Today we will talk about information protection: we will tell you why personal data can be turned into non-personal data and how it is done.
Modern companies don't need to talk a lot about the complexities of working with personal data. Everyone already knows how difficult it is to ensure the correct storage of such information, what serious threats even small incidents can turn into, not to mention leak scandals. There are also less obvious problems - for example, if a team creates a system that will work with data, the product needs to be tested somehow. It is better not to take real data for this, you have to modify, mask, anonymize it.
Developers have a whole range of technologies for different scenarios of working with persdata. To securely transmit information, it is encrypted. To prevent the call center operator from seeing the state of the client's account, the numbers are automatically hidden with a mask. And we want to tell you about the tokenization technology that was recently introduced in one of our projects.
What is tokenization
A token is an entity that replaces data in exchange processes between information systems. The tokenization system serves as a layer between the secure database and the systems that receive the data. It assigns to the data that correspond to a certain position in the database, a kind of identifier - a token.
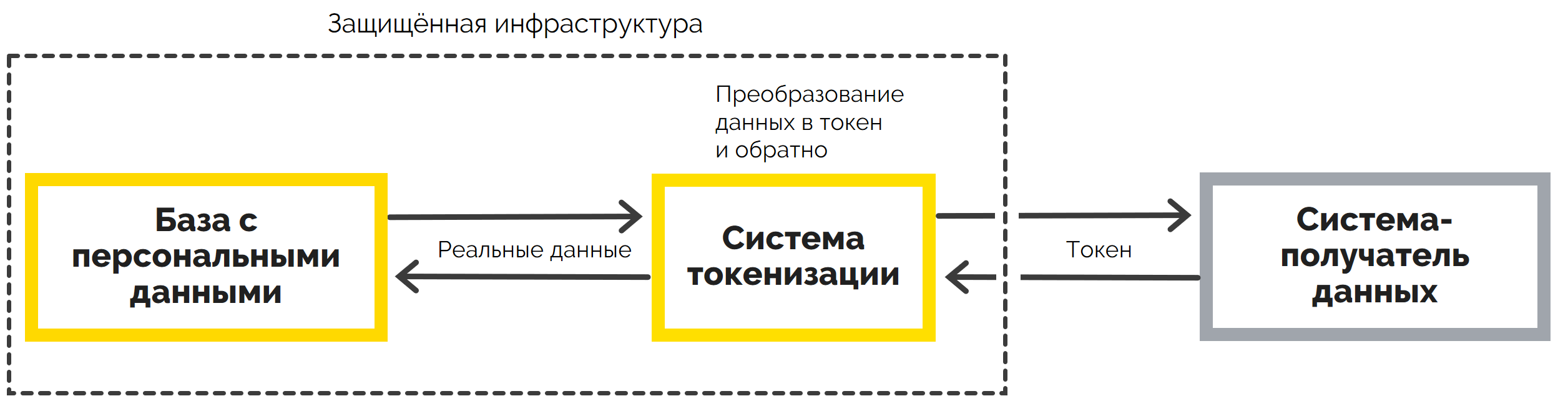
. , . , .
, . , , , - , .
. . . UI , . . , .
. - .
, , .
, . , , – - , .
- -, - , – - . , . , , ( , ).
, , , . . PCI DSS.
– , . – , – . , , . – .
, , . , , .