
The second article in a small series on protection used to hide the algorithm of an application. In the last article, we covered the main parts of protection and put together a test application. Here we will get acquainted with the structure of command handlers and try to debug and decode the executable file.
Description of VMProtect work
, -. :
;
;
, , .
:
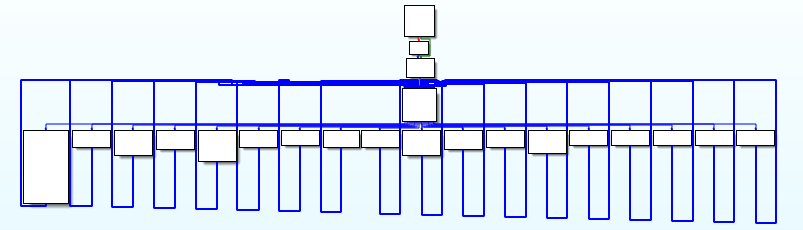
, VMP . , .
, , VMP . .
pusha ;
push 0 ;
mov esi, [esp+x+var] ; esi = VM , x var
mov ebp, esp ; VMProtect , ebp = VM "stack"
sub esp, 0C0h
mov edi, esp ; edi = ,
:
add esi, [ebp+0]
:
mov al, [esi]; EIP
movzx eax, al
sub esi, -1; EIP
jmp ds:VMHandlers[eax*4] ;
, :
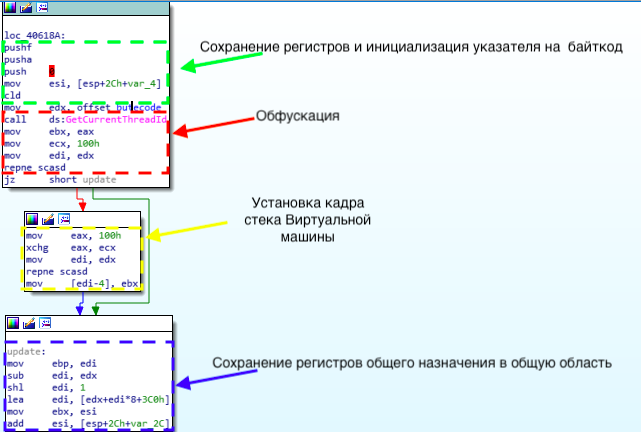
