Introduction
Digital transformation (DT) is primarily an innovative process that requires fundamental changes in industrial technologies, society and culture, financial transactions and the principles of creating new products and services. In fact, it is not just a set of IT products and solutions to be deployed in companies and in production, but a global redefinition of approaches and strategies in business, carried out using information technology. Digital transformation is a transition period to the sixth technological order during the fourth industrial revolution (Industry 4.0).

Fig 1. Digital transformation - the transition to the 6th technological paradigm
Not all companies are ready for the new and rather stringent requirements of the DH, namely, for a complete modernization of business methods, revision of internal business processes and a new culture of relationships within the company. Moreover, management must be prepared for both the positive and negative consequences of digital transformation.
Digital transformation is not just the automation and digitalization of individual production processes on the ground, it is the integration of conventional office and industrial technologies that we use on a daily basis, with completely new IT-specific areas for DH (cloud computing, artificial intelligence and machine learning , IoT, etc.).
The negative consequences of digital transformation
However, there is a negative side to the processes that digital transformation brings about. The revolutionary changes that the DH business brings to the business have generated certain problems for information security services (IS), namely, new vectors of information security threats have emerged and the range of vulnerabilities for potential cyberattacks has expanded.
"Fashionable technology" DevOps is a subject of special alertness of information security specialists, since it fundamentally changed the relationship between software developers, system administrators, and technical services. support and end users. ( DevOps methodology means integrating the activities of developers and maintainers of software, networks and equipment in teams and companies).

Figure 2. What is DevOps
I would also like to note that one of the major obstacles to the rapid implementation of DH in companies is the old (legacy) technologies that have been serving production and office processes for many years. On the one hand, they cannot be replaced quickly (without stopping business processes), and on the other hand, they do not fit well into digital transformation processes and carry multiple information security threats.
Below we will dwell on the main problems of information security, and also outline the ways of resolving these problems in the course of DH.
Information security problems in a DH environment
1. Non-transparency of information security events in the corporate infrastructure of enterprises
Large companies everywhere use various technological locations deployed in cloud services, moreover, equipped with their own information security tools and various internal services. However, there are still problems, both with the integration of such solutions, and with the transparency and recording of all incidents and information security events in such a complex IT infrastructure. Moreover, digital transformation implies significant growth, both cloud solutions and the complexity of corporate infrastructure due to the introduction of IoT, blockchain, AI, etc.
2. Difficulties with the issue of automating all information security processes
In an ordinary medium or even large company, many information security processes remain non-automated, and even a general approach to their automation has not been developed. However, the employees of the information security departments of such companies are confident that the protection works for all possible attack vectors, both inside the perimeter and in the clouds, on mobile devices, web servers, etc. firewalls, intrusion detection systems, etc.) still provide a certain level of security in certain areas and reduce the number of information security incidents, but without developing a general strategy and security policy in such an organization, there will certainly be problems with information security in the future, during the implementation of DH ...
3.Integration of information security solutions
I would like to note that in most organizations it is still bad with the integration of various information security solutions, there is no end-to-end visibility of all threats, it is bad with the control of compliance with the requirements of regulators (compliance).
4.Flexible scaling
According to the results of surveys and research in the field of information security, experts have found that at many enterprises, a quarter of the corporate infrastructure remains unprotected. As the IT infrastructure grows due to digital transformation, as well as in connection with the complexity of cyber attacks, there is a need for scalability of information security solutions. And even if the company has effectively working solutions that protect individual components of the IT infrastructure (for example, antiviruses, firewalls, etc.), then in general this does not increase the overall level of security in the organization, due to poor integration and scalability of these individual solutions ...
At the moment, the biggest problem for cybersecurity professionals is complex polymorphic cyberattacks, targeted cyberattacks (APT, advanced persistent threat), as well as the growing use of DevOps methodology, which increases the risk of untimely discovery of new vulnerabilities.
