The task was to unite the branches with the head office of the enterprise, where the server room was located. Fortigate 60E organized Internet access and acted as a firewall at the head office, in branches it acted as Internet access Mikrotik of various models. It was also necessary to configure dynamic OSPF routing and set up IPsec VPN tunnels with GRE. Having rummaged through the Internet, I found a couple of scattered articles about connecting Fortigate to microtic via IPsec VPN and GRE tunnel. I decided to combine this information in one of my articles in order to use it myself as a cheat sheet in the future. I will write about OSPF dynamic routing in the next article.
So the input data:
1. Head office of HQ FortiOS 6.4.5:
Public IP XXXX (network interface port1)
Internal network 192.168.111.0/24 (network interface port2)
2. Branch of the enterprise Branch Mikrotik RouterOS 6.48.1:
Public IP YYYY ether1 network interface
Internal network 192.168.112.0/24 (ether2 network interface)
In fig. the connection of the main office and the branch is shown schematically.

Fortigate mikrotik, , IPsec GRE. mikrotik . GRE, Winbox mikrotik Interfaces->GRE Tunnel->+( , ), : - Local Address Y.Y.Y.Y - Remote Address X.X.X.X "keepalive", . , , , . 10 10 . . ., 100 . , . GRE IPsec "Allow Fast Path", "Local Address:" IPsec. “IPsec Secret”, IPsec. , “IPsec Secret”.

IP GRE-. IP->Addresses->+

:
/interface gre
add name=gre-tunnel1 keepalive=10s,10 local-address=Y.Y.Y.Y remote-address=X.X.X.X allow-fast-path=no
/ip address
add address=10.10.10.2/30 interface= gre-tunnel1
IPsec . phase-1, , IP , IP->IPsec->Profiles.

Peer phase-1, IP->IPsec->Peers. name Branch-HQ, FortiGate HQ, profile1, phase-1.

IPsec phase-1.

phase-2, IPsec, IPsec (AH ESP), IPsec SA. IP->IPsec->Proposals

IPsec , IP->IPsec->Policies->General. Peer Branch-HQ, . Src. Address – mikrotik Y.Y.Y.Y, Dst. Address – FortiGate HQ X.X.X.X, GRE Protocol - 47.

Action Proposal – porposal1, .
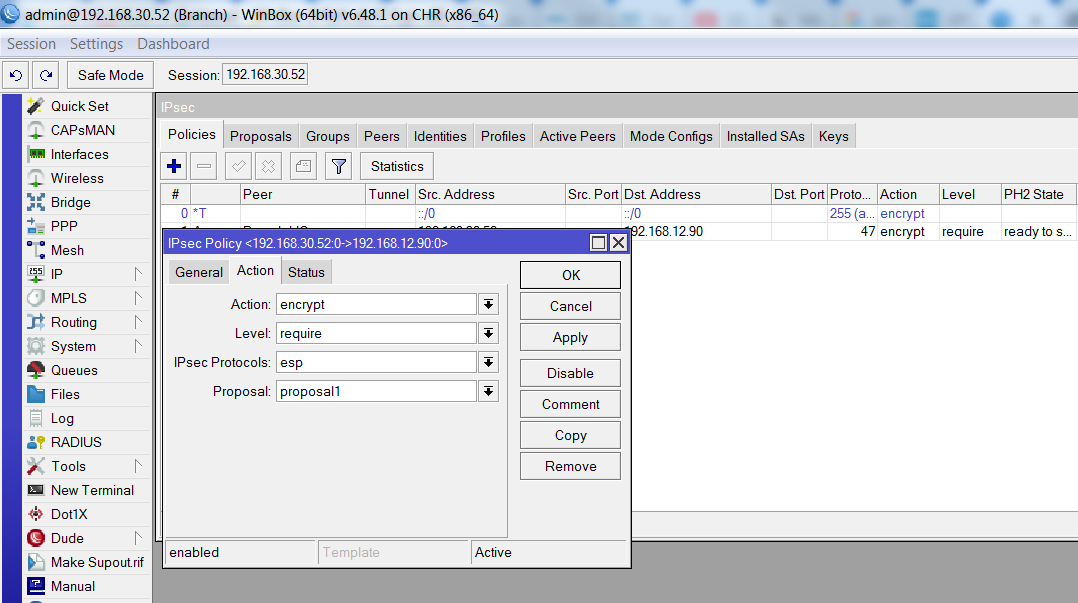
:
/ip ipsec profile
add dh-group=modp1536,modp2048 enc-algorithm=aes-256 hash-algorithm=sha256 lifetime=24h name=profile1
/ip ipsec peer
add address=X.X.X.X local-address=Y.Y.Y.Y name=Branch-HQ profile=profile1
/ip ipsec proposal
add auth-algorithms=sha256 enc-algorithms= aes-256-cbc lifetime=30m name=proposal1
pfs-group=modp1536
/ip ipsec policy
add peer=Branch-HQ src-address= Y.Y.Y.Y dst-address= X.X.X.X protocol=47 proposal=proposal1
/ip ipsec identity
add peer=Branch-HQ secret=#!@BRaNCH@!#
IP->Firewall->Filter Rules:
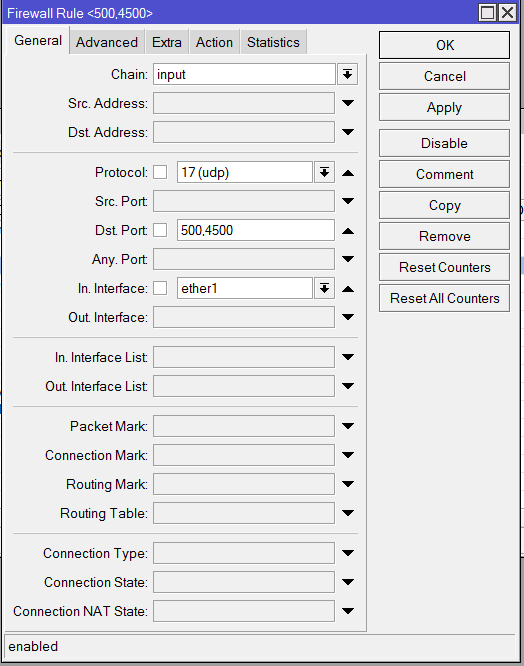