, , :

, , .
VM
x64dbg, Windows ( WinDBG). , , . :
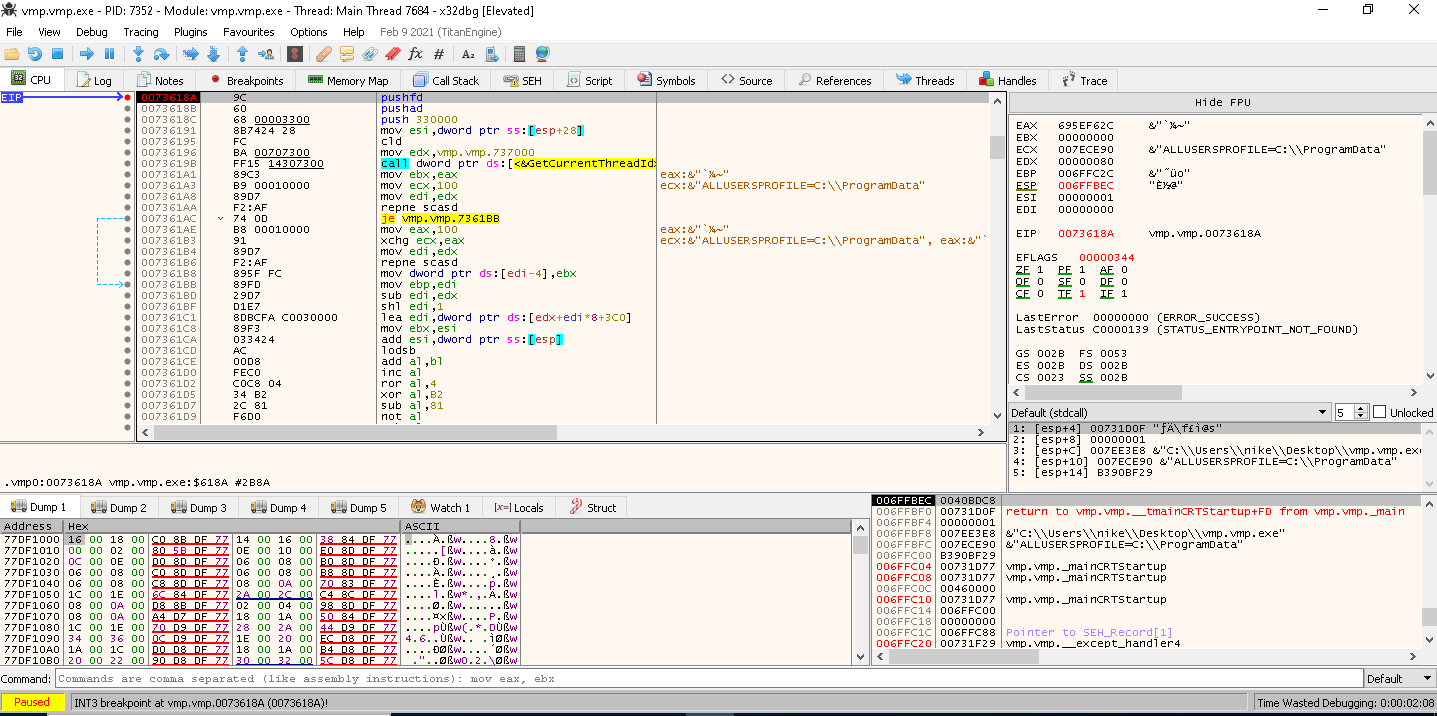
, . , , main_loop. , :

main loop. , , ESI. EIP AX . . , , . , , breakpoint, . .
, :
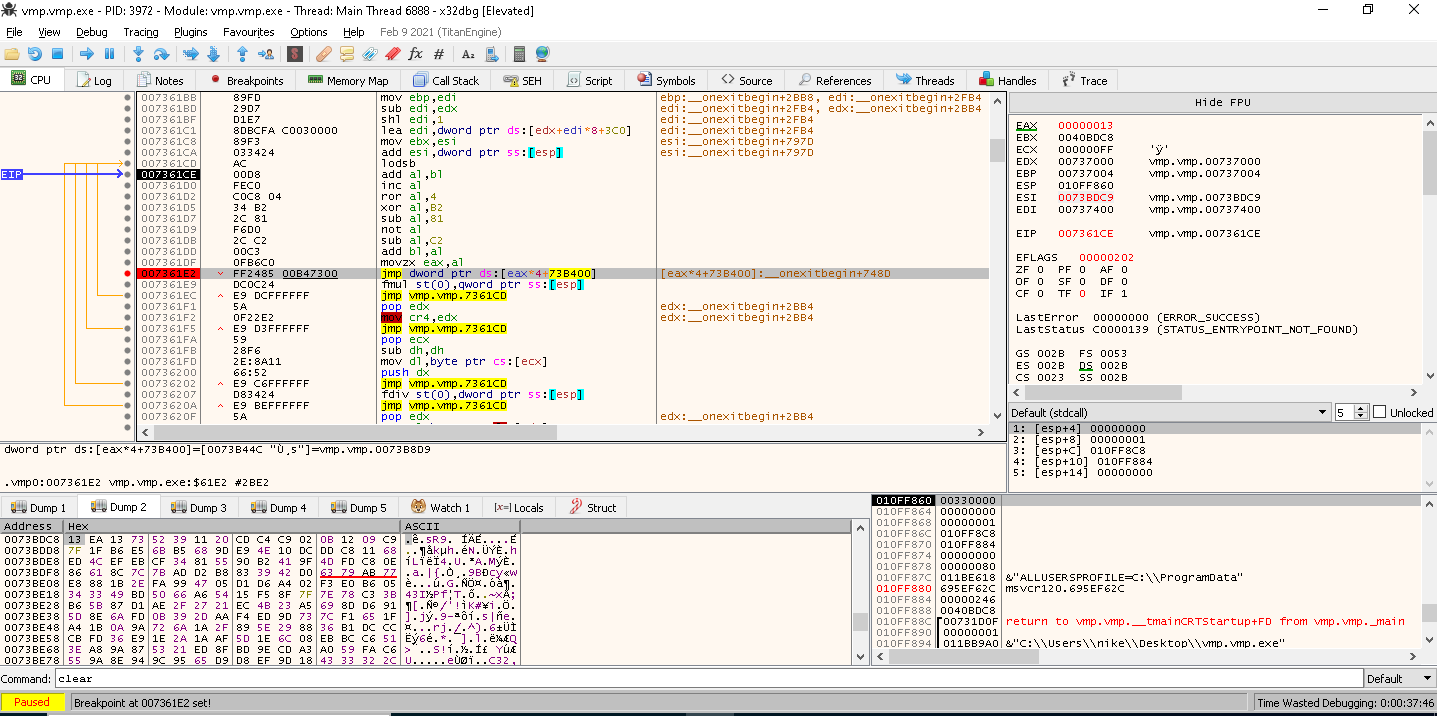
"breakpoints" :
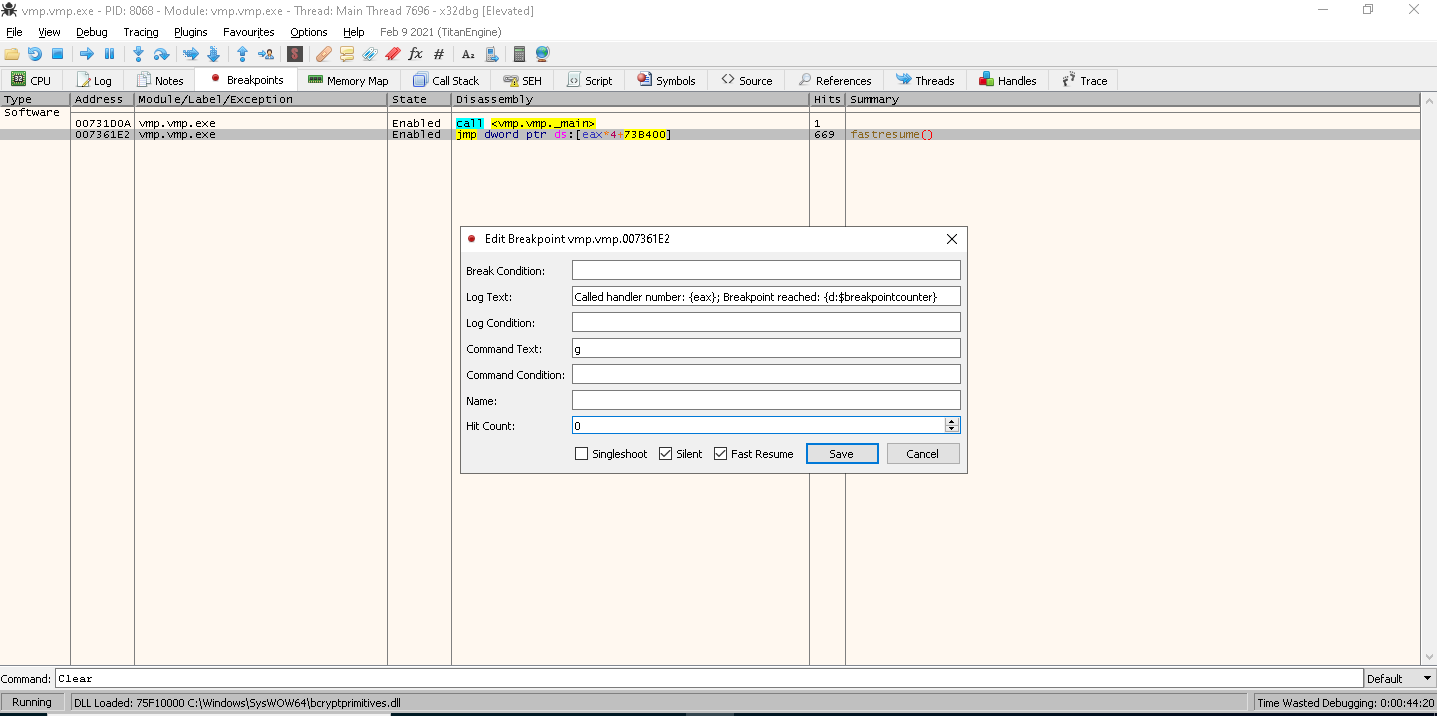
, "Log Text" . , : { : }
. eax
$breakpointcounter
.