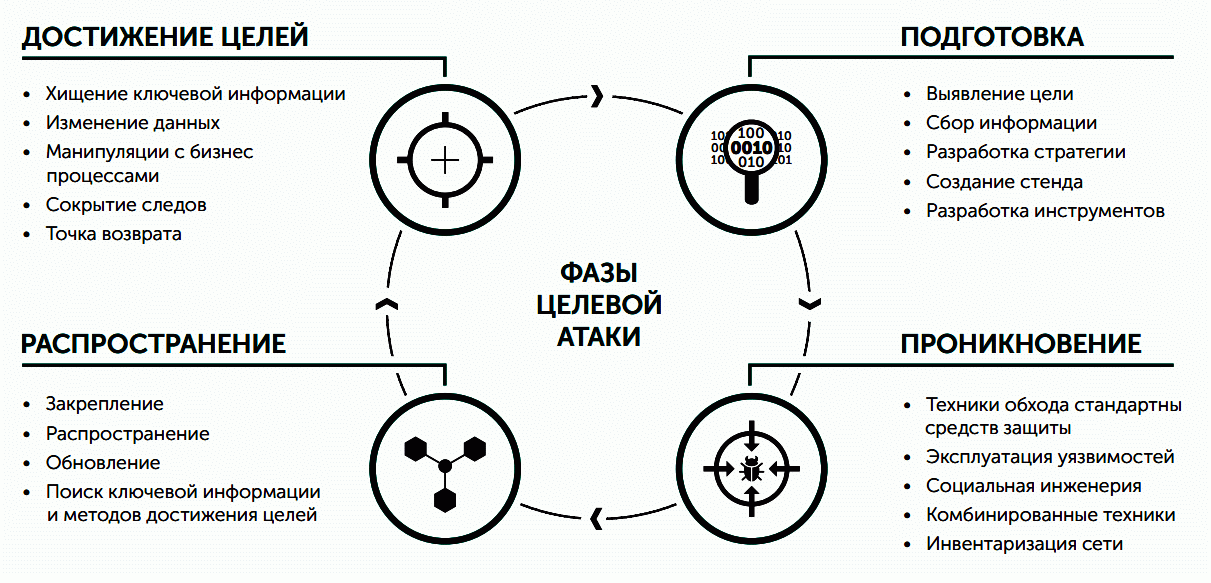
Fig 3. Phases of an advanced persistent threat (APT).
5. Consequences of software updates
Until now, there are still dangerous threats associated with updating software, since often along with "patches" and "updates" can be installed and malicious software.
DH security strategy or threat countermeasures
In the future, DH can be used both for positive changes in society and for realizing a threat to global stability and security. Such a negative example is the so-called "cyber weapon". In order to determine the security strategy of your business and public administration systems in the conditions of constantly growing instability, you need to understand for yourself in general what “security” is and what it is.
Thus, the very concept of "security" is divided into 3 large groups: personal, public and state.
Personal safety is a state when a person is protected from any type of violence (for example, psychological, physical, etc.)
Public safety is the ability of social institutions of the state to protect the individual and society from various types of threats (mainly internal).
State security is a system for protecting the state from external and internal threats.
Another important area of security is information security and information protection. The goal of information security specialists is to ensure its confidentiality, availability and integrity. In general, these three key principles of information security are called the CIA triad , below we will reveal the meaning of these concepts.
- Confidentiality (from the English "confidentiality" ) is the property of information to be closed to unauthorized persons;
- Integrity ( .«») — ;
- Availability ( . – «») — .

Fig 4. Three key principles of information security (triad of CIA)
The main goal of information security in the context of DH is to ensure the security of both information and IT infrastructure from accidental or deliberate influences (attacks, etc.) that can cause unacceptable damage to the owners information assets.
Particular attention should be paid to information security incidents at critical information infrastructure (CII) facilities, these can be both targeted attacks (APT) and man-made disasters, physical theft of assets, and other threats. As the attacks become more sophisticated, so do the “defenses” (that is, the information security infrastructure).
Against this background, SIEM systems (Security information and event management) are gaining more and more popularity, the main task of which is to monitor corporate systems and analyze security events in real time, including with the widespread use of AI systems and deep machine learning (Deep learning). ...
Large technology companies that lead in the field of DH are much more likely than others to integrate their products and information security tools into a single corporate security architecture. It should be noted that in such companies they give preference to a strategic approach and the formation of a security policy, which allows:
- quickly detect threats and promptly respond to them;
- provide high-quality protection of information assets;
- have a transparent technological environment for threat detection.
