
Who is this article for
An article for interface designers who want to understand how the registration, authorization, password recovery processes used in various systems work. If you are a developer / designer, and you find an error / inaccuracy, then let me know (I will gladly finalize the article).
Start
Today I would like to talk about how authentication takes place in applications of various platforms - from mobile applications to console utilities.
Authentication is the process by which a user authenticates their identity to a system. The system provides personal data only to its owner.
The authentication mechanism at the basic level is quite simple - you need to enter data in the form of a username and password. Check the data for a match, and if the data match, then you are the true owner of the account.
An account is a collection of user data stored in the system. As a rule, only one user has access to an account - its owner.
Example:
In the movies, when a spy is asked to name a passphrase to confirm his identity, then, in fact, the user authentication process is carried out. If the passphrase (password) is correct, then the spy is trusted and provided with data hidden from the rest. (Exaggerated)
Authentication processes
- ( ) - , , . , .
(CREATE) -
(READ) -
(UPDATE) - - , .
(DELETE) -
()

- . :
Email (username@mail.com)
(+996 777 777 777)
(username)
(Google, Facebook, Apple… )
- , . ( Google, Figma). /.
()

- , (), - ( - ).
- ( ) , (, , , ). , , .
. : , , .
, . , , .
. :
|
|
|
|
|
|
|
|
|
|
|
PIN |
PIN |
PIN |
|
|
|
|
SMS |
|
- , - .


.
, , , .
.
.

, - . - Email + , .
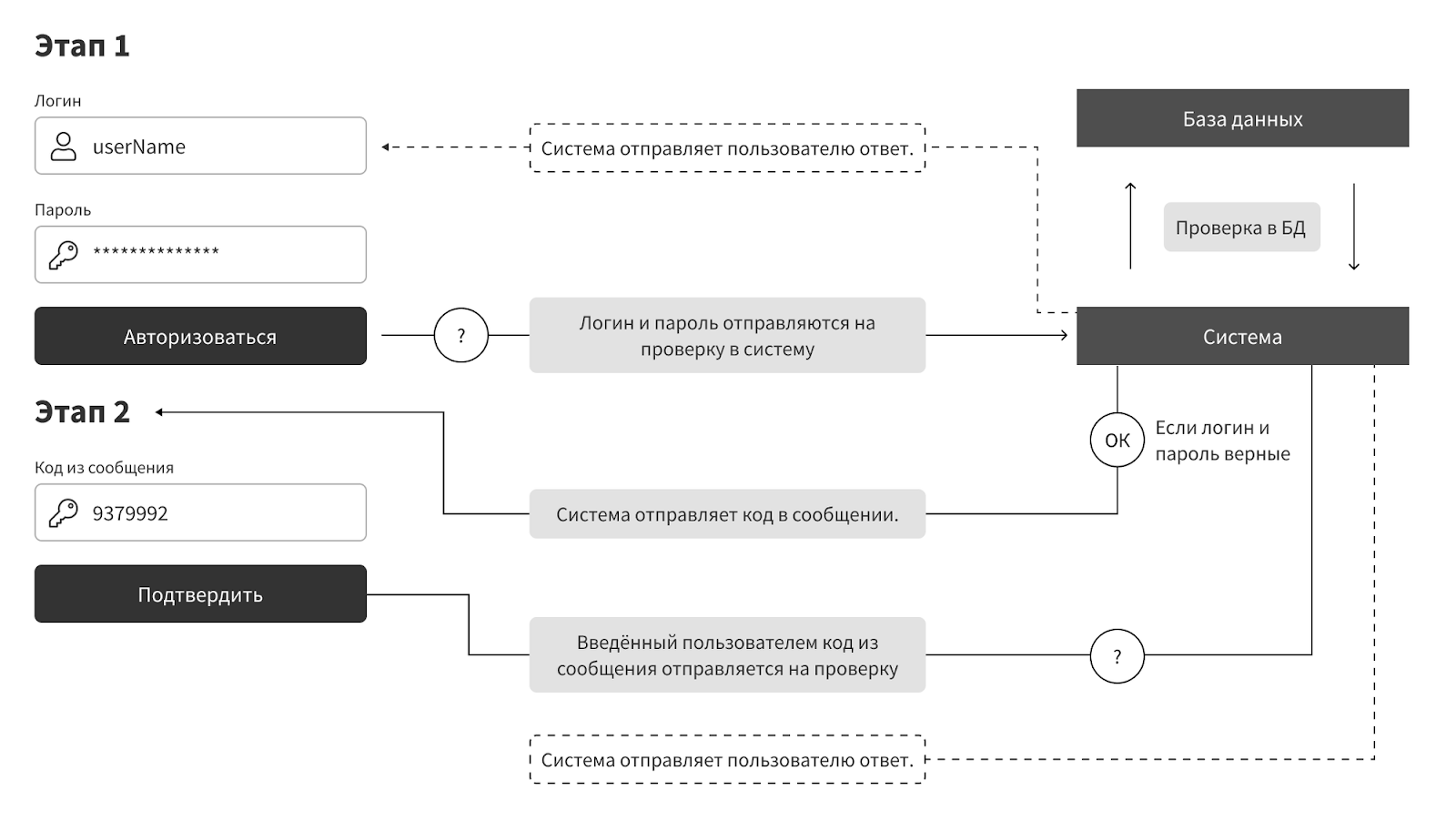
, - . , ( ) . , . - . . . - . - , .

, .
,
. , . ( ).

, - . .
( )
.
. , - .
, - . , .
""
- . . - , .
- (), Cookies. , ( ) .
Cookies

Cookies - , () . , - Cookies, . - () , () .
, .
In this article, we examined the basic principles of how authentication works in various systems. This entire article is aimed at helping interface designers understand how the authentication process works, what it is for, what types it is and what happens at most stages during authorization, registration, password recovery by the user.
I hope it was useful to you, and at least a little interesting.