Introduction

Hello everyone!
I work in the field of information security and analyze the security of web applications. In my free time, I try to improve my technical skills and therefore practice bughanting on the hackerone platform or solve labs on the hackthebox .
In general, it is logical to carry out any analysis of a web application from the stage of collecting information or reconnaissance (as you like, this does not change the essence). At the stage of collecting information about the system under investigation, I use a tool called nmap . I dare to assume that this legendary utility needs no introduction, but if suddenly someone did not hear here is the link .
Nmap is a console application (yes of course there are various forks, for example Zenmap, etc.), and its output is also displayed in the console by default. Of course, it also supports saving to a file, in different formats, I will not dwell on this in detail, anyone interested can see the full list of keys. ( List of options for Nmap ).
All is well when you scan N - hosts, and this N does not exceed 10 or 20 pieces. But what if the number of hosts becomes much larger? Now let's imagine that some of these hosts, for example dev.example.com or test123.example.com, were simply forgotten by the developers to decommission and they are not included in the analysis? Every time you write a report and spend a significant part of your time on it?I'm not a fan of scribbled reports at all, especially at such a simple stage. Therefore, I began to look for simple ways to solve this problem.
As the classics said, everything ingenious is simple.
nmap-bootstrap-xsl
Link to developer's github Produces a
nice html page where everything is conveniently broken down and presented.


How to use?
1. Download the stylesheet itself link
2. Add nmap-bootstrap.xsl as a stylesheet to your Nmap scan with the --stylesheet argument:
nmap -sS -A -p0-65535 -oA drive2 --stylesheet /home/kali/OSINT/nmap-bootstrap-xsl/nmap-bootstrap.xsl -iL /home/kali/Documents/Habr/drive2_domain.txt
drive2- the name of the xml file that will be created after nmap
3. Use xsltproc to convert the file to html.
xsltproc -o drive2.html /home/kali/OSINT/nmap-bootstrap-xsl/nmap-bootstrap.xsl drive2.xml
drive2.html - the name of the html page that will turn out
drive2.xml - the name of the xml file that was created after nmap
Demonstration of work
To demonstrate the work we take any open program on bug bounties, for example DRIVE.NET, Inc .

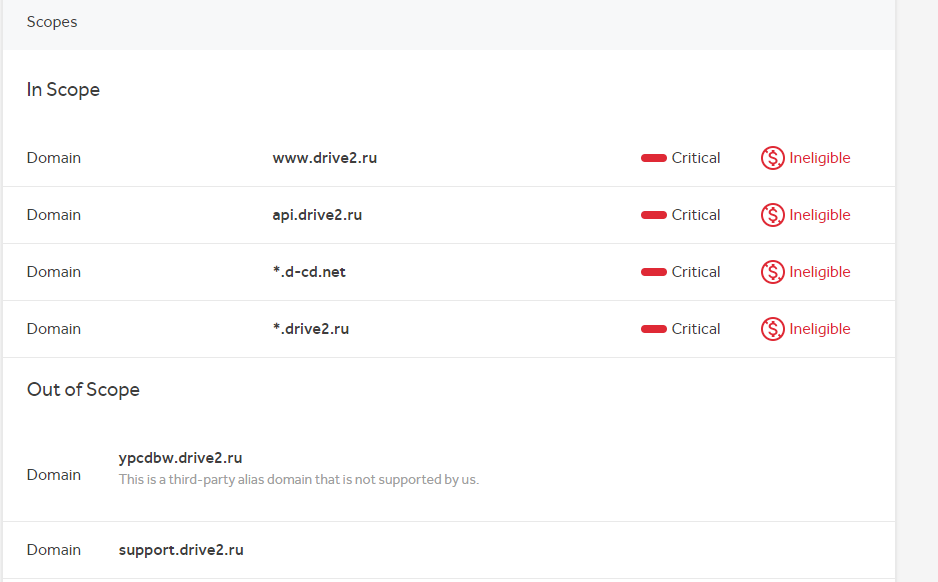
Let's find all the domains of the * .drive2.ru domain and scan them with nmap right away using the nmap-bootstrap-xsl style.
1. Search for domains of the * .drive2.ru domain using sublister ( link to github )


2. Run nmap scan
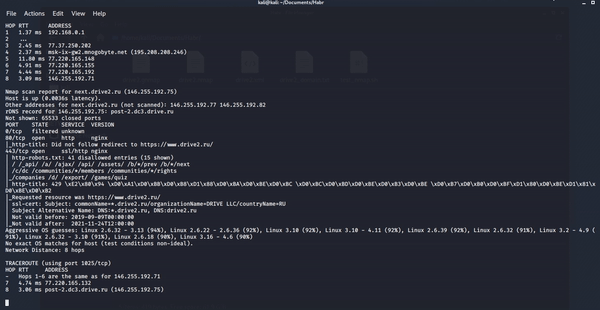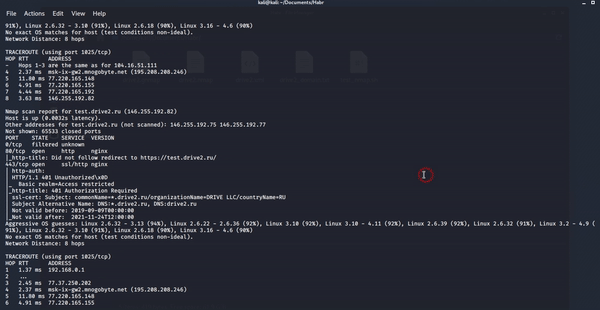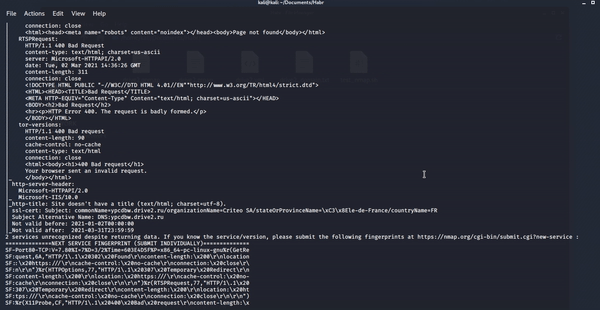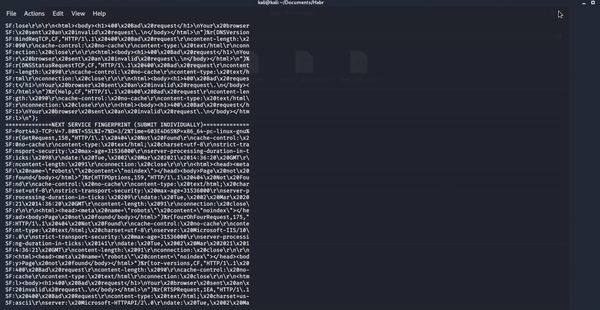
3. Received files after scanning.

4. Use xsltproc to convert the file to html.
xsltproc -o drive2.html /home/kali/OSINT/nmap-bootstrap-xsl/nmap-bootstrap.xsl drive2.xml
5. We look at the result

An example of the final html page added to Yandex disk. ( link to Yandex disk )
Output
The presented solution is as simple as possible. You just need to download this style and enable it when scanning. This will allow you to get a list of hosts with open ports and services, in a convenient readable form.
I hope the information provided will help you save time on the tasks that I encountered and described in the article.
It would also be interesting to know who uses what for such tasks. It will be cool if you share something interesting in the comments. All beaver.