At present, in the era of the developed Internet, we are so accustomed to good information security of information transfer protocols that the topic of creating new protocols has somewhat receded into the shadows. Why invent something else? Just choose from the available ones. But the Internet of Things is bringing this up anew.
To illustrate the relevance, I will cite as an example the CRISP protocol , by the way, domestic development. The presence of such a development, already brought to the status of methodological recommendations of the Technical Committee for Standardization "Cryptographic information security", confirms the practical unsuitability of conventional "heavy" security protocols for the Internet of Things. They turn out to be too resource intensive.
A huge variety of various radio protocols of the Internet of Things have now spawned, but in the LPWAN field, not everywhere the developers of the transmission protocol take on the heavy burden of protecting information. It can be argued for a long time whether it is necessary to include protection in the LPWAN radio protocol at all, and not to shift it to higher levels, but if the proposed scheme is good, then one should hope for a high probability of introducing the standard into the industry. The main thesis: in general, it is no longer possible without protection on the Internet of Things. And it should be up to par.
The OpenUNB developers also reasoned, putting energy efficiency and built-in information security at the forefront. For those who still do not know anything about OpenUNB, I advise you to read the previous articles on this topic:
- Internet of Things in Russian. Minimalism and openness OpenUNB
- Internet of Things in Russian. The multichannel power of the OpenUNB base station physical layer
- Internet of Things in Russian. Noise-immune coding in OpenUNB
- Internet of Things in Russian. Link layer OpenUNB. General provisions and device addressing
- Internet of Things in Russian. OpenUNB activation procedure
and also study the original source on the Skoltech website.
Today we will consider the mechanism of cryptographic protection of transmitted data (encryption, integrity and authenticity control).
, - , , . OpenUNB K0, k, 128 256 . , , , . .
OpenUNB Na Ne, . :
Km Ke:
OpenUNB «», n = 64 k = 256 , 34.12-2015.
:
Nn — , :
P n MACPayload. len –
,
MACPayload ( len 16 48), :
len = 48 n = 64,
CMAC24 " " .
. :
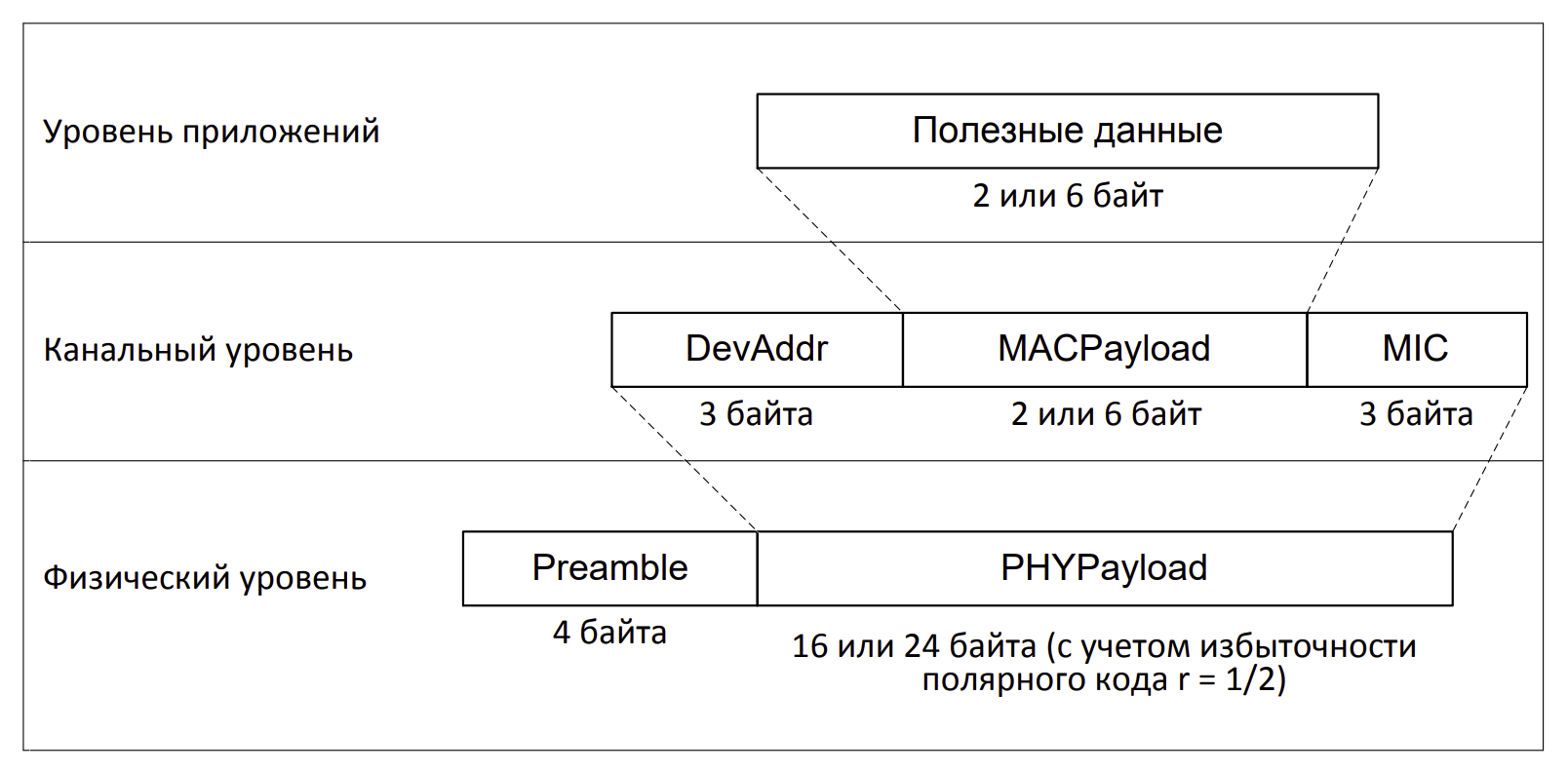
In more detail, with all the details, you can read about security in OpenUNB in the primary source .
As we can see, the developers have tried to make energy efficiency and protection in OpenUNB uncompromising. However, one of the goals of my publications is to get experts to take a close look at OpenUNB and constructively criticize the protocol.
As always, the sources of crypto-transformations from deef137available on Github .