Hello, Khabrovites. For future students of the course “Reverse-Engineering. Basic ” Alexander Kolesnikov has prepared a useful article.
We also invite everyone to visit the open webinar on the topic "Exploitation of vulnerabilities in the driver . " The first part of the webinar will be an example of the classic buffer overflow vulnerability as well as the integer overflow vulnerability. Also, participants, together with an expert, will analyze the features of developing exploits in kernel mode.

2 — , , . . , , Internals.
Disclamer: .
« » , — . — . — , . :
, ;
;
;
;
;
«», «».
, , . . WinLicense, Themida, Enigma Protector.
. , , . , , . FinSpy RAT, « ».
— . , . . ? ? .
? , , , . 2 :
, , . .
, . , , . , . « ».
:
;
switch , ;
, . , . Themida, , 4 . , .
, — switch . , :

? :
;
;
;
;
( native );
.
.
VMProtect 1.1 . . :
#include <iostream>
int main
{
std::cout<< "Hello World!" <<std::endl;
system("pause");
return 0;
}
release . Main :
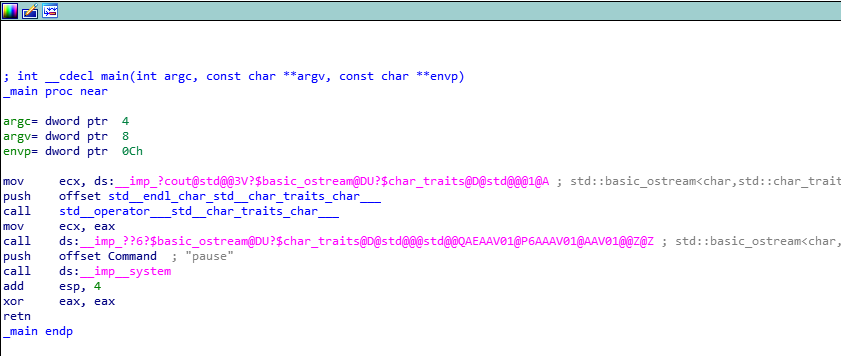
VMProtect
:

- , switch , .
:

. , .

, , . , :

edx .
, :

.
« ».