Command Text
. , .
:

, — 669. , , . . notepad++ :
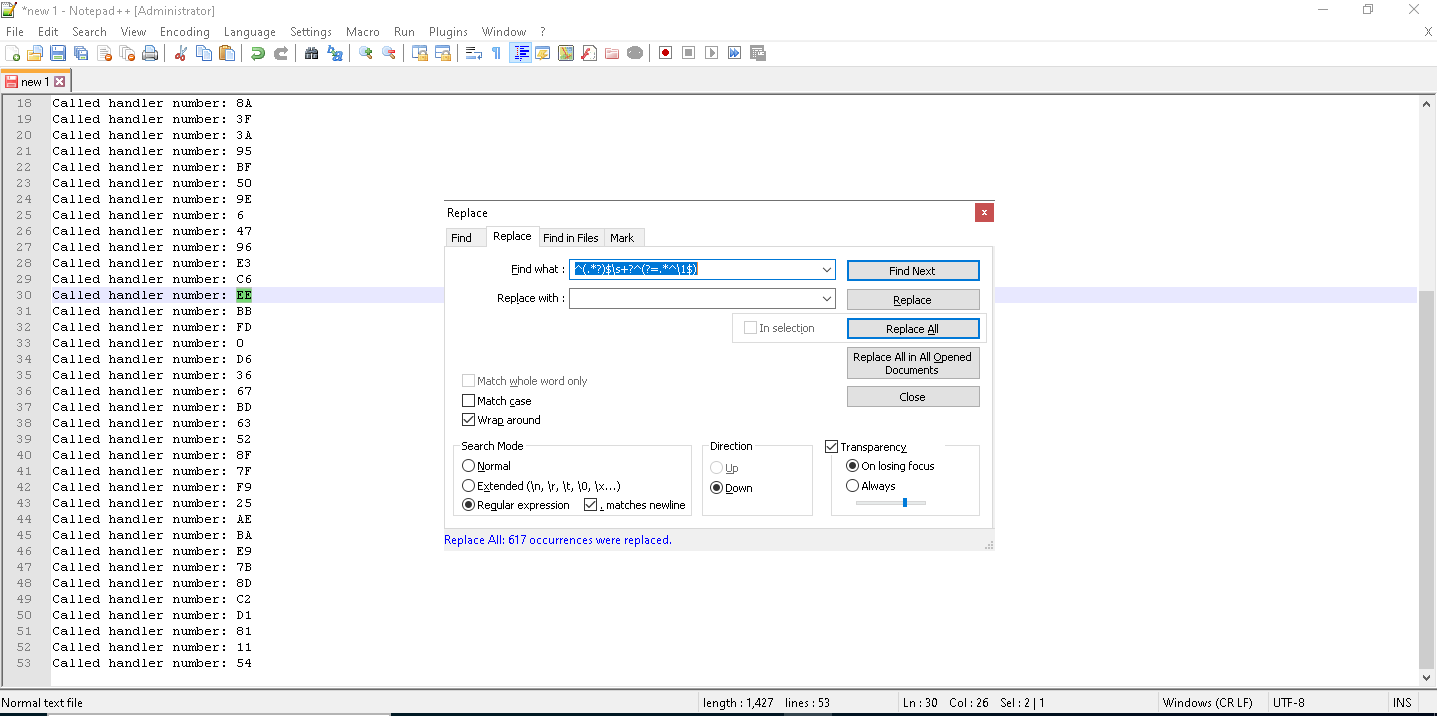
: ^(.*?)$\s+?^(?=.*^\1$)
53 . , .
, . , main loop. ? .
, :
import pefile
#
pe = pefile.PE(filePath)
#
image = pe.get_memory_mapped_image()
#
baseOffset = 0xB400
# 255
handlers = []
for i in range(255):
offset+=4
handlers.append(image[offset])
#
for h in handlers:
md = Cs(CS_ARCH_X86, CS_MODE_32)
for i in md.disasm(h, 0x1000):
print("0x%x:\t%s\t%s" %(i.address, i.mnemonic, i.op_str))
:

— . , . . .
— .
"Reverse-Engineering. Basic".
« . 2»: type confusion; .