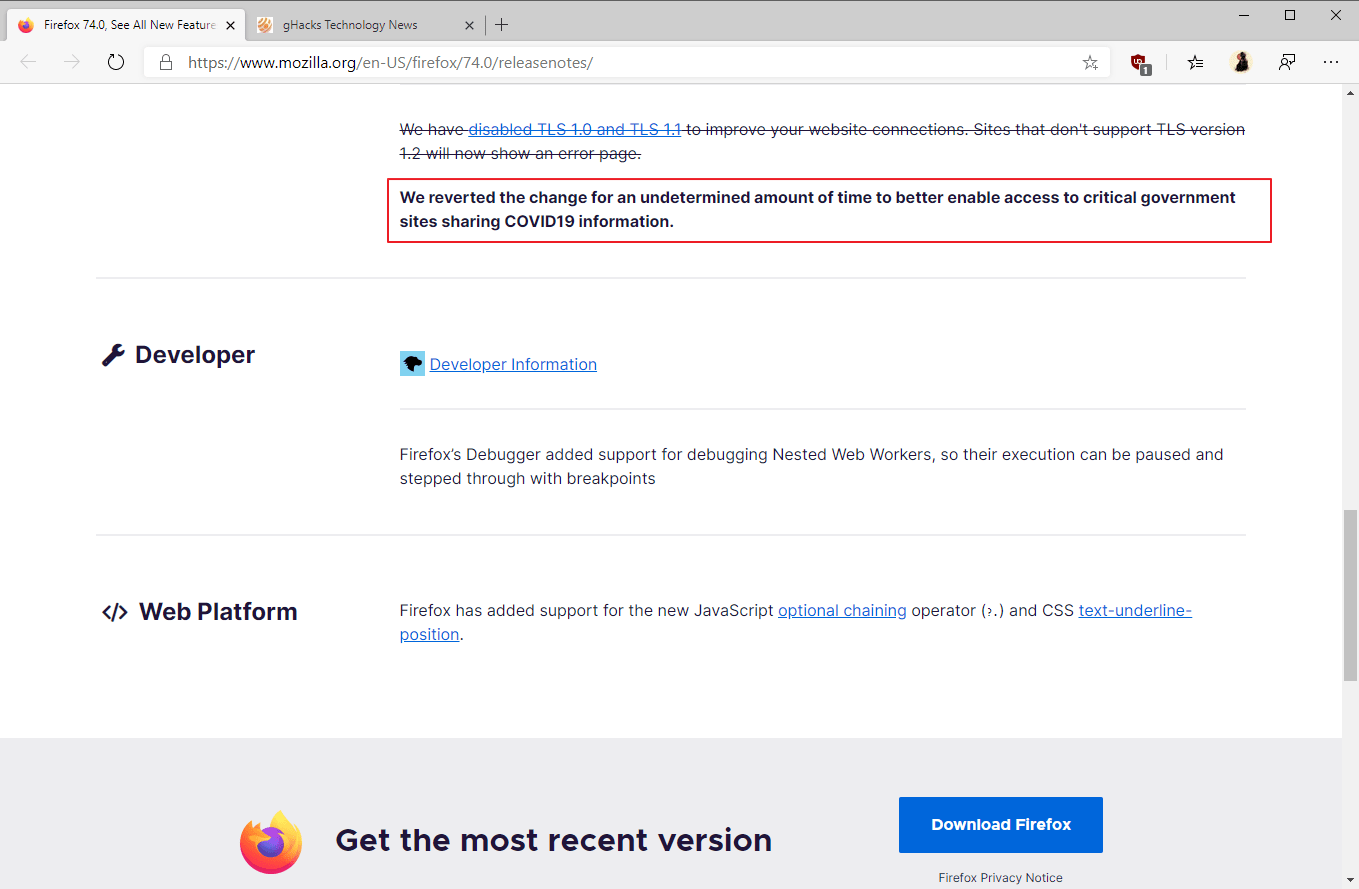
However, everything did not go according to plan. In March 2020 Firefox temporarily refused to remove support for TLS 1.0 and 1.1 . Formally, this was done due to the coronavirus (see screenshot below), but in fact, the Mozilla developers were afraid that Google colleagues would back down and leave support for TLS 1.0 and 1.1, so that Firefox will be the only browser without this support.
But in the end, support for old protocols in browsers was still disabled. If necessary, you can change the setting in Firefox
security.tls.version.enable-deprecated
.
TLS 1.0 and 1.1 are gradually being removed from applications and services. Amazon, CloudFlare, GitHub, KeyCDN, PayPal and other web services have done this. Since January 15, 2020, support for old protocols has been disabled on Habr's resources .