Leaders of digital transformation, as a rule, are more willing to automate information security processes in the company, it is much more effective than manual monitoring of threats and information security events, which was used everywhere before the period of DH. A positive example of this automation and integrated approach is the implementation of the SOC (Security Operations Center). However, it should be borne in mind that setting up the automation of all work processes requires more testing time and the need to attract competent specialists.
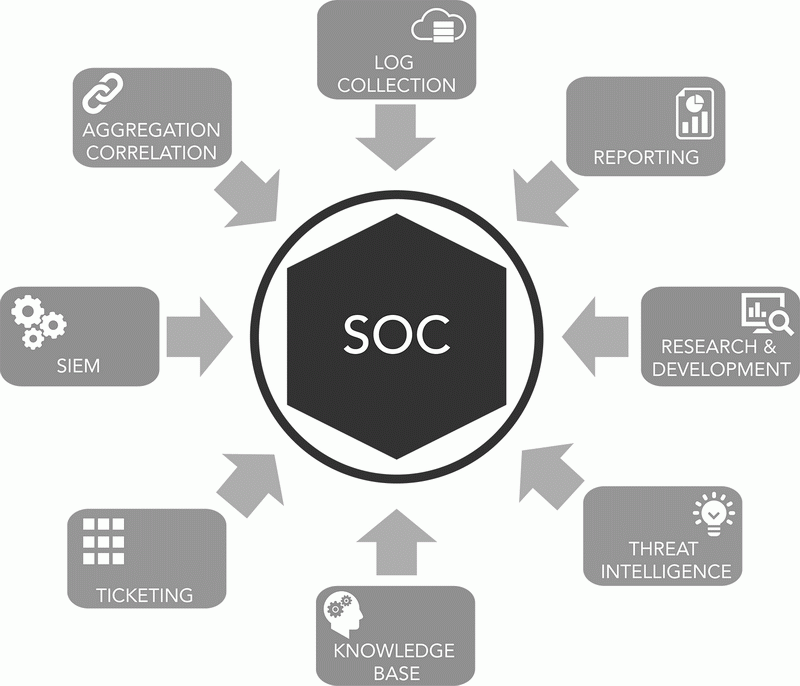
Fig 5. Implementation of SOC (Security Operations Center) in the company
One of the features of information security in the era of digital transformation is the process of introducing into the corporate system the means of centralized control of compliance with both industrial standards and IT and information security standards, which increases the efficiency of such an area of information security as compliance.
Conclusion
One of the major obstacles on the way of companies to DH is the need to ensure a high level of information security, which is not always within the reach of most companies, especially firms from the SMB sector. At the same time, it is necessary to take into account the growth factors of both internal and external information security threats associated with a significant growth in the cybercrime sector, as well as risks arising naturally during the implementation of the DevOps methodology, cloud technologies, IoT, etc.
One of the fairly new, but effective approaches to ensuring the security of information assets is the use of proactive defense methods that can not only protect, but also prevent cyberattacks. Here I would like to mention technologies such as honeypots and honeynets, as well as more advanced systems for deploying a distributed infrastructure of false targets (Distributed Deception Platform, DDP).
As a result, we can highlight the best information security practices that we can recommend to companies and businesses during the digital transformation process:
- build a unified security architecture that will provide centralized management of IT infrastructure and transparency of all information security events;
- develop a corporate network protection strategy and company security policy;
- implement built-in controls for compliance with standards and regulatory requirements;
- use methods of both preventive and proactive protection.
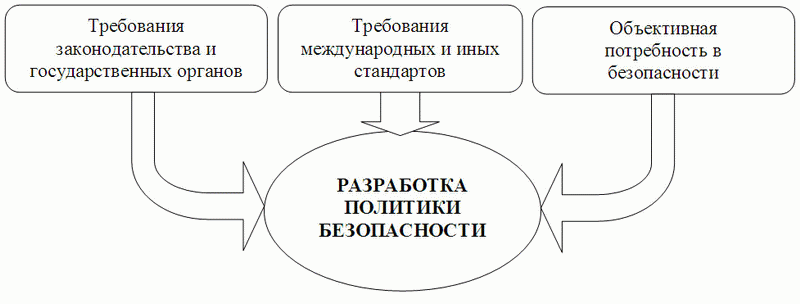
Fig 6. Strategic approach to information security - development of a company's security policy