:
/ip firewall filter
add chain=input protocol=17 dst-port=500,4500 in-interface=ether1 action=accept
, :
/ip route
add dst-address=192.168.111.0/24 gateway=10.10.10.1
mikrotik , FortiGate.
FortiGate IPsec phase-1 :
config vpn ipsec phase1-interface
edit HQA-Branch
set peertype any
set proposal aes256-sha256
set dpd on-idle
set dhgrp 5 14
set auto-discovery-sender enable
set remote-gw Y.Y.Y.Y
set psksecret #!@BRaNCH@!#
set dpd-retryinterval 5
next
end
Phase-2 , “protocol 47” transport-mode ( ) GRE:
config vpn ipsec phase2-interface
edit "HQA-Branch"
set phase1name "HQA-Branch"
set proposal aes256-sha256
set dhgrp 5 14
set auto-negotiate enable
set encapsulation transport-mode
set protocol 47
next
end
GRE tunnel:
config system gre-tunnel
edit "HQ-Branch"
set interface "HQA-Branch"
set remote-gw Y.Y.Y.Y
set local-gw X.X.X.X
next
end
IP IP :
config system interface
edit "HQ-Branch"
set ip 10.10.10.1 255.255.255.255
set remote-ip 10.10.10.2 255.255.255.252
set interface "HQA-Branch"
next
end
GRE, IPsec, , . , , GRE IPsec. FortiOS IPsec . «» IPsec (, IPsec ).
config firewall policy
edit 2
set name "Enable IPsec"
set srcintf "HQA-Branch"
set dstintf "HQA-Branch"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
port2 GRE :
config firewall policy
edit 3
set name "GRE HQ->Branch"
set srcintf "port2"
set dstintf "HQ-Branch"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
edit 4
set name "GRE Branch->HQ"
set srcintf "HQ-Branch"
set dstintf "port2"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
end
GRE, GRE IPsec. , remote-gw gre-tunnel IPsec. :
config router static
edit 1
set dst Y.Y.Y.Y/30
set device "HQA-Branch"
next
edit 2
set dst 192.168.112.0 255.255.255.0
set device "HQ-Branch"
next
end
And now IPsec and GRE have risen, traffic from the local network of the head office enters the local network of the branch office and vice versa.
Used the following articles:
1. Fortinet
2. Wiki Mikrotika
This is my second work, please do not kick too much.